- Cisco Community
- Technology and Support
- Networking
- Routing
- GRE over IPsec Issue
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
GRE over IPsec Issue
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 07:54 AM
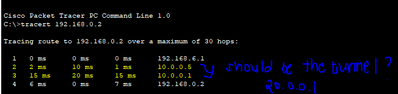
I'm in a tough spot and currently having an issue with configuring a GRE over IPsec in my personal project. I think the configurations are right based on the verification commands that I used which are: show crypto isakmp sa and show crypto ipsec sa. However, when I try to ping from a network to another, it doesn't use the tunnel that I've established. Example:
Here is the configuration:
*DEPT-R1 to DEPT-R2
en
conf t
int tunnel 1
ip address 20.0.0.1 255.255.255.252
tunnel source s0/1/0
tunnel destination 10.0.0.6
end
crypto isakmp policy 1
encryption aes 256
hash sha
authentication pre-share
group 2
lifetime 3600
ext
crypto isakmp key privkey address 10.0.0.6
crypto ipsec transform-set GRE-VPN esp-aes 256 esp-sha-hmac
ip access-list extended GRE-VPN-ACL
permit gre host 10.0.0.1 host 10.0.0.6
exit
crypto map GRE-CMAP 10 ipsec-isakmp
match address GRE-VPN-ACL
set transform-set GRE-VPN
set peer 10.0.0.6
exit
int s0/1/0
crypto map GRE-CMAP
// CONFIG OSPF TO ADVERTISE TUNNEL INT
router ospf 10
network 20.0.0.0 0.0.0.3 area 0
*DEPT-R2 to DEPT-R1
en
conf t
int tunnel 1
ip address 20.0.0.2 255.255.255.252
tunnel source s0/1/1
tunnel destination 10.0.0.1
tunnel mode gre ip
end
crypto isakmp policy 1
encryption aes 256
hash sha
authentication pre-share
group 2
lifetime 3600
ex
crypto isakmp key privkey address 10.0.0.1
crypto ipsec transform-set GRE-VPN esp-aes 256 esp-sha-hmac
ip access-list extended GRE-VPN-ACL
permit gre host 10.0.0.6 host 10.0.0.1
exit
crypto map GRE-CMAP 10 ipsec-isakmp
match address GRE-VPN-ACL
set transform-set GRE-VPN
set peer 10.0.0.1
exit
int s0/1/1
crypto map GRE-CMAP
// CONFIG OSPF TO ADVERTISE TUNNEL INT
router ospf 10
network 20.0.0.0 0.0.0.3 area 0
Thanks,
M
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 08:03 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 08:10 AM
Much appreciated. Will try it again.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 08:50 AM - edited 03-27-2024 08:55 AM
GRE/IPSec tunnels using crypto maps is an old approach.
If you're using 4k ISRs, would expect the to support VTI IPSec tunnels, eliminates GRE overhead.
I also recall (???) GRE/IPSec tunnel later variants didn't need to use a crypto map.
Edit: just looked at @@MHM Cisco World reference, and it appears to show using GRE/IPSec without a crypto map.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 09:07 AM
I just found out that using crypto maps were outdated. My resource material, aka YouTube is not helping me right now, lol. Currently trying and learning it right now. Thank you for replying. ☺️
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
03-27-2024 10:28 AM
Good source of Cisco information is Cisco's main site. Especially look at documentation for your IOS release and TechNotes or WhitePapers explaining an aspect of Cisco technology.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide