- Cisco Community
- Technology and Support
- Networking
- Routing
- Re: Remote Access IPSec VPN
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 12:02 AM
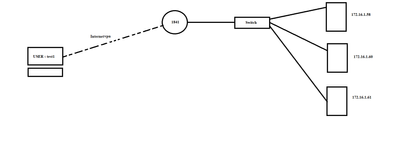
i have a vpn Remote access using Router Cisco 1841, all users can access the all internal servers.
My issues, is how to let some users(for example the user with the username " test1 " access only the server 172.16.1.58 and others access the others servers.
Help !
Solved! Go to Solution.
- Labels:
-
Routing Protocols
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 12:23 AM - edited 11-30-2020 12:24 AM
As always, there are many ways to achieve this. What the best solution is and how to implement it depends on what you already have configured. Sadly you don't tell us.
So here is a simple solution. You have probably something like this configured:
crypto isakmp client configuration group VPN key verysecurekey domain example.com pool VPN-POOL
You configure another VPN like the following:
ip access-list standard SPLIT-TUNNEL permit host 172.16.1.58 ! crypto isakmp client configuration group VPN-2 key anotherverysecurekey domain example.com pool VPN-POOL acl SPLIT-TUNNEL
If the one user is forced to use this new VPN, he only has access to the systems specified in the ACL SPLIT-TUNNEL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 12:23 AM - edited 11-30-2020 12:24 AM
As always, there are many ways to achieve this. What the best solution is and how to implement it depends on what you already have configured. Sadly you don't tell us.
So here is a simple solution. You have probably something like this configured:
crypto isakmp client configuration group VPN key verysecurekey domain example.com pool VPN-POOL
You configure another VPN like the following:
ip access-list standard SPLIT-TUNNEL permit host 172.16.1.58 ! crypto isakmp client configuration group VPN-2 key anotherverysecurekey domain example.com pool VPN-POOL acl SPLIT-TUNNEL
If the one user is forced to use this new VPN, he only has access to the systems specified in the ACL SPLIT-TUNNEL.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 01:43 AM
here is my configuration :
***********************************************************
crypto isakmp policy 1
encr 3des
authentication pre-share
group 2
***********************************************************
crypto isakmp client configuration group Remote
key Re**te$MPlmmre56.sd
pool SDM_POOL_1
acl 101
netmask 255.255.255.0
***********************************************************
crypto ipsec transform-set ENC esp-3des esp-sha-hmac
mode tunnel
***********************************************************
crypto dynamic-map SDM_DYNMAP_1 1
set transform-set ENC
reverse-route
***********************************************************
crypto map SDM_CMAP_1 client authentication list sdm_vpn_xauth_ml_1
crypto map SDM_CMAP_1 isakmp authorization list sdm_vpn_group_ml_1
crypto map SDM_CMAP_1 client configuration address respond
crypto map SDM_CMAP_1 65535 ipsec-isakmp dynamic SDM_DYNMAP_1
***********************************************************
route-map SDM_RMAP_1 permit 1
match ip address 100
***********************************************************
ip local pool SDM_POOL_1 10.10.0.70 10.10.0.80
ip forward-protocol nd
***********************************************************
access-list 100 remark SDM_ACL category=2
access-list 100 deny ip 10.10.0.0 0.0.0.255 host 10.10.0.70
access-list 100 deny ip 10.10.0.0 0.0.0.255 host 10.10.0.71
access-list 100 deny ip 10.10.0.0 0.0.0.255 host 10.10.0.72
access-list 100 deny ip 10.10.0.0 0.0.0.255 host 10.10.0.73
access-list 100 deny ip 10.10.0.0 0.0.0.255 host 10.10.0.74
access-list 100 deny ip 10.10.0.0 0.0.0.255 host 10.10.0.75
access-list 100 deny ip 10.10.0.0 0.0.0.255 host 10.10.0.76
access-list 100 deny ip 10.10.0.0 0.0.0.255 host 10.10.0.77
access-list 100 deny ip 10.10.0.0 0.0.0.255 host 10.10.0.78
access-list 100 deny ip 10.10.0.0 0.0.0.255 host 10.10.0.79
access-list 100 deny ip 10.10.0.0 0.0.0.255 host 10.10.0.80
access-list 100 permit ip 10.10.0.0 0.0.0.255 any
access-list 101 remark Vpn entries
access-list 101 remark SDM_ACL category=4
access-list 101 permit ip 10.10.0.0 0.0.0.255 any
***********************************************************
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 01:56 AM
If that is the real Pre-Shared-Key that you just posted in the config, then you should immediately change it.
With that config, it is just the new block of VPN-config:
ip access-list standard SPLIT-TUNNEL-172.16.1.58 permit host 172.16.1.58 ! crypto isakmp client configuration group Remote2 key anotherverysecurekey pool SDM_POOL_1 acl SPLIT-TUNNEL-172.16.1.58
netmask 255.255.255.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 02:30 AM
don't worry about Pre-Shared-Key, it isn't the real one, the configuration that i send you is the one that all users can access all servers and it works well, i added now another one to specified that one user access only the server 172.16.1.58 :
ip access-list standard SPLIT-TUNNEL permit host 172.16.1.58 ! crypto isakmp client configuration group VPN-2 key anotherverysecurekey domain example.com pool VPN acl SPLIT-TUNNEL
Unfortunately, i can connect to the vpn, but i can't access 172.16.1.58.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
11-30-2020 02:51 AM
1) Is the POOL the same as with the other users? If not, you likely have to also change your NAT-Exemption.
2) How are you testing to access the server? If you try to reach it by FQDN (like www.example.local) then you also have to add access to your internal DNS-servers.
3) When connected to the VPN, look at the clients routing-table and compare it to one of the regular clients. Do you route traffic to the server to the VPN-adapter?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-01-2020 07:46 AM
1 - i tried with same pool and different pool but nothing
2- i do ping to test my access to the server
3- same route-table
unfortunalety no access to my server !
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide