- Cisco Community
- Technology and Support
- Small Business Support Community
- Other Topics - Small Business
- Re: RV340 L2TP/IPSEC VPN with Windows 10 clients - how secure it is?
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RV340 L2TP/IPSEC VPN with Windows 10 clients - how secure it is?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-07-2021 01:28 PM
We just upgraded to RV340 as our company main gateway and I had to configure the network. As we need to work remotely I wanted to set up a VPN server - and there was first shock as RV340 to my knowledge has no OpenVPN server built in. I need a secure tunneling so PPTP is not an option so i decided to setup L2TP server - how hard can it be?
As I found ot it is unnecesarly hard as neither Cisco nor Windows have an obvious instructions how to do it. I had some problems as I am new to the cisco products and there are separate manuals on how to add use, user group or prepare L2TP server but those manuals are separate for all the steps and in different places on the support page. But the real nightmare was to setup Windows client to use a secure tunneling (I do not consider 3DES and SHA1 secure). Here is step by step how I configured my router:
1. Under System Configuration add user group with selected L2TP option only,
2.Under System Configuration add user in the user group from step 1,
3. Ad a new IPSec profile:
IKE Version: IKEv1
Phase I options: DH Group - Group2, Encryption - AES-256, Authentication - SHA2-256
Phase II oprions: Protocol Selection - ESP, Encryption - AES-256, Authentication-SHA2-256, PFS - off
4. I turned on the L2TP server with user group from step 1, IPSEC on and selected profile from step 3 and assigned preshared Key
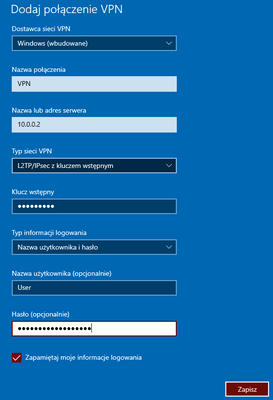
5.To setup a VPN client in windows I added a new network in Windows VPN Settings
6.To force Windows to use IPSEC settings compatibile with what I prepared on the router I had to run PowerShell as administrator and use a command to set the IPSEC for my connection:
Set-VpnConnectionIPsecConfiguration -ConnectionName "VPN" -AuthenticationTransformConstants SHA256128 -CipherTransformConstants AES256 -EncryptionMethod AES256 -DHGroup Group2 -IntegrityCheckMethod SHA256 -PfsGroup None
7.Last step was in network settings to setup the connection to use PAP (I found that somwhere on the support page, no idea why not CHAP)
Finally I could establish a tunnelled connection with our servers. But I am not sure how secure is this connetion. I have no idea on how to make any changes to the Phase II IPSEC settings or enable PFS. Also I would prefer to have CHAP instead of PAP. So my question is how secure connection do I have finally? Adn why does it have to be that complicated?
- Labels:
-
Small Business Support
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2021 02:12 AM
Hello Adam,
It is secure but not the latest and most secure method we would say. The point is at that time the RV34x series do not have implemented CHAP as a local database authentication method. Please refer to the following thread for more info: https://community.cisco.com/t5/vpn/is-using-pap-with-l2tp-secure/td-p/807276
Regards,
Martin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2021 04:10 AM
Hello Martin,
for now I reached an acceptable level of security then. Are there plans to implement CHAP in forseeable future?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-08-2021 04:34 AM
Hi Adam,
No such plans so far at least in the near future.
Regards,
Martin
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide