- Cisco Community
- Technology and Support
- Security
- Network Security
- Who Me Too'd this topic
Who Me Too'd this topic
Possible CLDAP DDoS - But how is traffic coming from outside to inside with no open ports or NAT to pubic IP?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-24-2020 01:46 PM
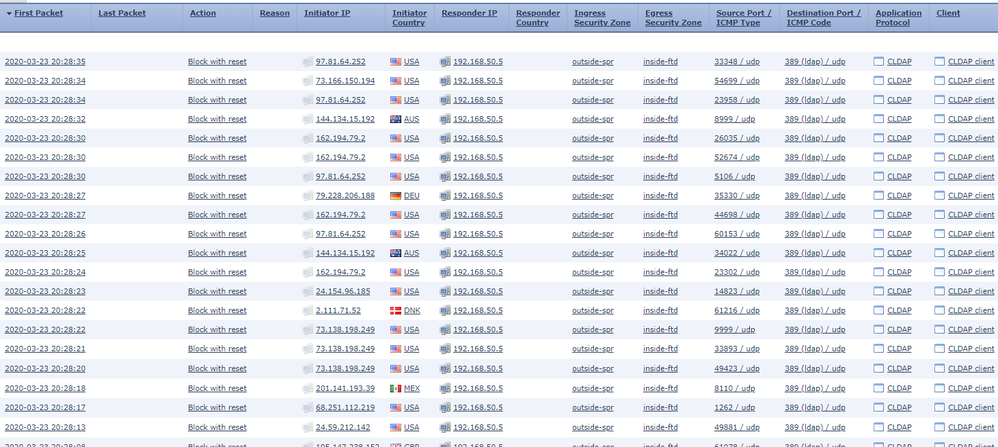
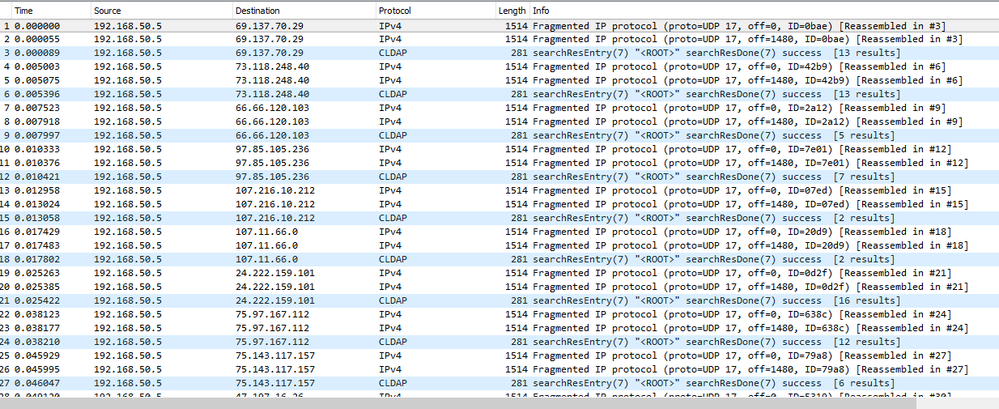
I noticed numerous amount of CLDAP traffic to one of my DC starting 3/17/20. The device is a Firepower 1010 running FTD 6.5.0.4. The FTD has no open ports and only two NAT rules. One rule for a site to site VPN and the other rule for devices from the inside to the outside. From vFMC, I can see the connections attempt from the outside source (Initiator) hitting my internal DC at 192.168.50.5 (Responder) with my Firepower rule to block udp/389, see Figure 1. Figure 2 is Wireshark capture prior to the block rule which seems to indicate the DC is repsonding to the CLDAP queries.
How is this network connection possible if there are no open ports on the FTD and no NAT to public IP? Am I reading this correctly?
Figure 1: Outside source to inside DC
Figure 2: Wireshark prior to blocking port 389