- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- How to Deploy ISE Device Admin with Duo MFA
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
03-28-2019
05:05 AM
- edited on
04-15-2019
08:27 AM
by
thomas
![]()
- Introduction
- Requirements
- ISE Device Admin with Duo MFA flow
- Duo Deployment
- Sign up for Duo Account and Protect Application
- Create Duo Proxy Server
- Enrolling Duo Users
- ISE Device Admin Deployment
- Enable TACACS+
- Add Active Directory to ISE andImport Domain Groups
- Add Network Access Device (NAD) to ISE
- Add Duo Proxy Server to ISE
- Setting up TACACS Policy Elements
- Create Device Admin Policy Set / Authentication / Authorization
- Initiate Login Process
- TACACS Live Logs
Introduction
Two Factor Authentication adds a second layer of security to your existing account before granting access to corporate applications and services as well as Network Access Devices (NAD).
As you may already have an existing account in your company such as Active Directory, LDAP etc . With 2FA you verify your existing identity using a second factor , like your phone or other mobile devices to provide a secondary password.
The prevents just anyone logging in even if your primary password is compromised , and your secondary factor of authentication is independent from your primary username and password , so Duo never sees your primary password.
Requirements
- ISE2.x
- Identity Store
- Duo Proxy Server
- Duo Account
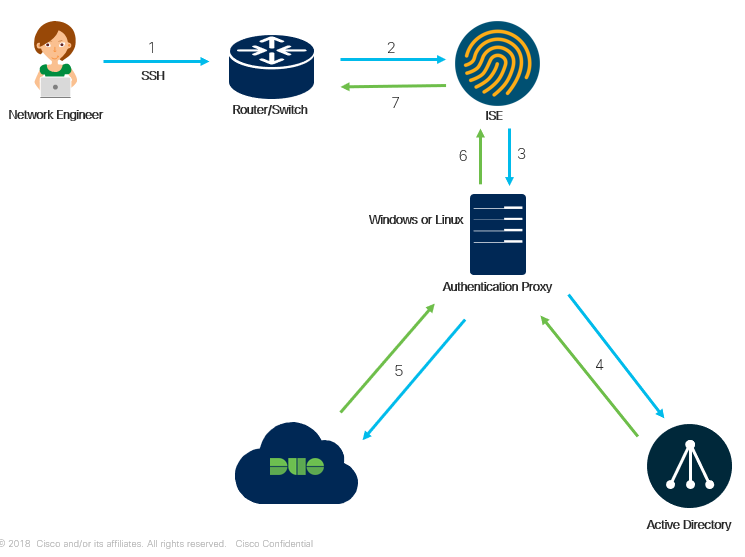
ISE Device Admin with Duo MFA flow
- User Initiates an SSH session to the Network Device and is prompt for a username and password , at this stage the end user will provide this Primary Password (In this scenario we are using Active Directory) along with a secondary password which is the Duo Passcode , this is obtained by the duo application that is running on the end users mobile device.
- TACACS+ authentication request is sent to ISE
- ISE sends the Authentication request over Radius to the Duo Security Authentication Proxy Server
- The Primary Authentication is done using the Active Directory password account , and only if successful will the proxy server continue with Secondary Authentication.
- A Secondary Authentication request is sent to the Duo Security Service using the passcode generated by the duo application running on the user ends mobile device.In this step the proxy server will create an outbound connection to the Duo Security Service over tcp port 443 , keep this in mind if you have a FW or any blocking of access along the path.
- The Authentication is successful which at step 6 the Authentication proxy server will send a radius response of Access-Accept to ISE.
- ISE will provide Access and Authorization based on Device Admin policy set.
Note You may use either the passcode provided by the application on your mobile device or by Duo sending a PUSH notification to your mobile device requesting to Approve or Deny the login request.
Duo Deployment
Sign up for Duo Account and Protect Application
- Go to following link to request a free trial account and follow the first 5 steps only.https://duo.com/docs/getting-started
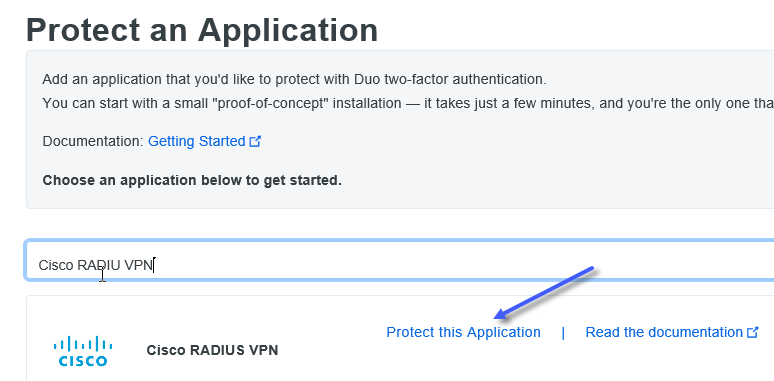
- In Step 5 you will be requested to choose a service/system/appliance you wish to protect with Duo . This is done from your Duo Admin Panel Dashboard you you logged onto in Step 4 under "Applications" (on the left hand side)
- Go to following link to request a free trial account and follow the first 5 steps only.https://duo.com/docs/getting-started
- In Step 5 you will be requested to choose a service/system/appliance you wish to protect with Duo . This is done from your Duo Admin Panel Dashboard you you logged onto in Step 4 under "Applications > Protect an Application" (on the left hand side) enter "Cisco RADIUS VPN" and click on "Protect this Application"
- The "Cisco RADIUS VPN" application will have your Integration Key/Secret Key information which is needed when setting in the next step when setting up your Duo Proxy Server.
- At the bottom of the page provide a "Name" , Duo users will see this in their push notifications that are sent to their mobile devices.
Create Duo Proxy Server
The Duo Proxy Server can be installed on Windows or Linux as well as a Virtual host.
Use the following document as guidance steps to deploy your proxy server: Install the Duo Authentication Proxy
Your configuration file (authproxy.cfg) should look something like this:
[ad_client]
host=x.x.x.x (your domain controller)
service_account_username=duouser
service_account_password=password
search_dn=DC=example,DC=com
[radius_server_auto]
ikey=XXXXXXXXXXXXXXXXX
skey=XXXXXXXXXXXXXXXXXX
api_host=xxxxxxxxxxxxxxxx
radius_ip_1=x.x.x.x (your ISE RADIUS Server)
radius_secret_1=isesecret
failmode=safe
client=ad_client
port=1812
The following fields ikey/skey/api_host can be found in your Duo Dashboard under the protected application that you have chosen.
Once your file is completed start the Proxy as followed in Start the Proxy.
If your having any trouble starting your proxy please refer to Troubleshooting.
Enrolling Duo Users
Duo provides several enrollment methods to add users to the system.
In this example we will be using the "Manual Enrollment" method from manual-enrollment.
Keep in mind since this is a manual enrollment be sure that the Duo username matches the users primary authentication username (in this scenario it will be our Active Directory account).
Maker sure to Install Duo App on your mobile device. This can be done either via your dashboard or by going to Play Store and downloading Duo App. See manual-enrollment process.
You have completed the Duo portion of the setup.
ISE Device Admin Deployment
Enable TACACS+
Log into ISE and enable Tacacs+ Service by going to Administration > System > Deployment , choose the relevant node you with to run Device Admin Services on and check mark the box next to "Enable Device Admin Service"
Add Active Directory to ISE and Import Domain Groups
- Go to Administration > Identity Management > External Identity Sources > Active Directory
-
Click on "Add" fill in the following fields and click "Submit"
Joint Point Name: AD1
Active Directory Domain: isedemo.net
See following Document on How To Add Active Directory to ISE and retrieve groups: Getting Started With ISE.
In this example we will import the AD Group "West_Coast"
Add Network Access Device (NAD) to ISE
In this section we will add the NAD to ISE which we will use for Tacacs+ (Device Admin)
- Go to Administration > Network Resources > Network Devices > Click on "Add"
- Fill in the following Fields
Name: Your Device Name
IP: x.x.x.x - Check mark "TACACS Authentication Settings" and enter "Shared Secret"
- Click "Submit" at the bottom of the page.
Add Duo Proxy Server to ISE
In this section we will add the duo proxy server we setup in previous steps to ISE , in order to allow for mutual communication between the two.
- Go to Administration > Identity Management > External Identity Sources > RADIUS Token
- Click "Add"
- Under Tab "General" enter a name that makes sense to you
- Under Tab "Connection" fill in the following fields
Host IP: <IP address of your Proxy Server>
Shared Secret: <same Shared Secret used when setting up the Proxy Server file authproxy.cfg>
Server Timeout: 60 - note default time is 5 , make sure to modify to 60 to avoid radius timeouts - Click "Submit"
Setting up TACACS Policy Elements
Before we setup a Policy Set with Authentication and Authorization Policies we need to create Tacacs policy elements to provide TACACS Profiles and command sets.
Guide lines on how to configure these can be found at the following:
TACACS Profile
Create Device Admin Policy Set / Authentication / Authorization
Device Admin contains its own Policy Set as well as Authentication and Authorization policies.Do not confuse this with the policy sets that are used for Network Access Control.
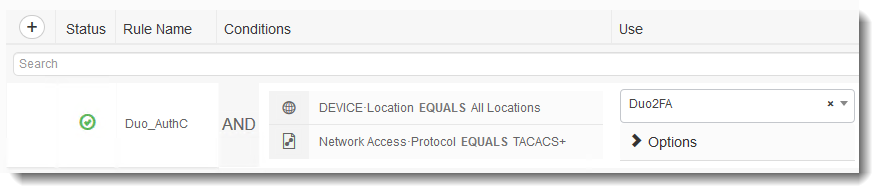
In the following example we have created a Policy Set called "Duo 2FA" and the Condition to be met will be the IP Address of my NAD device , leaving "Default Device Admin" Protocols.

With in the Policy set we will create the Authentication Policy and use the Duo Proxy we created in previous steps for Authentication.
Authentication
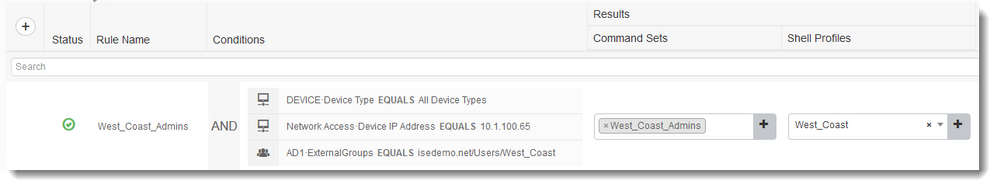
Authorization
Notice the 3rd condition is to match the AD Group we imported "West_Coast"
Initiate Login Process
At this point we are ready to login to our Network Access Device using Duo 2FA
There are a couple of methods to Authenticate with Duo
- When you SSH to device and are prompt for password enter your Primary Password first followed by a comma and then passcode generated from the mobile app.They syntax should look like this:
Password:mypassword,duopasscode - Another option is to have Duo send a PUSH notification to your mobile for approval. The syntax to be used is your Primary Password follow by a comman and then the phrase "push". The syntax should look like this:
Password:mypassword,push
TACACS Live Logs
In the following diagram we have achieved Authentication using the Duo_AuthC policy we configured previously.
Note the user "hdwest" is a part of the AD group "West_Coast"
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @ldanny
This article was written a while ago - I wasn't a Duo user back then, but things are a bit different today (2021). I just did an ISE 3.0 install and the customer wanted TACACS+ enabled in ISE. The authentication used was Duo Proxy. Their Duo Proxy sends the user's credentials to AD server for authentication. If the authentication is correct, the proxy sends a Push to the user's Duo app. Once the user approves the Duo push notification, the Radius proxy sends Access-Accept back to ISE. Then the TACACS+ success is sent back to the NAS. Very different to your call diagram.
I was struggling to get the Authorization to work - Duo Support instructed us to create an ISE Identity Source Sequence that goes to Duo Proxy first, followed by AD. I was VERY surprised by that. But it works. Now I can use AD Groups in ISE for Authorization.
I was expecting the Duo Proxy to return RADIUS attributes that ISE could use during Authorization. I find the AD authN/authZ combination a bit dirty and I feel it's not optimal. What is the suggested ISE config in this scenario (i.e. does ISE use the returned Proxy RADIUS attributes for authZ or must AD be involved for authZ)?
Another very important note is that in this scenario, the NAS TACACS+ timeout settings should NOT be 2 or 5 seconds. It's too short. Users will need some extra time to unlock their phones and click the 'Yes' button. I noticed retry issues with those values and changed it to 30 seconds. No more issues.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @Arne Bier , THANK YOU, this saved me a lot of time and troubleshooting. Changing the Identity Source Sequence and adding Duo before AD did the trick for me. Duo authentication was working just fine, but authorization was not working. After the Identity Source Sequence change, no more "Command Authorization Failed" when entering commands.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
While doing "Protect an application" in Duo, we use "Cisco RADIUS VPN" to configure it for VPN 2FA.
What applicaion will we protect when we need to configre it for device admin (SSH to a switch/router) 2FA.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Awesome, Thank You for sharing!!!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: