- Cisco Community
- Technology and Support
- Security
- Network Access Control
- 802.1x in Windows 10 with Hypver-v
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-12-2016 11:39 AM - edited 03-10-2019 11:34 PM
Hello,
I'm trying to get Windows 10 with Hypver-v enabled to successfully complete 802.1x negotiations and posture assessment with Cisco ISE. When Hypver-V is enabled on Windows 10 with an External type vSwitch, the 802.1x service is moved from the physical NIC to the vSwitch nic. The issue I have noticed is that the vSwitch nic does not respond to any EAPOL messages. As a workaround, I have tried to leverage the Cisco NAM module to negotiate 802.1x which does work, but the issue is that the Cisco Anyconnect Network Access Manager Filter Driver does not recognize the existence of the vSwitch nic.
In the below pic, 802.1x auth completed successfully but anyconnect can't determine the status because the Filter Driver is not functioning on the vSwitch nic.
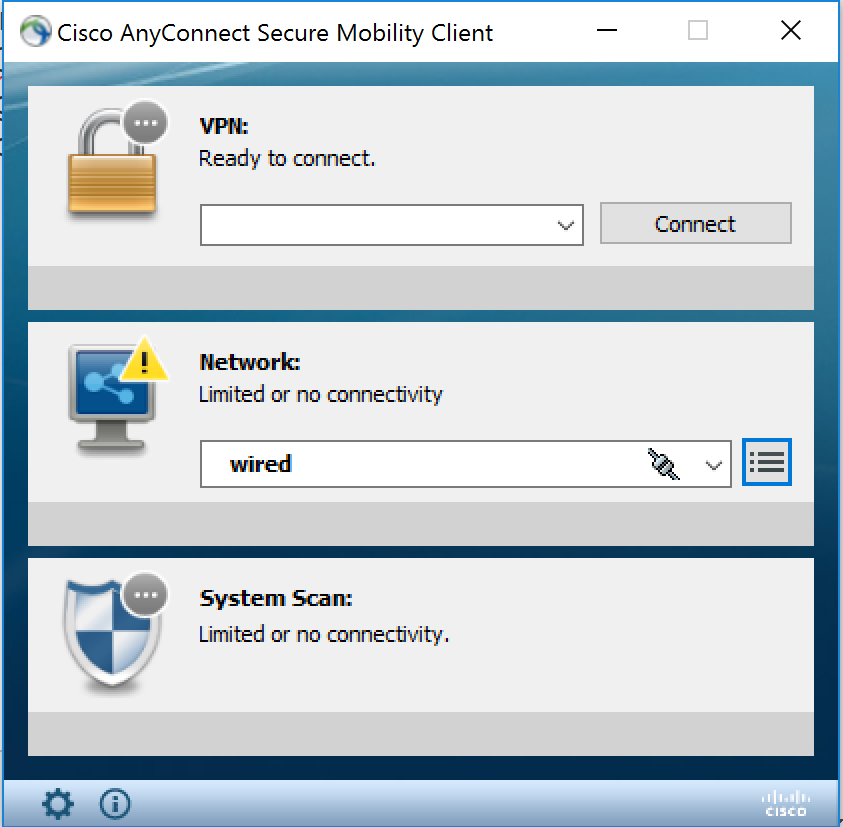
vSwitch nic (Filter Driver is there but non functional. If I click the checkbox and then click Ok Windows prompts to disable the driver which is odd. It is as if Windows believes the driver is falsely enabled.)
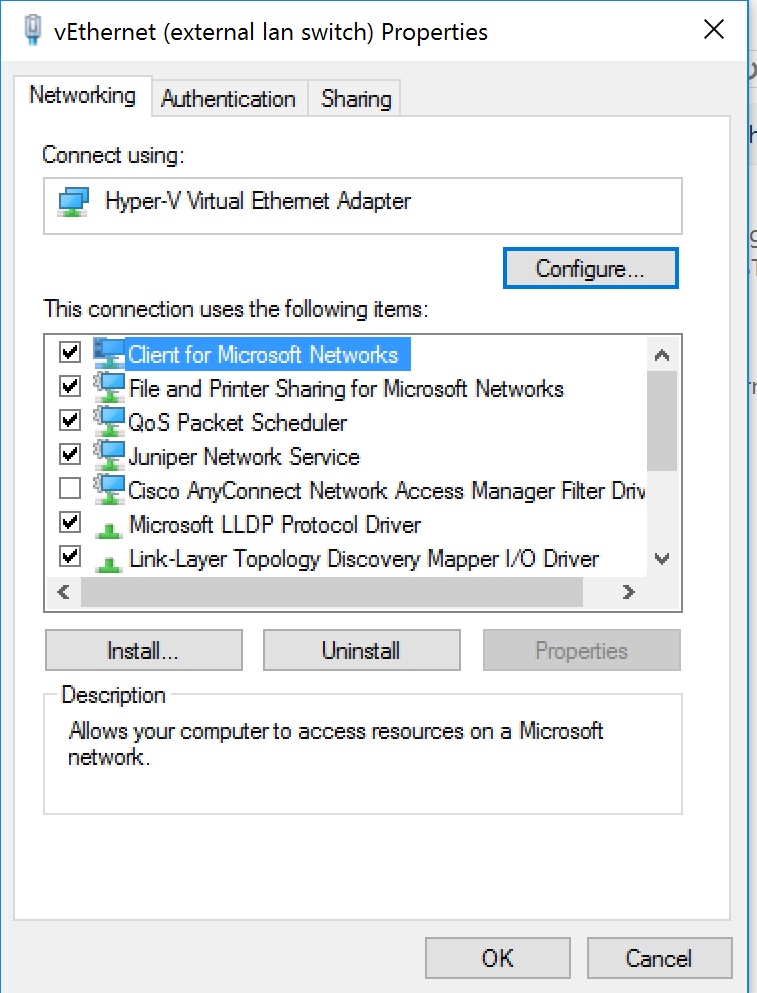
The physical nic has the Filter Driver enabled but because Windows 10 has moved all the network functionality to the vSwitch nic, Cisco NAM is looking in the wrong place.

Thank you for your help.
Solved! Go to Solution.
- Labels:
-
AAA
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 05:27 PM
It is supported with Windows Server 2019 & Windows 10 version 1809 and above. 802.1x through the Hyper-V vSwitch is supported by making following registry edit:
Run the following from an elevated command prompt.
reg add “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\vmsmp\parameters” /v 8021xEnabled /t REG_DWORD /d 1 /f
shutdown /r /t 0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-29-2016 12:32 AM
Hi Steven-
The issues that you are facing are not with the supplicant/client but the network access device (NAD) which in your case is the vSwitch which does not understand/support 802.1x/EAPoL.
To provide secure access in your scenario you will also need the Nexus 1000v and SGT/SGA/TrustSec.
Have a look at the following link:
Thank you for rating helpful posts!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-16-2019 05:27 PM
It is supported with Windows Server 2019 & Windows 10 version 1809 and above. 802.1x through the Hyper-V vSwitch is supported by making following registry edit:
Run the following from an elevated command prompt.
reg add “HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\vmsmp\parameters” /v 8021xEnabled /t REG_DWORD /d 1 /f
shutdown /r /t 0
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide

