- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: CISCO ISR 4321 SSL VPN (WebVPN) issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2022 01:25 PM - edited 10-28-2022 04:50 AM
Hi Experts,
I am trying to configure
anyconnect
on Cisco ISR 4321 but somehow the command is not being executed and I am unable to enable
WebVPN
command .
image with ISR_4321_Security License enabled
^
It seems the command is not known?
Appreciate if there is any workaround for this to work
Regards,
Avei
Solved! Go to Solution.
- Labels:
-
ISR 4000 Series
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2022 01:46 PM
Hello,
as far as I recall, clientless SSL VPN (webvpn) is not supported at all on the platform. The below are:
FlexVPN, Easy VPN remote server, Enhanced Easy VPN, Dynamic Multipoint VPN (DMVPN), Group Encrypted Transport VPN (GET VPN), V3PN, MPLS VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2022
01:36 PM
- last edited on
10-28-2022
02:33 AM
by
Translator
![]()
The first step when
AnyConnect
is configured on an IOS Router headend is to confirm that the license has been correctly installed (if applicable) and enabled. Refer to the licensing information in the previous section for the licensing specifics on different versions. It depends on the version of code and platform whether the show license lists an SSL_VPN or securityk9 license. Regardless of the version and license, the EULA will need to be accepted and the license will show as Active.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2022 01:46 PM
Hello,
as far as I recall, clientless SSL VPN (webvpn) is not supported at all on the platform. The below are:
FlexVPN, Easy VPN remote server, Enhanced Easy VPN, Dynamic Multipoint VPN (DMVPN), Group Encrypted Transport VPN (GET VPN), V3PN, MPLS VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-26-2022 02:33 PM - edited 10-27-2022 03:05 AM
Thanks MHM Cisco World and Georg Pauwen
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-27-2022 05:29 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2022 08:06 PM
Thanks so much MHM Cisco World .
I am getting the below error . Do you notice anything wrong in the debug
##########################################################
VID Next payload: NOTIFY, reserved: 0x0, length: 29
NOTIFY(NAT_DETECTION_SOURCE_IP) Next payload: NOTIFY, reserved: 0x0, length: 28
Security protocol id: IKE, spi size: 0, type: NAT_DETECTION_SOURCE_IP
NOTIFY(NAT_DETECTION_DESTINATION_IP) Next payload: VID, reserved: 0x0, length: 28
Security protocol id: IKE, spi size: 0, type: NAT_DETECTION_DESTINATION_IP
VID Next payload: CFG, reserved: 0x0, length: 20
CFG Next payload: NOTIFY, reserved: 0x0, length: 14
cfg type: CFG_REQUEST, reserved: 0x0, reserved: 0x0
Oct 30 03:03:45.162: attrib type: Unknown - 28728, length: 2
NOTIFY(REDIRECT_SUPPORTED) Next payload: NONE, reserved: 0x0, length: 8
Security protocol id: Unknown - 0, spi size: 0, type: REDIRECT_SUPPORTED
Oct 30 03:03:45.166: IKEv2-ERROR:(SESSION ID = 22,SA ID = 4):Received Policies: : Failed to find a matching policyProposal 1: AES-GCM-256 AES-GCM-192 AES-GCM-128 SHA384 SHA512 SHA256 SHA1 None DH_GROUP_256_ECP/Group 19 DH_GROUP_384_ECP/Group 20 DH_GROUP_521_ECP/Group 21 DH_GROUP_3072_MODP/Group 15 DH_GROUP_4096_MODP/Group 16
Oct 30 03:03:45.166:
Oct 30 03:03:45.166: Proposal 2: AES-CBC-256 AES-CBC-192 AES-CBC-128 SHA384 SHA512 SHA256 SHA1 SHA256 SHA384 SHA96 SHA512 DH_GROUP_256_ECP/Group 19 D H_GROUP_384_ECP/Group 20 DH_GROUP_521_ECP/Group 21 DH_GROUP_3072_MODP/Group 15 DH_GROUP_4096_MODP/Group 16
Oct 30 03:03:45.167:
Oct 30 03:03:45.167:
Oct 30 03:03:45.167: IKEv2-ERROR:(SESSION ID = 22,SA ID = 4):Expected Policies: : Failed to find a matching policyProposal 1: AES-CBC-256 SHA512 SHA5 12 DH_GROUP_2048_MODP/Group 14
Oct 30 03:03:45.167:
Oct 30 03:03:45.167:
Oct 30 03:03:45.167: IKEv2-ERROR:(SESSION ID = 22,SA ID = 4):: Failed to find a matching policy
Oct 30 03:03:45.167: IKEv2-PAK:(SESSION ID = 22,SA ID = 4):Next payload: NOTIFY, version: 2.0 Exchange type: IKE_SA_INIT, flags: RESPONDER MSG-RESPONS E Message id: 0, length: 36
Payload contents:
NOTIFY(NO_PROPOSAL_CHOSEN) Next payload: NONE, reserved: 0x0, length: 8
Security protocol id: Unknown - 0, spi size: 0, type: NO_PROPOSAL_CHOSEN
Oct 30 03:03:45.168: IKEv2-ERROR:(SESSION ID = 22,SA ID = 4):Initial exchange failed: Initial exchange failed
Oct 30 03:04:01.661: %SEC-6-IPACCESSLOGP: list DIA denied udp 10.5.50.105(60215) -> 255.255.255.255(5246), 6 packets
Oct 30 03:04:01.661: %SEC-6-IPACCESSLOGP: list DIA denied udp 10.5.50.101(54739) -> 255.255.255.255(5246), 6 packets
Oct 30 03:04:01.661: %SEC-6-IPACCESSLOGP: list DIA denied udp 10.5.50.104(54715) -> 255.255.255.255(5246), 6 packets
Oct 30 03:04:19.801: IKEv2-PAK:(SESSION ID = 19,SA ID = 3):Next payload: ENCR, version: 2.0 Exchange type: INFORMATIONAL, flags: RESPONDER Message id: 3, length: 96
Payload contents:
ENCR Next payload: NONE, reserved: 0x0, length: 68
Oct 30 03:04:19.814: IKEv2-PAK:(SESSION ID = 19,SA ID = 3):Next payload: ENCR, version: 2.0 Exchange type: INFORMATIONAL, flags: INITIATOR MSG-RESPONSE Message id: 3, length: 96
Payload contents:
#################################################
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2022 08:51 PM
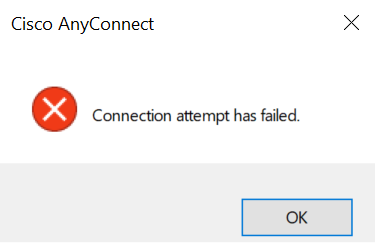
Along side with debug error I am getting the above error from Anyconnect client VPN
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2022 08:57 PM
If I am trying to connect via IP address I am getting the below error
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-29-2022 09:20 PM - edited 10-29-2022 09:21 PM
crypto ikev2 authorization policy IKEV2_AUTHORIZATION_POLICY
pool VPN_POOL
dns 192.168.99.1
def-domain nwl.lab
route set interface
route set remote ipv4 192.168.99.1 255.255.255.255
!
crypto ikev2 proposal IKEV2_PROPOSAL
encryption aes-cbc-256
integrity sha256
group 15
!
crypto ikev2 policy IKEV_POLICY
! Policy Incomplete(MUST have atleast one complete proposal attached)
match fvrf any
!
!
crypto ikev2 profile IKEV2_PROFILE
match identity remote key-id *$AnyConnectClient$*
authentication local rsa-sig
authentication remote anyconnect-eap aggregate
pki trustpoint R1-Client
aaa authentication anyconnect-eap AAA_AUTHENTICATION_LOGIN
aaa authorization group anyconnect-eap list AAA_AUTHORIZATION_NETWORK IKEV2_AUTHORIZATION_POLICY
virtual-template 1
!
!
!
!
!
!
crypto ipsec transform-set TRANSFORM_SET esp-aes 256 esp-sha256-hmac
mode tunnel
!
crypto ipsec profile IKEV2_PROFILE
set transform-set TRANSFORM_SET
set ikev2-profile IKEV2_PROFILE
!
!
!
!
!
!
!
interface Loopback99
description local address
ip address 192.168.99.1 255.255.255.0
!
interface Embedded-Service-Engine0/0
no ip address
shutdown
!
interface GigabitEthernet0/0
ip address 192.168.0.254 255.255.255.0
duplex auto
speed auto
!
interface GigabitEthernet0/1
no ip address
shutdown
duplex auto
speed auto
!
interface Virtual-Template1 type tunnel
ip unnumbered Loopback99
ip mtu 1400
tunnel source GigabitEthernet0/0
tunnel mode ipsec ipv4
tunnel protection ipsec profile IKEV2_PROFILE
!
ip local pool VPN_POOL 192.168.18.5 192.168.18.10
ip forward-protocol nd
!
ip http server
no ip http secure-server- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2022 12:13 AM
Hello,
there is at least one error in your FlexVPN configuration. Add the line marked in bold:
crypto ikev2 policy IKEV_POLICY
! Policy Incomplete(MUST have atleast one complete proposal attached)
--> proposal IKEV2_PROPOSAL
match fvrf any
Also, which AnyConnect client version do you have, and on which clients (e.g. Windows 11) are those clients installed ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
10-30-2022 03:48 AM - edited 10-30-2022 03:49 AM
Thanks Georg,
Sorry I didn't add it in the forum but I have that fixed before the post . I am using Cisco ISR 4321 and on windows 10 with the latest Anyconnect version 4.10
I can only think it as the device itself not supporting ?
Thanks
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide