- Cisco Community
- Technology and Support
- Networking
- SD-WAN and Cloud Networking
- Re: vManage API - GET works, POST fails
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 02:00 PM
Hello,
With 19.2 I'm having trouble with the API calls, in my python scripts and POSTMAN.
For a GET with BasicAuth I get the expected results. For example with
<html> <head> <title>Error</title> </head> <body>SessionTokenFilter: Token provided via HTTP Header does not match the token generated by the server.</body> </html>
{
"query": {
"condition": "AND",
"rules": [
{
"value": [
"3"
],
"field": "entry_time",
"type": "date",
"operator": "last_n_hours"
},
{"value": ["major"], "field": "severity_level", "type": "string", "operator": "in"},
{"value": ["App-Route"], "field": "component", "type": "string", "operator": "in"},
{"value": ["100.90.3.4"], "field": "system_ip", "type": "string", "operator": "in"},
{"value": ["sla-change","sla-violation","sla-violation-pkt-drop"],"field": "eventname","type": "string","operator": "in"}
]
},
"size": 10000
}Solved! Go to Solution.
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 05:17 PM - edited 09-24-2019 02:31 AM
Hi,
With 19.2 vManage version, API authentication is enhanced to include token in the POST/PUT/DELETE request Headers.
Once login(/j_security_check) is successful run GET request to retrieve token and add it to session headers of subsequent POST/PUT/DELETE requests. Method: GET Request URL: https://vmanage-ip:vmanage-port/dataservice/client/token Store the response XSRF-TOKEN in session headers using “sess.headers['X-XSRF-TOKEN'] = login_token.content”
Sample python code:
def login(self):
base_url = 'https://%s:%s/'%(self.vmanage_host,self.vmanage_port)
login_action = '/j_security_check'
#Format data for loginForm
login_data = {'j_username' : username, 'j_password' : password}
#URL for posting login data
login_url = base_url + login_action
#URL for retrieving client token
token_url = base_url + 'dataservice/client/token'
sess = requests.session()
#If the vmanage has a certificate signed by a trusted authority change verify to True
login_response = sess.post(url=login_url, data=login_data, verify=False)
if b'<html>' in login_response.content:
print ("Login Failed")
exit(0)
#update token to session headers
login_token = sess.get(url=token_url, verify=False)
if login_token.status_code == 200:
if b'<html>' in login_token.content:
print ("Login Token Failed")
exit(0)
sess.headers['X-XSRF-TOKEN'] = login_token.content
self.session[vmanage_host] = sess
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-18-2019 05:17 PM - edited 09-24-2019 02:31 AM
Hi,
With 19.2 vManage version, API authentication is enhanced to include token in the POST/PUT/DELETE request Headers.
Once login(/j_security_check) is successful run GET request to retrieve token and add it to session headers of subsequent POST/PUT/DELETE requests. Method: GET Request URL: https://vmanage-ip:vmanage-port/dataservice/client/token Store the response XSRF-TOKEN in session headers using “sess.headers['X-XSRF-TOKEN'] = login_token.content”
Sample python code:
def login(self):
base_url = 'https://%s:%s/'%(self.vmanage_host,self.vmanage_port)
login_action = '/j_security_check'
#Format data for loginForm
login_data = {'j_username' : username, 'j_password' : password}
#URL for posting login data
login_url = base_url + login_action
#URL for retrieving client token
token_url = base_url + 'dataservice/client/token'
sess = requests.session()
#If the vmanage has a certificate signed by a trusted authority change verify to True
login_response = sess.post(url=login_url, data=login_data, verify=False)
if b'<html>' in login_response.content:
print ("Login Failed")
exit(0)
#update token to session headers
login_token = sess.get(url=token_url, verify=False)
if login_token.status_code == 200:
if b'<html>' in login_token.content:
print ("Login Token Failed")
exit(0)
sess.headers['X-XSRF-TOKEN'] = login_token.content
self.session[vmanage_host] = sess
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2019 09:36 AM
Hi msuchand,
"With 19.2 vManage version, API authentication is enhanced to include token in the POST/PUT/DELETE request Headers."
From my understanding, it would mean that GET routes aren't affected if the token is missing
My problem is:
GET - /dataservice/client/about doesn't work without the token
GET- /dataservice/device/vedgeinventory/detail?status=deployed works without the token
Finally, when is this token required?
I thougth all GET would get their way through without it...
Thanks for the help,
Laurent.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2019 10:39 AM
Hi Laurent,
GET request should work without token.
I tried https://{{vmanage}}:{{port}}/dataservice/client/about on my lab vManage running 19.2 release and didn't see any issue.
Could you please let me know the error you are seeing.
Thanks,
Sai
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2019 12:43 PM - edited 09-24-2019 12:44 PM
Hello,
the only time I got a response was when using POSTMAN.
https://10.48.x.y/dataservice/client/about
Do we have some examples in cURL ?
Regards,
Danny
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-24-2019 11:18 PM
Hello,
I have tested the below sequence of curl commands and it works.
curl --request POST -k -c 'cookies.txt' --url https://vmanage-ip-address/j_security_check --data 'j_username=username&j_password=password'
curl-k -b 'cookies.txt' --url https://vmanage-ip-address/dataservice/client/about
Thanks,
Sai
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2019 05:39 AM - edited 09-25-2019 05:42 AM
Hi Sai,
I tried the curl command as you said and got this:
curl --request POST -k -c 'cookies.txt' --url https://vmanage-ip-address/dataservice/j_security_check --data 'j_username=admin&j_password=admin' curl -k -b 'cookies.txt' --url https://vmanage-ip-address/dataservice/client/about <html><head><title>Error</title></head><body>SessionTokenFilter: Token provided via HTTP Header does not match the token generated by the server.</body></html>
Or more precisely:
curl -i -k -b 'cookies.txt' --url https://vmanage-ip-address/dataservice/client/about HTTP/1.1 403 Forbidden Cache-Control: no-cache, no-store, must-revalidate X-XSS-Protection: 1; mode=block X-Frame-Options: DENY Date: Wed, 25 Sep 2019 12:40:33 GMT Connection: keep-alive Vary: Accept-Encoding Strict-Transport-Security: max-age=31536000; includeSubDomains X-Content-Type-Options: nosniff Content-Type: text/html;charset=UTF-8 Content-Length: 159 <html><head><title>Error</title></head><body>SessionTokenFilter: Token provided via HTTP Header does not match the token generated by the server.</body></html>
However if I add the X-XSRF-TOKEN header it works:
curl -k -b 'cookies.txt' -H "X-XSRF-TOKEN:XXXX" --url https://vmanage-ip-address/dataservice/client/about
{"header":{},"data":{"title":"Cisco vManage","version":"Platform Version: 19.2.0","applicationVersion":"Application Version: 19.2R-vbamboo-14-Aug-2019 19:54:05 PDT","applicationServer":"Server: vmanage","copyright":"Copyright (c) 2019, Cisco. All rights reserved.","time":"2019-09-25 12:33:32,813","timeZone":"UTC","logo":"/dataservice/client/logo.png"}}
Is this normal that we need token for a GET request?
I'd like to avoid this token as much as possible since I only use GET methods of VManage api...
Thanks for the help,
Laurent.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-25-2019 03:23 PM
One can always look at the logfiles on the vManage to see which errors get generated.
I got the same error Token provided via HTTP Header does not match the token generated by the server using cURL.
The vmanage-server-rest.log show error.
25-Sep-2019 23:34:40,172 CEST WARN [vmanage] [DataServiceLoggingFilter] (default task-11) Unable to process request = /client/about from client = 10.24.23.107/admin!: java.io.IOException: UT010029: Stream is closed
With the token cURL example you gave it works indeed.
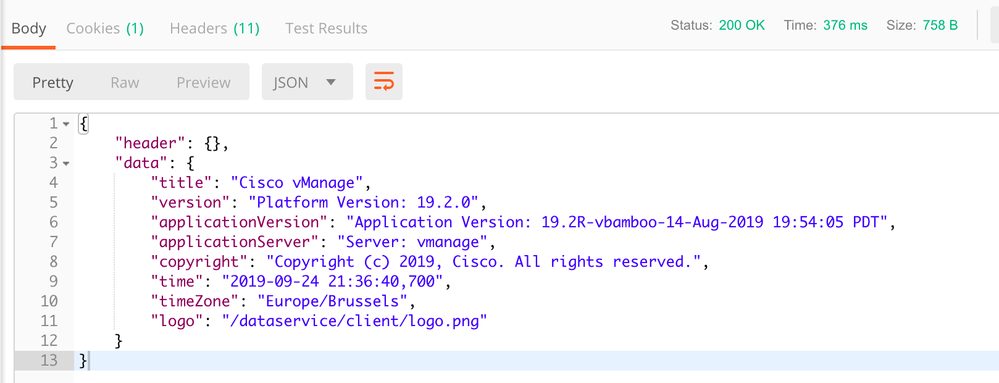
M-82HC:~ dderidde$ curl -s -k -b 'cookies.txt' -H "X-XSRF-TOKEN:AB4C1C8F02AC42DCE1B672C86C23C8F5AE1211A976CC6589226D41829EBD022C84548390B351BA4CB22642AD16747D77C0A5" --url https://10.48.x.y/dataservice/client/about | python -m json.tool
{
"data": {
"applicationServer": "Server: vmanage",
"applicationVersion": "Application Version: 19.2R-vbamboo-14-Aug-2019 19:54:05 PDT",
"copyright": "Copyright (c) 2019, Cisco. All rights reserved.",
"logo": "/dataservice/client/logo.png",
"time": "2019-09-26 00:20:54,980",
"timeZone": "Europe/Brussels",
"title": "Cisco vManage",
"version": "Platform Version: 19.2.0"
},
"header": {}
}
M-82HC:~ dderidde$
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
09-26-2019 07:24 AM
Hi Laurent,
Sorry I missed that I had enabled whitelist on my lab vManage to skip token requirement.
For whitelisting please reach out to TAC as suggested at link: https://www.cisco.com/c/en/us/td/docs/routers/sdwan/software/configuration/sdwan-xe-gs-book/sdwan-xe-gs-book_chapter_011.html
Thanks,
Sai
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-07-2021 09:02 AM
Could you point documentation, where it is copied from?
I wasn't able to find documentation in any configuration guide about authorisation steps used by sd-wan.
There is quite well documented guide in devnet site, but I think we wouldn't have access to that resource during the CCIE EI lab exam.
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide