NOTE: Check out
How to Format Your Document from a Templatefor the HTML CODE to copy
Introduction
This simple example shows how to enforce process checks via Dynamic Access Policy (DAP) that specifies that
Vista machines must be running CSD Vault to allow the Clientless SSL VPN session to be established.
Configuration
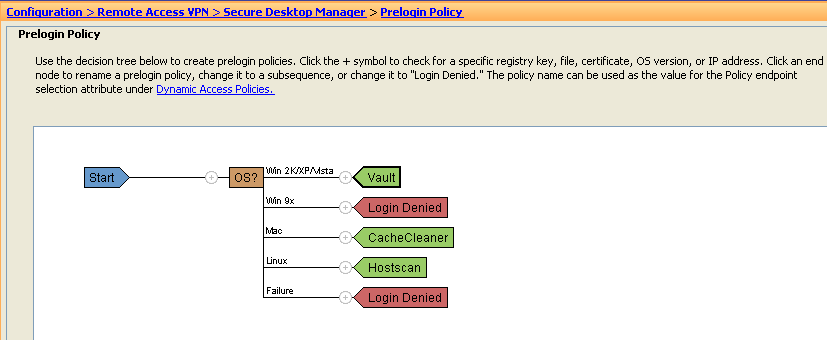
1) In ASDM, under Configuration-Remote Access VPN-Secure Desktop Manager-Prelogin Policy, define Prelogin check(s) .
We chose a simple OS check for Vista and a policy name called Vault. Other types of checks or nested checks can be performed depending on the granularity of the posture assessment desired.
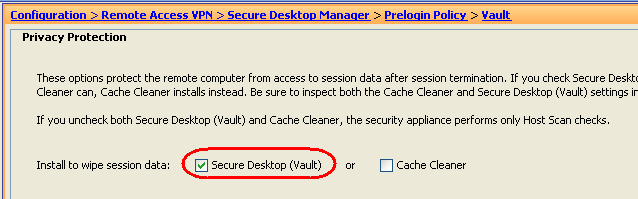
2) In ASDM, under Configuration-Remote Access VPN-Secure Desktop Manager-Prelogin Policy-Vault, select the functionality the Vault
policy will carry out. Choose the Secure Desktop (Vault) option.
3)In ASDM, under Configuration-Remote Access VPN-Secure Desktop Manager-Host Scan,define the process(es) that represent the Vault.
Note: CSD Vault spawns 2 processes: Main.exe and Storage.exe. Hostcan spawns Host.exe and Cache Cleaner spawns Cleaner.exe.
We chose 2 process IDs(names) for the 2 Vault processes.

4) In ASDM, under Configuration-Remote Access VPN-Clientless SSL VPNAccess -Dynamic Access Policies, definea DAP policy with the required checks
In our example we assume the following:
The VPN remote access will use Active Directory for authentication:
The AAA attribute verifies the user is part of the AD's Employees group
The endpoint.process attributes verifies that CSD is running
The endpoint.os check attribute verifies that only Vista machines meet this DAP policy

5) The DAP policy checks represented in LUA are as follows:
5540-1(config)# debug menu dap 2
DAP record [ check-if-Vault-is-running ]:
(EVAL(aaa.ldap.memberOf,"EQ","Employees","caseless")) and ((EVAL(endpoint.os.version,"EQ","Windows Vista","string"))) and ((EVAL(end
point.process["CSD-Main.exe"].exists,"EQ","true","string")) and (EVAL(endpoint.process["CSD-Storage.exe"].exists,"EQ","true","string
")))
Related Information