- Cisco Community
- Technology and Support
- Networking
- Routing
- GRE tunnel flapping
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
GRE tunnel flapping
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2021 03:12 PM - edited 07-11-2021 03:45 PM
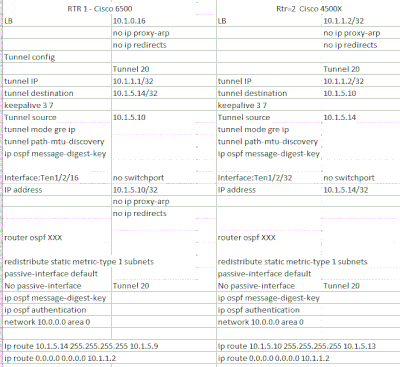
Trying to create a GRE tunnel between two routers that cross another network.
I have the following configs on the routers, I can ping across the tunnel, everything seems to work until I try adding ospf.
then I the following error: FULL to DOWN, Neighbor Down: Interface down or detached
- Labels:
-
Routing Protocols
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2021 04:23 PM
yes I'm seeing the error on both routers.
Sorry missed this and didn't look at the log while at work, will see if I can find anything interesting in it
I did " debug ip ospf hello and packet, I was seeing send and receive hello's on both routers.
I didn't see any error on the packets.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2021 07:10 AM
In my R1 log I’m getting:
I noticed on the original IP list R2 LB is incorrect should be 0.2/32
OSPF-5-ADJCHG NBR 0.2 Loading to Full, loading done
OSPF-5-ADJCHG NBR 0.2Full to Down, neighbor down: interface down or detached
C4K_Switchingengineman-4-vfeopinterrupt:standby:vfe op rrqenqcntexceed inerrupt
Router 1 is a pair of 4500X set up in VSS
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2021 08:29 AM
Hi Scott,
Can you try modifying the static routes for the tunnel destination on both RTR-1 and RTR-2 as follow and see if it makes a difference.
RTR-1:
ip route 10.1.5.14 255.255.255.255 Ten1/2/16 10.1.5.9
RTR-2:
ip route 10.1.5.10 255.255.255.255 Ten1/2/32 10.1.5.13
Regards,
Harold Ritter, CCIE #4168 (EI, SP)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2021 02:21 PM - edited 07-13-2021 04:35 AM
....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2021 04:05 PM
the 5.9 and 5.13 are direct connected encryption devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2021 05:01 PM - edited 07-13-2021 04:34 AM
....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2021 06:28 PM
Was there a link to the document?
Will I need to enable multicast routing?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2021 04:21 AM - edited 07-13-2021 04:34 AM
....
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2021 07:36 PM
Apart from including the tunnel interface IP address in the router ospf network statement, there is nothing special that needs to be configured to run ospf over the tunnel interfaces.
Regards,
Harold Ritter, CCIE #4168 (EI, SP)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-11-2021 10:01 PM - edited 07-11-2021 10:04 PM
Hello
Stop the redistribution of all your static routes to negate recursive routing and as stated the next hop ip addressing of your default static routes are the same which is incorrect
Please rate and mark as an accepted solution if you have found any of the information provided useful.
This then could assist others on these forums to find a valuable answer and broadens the community’s global network.
Kind Regards
Paul
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-12-2021 01:17 PM
Tried on router 1 still seeing the error, cant on router 2, it has a bunch of static routes.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2021 07:45 AM
Hello @scottshaw2 ,
you can use a route-map on R2 to avoid redistribution of the static route for the tunnel destination and you can then still redistribute all the other static routes.
ip prefix-list TUN-DEST permit 10.1.5.10/32
route-map STATIC-INTO-OSPF deny 10
match address prefix TUN-DEST
route-map STATIC-INTO-OSPF permit 20
router ospf 1
redistribute static subnets type 1 route-map STATIC-INTO-OSPF
Hope to help
Giuseppe
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2021 04:58 AM
Hi friend I make deep view and I think I found issue here,
this is IP and subnet you use as your original post.
IN R1 there must be two important prefix
S 10.1.5.14 255.255.255.255 10.1.5.9 <- that OK if the 10.1.5.9 is direct connect BUT
as you see 10.1.5.10/30 subnet there is 10.1.5.9 ip address this this subnet pool!!!!
also
this show ip route in R1,
if the R2 redistribute the route into OSPF and R1 learn this route from R2 via tunnel OSPF then there must two
S 10.1.5.14 255.255.255.255 via 10.1.5.9
O 10.1.5.8/30 via 10.1.1.2 tunnel "because the R2 have this static route toward R1 for tunnel destination"
But It have 10.1.5.12/30 which mean that R2 have S route toward 10.1.5.12 not toward 10.1.5.8, and for the tunnel how it UP because it use the default route not this wrong static route.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2021 06:03 AM
Not sure I'm following what you are saying.
R2 has a static 10.1.5.10 255.255.255.255 10.1.5.13
the .9 and .13 are direct connected crypto devices.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-13-2021 08:55 AM
I cant find the post, but someone mentioned adding a "tunnel key xx" to the tunnel configuration.
when I use the command I get a warning saying " feature not supported in hardware. packets will be software switched"
however using this command seams to be the solution, I'm going to assume its something unique to the 4500X, since I have tunnels configure the same way running between 6509's that don't have the "tunnel key xx".
thanks for everyone's thoughts and assistance.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide



