- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- Re: RV325 - Port forwarded but still closed
RV325 - Port forwarded but still closed
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
04-17-2018 04:43 PM - 편집 03-21-2019 11:08 AM
We have a RV325 (192.168.63.1) router behind our TP-Link router (192.168.0.1), in a pretty simple setup.
RV325 is also the DHCP server. Everything works great except that no device in 192.168.63.0/24 is accessible from outside (Internet). We forwarded all ports that we needed from TP-LINK to RV325, but looks like RV325 is not forwarding any ports to other IPs (192.168.63.2 for example)
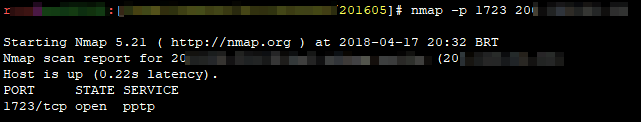
For this example, we did a PAT the TCP port 3000 to 192.168.63.2 81 and ran a nmap scan from an external machine:
Nmap scan report for XXXXXXX (XXXXXXXXX) Host is up (0.22s latency). PORT STATE SERVICE 3000/tcp closed ppp
TP-Link is certainly not the problem since if we enable PPTP in RV325, it will show the 1723/tcp open
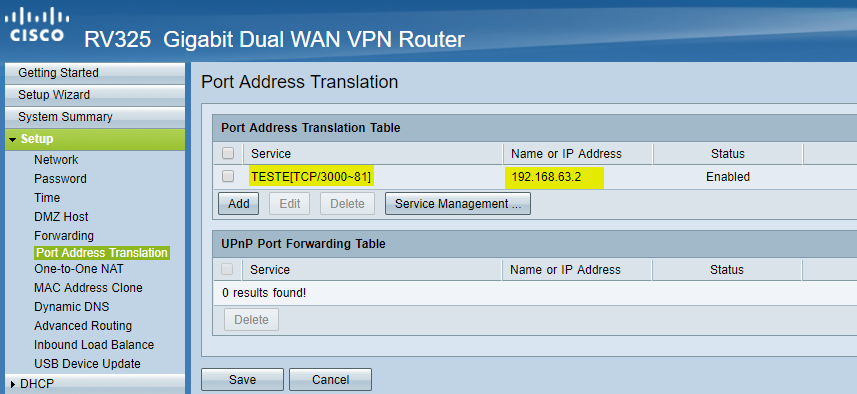
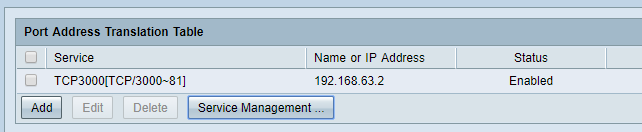
Here is our PAT settings:
We tried to set firewall permissive access rules or even disable the firewall but to no avail.
Running RV325 on latest firmware, can ping 192.168.63.2 just fine. We just did a factory reset.
Can anyone shed a light?
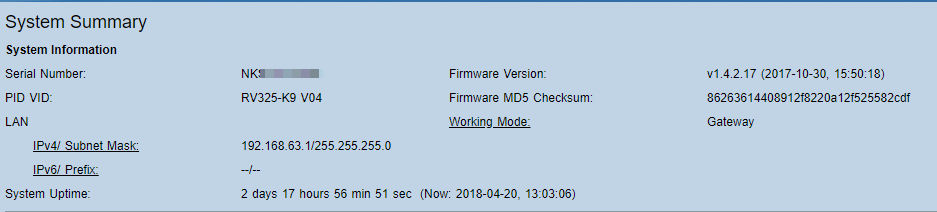
| Firmware Version: | v1.4.2.17 (2017-10-30, 15:50:18) | |
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
날짜: 04-20-2018 04:51 AM
I own a RV220W which doesn't have the Port Address Translation. I use the Forwarding menu to redirects ports to inside IPs.
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
날짜: 04-20-2018 05:03 AM
In RV325, Port Forwarding must be used if you forward the same external and internal port numbers. In order to forward external 3000 to internal 81, you need to use PAT.
Unfortunately, I tried both Port Forwarding and Port Address Translation, none of them work. I really think my unit is faulty but I can't RMA it yet because we have a site-to-site VPN online. I'll try to downgrade my Firmware. If it doesn't works I'll simply buy other VPN router. And will not be a Cisco because Cisco Small Business support is non-existent.
Thanks for the reply anyway.
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
날짜: 04-20-2018 06:14 AM
This is how I would do it.
In Port Address Translation -> Service Management I would enter
Service name: TCP3000
Protocol: TCP
External Port: 3000
Internal Port: 81
Then I would go to Forwarding and enter
Service: TCP3000
IP Address: 192.168.63.2
Status: enabled
Can you try that?
PAT AFAIK is used to reserve a port range for a specific internal IP when it goes out the WAN interface. It doesn't open any port.
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
날짜: 04-20-2018 06:39 AM
Hello,
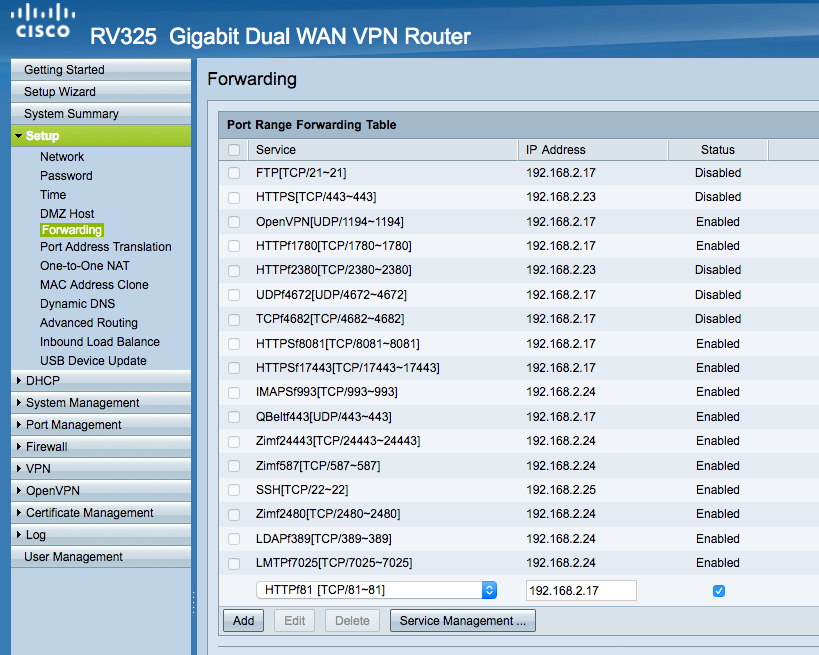
That didn't work since PAT's Service Management is separated from Port Forwarding Service Management.
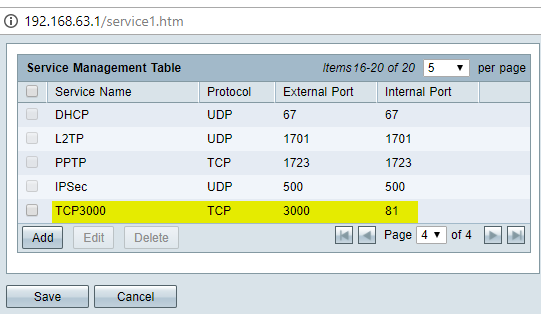
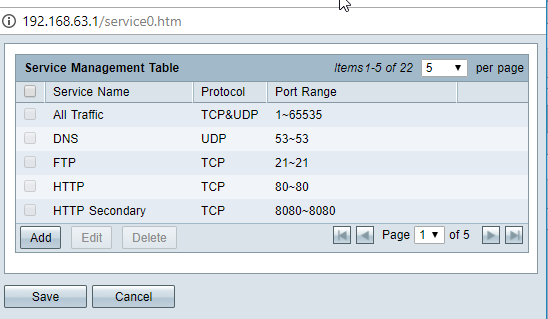
Here is the Service Management for PAT:
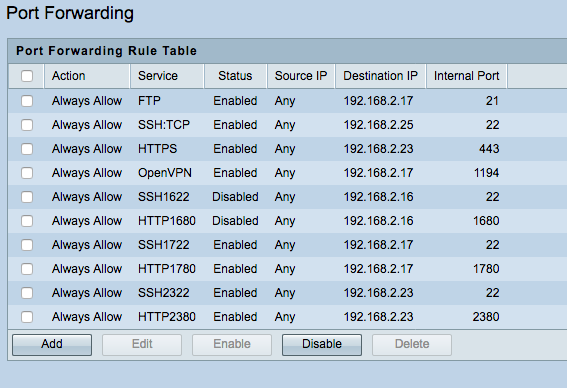
And here is the Service Management for Port Forwarding. In this window, you can't forward port 3000 to 81 only 3000 to 3000:
I event tried to delete PAT rule and forward ALL inbound traffic (ports 1~65535) to 192.168.63.2. In this case, we would use external port 81, but still shows as "closed".
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
04-20-2018 06:55 AM - 편집 04-20-2018 07:18 AM
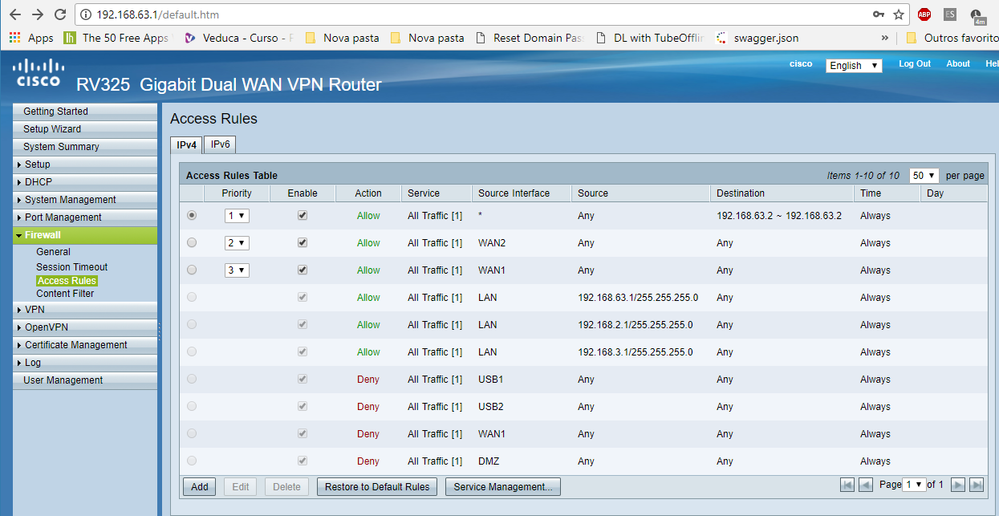
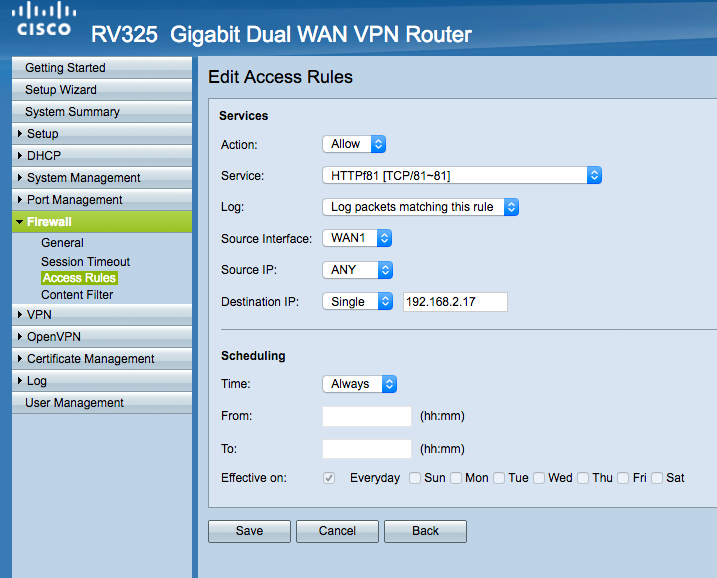
Do you have an entry in Firewall -> Access Rules like
Enable: yes
Action: Allow
Service: TCP3000
Source Interface: WAN1
Source: Any
Destination: 192.168.63.2
?
I believe that there is only one Service Table but two views into this table. One for the Forwarding menu and one for the PAT menu. So my understanding right now is that you use Firewall -> Access Rules to open ports and Forwarding or PAT to tell the router what to do with the packets.
Does it make sense ?
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
날짜: 04-20-2018 07:33 AM
Yes, I tried to set the firewall to the most permissive mode ever (allowing any traffic) or disable the firewall.
In my KIWI SNMP log I see the RV325 ALLOWing traffic but the port remais closed. So looks like something "inside" RV325 is still blocking or not forwarding the traffic correctly.
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
날짜: 04-20-2018 08:57 AM
@randrade86 wrote:
In my KIWI SNMP log I see the RV325 ALLOWing traffic but the port remais closed. So looks like something "inside" RV325 is still blocking or not forwarding the traffic correctly.
Or it could be the firewall on your server. You could capture packets on it via Wireshark and see.
I just ordered a RV325 online. Should be here in max 2 weeks. I'll have a better understanding then.
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
날짜: 04-20-2018 09:05 AM
We disabled 192.168.63.2 firewall entirely.
When we had only the TP-LINK router, it worked flawlessly. Due to business reasons, we needed to add a VPN Router with Site-to-Site capability hence we bought a RV325. VPN Site-to-Site is working great so far but the port forwarding problem is really hurting us because we need our customer to access us from outside.
I hope you have a better experience than I did. Here is our hardware / firmware versions.
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
05-02-2018 10:12 AM - 편집 05-02-2018 10:14 AM
Hi.
I got my rv325 yesterday. I replicated my rv220w config on it and everything works perfectly.
Here is what I did to replicate my firewall rules.
I will use two cases.
1) I want to open port https on 17443 and redirect it to 192.168.2.17 https 17443 (straight Forwarding)
2) I want to open port ssh on 1722 and redirect it to 192.168.2.17 ssh 22. (Port Address Translation)
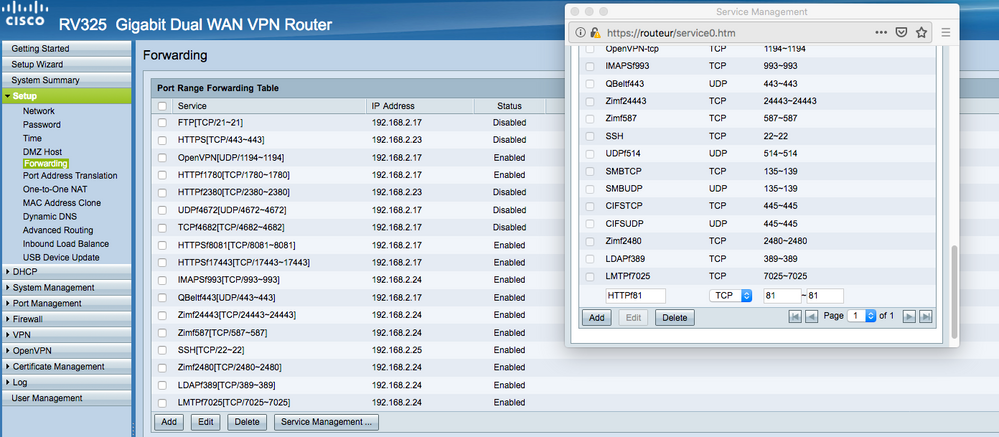
For case #1, I created a new service HTTPSf17443 and added a firewall rule then added a forwarding rule.
Firewall -> Access Rules -> Service Management… -> Add
HTTPSf17443 / TCP / 17443-17443
Firewall -> Access Rules -> Add
Allow HTTPSf17443 from WAN1 source ANY destination 192.168.2.17
Setup -> Forwarding -> Add
HTTPSf17443 / 192.168.2.17 / Enabled
For case #2, I created a new service SSHf1722 and added a firewall rule then added a new Port Address Translation service SSHp1722 and added a Port Address Translation entry
Firewall -> Access Rules -> Service Management… -> Add
SSHf1722 / TCP / 1722-1722
Firewall -> Access Rules -> Add
allow SSHf1722 from WAN1 source ANY destination 192.168.2.17
Setup -> Port Address Translation -> Service Management… -> Add
SSHp1722 / TCP / 1722 / 22
Setup -> Port Address Translation -> Add
SSHp1722 / 192.168.2.17 / Enabled
That's it.
I use _protocole_ f _wan_port_ for forwarding services and firewall rules and _protocole_ p _wan_port_ for Port Address Translation services.
Hope it helps.
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
날짜: 05-03-2018 05:51 AM
Thanks for your reply.
That's exactly what I have tried since the beginning. I even tried to factory reset my router and the problem persists.
Unfortunately, looks like my unit is faulty.
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
날짜: 06-14-2019 06:50 AM
Sorry to hear. Did you try to contact Cisco Small Business Service?
Devices have lifetime warranty if the hardware is faulty.
https://www.cisco.com/c/en/us/support/web/tsd-cisco-small-business-support-center-contacts.html
Cheers
Jo
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
날짜: 06-13-2019 07:34 PM
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
날짜: 06-13-2019 11:52 PM
Hi.
Does it work if you connect your server directly to your service provider? My service provider blocks tcp/80 and tcp/25 maybe yours is blocking tcp/81.
Since you are opening tcp/81 on the router and your server, you should use port forwarding + firewall acl.
This works for me as you can see from the firewall log:
<1>1 2019-06-14T02:44:18.828946-04:00 ALLOW TCP - - - TCP 24.114.108.206:31802 -> 173.177.3.66:81 on eth1
<1>1 2019-06-14T02:44:18.831877-04:00 ALLOW TCP - - - TCP 24.114.108.206:31802 -> 192.168.2.17:81 on eth1
- New로 표시하기
- 북마크
- 구독
- 소거
- RSS 피드 구독
- 고유주소(Permalink)
- 인쇄
- 부적절한 컨텐트 신고
날짜: 12-02-2019 05:14 PM
Had the same problem on my Rv325, had a cisco engineer confirm my setup was correct & RMA'd the product; upgraded to a rv345 still the same problem; found this on the rv345 thread: https://community.cisco.com/t5/small-business-routers/rv345-port-forwarding-not-working-when-inter-vlan-routing/td-p/3094792
Don't forget to check the settings of your fibre/dsl modem as well.. that's what it turned out to be fore me.
새로운 아이디어를 발견하고 저장하세요. 전문가 답변, 단계별 가이드, 최근 주제 등 다양한 내용을 확인해 보세요.
처음이신가요? 아래 팁들을 확인해 보세요. 시스코 커뮤니티 사용하기 새 멤버 가이드