- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ASA Smart Call Home: Using Call-Home to automatically bring up Dynamic IPSEC SAs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 03-08-2011 06:01 AM
Objective:
- The remote access clients should be able to access clients behind the spoke end points at all times
- Devices behind each spoke should be able to communicate with devices behind other spokes at all times
Problem Decsription:
If the lan2lan tunnel between the headend(ASA-H) and any of the spoke ASAs(ASA-Sx) goes down:
- the remote access clients that connect to the headend are not able to reach the devices behind the spoke ASA.
- devices behind other spokes will not be able to to communicate with devices behind that particular spoke
The reason they will not be able to communicate is because an IPSEC SA cannot be initiated from the side that has a dynamic crypto map.
Scenario:
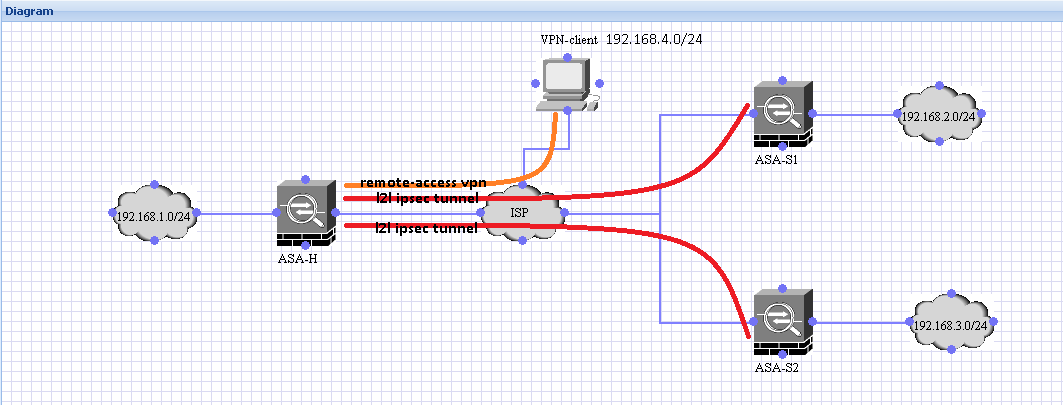
Configuration on ASA-H:
hostname ASA-H
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Ethernet0/0
nameif inside
security-level 100
ip address 192.168.1.1 255.255.255.0
!
interface Ethernet0/1
nameif outside
security-level 0
ip address 1.1.1.1 255.255.255.0
!
//some commands missing
!
boot system disk0:/asa822-k8.bin
same-security-traffic permit intra-interface
//some commands missing
!
ip local pool vpnpool 192.168.4.1-192.168.4.254 mask 255.255.255.0
route outside 0.0.0.0 0.0.0.0 1.1.1.2 1
!
group-policy clientgroup internal
group-policy clientgroup attributes
vpn-idle-timeout 20
split-tunnel-policy tunnelall
!
crypto ipsec transform-set ASA-H esp-des esp-md5-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto dynamic-map ASA-H 1 set transform-set ASA-H
crypto map outside 65535 ipsec-isakmp dynamic ASA-H
crypto map outside interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
no crypto isakmp nat-traversal
crypto isakmp disconnect-notify
!
management-access inside
!
username cisco password ffIRPGpDSOJh9YLq encrypted
tunnel-group DefaultL2LGroup ipsec-attributes
pre-shared-key *****
tunnel-group DefaultRAGroup ipsec-attributes
isakmp keepalive threshold 10 retry 2
tunnel-group remote type ipsec-ra
tunnel-group remote general-attributes
address-pool vpnpool
authentication-server-group none
default-group-policy clientgroup
tunnel-group remote ipsec-attributes
pre-shared-key *****
!
class-map inspection_default
match default-inspection-traffic
!
//some command missing
prompt hostname context
:end
Configuration on ASA-S1:
hostname ASA-S1
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Ethernet0/0
nameif inside
security-level 100
ip address 192.168.2.1 255.255.255.0
!
interface Ethernet0/1
nameif outside
security-level 0
ip address 3.3.3.1 255.255.255.0
!
//some commands missing
!
boot system disk0:/asa822-k8.bin
!
access-list cryacl extended permit ip 192.168.2.0 255.255.255.0 192.168.0.0 255.255.0.0
!
//some commands mising
!
route outside 0.0.0.0 0.0.0.0 3.3.3.2 1
!
crypto ipsec transform-set test esp-des esp-md5-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto map outside 1 match address cryacl
crypto map outside 1 set connection-type originate-only
crypto map outside 1 set peer 1.1.1.1
crypto map outside 1 set transform-set test
crypto map outside interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
no crypto isakmp nat-traversal
crypto isakmp disconnect-notify
!
management-access inside
!
tunnel-group DefaultL2LGroup ipsec-attributes
pre-shared-key *****
!
//some commands missing
prompt hostname context
:end
Configuration on ASA-S2:
hostname ASA-S2
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Ethernet0/0
nameif inside
security-level 100
ip address 192.168.31 255.255.255.0
!
//some commands missing
!
boot system disk0:/asa822-k8.bin
!
access-list cryacl extended permit ip 192.168.30 255.255.255.0 192.168.0.0 255.255.0.0
!
//some commands missing
!
route outside 0.0.0.0 0.0.0.0 4.4.4.2 1
!
dynamic-access-policy-record DfltAccessPolicy
!
crypto ipsec transform-set test esp-des esp-md5-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto map outside 1 match address cryacl
crypto map outside 1 set connection-type originate-only
crypto map outside 1 set peer 1.1.1.1
crypto map outside 1 set transform-set test
crypto map outside interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
no crypto isakmp nat-traversal
crypto isakmp disconnect-notify
!
management-access inside
!
tunnel-group DefaultL2LGroup ipsec-attributes
pre-shared-key *****
!
//some commands missing
prompt hostname context
:end
Solutions:
- Setting up a Continuous Ping
The easiest way to resolve this issue is to have continuous traffic going through the tunnels. The traffic needs to match the crypto access-lists for the SAs that need to be kept alive. One way to accomplish this would be to set up a device behind each spoke ASA(ASA-Sx) to continuously ping the internal interfaces of all the ASAs. Managament access needs to be enabled on all ASAs. The downside to this is that often the network is such that there are only client machines behind the spoke ASA, and it isn't feasible to have the client machine on 24x7 just to run pings to keep an SA alive. Perhaps a neater solution to this is using the CALL-Home feature introduce in ASA software v8.2.2. Using the smart call home feature, we can create a snapshot of commands that the ASA is forced to execute at a periodic interval. Thus by using this feature, and enabling Management Access on all the inside interfaces of the ASAs we can keep the SAs alive.
The commands that need to be added to the spoke ASAs are:
call-home
no alert-group inventory
alert-group-config snapshot
add-command "ping inside 192.168.1.1" // use the add-command to configure all the commands that you would like to execute automatically
add-command "ping inside 192.168.x.1" // to bring up the SAs between two spokes.
contact-email-addr <dummy-mail-address> // the email address can be a dummy value as we do not require any reports to be sent after the commands are executed.
mail-server <dummy-mailserver-ipaddress> priority 1
profile ping
destination address email <dummy-mail-address>
destination transport-method email
subscribe-to-alert-group snapshot periodic interval 1
Configuration on ASA-H: no changes
Configuration on ASA-S1:
hostname ASA-S1
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Ethernet0/0
nameif inside
security-level 100
ip address 192.168.2.1 255.255.255.0
!
//some commands missing
!
boot system disk0:/asa822-k8.bin
!
access-list cryacl extended permit ip 192.168.2.0 255.255.255.0 192.168.0.0 255.255.0.0
!
//some commands missing
!
route outside 0.0.0.0 0.0.0.0 3.3.3.2 1
!
dynamic-access-policy-record DfltAccessPolicy
!
crypto ipsec transform-set test esp-des esp-md5-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto map outside 1 match address cryacl
crypto map outside 1 set connection-type originate-only
crypto map outside 1 set peer 1.1.1.1
crypto map outside 1 set transform-set test
crypto map outside interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
no crypto isakmp nat-traversal
crypto isakmp disconnect-notify
!
management-access inside
!
tunnel-group DefaultL2LGroup ipsec-attributes
pre-shared-key *****
!
//some commands missing
!
service call-home
call-home
no alert-group inventory
alert-group-config snapshot
add-command "ping inside 192.168.1.1"
add-command "ping inside 192.168.3.1"
contact-email-addr test@cisco.com
mail-server 172.18.254.93 priority 1
profile CiscoTAC-1 // default profile configured on all devices
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
profile ping
destination address email dummy@cisco.com
destination transport-method email
subscribe-to-alert-group snapshot periodic interval 1
:end
Configuration on ASA-S2:
hostname ASA-S2
enable password 8Ry2YjIyt7RRXU24 encrypted
passwd 2KFQnbNIdI.2KYOU encrypted
names
!
interface Ethernet0/0
nameif inside
security-level 100
ip address 192.168.31 255.255.255.0
!
interface Ethernet0/1
nameif outside
security-level 0
ip address 4.4.4.1 255.255.255.0
!
// some commands missing
!
boot system disk0:/asa822-k8.bin
!
access-list cryacl extended permit ip 192.168.30 255.255.255.0 192.168.0.0 255.255.0.0
!
// some commands missing
!
route outside 0.0.0.0 0.0.0.0 4.4.4.2 1
!
dynamic-access-policy-record DfltAccessPolicy
!
crypto ipsec transform-set test esp-des esp-md5-hmac
crypto ipsec security-association lifetime seconds 28800
crypto ipsec security-association lifetime kilobytes 4608000
crypto map outside 1 match address cryacl
crypto map outside 1 set connection-type originate-only
crypto map outside 1 set peer 1.1.1.1
crypto map outside 1 set transform-set test
crypto map outside interface outside
crypto isakmp enable outside
crypto isakmp policy 10
authentication pre-share
encryption des
hash md5
group 2
lifetime 86400
no crypto isakmp nat-traversal
crypto isakmp disconnect-notify
!
management-access inside
!
tunnel-group DefaultL2LGroup ipsec-attributes
pre-shared-key *****
!
//some commands missing
!
service-policy global_policy global
prompt hostname context
service call-home
call-home
no alert-group inventory
alert-group-config snapshot
add-command "ping inside 192.168.1.1"
add-command "ping inside 192.168.2.1"
contact-email-addr test@cisco.com
mail-server 172.18.254.93 priority 1
profile CiscoTAC-1 // default profile configured on all devices
no active
destination address http https://tools.cisco.com/its/service/oddce/services/DDCEService
destination address email callhome@cisco.com
destination transport-method http
subscribe-to-alert-group diagnostic
subscribe-to-alert-group environment
subscribe-to-alert-group inventory periodic monthly
subscribe-to-alert-group configuration periodic monthly
subscribe-to-alert-group telemetry periodic daily
profile ping //profile that
destination address email dummy@cisco.com
destination transport-method email
subscribe-to-alert-group snapshot periodic interval 1
:end
Alternatively, the following enhancement request #CSCtn29607 has also been filed to modify the behavior of SLA monitoring so as to allow SLA monitoring to source pings from interfaces that have management access enabled on them. If you would like to see this feature implemented, please attach this enhancement request to your service request and get in touch with your account team.
2. EZVPN
Apart from this solution the other way that this can be resolved involves an overhaul of the design. Instead of using dynamic crypto maps, the ASAs need to be configured for EzVPN. The previous link provides the configuration guide for EzVPN. The only downside to EzVPN is only ASA5505s can be configured as EzVpn clients, so in this case all the spokes will have to be ASA5505s.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Could you have used following commands under group-policy DfltGrpPolicy to do the same job?
vpn-session-timeout none
vpn-idle-timeout none
I am not sure if it would have worked for l2l VPN.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The session timeout values might be helpful if the tunnel was already up, however in cases where the connectivity between the two peers itself goes down, the tunnel itself will be down. In this case in order to bring up the tunnel the only way to resolve the issue would be by running traffic that matches the crypto acls.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: