- Cisco Community
- Technology and Support
- Security
- Network Access Control
- Integrate ISE with MS Active Directory for logins Authentication
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2018 05:09 PM - edited 03-11-2019 01:50 AM
Hi All,
Cisco ISE (2.4 ) is integrated with Microsoft AD. I would like to restrict ISE logins with AD logins like
These groups can be created in AD.
Groug1 - Full access
Group2 - RO Access
Grout3 - Sponsor Access
I just want make some account to access ISE login. I research on this requirement but could not find relevant documents. Please help!
Thanks
Sri
Solved! Go to Solution.
- Labels:
-
Identity Services Engine (ISE)
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2018 06:22 PM
Hi!
That's quite simple but you have to have everything tuned inside ISE, the guide for this is https://www.cisco.com/c/en/us/td/docs/security/ise/2-4/admin_guide/b_ise_admin_guide_24/b_ise_admin_guide_24_new_chapter_0101.html#ID269 and you can see that you can assign access based on a specific role, but for a summary you should:
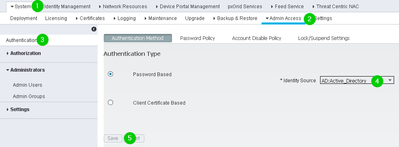
1. Inside Administration > System > Admin Access > Authentication you should change the password based method:
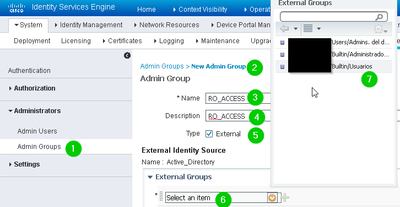
2. Then, inside Administration > System > Admin Access > Administrators > Admin Groups then add a new group:
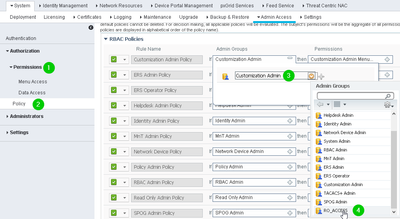
3. And last, you create a Policy inside Administration > System > Admin Access > Permissions > Policy for each group:
4. Optional, if you want to use a different Permission options that you might need, please consider going to Administration > System > Admin Access > Permissions > Menu Access / Data Access to control your permissions list.
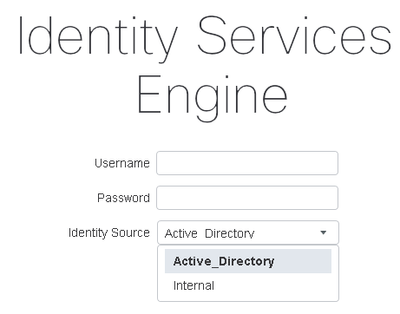
In the field you should find that the Cisco ISE 2.4 enables the option to choose wheather to connect via internal users or Active Directory option in the login page:
Hope it helps,
**please, consider rating helpful or as a solution, thank you**
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2018 04:10 AM
Angel gave a good start, but no need to create new admin groups.
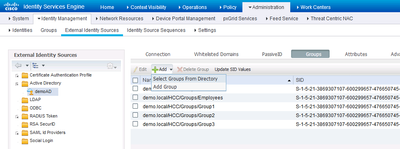
First of all, add the three groups from AD.
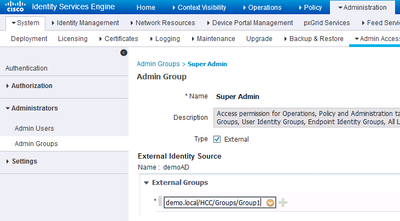
For "full" ISE admin web access, after selecting AD as the ID source, go to "Super Admin" group, check the option "External" and put "Group1" as the External Group.
For RO ISE admin web access, go to "Read Only Admin", check the option "External" and put "Group2" as the External Group.
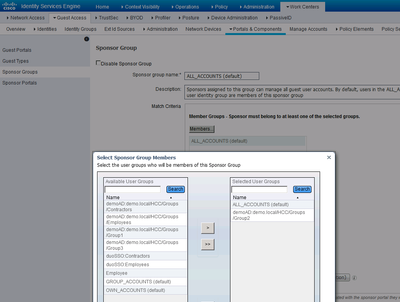
For Sponsor access, go to the Sponsor Groups, select the desired access, and pick members from the list of available groups.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-20-2018 06:22 PM
Hi!
That's quite simple but you have to have everything tuned inside ISE, the guide for this is https://www.cisco.com/c/en/us/td/docs/security/ise/2-4/admin_guide/b_ise_admin_guide_24/b_ise_admin_guide_24_new_chapter_0101.html#ID269 and you can see that you can assign access based on a specific role, but for a summary you should:
1. Inside Administration > System > Admin Access > Authentication you should change the password based method:
2. Then, inside Administration > System > Admin Access > Administrators > Admin Groups then add a new group:
3. And last, you create a Policy inside Administration > System > Admin Access > Permissions > Policy for each group:
4. Optional, if you want to use a different Permission options that you might need, please consider going to Administration > System > Admin Access > Permissions > Menu Access / Data Access to control your permissions list.
In the field you should find that the Cisco ISE 2.4 enables the option to choose wheather to connect via internal users or Active Directory option in the login page:
Hope it helps,
**please, consider rating helpful or as a solution, thank you**
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-23-2018 08:44 AM
This is the trick, that I forgot. Once It is enabled, I managed to complete rest easily. Thank you again!!!
@Angel_Inglese wrote:
Hi!
That's quite simple but you have to have everything tuned inside ISE, the guide for this is https://www.cisco.com/c/en/us/td/docs/security/ise/2-4/admin_guide/b_ise_admin_guide_24/b_ise_admin_guide_24_new_chapter_0101.html#ID269 and you can see that you can assign access based on a specific role, but for a summary you should:
1. Inside Administration > System > Admin Access > Authentication you should change the password based method:
2. Then, inside Administration > System > Admin Access > Administrators > Admin Groups then add a new group:
3. And last, you create a Policy inside Administration > System > Admin Access > Permissions > Policy for each group:
4. Optional, if you want to use a different Permission options that you might need, please consider going to Administration > System > Admin Access > Permissions > Menu Access / Data Access to control your permissions list.
In the field you should find that the Cisco ISE 2.4 enables the option to choose wheather to connect via internal users or Active Directory option in the login page:
Hope it helps,
**please, consider rating helpful or as a solution, thank you**
Inside Administration > System > Admin Access > Authentication you should change the password based method:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-21-2018 04:10 AM
Angel gave a good start, but no need to create new admin groups.
First of all, add the three groups from AD.
For "full" ISE admin web access, after selecting AD as the ID source, go to "Super Admin" group, check the option "External" and put "Group1" as the External Group.
For RO ISE admin web access, go to "Read Only Admin", check the option "External" and put "Group2" as the External Group.
For Sponsor access, go to the Sponsor Groups, select the desired access, and pick members from the list of available groups.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide