- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Anyconnect VPN SAML SSO with Azure IdP, Multi-Tunnel Groups
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 03-03-2022 07:16 AM
Symptoms
I had incredible difficulty locating details and even vendor support surrounding setting up Azure SSO to service anyconnect connectivity with multiple tunnel groups. So thought I'd potentially help by documenting the fix
Diagnosis
After following the microsoft or cisco community documentation for SAML SSO setup with anyconnect/ASA:
Tutorial: Azure Active Directory single sign-on (SSO) integration with Cisco AnyConnect | Microsoft Docs
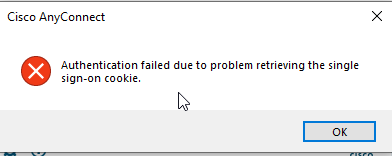
However, at the point of registering the Identity URL. DO NOT make the same mistake and assumption of adding the additional Tunnel Group URLs to the identity and reply URLs, The last entry in the URL list will succeed but the other profiles will fail and lead to the following error on client side:
Solution
Pre-Requisites
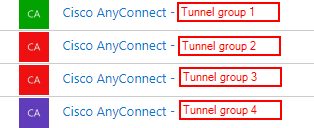
- Create separate enterprise apps for each tunnel group <TunnelGroupName>
- External SSL Certificate for your domain registered for anyconnect (I had a wildcard cert for this)
Azure config:
- Follow guide, for each created app for each tunnel group:
Tutorial: Azure Active Directory single sign-on (SSO) integration with Cisco AnyConnect | Microsoft Docs
until this point:
- Click Edit
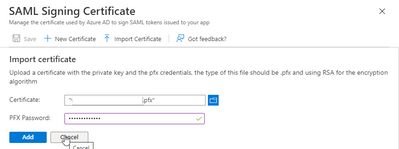
- Select import Cert:
- Select your cert and enter passphrase (must be PFX format), Click Add
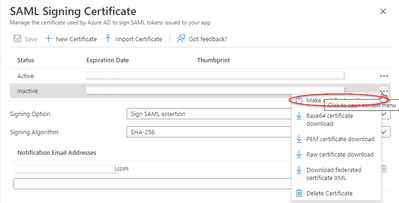
- Activate Certificate:
NOTE: Certifate for each app must all be the same
ASA Config:
You are going to do this on the CLI first, you might come back through and do an ASDM walk-through at another time.
Connect to your VPN Appliance, you are going to be using an ASA running 9.8 code train, and your VPN clients will be 4.6+.
First you will create a Trustpoint and import our SAML cert.
config t crypto ca trustpoint AzureAD-AC-SAML revocation-check none no id-usage enrollment terminal no ca-check crypto ca authenticate AzureAD-AC-SAML -----BEGIN CERTIFICATE----- … PEM Certificate Text from download goes here … -----END CERTIFICATE----- quit
The following commands will provision your SAML IdP.
webvpn saml idp https://sts.windows.net/xxxxxxxxxxxxx/ (This is your Azure AD Identifier from the Set up Cisco AnyConnect section in the Azure portal) url sign-in https://login.microsoftonline.com/xxxxxxxxxxxxxxxxxxxxxx/saml2 (This is your Login URL from the Set up Cisco AnyConnect section in the Azure portal) url sign-out https://login.microsoftonline.com/common/wsfederation?wa=wsignout1.0 (This is Logout URL from the Set up Cisco AnyConnect section in the Azure portal) trustpoint idp AzureAD-AC-SAML trustpoint sp (Trustpoint for SAML Requests - you can use your existing external cert here) no force re-authentication no signature base-url https://my.asa.com
Now you can apply SAML Authentication to a VPN Tunnel Configuration.
tunnel-group AC-SAML webvpn-attributes saml identity-provider https://sts.windows.net/xxxxxxxxxxxxx/ authentication saml end write mem
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @nathan.browning ,
Ii this working with firepower 2100?
Am i obligated to use one anyconnect app per tunnel group or can be used only one app modifying the entity id string and reply URL on azure?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
i've tried your procedure and worked!!!! thank you man! you saved me
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This was super helpful. Something to note is that you need to create your own PFX certificate which you can use in Azure AD Signing Certificate for all Enterprise App SAML configs.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I believe the need for multiple Azure IdP apps would be prevented once this bug is fixed:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello @nathan.browning ,
can someone explain more part about the certificate?
- External SSL Certificate for your domain registered for anyconnect (I had a wildcard cert for this)
What certificate did you use? wildcard for your organization or selfsignecertificate?
Best regards,
Ivan
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
So, I've been trying to get this to work and I've been running into issues. I've followed this guide, which is great btw, and when I go to test it I get an error saying that the application with identifier was not found. We have four tunnel groups and have our group urls set up as 'https://subdomain.domain.com', if I don't add a base-url it looks for 'http://fqdn/saml...' and when I do add a base-url it looks for 'https://domain.com/saml...'. I have the config in Azure set up just like it shows in this guide and I have verified that the URLs are upper/lowercase where needed and using https, I have users assigned to the tunnel group that I'm testing, and have checked the saml metadata on the ASA which has the incorrect URL (http://fqdn/saml...). I'm obviously missing something simple. We're using a FirePower 2110 FTD with ASA 9.14 installed managed by ASDM and using Microsoft Authenticator for MFA.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@MaErre21325 hello dear
yes you need to create different Enterprise app for each tunnel group
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: