- Cisco Community
- Technology and Support
- Small Business Support Community
- Routers - Small Business
- RV340 i can't change default certificate
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
RV340 i can't change default certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-10-2018 08:17 AM - edited 03-21-2019 11:08 AM
How do I replace the default certificate? I didn't found a way so far.
- Labels:
-
Small Business Routers
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-19-2018 04:24 AM
Hi,
Please follow the below steps to generate certicate
Step 1 Click Generate CSR/Certificate.
Step 2 Select the type of certificate to generate from the drop-down list.
Step 3 Enter the following information:
Certificate Name Enter a name for certificate. Certificate name should not contain spaces or special
characters.
Subject Alternative Name Enter a name and select one of the following: IP Address, FQDN, or Email.
Country Name Select a country from the drop-down list.
State or Province Name Enter a State or Province.
Locality Name Enter a locality name.
Organization Name Enter the name of the organization.
Organization Unit Name Enter the name of the organization unit.
Common Name Enter a common name.
Email Address Enter the email address.
Key Encryption Length Select the Key Encryption Length from the drop-down menu. It should be 512, or 2048.
Valid Duration Enter the number of days (Range 1-10950, Default: 360).
Step 4 Click Generate.
Regards,
K**bleep**ij Tiwari
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-20-2018 12:27 AM
What you have described is how to create a new self-signed certificate. The problem is that the system does not allow to establish the new certificate as the main one.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2018 05:48 PM
@Cimmerio wrote:
What you have described is how to create a new self-signed certificate. The problem is that the system does not allow to establish the new certificate as the main one.
If you mean you are trying to replace the HTTPS certificate of the web config interface, then you can’t, as far as i know.
After you generate a CSR and import back the corresponding cert, it becomes an option you can select it for use in a site-to-site or client-to-site or SSL VPN (NOT an L2TP VPN, unfortunately). There is no way to change the built in web server’s certificate.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-08-2019 01:08 PM
So if I have a license for Security services (Anti Threat Services: IPS, AppID, Dynamic Web Filter, Gateway Anti Virus) the chrome user will timeout on the redirection page of the router webServer? That makes my licence almost useless since it generate calls from users that will timeout on a blocked site...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2019 06:39 AM
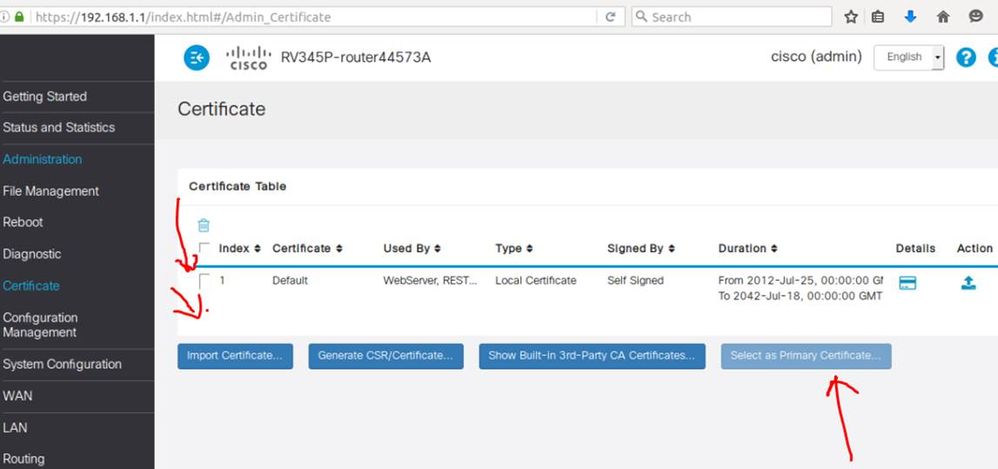
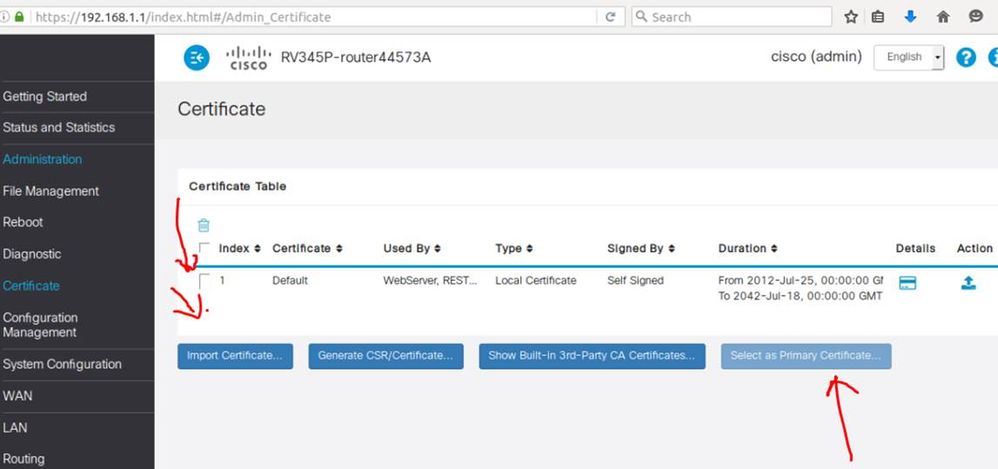
Hi, you can import your own and set as primary.
Thx
Jo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2019 06:41 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-11-2019 10:22 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2019 02:40 AM
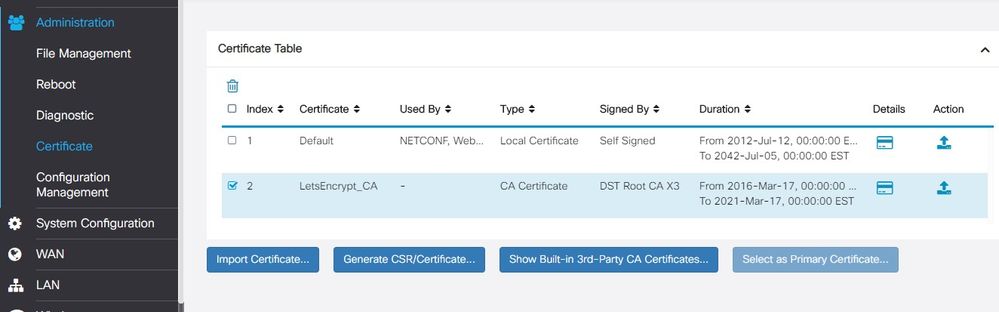
Hi I am not a great expert on certificates , so please excuse my questions. It seems this might be an intermediate certificate from LetsEncrypt. Did you get a signed server certificate from LetsEncrypt ( type local ) ?.
You need to generate a certificate signing request form the RV340 and have it signed by LetsEncrypt.
This and the intermediate need to be installed on the router.
Jo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2019 04:23 AM
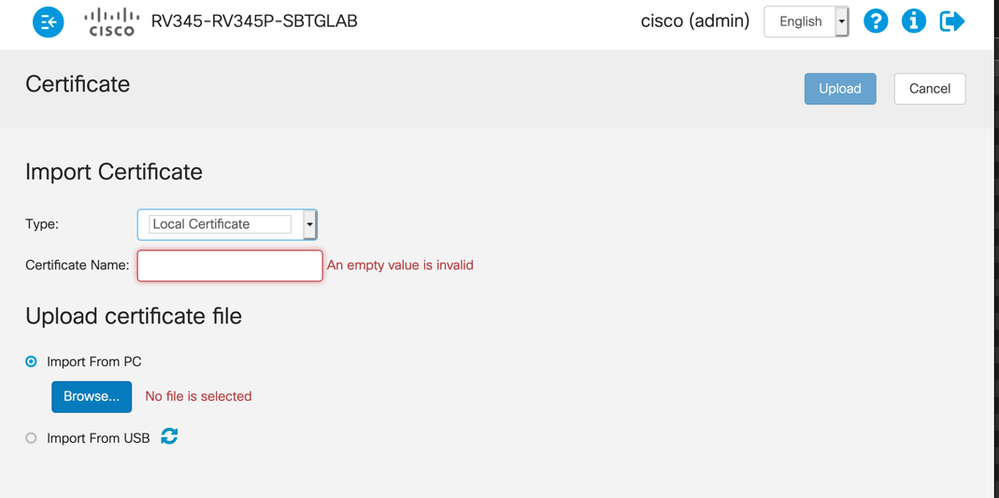
Hi, please try to import it as a local certificate type:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-12-2019 04:19 PM
I finally find a way to import the wilcard domain certificate I got by importing a PKCS#12 encoded file that I generate with a openssl command:
openssl> pkcs12 -export -out mydomain.com.pfx -in cert.pem -inkey privkey.pem -certfile chain.pem -name "mydomain.com"
The import generate both a local cert and a CA cert
After that I've been able to set the freshly created local certificate as default
After a router reboot, everything was working...well almost.
The redirection page redirect users to the IP of the router (in my case, https://192.168.1.1/blocked.php?t=0&c=11&url=http://blockedsite.com/)
Of course, my certificate is issued to the FQDN of my hosts so I get a warning in chrome. What will resolve all my problem would be that te router redirection use the FQDN...something like :https://rv340w.mydomain.com/blocked.php?t=0&c=11&url=http://blockedsite.com/
Is ther a way to do that?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-13-2019 04:32 AM
I've seen this exact kind of issue on a ZyXel device, because the config page was trying to redirect to HTTPS, and was using the IP address instead of the domain name that the user originally used to access the page. The result was broken HTTPS and a warning message like this shown.
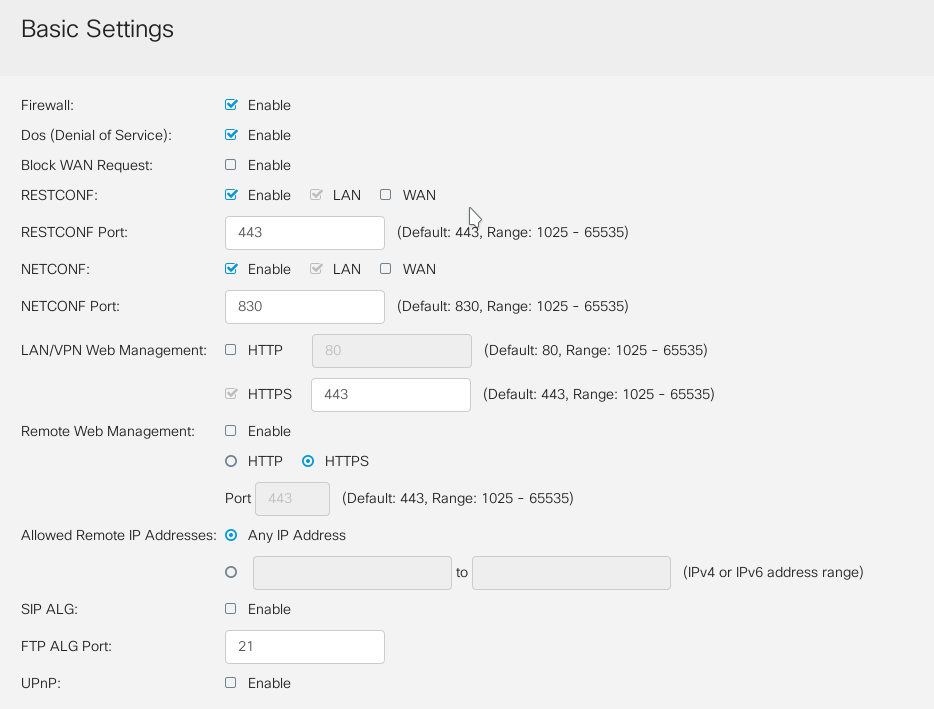
On that Zyxel device, I could disable HTTPS for the config page and use plain HTTP, which fixed this. Unfortunately, the Cisco device does not appear to allow this. The checkbox is greyed out for HTTPS (located at Firewall -> Basic Settings -> HTTPS), meaning you cannot disable it.
The only other option would be to possibly include the IP address of the Cisco device into the certificate, using an IP:<ipaddr> option in the X509v.3 extension header. That way the HTTPS redirect should be valid.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
06-17-2019 05:36 AM
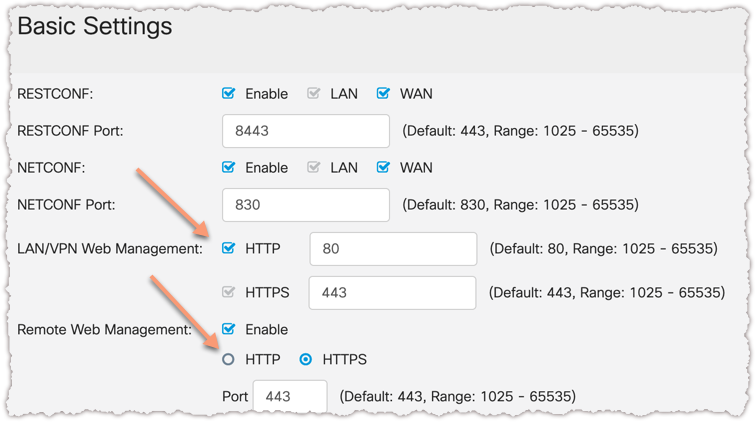
In the latest firmware ( 1.0.03.15) you can toggle between HTTP and HTTPS for remote access. Of course strongly discouraged since the http will be not encrypted. To "ungrey" the toggle you might need to checkmark "Firewall" =ON in the GUI first. After you set to HTTP you can unckeck Firewall.
/Jo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-08-2019 09:28 PM - edited 07-08-2019 09:29 PM
Jo - where is the option you are talking about with regards to "Firewall =ON" ? If you mean the checkbox on this page next to the word "Firewall" and labeled "Enable", all this does is grey out all of the options on the page. Selecting/Deselecting it still does not allow you to deselect the "HTTPS" option. It remains permanently selected, and greyed out.
Shown below is my RV340W's page running 1.0.03.15:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2019 05:55 AM
Yes.
I meant Firewall = Enable checked.
Then the settings are not greyed out.
For Remote access to management GUI over WAN interface you can disable/enable and select the protocol http or https.
For local access to management GUI you cannot deselect https, you are right.
As the GUI is the only means to manage the device we need to minimize the risk you loose connectivity.
You can enable http and access the GUI with:
http://<ip-address>:80
e.g.
Cheers
Jo
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide