- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ASA Cut Through (Authentication) Proxy Configuration and Examples
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-14-2011 08:52 AM - edited 03-08-2019 06:38 PM
- Authentication Proxy Overview
- Authentication Proxy Configuration
- Authentication Proxy Troubleshooting Commands
- Integration with ACS
- Radius Authentication
Authentication Proxy Overview
Authentication proxy is a feature on the ASA platforms that allows a network administrator to force users to authenticate to the ASA before users are allowed access through the device. The ASA can authenticate these users using Radius, TACACS or local user databases.
Authentication proxy is used to control access through the ASA in a more granular and user based fashion.
Authentication Proxy Configuration
The following configuration lines will set up authentication proxy for HTTP connections:
hostname(config)# aaa-server TACACS protocol tacacs+
hostname(config)# aaa-server TACACS (inside) host 10.0.0.100
hostname(config-aaa-server-host)# key CISCO
hostname(config)# access-list AUTH_ACL extended permit tcp any any eq 80
hostname(config)# aaa authentication match AUTH_ACL inside TACACS
This configuration will have the ASA intercept all HTTP requests made outbound by inside users. Specifically, if users use Firefox, they will receive a popup window like below:

Users of Internet Explorer will see the following window:

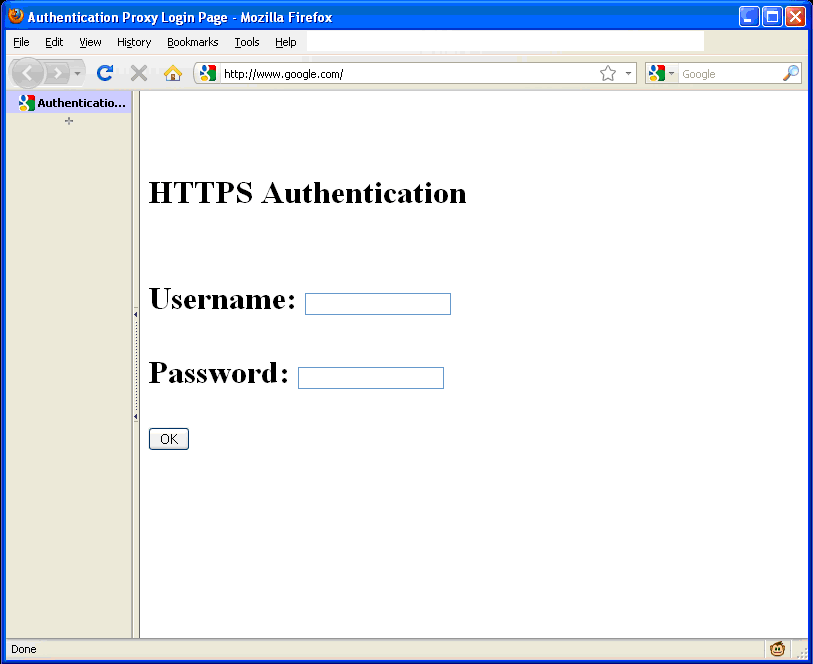
The network requirements may require HTTPS authenication for web based authentication proxy. If that is the case, run the following command:
hostname(config)# aaa authentication secure-http-client
Using the above command, the authentication page will now look like:
Authentication Proxy Troubleshooting Commands
To check the current uauth database, use the show uauth command.
hostname# show uauth
Current Most Seen
Authenticated Users 1 1
Authen In Progress 0 2
user 'cisco' at 10.1.1.2, authenticated
absolute timeout: 0:05:00
inactivity timeout: 0:00:00
Additionally, the command test aaa authentication will test a user against the AAA server.
hostname# test aaa-server authentication RADIUS username cisco password cisco
Server IP Address or name: 10.1.1.1
INFO: Attempting Authentication test to IP address <10.1.1.1> (timeout: 12 seconds)
ERROR: Authentication Rejected: AAA failure
Integration with ACS
Radius Authentication
The ASA and Radius can work together using downloadable ACLs and authentication proxy to create per-user customizable access profiles. On the ASA, the following configuration is required:
hostname(config)# aaa-server RADIUS protocol radius
hostname(config)# aaa-server RADIUS (inside) host 10.0.0.100
hostname(config-aaa-server-host)# key CISCO
hostname(config)# access-list AUTH_ACL extended permit tcp any any eq 80
hostname(config)# aaa authentication match AUTH_ACL inside TACACS
hostname(config)# virtual http 10.0.0.200
hostname(config)# access-list INSIDE_INBOUND extended permit tcp any host 10.0.0.200 eq 80
hostname(config)# access-group INSIDE_INBOUND in interface inside per-user-override
In this condition, the user will be required to access http://10.0.0.200
where the ASA will prompt the user for authentication. Once the user enters the authentication username and password, the ASA will forward this information to the Radius server. The Radius server is configured to return a downloadable ACL via the class 26 vendor specific attribute. The ASA will download this ACL and install it into its database specific to this user.
The outputs from a successful authentication are included below:
hostname(config)# show uauth
Current Most Seen
Authenticated Users 1 1
Authen In Progress 0 2
user 'cisco' at 10.1.1.2, authenticated
access-list #ACSACL#-IP-cisco-4d30a35b (*)
absolute timeout: 0:05:00
inactivity timeout: 0:00:00
The associate ACL lines are included below:
access-list #ACSACL#-IP-cisco-4d30a35b; 3 elements; name hash: 0x34134156 (dynamic)
access-list #ACSACL#-IP-cisco-4d30a35b line 1 extended permit tcp any any eq www (hitcnt=1) 0x3f7a6230
access-list #ACSACL#-IP-cisco-4d30a35b line 2 extended permit tcp any any eq netbios-ssn (hitcnt=0) 0xbdefa208
access-list #ACSACL#-IP-cisco-4d30a35b line 3 extended permit icmp any any (hitcnt=0) 0x25be1e4f
In the above example, the users cannot get out to the internet before authenticating via authentication proxy. After authenticating, the user is able to access all network resources using HTTP, Netbios and ICMP.
The above example can be used when trying to mitigate the spread of a worm that uses TCP port 139 as its communication medium. As a result, the network policy dictates that all computers must manually authenticate before they can obtain network access.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have this working with Microsoft RADIUS server however I only want to restrict access to one server sitting in the DMZ using this method and once users authenticate they can RDP to the server. When I apply all the settings I lose all access other than just to this server. Can this be done for one particular server in DMZ and rest of the traffic to the Internet stays the way it is?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: