- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Troubleshooting Site to Site VPN Implementations.
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 12-18-2014 07:02 AM
Introduction:
This document describes multiple scenarios for troubleshooting Site to Site VPN installation faced by users.
Scenario 1:site to site vpn config not working
Problem:
User have just attempted to configure a test site to site VPN. Diagram of arrangement is attached. Router R2 is supposed to act like the 'Internet' just to allow connectivity between both networks.
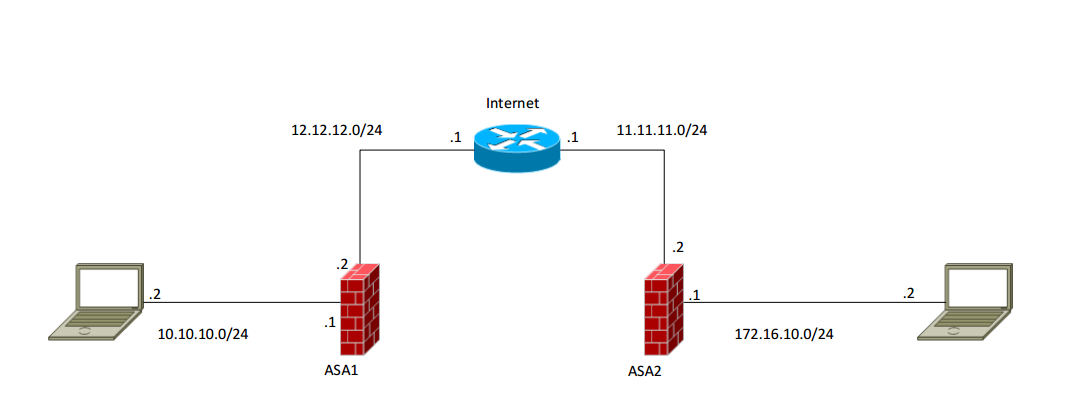
VPN configs on ASA1 and ASA2 are below:
ASA1
access-list outside_cryptomap_1 remark Encrypt VPN traffic
access-list outside_cryptomap_1 extended permit ip 10.10.10.0 255.255.255.0 172.16.10.0 255.225.255.0
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
tunnel-group 11.11.11.2 type ipsec-l2l
tunnel-group 11.11.11.2 ipsec-attributes
ikev1 pre-shared-key cisco
crypto ipsec ikev1 transform-set AES-SHA esp-aes-256 esp-sha-hmac
crypto map outside_map 1 match address outside_cryptomap_1
crypto map outside_map 1 set peer 11.11.11.2
crypto map outside_map 1 set transform-set AES-SHA
crypto map outside_map interface outside
ASA2
access-list outside_cryptomap_1 remark Encrypt VPN traffic
access-list outside_cryptomap_1 extended permit ip 172.16.10.0 255.255.255.0 10.10.10.0 255.225.255.0
crypto ikev1 enable outside
crypto ikev1 policy 1
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
tunnel-group 12.12.12.2 type ipsec-l2l
tunnel-group 12.12.12.2 ipsec-attributes
ikev1 pre-shared-key cisco
crypto ipsec ikev1 transform-set AES-SHA esp-aes-256 esp-sha-hmac
crypto map outside_map 1 match address outside_cryptomap_1
crypto map outside_map 1 set peer 12.12.12.2
crypto map outside_map 1 set transform-set AES-SHA
crypto map outside_map interface outside
User can ping from ASA1 to ASA2, but when he try to test the VPN by trying from one PC to the other, he get nothing.He tried some show commands and they came out absolutely blank..like he configured nothing:
sh crypto isakmp sa detail
There are no IKEv1 SAs
There are no IKEv2 SAs
sh crypto ipsec sa
There are no ipsec sas
Solution:
nat exemption
On ASA1:
nat (inside,outside) source static lan1 lan1 destination static lan2 lan2
object network lan1
subnet 10.10.10.0 255.255.255.0
object network lan2
subnet 172.16.10.0 255.255.255.0
On ASA2:
nat (inside,outside) source static lan2 lan2 destination static lan1 lan1
object network lan1
subnet 10.10.10.0 255.255.255.0
object network lan2
subnet 172.16.10.0 255.255.255.0
If it did not work with that, please try if you can ping the router interface 11.11.11.x from pc 10.10.10.x behind the ASA1, if not try to check if the icmp inspection is set:
policy-map global_policy
class inspection_default
inspect icmp
ASA 1:
ASA1(config)# sh run
: Saved
:
ASA Version 8.0(2)
!
hostname ASA1
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 12.12.12.2 255.255.255.0
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 10.10.10.2 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/5
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list vpn extended permit ip 10.10.10.0 255.255.255.0 172.16.10.0 255.255.255.0
pager lines 24
mtu inside 1500
mtu outside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
route outside 0.0.0.0 0.0.0.0 12.12.12.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set tset esp-3des esp-sha-hmac
crypto map cmap 1 match address vpn
crypto map cmap 1 set peer 11.11.11.2
crypto map cmap 1 set transform-set tset
crypto map cmap interface outside
crypto isakmp enable outside
crypto isakmp policy 1
authentication pre-share
encryption 3des
hash md5
group 5
lifetime 86400
crypto isakmp policy 65535
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
!
tunnel-group 11.11.11.2 type ipsec-l2l
tunnel-group 11.11.11.2 ipsec-attributes
pre-shared-key *
prompt hostname context
Cryptochecksum:00000000000000000000000000000000
: end
ASA1(config)#
ASA 2:
ASA2(config)# sh run
: Saved
:
ASA Version 8.0(2)
!
hostname ASA2
enable password 8Ry2YjIyt7RRXU24 encrypted
names
!
interface Ethernet0/0
nameif outside
security-level 0
ip address 11.11.11.2 255.255.255.0
!
interface Ethernet0/1
nameif inside
security-level 100
ip address 172.16.10.2 255.255.255.0
!
interface Ethernet0/2
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/3
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/4
shutdown
no nameif
no security-level
no ip address
!
interface Ethernet0/5
shutdown
no nameif
no security-level
no ip address
!
passwd 2KFQnbNIdI.2KYOU encrypted
ftp mode passive
access-list vpn extended permit ip 172.16.10.0 255.255.255.0 10.10.10.0 255.255.255.0
pager lines 24
mtu outside 1500
mtu inside 1500
no failover
icmp unreachable rate-limit 1 burst-size 1
no asdm history enable
arp timeout 14400
route outside 0.0.0.0 0.0.0.0 11.11.11.1 1
timeout xlate 3:00:00
timeout conn 1:00:00 half-closed 0:10:00 udp 0:02:00 icmp 0:00:02
timeout sunrpc 0:10:00 h323 0:05:00 h225 1:00:00 mgcp 0:05:00 mgcp-pat 0:05:00
timeout sip 0:30:00 sip_media 0:02:00 sip-invite 0:03:00 sip-disconnect 0:02:00
timeout uauth 0:05:00 absolute
dynamic-access-policy-record DfltAccessPolicy
no snmp-server location
no snmp-server contact
snmp-server enable traps snmp authentication linkup linkdown coldstart
crypto ipsec transform-set tset esp-3des esp-sha-hmac
crypto map cmap 1 match address vpn
crypto map cmap 1 set peer 12.12.12.2
crypto map cmap 1 set transform-set tset
crypto map cmap interface outside
crypto isakmp enable outside
crypto isakmp policy 1
authentication pre-share
encryption 3des
hash md5
group 5
lifetime 86400
crypto isakmp policy 65535
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
telnet timeout 5
ssh timeout 5
console timeout 0
threat-detection basic-threat
threat-detection statistics access-list
!
!
!
tunnel-group 12.12.12.2 type ipsec-l2l
tunnel-group 12.12.12.2 ipsec-attributes
pre-shared-key *
prompt hostname context
Cryptochecksum:00000000000000000000000000000000
: end
OUTPUTS:
ASA1(config)# sh crypto isakmp sa
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 11.11.11.2
Type : L2L Role : initiator
Rekey : no State : MM_ACTIVE
---------------------
ASA1(config)# sh crypto ipsec sa
interface: outside
Crypto map tag: cmap, seq num: 1, local addr: 12.12.12.2
access-list vpn permit ip 10.10.10.0 255.255.255.0 172.16.10.0 255.255.255.0
local ident (addr/mask/prot/port): (10.10.10.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (172.16.10.0/255.255.255.0/0/0)
current_peer: 11.11.11.2
#pkts encaps: 50, #pkts encrypt: 50, #pkts digest: 50
#pkts decaps: 49, #pkts decrypt: 49, #pkts verify: 49
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 50, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 12.12.12.2, remote crypto endpt.: 11.11.11.2
------------------------
ASA2(config)# sh crypto isakmp sa
Active SA: 1
Rekey SA: 0 (A tunnel will report 1 Active and 1 Rekey SA during rekey)
Total IKE SA: 1
1 IKE Peer: 12.12.12.2
Type : L2L Role : responder
Rekey : no State : MM_ACTIVE
------------------------
ASA2(config)# sh crypto ipsec sa
interface: outside
Crypto map tag: cmap, seq num: 1, local addr: 11.11.11.2
access-list vpn permit ip 172.16.10.0 255.255.255.0 10.10.10.0 255.255.255.0
local ident (addr/mask/prot/port): (172.16.10.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (10.10.10.0/255.255.255.0/0/0)
current_peer: 12.12.12.2
#pkts encaps: 49, #pkts encrypt: 49, #pkts digest: 49
#pkts decaps: 50, #pkts decrypt: 50, #pkts verify: 50
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 49, #pkts comp failed: 0, #pkts decomp failed: 0
#pre-frag successes: 0, #pre-frag failures: 0, #fragments created: 0
#PMTUs sent: 0, #PMTUs rcvd: 0, #decapsulated frgs needing reassembly: 0
#send errors: 0, #recv errors: 0
local crypto endpt.: 11.11.11.2, remote crypto endpt.: 12.12.12.2
Scenario 2:
Problem:
User trying to establish a site to site VPN in packet tracer. He followed the instructions from a website, but can't seem to get it working. The site said that it would break OSPF updates and he would need to set up a GRE tunnel. So far it broke all traffic except OSPF updates...show ip route shows all the needed routes. He has uploaded the packet tracer as well as both router configs.
Solution:
Just briefly checking your config:
Pre-shared-key is missing.
S2Router is missing PFS2 in crypto map.
Crypto ACL SECURED_TRAFFIC MUST BE AN EXACT REPLICA (in-reverse) on each router.
once you fix these basic vpn issues, if it still doesn't work, we can look into advanced troubleshooting. at this stage its just your config which needs to be correct.
And you better use GNs3 etc for this sort of test, or physical hardware if possible.
Source Discussion:
site to site vpn config not working
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Anim Saxena,
Could you please help me to configure VPN site-to site. I make ping from 192.168.7.10, PC, connected to test interface. When I start ping from 192.168.7.10 VNP doesnt UP.
From opposite site (ASA1) the configuration the same but version another 9.1. And from opposite site (ASA1) when I start ping the VPN became UP. I make ping from 172.16.0.3, PC, connected to inside interface of ASA1 (opposite side). I see packets coming to 192.168.7.10 (via wireshark) and 192.168.7.10 makes reply. HERE on ASA1 I discovered next config than may affect
access-list outside_access_in remark Block all Management traffic on outside interface
access-list outside_access_in extended deny ip any any log disable
access-list outside_access_in_1 remark vpn test, can be removed
access-list outside_access_in_1 extended permit ip object ASA2_VPN_test any
access-list outside_access_in_1 extended permit ip any object VideoTerminal1
access-group outside_access_in in interface outside control-plane
access-group outside_access_in_1 in interface outside
best regards,
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I found mistake, it is on opposite side (ASA1):
access-list outside_access_in extended deny ip any any log disable
Thank you
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: