- Cisco Community
- Technology and Support
- Security
- Security Analytics
- StealthWatch SSL/TLS Client Identity Certificate
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
StealthWatch SSL/TLS Client Identity Certificate
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-04-2024 10:23 PM
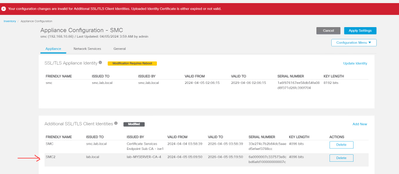
Uploaded the Trusted CA Root certificate to the "Trust Store" in the SMC. Then I generated a CSR from the SMC "Additional SSL/TLS Client Identities" and signed it by the CA server "Windows server", but when I upload the new signed certificate and click "Apply Setting", I received the message as shown below
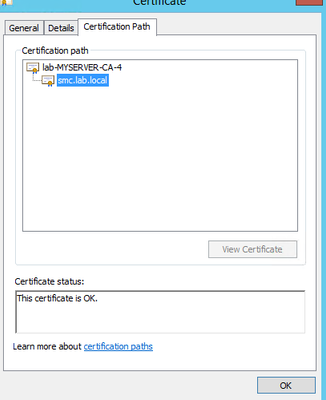
The certificate looks good to me
Please advise if you any of you seen this before.
- Labels:
-
Stealthwatch
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
04-22-2024 11:10 PM
Hi Adam99_Security,
The client identity is used for communication between external services such as Cisco Identity Services Engine (ISE) and Cisco Security Packet Analyzer.
And if you are using it to integrate with ISE, you may need add the ISE Root CA into Trust Store first and then add this additional SSL/TLS Client Identities.
Please kindly check the follow link address:
https://integratingit.wordpress.com/2020/03/03/ise-integration-with-stealthwatch/
-----------------------------------------
If you find my reply solved your question or issue, kindly click the 'Accept as Solution' button and vote it as helpful.
You can also learn more about Secure Network Analytics (formerly known as StealthWatch) through our live Ask the Experts (ATXs) session. Check out Cisco Network Security ATXs Resources [https://community.cisco.com/t5/security-knowledge-base/cisco-network-security-ask-the-experts-resources/ta-p/4416493] to view the latest schedule for upcoming sessions, as well as the useful references, e.g. online guides, FAQs.
-----------------------------------------
Best Regards,
Henry
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
07-31-2024 11:02 AM
Hi,
Stealthwatch is extremely picky with certificates. But as lohan already indicated, it just looks like you are trying to add a certificate to communicate with external services such as ISE, FMC, FTD etc. The obvious certificate to use here would be a pxGrid certificate which you could use to integrate with a lot of other products.
Anyway, the error message just means that it's not trusted so probably just missing the "RootCA" or "SubCA/IntermediateCA" in your truststore. I see that you have a SSL-certificate signed for the SMC appliance from "smc.lab.local".
While your new one is signed by "lab-MYSERVER-CA-4". Make sure to upload "lab-MYSERVER-CA-4" in SMC truststore as well as "smc.lab.local" and it should work.
Also noticed that it looks like you have multiple certs for the same device/cn (smc.lab.local) where one seems to be signed by ISE and another from a different CA. This might also cause some issues with how certificates are trusted. I would recommend to at least be able to distinguish between them.
HTH
-Daniel
Discover and save your favorite ideas. Come back to expert answers, step-by-step guides, recent topics, and more.
New here? Get started with these tips. How to use Community New member guide