- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-07-2016 04:25 AM - edited 03-05-2019 07:37 AM
Hello all,
I am having issues being able to SSH or HTTPS on the outside interface, looking at the log when trying I am getting an error message.
"Inbound TCP connection Denied from xx.xx.xx.xx to xx.xx.xx.xx/22 flags SYN on interface outside
Config is below, could anyone point out my stupid mistake?
hostname ASA
enable password password
passwd password
names
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.xx.xx255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
pppoe client vpdn group BTI
ip address xx.xx.xx.xx 255.255.255.255 pppoe setroute
!
boot system disk0:/asa923-k8.bin
boot system disk0:/asa922-4-k8.bin
boot system disk0:/asa921-k8.bin
boot system disk0:/asa917-9-k8.bin
ftp mode passive
clock timezone GMT 0
object network obj_any
subnet 0.0.0.0 0.0.0.0
object network Inside-NAT
host 192.168.3.0
object network ServerIP
access-list incoming-outside extended permit icmp any any echo
access-list incoming-outside extended permit icmp any any echo-reply
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
icmp permit any inside
icmp permit any outside
asdm image disk0:/asdm-761.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
!
object network obj_any
nat (inside,outside) dynamic interface
object network Inside-NAT
nat (inside,outside) dynamic interface
access-group incoming-outside in interface outside
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 0:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication enable console LOCAL
http server enable
http 192.168.3.0 255.255.255.0 inside
no snmp-server location
no snmp-server contact
crypto ca trustpool policy
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 43200
telnet timeout 5
no ssh stricthostkeycheck
ssh 192.168.3.0 255.255.255.0 inside
ssh xx.xx.xx.xx 255.255.255.255 outside
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
vpdn group BTI request dialout pppoe
vpdn group BTI localname broadband@bt.com
vpdn group BTI ppp authentication chap
vpdn username broadband@bt.com password password store-local
dhcpd auto_config outside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username User password password privilege 15
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
Cryptochecksum:66689f27bc0a96bb93219f6e73e07538
Thanks!
Solved! Go to Solution.
- Labels:
-
Other Routing
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-16-2016 03:41 AM
Hi Rick,
Thanks for coming back to me. I have cleared some errors up in the config which is posted below.
The ASA below does have a static address and it is the ASA with the static peer that I am doing this on and I am following the guide to the letter and as soon as I apply the first Ipsec rule it stops internet access and me being able to SSH.
ASDM Configuration
Central-ASA (Static Peer)
On an ASA with a Static IP address, set up the VPN in such a way that it accepts dynamic connections from an unknown peer while it still authenticates the peer using an IKEv1 Pre-shared Key:
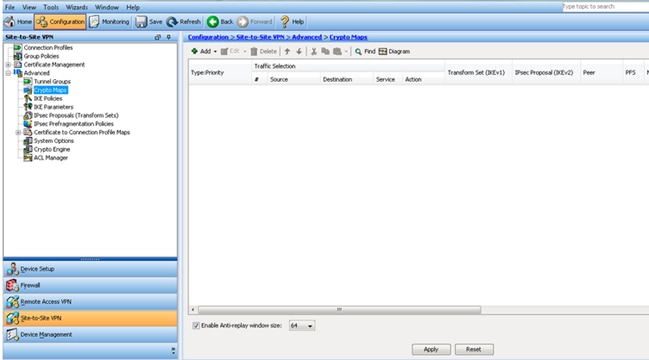
- Choose Configuration > Site-to-Site VPN > Advanced > Crypto Maps. The window displays the list of crypto map entries which are already in place (if there is any). Since ASA does not know what the Peer IP address is, in order for ASA to accept the connection configure Dynamic-map with matching transform-set (IPsec Proposal). Click Add.
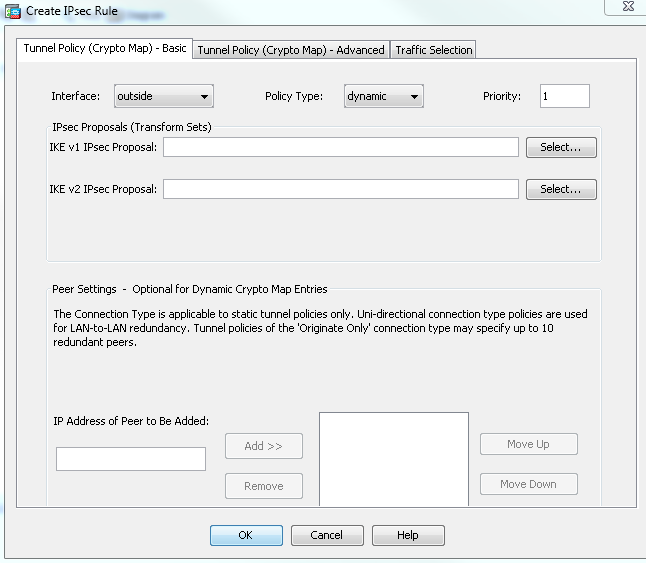
- In the Create IPsec Rule window, from the Tunnel Policy (Crypto Map) - Basic tab, choose outside from the Interface drop-down list and dynamic from the Policy Type drop-down list. In the Priority field, assign the priority for this entry in case there are multiple entries under Dynamic-Map. Next, click Select next to the IKE v1 IPsec Proposal field in order to select the IPsec proposal.
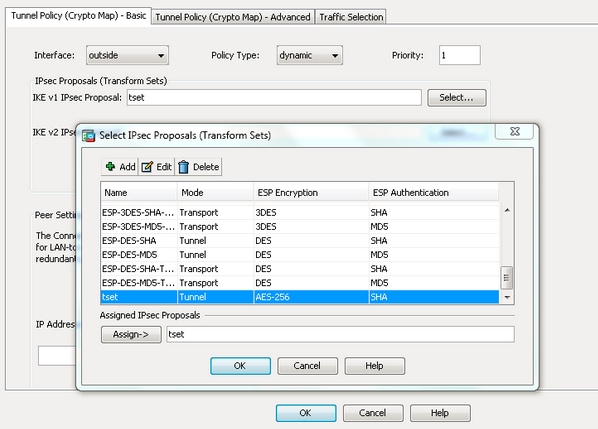
- When the Select IPsec Proposals (Transform Sets) dialog box opens, choose among the current IPsec proposals or click Add in order to create a new one and use the same. Click OK when you are done.
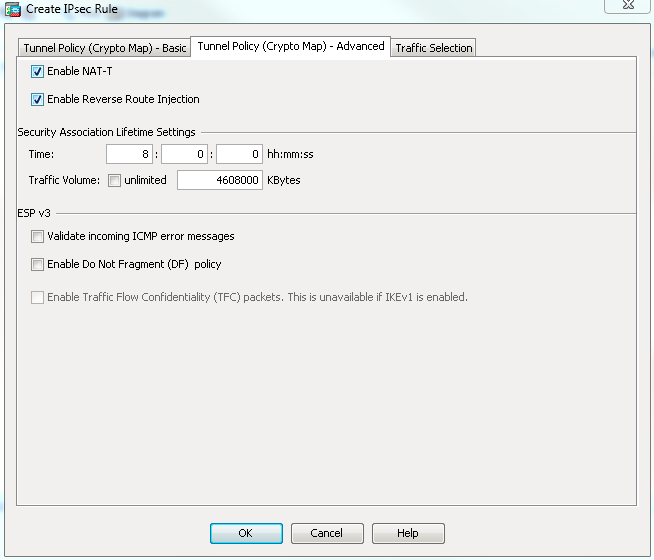
- From the Tunnel Policy (Crypto Map)-Advanced tab, check the Enable NAT-T check box (required if either peer is behind a NAT device) and the Enable Reverse Route Injection check box. When the VPN tunnel comes up for the dynamic peer, ASA installs a dynamic route for the negotiated remote VPN network that points to the VPN interface.
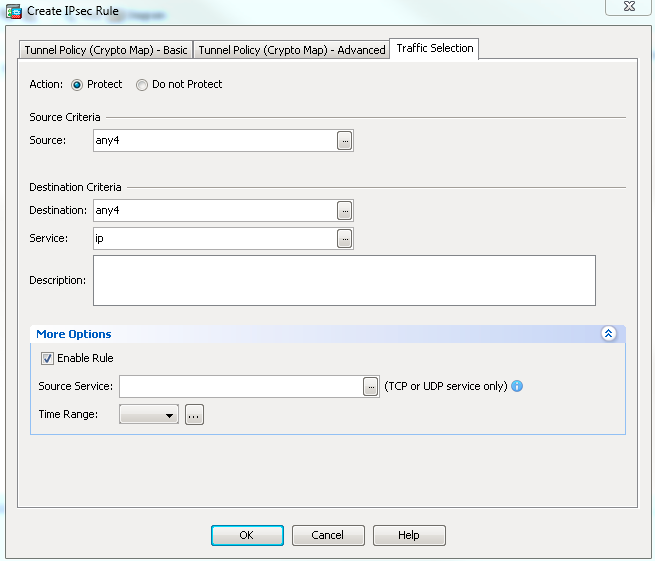
Optionally, from the Traffic Selection tab you can also define the interesting VPN traffic for the dynamic peer and click OK.
ASA Version 9.2(3)
!
hostname ASA
enable password Password
passwd Password
names
!
interface Ethernet0/0
switchport access vlan 2
!
interface Ethernet0/1
!
interface Ethernet0/2
!
interface Ethernet0/3
!
interface Ethernet0/4
!
interface Ethernet0/5
!
interface Ethernet0/6
!
interface Ethernet0/7
!
interface Vlan1
nameif inside
security-level 100
ip address 192.168.3.xx 255.255.255.0
!
interface Vlan2
nameif outside
security-level 0
pppoe client vpdn group BTI
ip address pppoe setroute
!
boot system disk0:/asa923-k8.bin
ftp mode passive
clock timezone GMT 0
object network obj_any
subnet 0.0.0.0 0.0.0.0
access-list incoming-outside extended permit icmp any any echo
access-list incoming-outside extended permit icmp any any echo-reply
pager lines 24
logging enable
logging asdm informational
mtu inside 1500
mtu outside 1500
icmp unreachable rate-limit 1 burst-size 1
icmp permit any inside
icmp permit any outside
asdm image disk0:/asdm-761.bin
no asdm history enable
arp timeout 14400
no arp permit-nonconnected
!
object network obj_any
nat (inside,outside) dynamic interface
access-group incoming-outside in interface outside
timeout xlate 3:00:00
timeout pat-xlate 0:00:30
timeout conn 0:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout sip-provisional-media 0:02:00 uauth 0:05:00 absolute
timeout tcp-proxy-reassembly 0:01:00
timeout floating-conn 0:00:00
dynamic-access-policy-record DfltAccessPolicy
user-identity default-domain LOCAL
aaa authentication ssh console LOCAL
aaa authentication enable console LOCAL
http server enable
http 192.168.3.0 255.255.255.0 inside
http 84.92.xx.xx 255.255.255.255 outside
no snmp-server location
no snmp-server contact
crypto ipsec security-association pmtu-aging infinite
crypto ca trustpool policy
crypto ikev1 enable outside
telnet timeout 5
no ssh stricthostkeycheck
ssh 192.168.3.0 255.255.255.0 inside
ssh 84.92.xx.xx 255.255.255.255 outside
ssh timeout 5
ssh key-exchange group dh-group1-sha1
console timeout 0
vpdn group BTI request dialout pppoe
vpdn group BTI localname Internet@bt.com
vpdn group BTI ppp authentication chap
vpdn username Internet@bt.com password password store-local
dhcpd auto_config outside
!
threat-detection basic-threat
threat-detection statistics access-list
no threat-detection statistics tcp-intercept
username User password Password privilege 15
!
class-map inspection_default
match default-inspection-traffic
!
!
policy-map type inspect dns preset_dns_map
parameters
message-length maximum client auto
message-length maximum 512
policy-map global_policy
class inspection_default
inspect dns preset_dns_map
inspect ftp
inspect h323 h225
inspect h323 ras
inspect rsh
inspect rtsp
inspect esmtp
inspect sqlnet
inspect skinny
inspect sunrpc
inspect xdmcp
inspect sip
inspect netbios
inspect tftp
inspect icmp
inspect ip-options
!
service-policy global_policy global
prompt hostname context
no call-home reporting anonymous
I have this exact setup on another couple of ASA's and it's been fine.
Thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-17-2016 08:35 AM
Simon
I am confused about this. You say that this ASA does have static IP but here is the config of the outside interface vlan
nterface Vlan2
nameif outside
security-level 0
pppoe client vpdn group BTI
ip address pppoe setroute
which is clearly learning its IP address dynamically via pppoe. The article is not saying that the ASA should have static IP on some interface but is saying that the ASA should have static IP on the interface it is using to peer with on the VPN.
HTH
Rick
Rick
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2016 04:04 AM
Hi Rick,
I now see what you are saying the ASA does have a static IP but the config doesn't reflect the ip, I now have it working using your suggestion of changing the access list traffic and all is now working.
Thank you!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
12-19-2016 06:24 AM
Simon
Good to know that it is now working. Thanks for posting back to the forum to confirm this.
HTH
Rick
Rick
- « Previous
-
- 1
- 2
- Next »
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide