- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- IPSec overhead calculator tool
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
06-30-2016 11:15 AM - edited 07-07-2023 12:20 PM
With the increasing popularity of IPSec VPN deployments on the Internet, there is often a need to understand the exact IPSec and other tunnel encapsulation overhead in order to determine the fragmentation boundary conditions for optimal MTU/MSS tuning, or to perform bandwidth budgeting on low-bandwidth links. Given these overheads vary depending on the specific IPSec protocols and algorithms used, we have developed a tool to make this task easier, and it can be found here:
IPSec Overhead Calculator Tool
This tool was just recently updated with an improved user interface and IPv6 support. Check it out and feel free to provide feedback or improvement ideas by clicking on the Feedback icon on the top right corner of the page.
Note, even though most of the overhead calculation for this tool is standard RFC based, some can be implementation specific, such as ESP padding. For those calculations, the tool is based on the Cisco IOS/IOS-XE implementation.
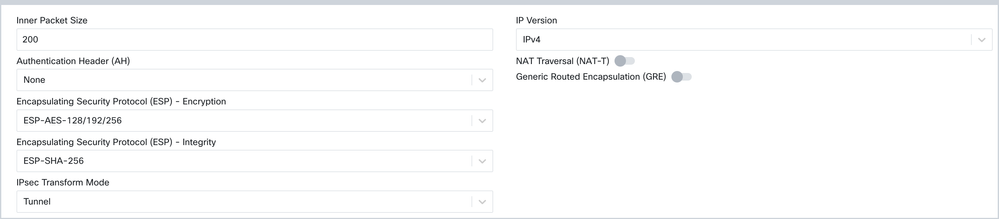
Here is an example user input:
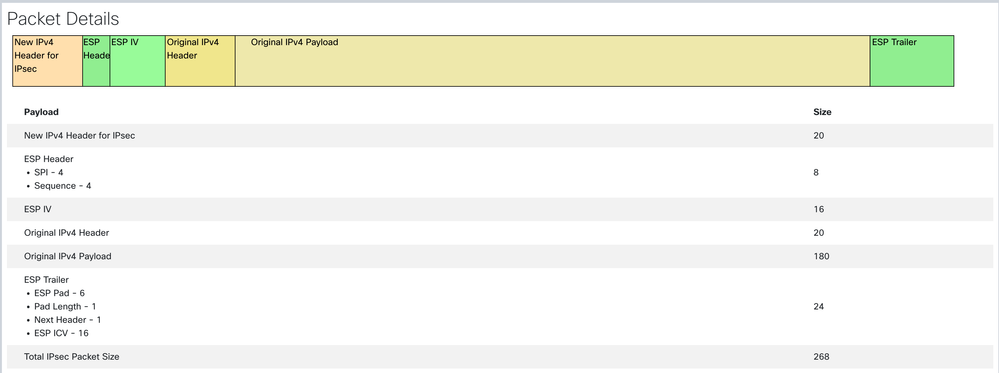
The result output of the tool:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
We are using (with ASR 1001-X):
GRE over IPSec + Tunnel Key
IPv4
Tunnel Mode "Transport"
ESP Encryption "ESP-GCM-256"
ESP Integrity "none"
AH Integrity "none"
Wireshark and Cisco Counters at the Router show an Overhead from 62 Bytes.
The "IPSec Overhead Calculator Tool" shows an Overhead from 64 Bytes.
I think the calculation is wrong in the "IPSec Overhead Calculator Tool".
Can you please check this?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Excellent tool - could you add the original IP header size to the "packet details"
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
How about ikev1 vs ikev2??
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@pboynton1 , I know this is a very late response but posting in case someone else has the same question. IKEv1 and IKEv2 are used as a control plane to negotiate and install IPSec SAs. The data going over the tunnel, called the data plane, will use ESP (and rarely AH), which is a separate protocol to IKEv1 and IKEv2. In short, it will be the same whether you use IKEv1 of IKEv2.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: