- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ASA: SSL VPN Certificate Authentication per Tunnel Group
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
12-02-2009 02:00 PM - edited 08-27-2017 10:54 PM
- Introduction
- Configuration CLI
- Configuration via ASDM
- Supported Modes
- Syslogs
- AnyConnect and Clientless WebVPN user behavior when using Certificates for Authentication
- Certificate Authentication for ASDM administrative sessions
- Cisco Secure Desktop (CSD)
- Scenario 2
- Solution:
- Documentation
- Source Discussion
Pardon for the pictures are not displaying well in the html version of the doc.
Select "Views as PDF" from the Actions box on the right to getter better picture clarity.
Introduction
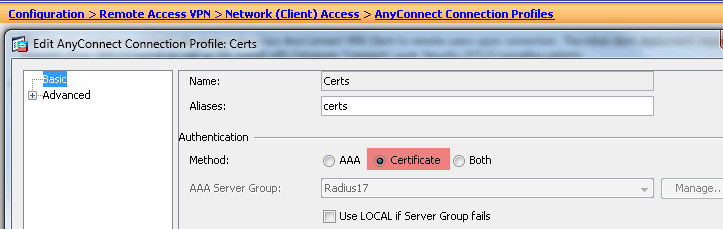
Enables certificate authentication to occur based on tunnel-group configuration, rather than global configuration.
Certificate Authentication per Tunnel Group (aka.referred to Connection Profile in ASDM) is a new feature introduced the ASA 8.2.1 release. It's goal is to avoid prompting all SSL VPN endpoints (Clientless and AnyConnect) for a certificate when it is unnecessary to do so.
In ASA releases prior to 8.2.x , when client certificate authentication is enabled , it is a global setting controlled with the '''ssl certificate-authentication interface ''<interface>'' port ''<portnum>''''' CLI. When enabled it would force all SSL VPN endpoints to see the certificate popup asking for a certificate. Users who wished to connect to tunnel groups using only AAA had to click Cancel or choose a certificate to get around the popup.
Configuration CLI
No new CLI syntax was added to the ASA. Only the semantics of existing commands.
- SSL CLI Commands
The key to this feature is that the '''ssl certificate-authentication''' command is no longer needed. When the '''ssl certificate-authentication''' command is configured, all connections to the specified interface and port are asked for a certificate.
ssl certificate-authentication interface outside port 443
Per-tunnel-group certificate authentication is enabled automatically when that CLI is removed.
no ssl certificate-authentication interface outside port 443
'''Note:''' Leaving the '''ssl certificate-authentication interface ''<interface>'' port ''<portnum>''''' CLI enabled will result in the exact same functionality as pre-8.2.x ASA.
- CLI Commands to enable certificate-authenticated HTTP (ASDM) sessions
The '''http authenticate-certificate ''<interface>''''' command was added back to 8.2.1 (it was removed in 8.0) to enable configuration for ASDM connections. This command has the same syntax as in 8.0.
http authenticate-certificate outside
- Tunnel-Group CLI Commands
The '''authentication''' command is used on a tunnel-group to specify that the incoming connection is to be authenticated via a certificate.
tunnel-group <group-name> webvpn-attributes
authentication certificate
Configuration via ASDM
ASDM panels:
Configuration > Remote Access VPN > Network (Client) Access > AnyConnect Connection Profiles-Basic (Authentication Method)
Configuration > Remote Access VPN > Clientless SSL VPN Access > Connection Profiles-Basic (Authentication Method)
Supported Modes
This feature is supported in all modes.
Troubleshooting / Debugging
No new '''show''' commands were added. However, a single counter was added to '''show counters'''
* Protocol: SSLNP
* Name: SSL forced certifificate on
This counter is incremented each time an address is added to the ''Forced Certificate Authentication'' database (FCADB).
Syslogs
No new syslogs were added.
=== Debugs ===
Debug commands were added to the SSL menu.
The following command displays the FCADB that is used on the ASA to force certain clients (e.g. AnyConnect) to always use certificate authentication.
debug menu ssl 2
The following command adds an IPv4 address to the FCADB:
debug menu ssl 3 ''<ip-addr>''
AnyConnect and Clientless WebVPN user behavior when using Certificates for Authentication
Although AnyConnect and Clientless WebVPN are both affected by this new feature the AnyConnect user experience is mostly unchanged since it does not prompt the user for a certificate.
Update: AnyConnect has since added capability to prompt the user for which certificate to use to authenticate the VPN session, so the behavior will be essentially the same as for the Clientless/browser session, when the option "Disable Automatic Certificate Selection" Preferences (Part 2) parameter is checked in the AnyConnect profile.
The tunnel-group (aka Connection Profile) settings to control authentication will remain unchanged and can be set for any of the following:
- Standard AAA only, no digital certificates
tunnel-group myaaaGroup webvpn-attributes
authentication aaa
- Digital certificates only, no standard AAA
tunnel-group mycertsGroup webvpn-attributes
authentication certificate
- Both AAA and Digital certificates
tunnel-group mycerts-aaaGroup webvpn-attributes
authentication certificate aaa
The table below indicates what the user experience will be for each client/connection type combination.
Update: AnyConnect has since added capability to prompt the user for which certificate to use to authenticate the VPN session, so the behavior will be essentially the same as for the Clientless/browser session, when the option "Disable Automatic Certificate Selection" Preferences (Part 2) parameter is checked in the AnyConnect profile.
Certificate Authentication for ASDM administrative sessions
ASDM certificate authentication will still be controlled by the ssl certificate-authentication CLI when it is enabled.
However, when ssl certificate-authentication CLI is NOT configured a new command (covered below) will be used for this.
Pre- ASA 8.2.x ASDM with Certificate authenticaiton behavior
ASDM on port 443 - ASDM were required to deal with the cert popup.
ASDM on port other than 443
# ASDM could operate with aaa-only or no aaa without seeing the cert popup
# ASDM could be prompted for cert auth separate from WebVPN using the ssl certificate-authentication CLI on whatever port ASDM (http server enable) was configured for.
Post ASA 8.2.x ASDM behavior
ASDM certificate authentication will be controlled using the new CLI - '''http authentication-certificate ''<interface>'''''. This new CLI will default to being disabled, having it enabled on an interface will cause ASDM connections to see a cert popup when connecting.
http authentication-certificate outside
Cisco Secure Desktop (CSD)
With the old ssl certificate-authentication setting, accessing CSD screens used to prompt for client certificate. This will no longer be the case, users will now be able to browse (or be redirected) to these URL's without a cert popup.
Local CA Certificates
When enrolling for a new client certificate, the login page where users enter username and One Time Password (OTP) to download their certificate would prompt for client certificate. As a result, users were required to cancel out of the cert popup or choose a cert (if one existed) just to get to the enrollment page. Now, with the new behavior, browsing to the Local CA enrollment page now works without a cert popup.
Scenario 2
User wishes to implement setup as shown in diagram. User needs help for configuring the same:
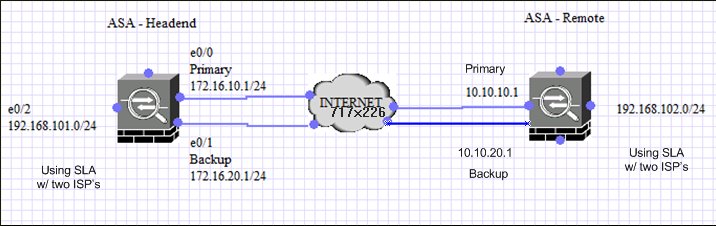
Solution:
User can refer the below link and configure the ASA's @ Head end and Tailend accordingly to your requirement.
You need to tweak the given example configuration similar with both the ends..dual ISP's @ both the ends in your scenario:
example link
Documentation
Several technical notes on configuring certificates authentication between Cisco VPN remote access session types and ASA5500 security applicances can be found at http://www.cisco.com/en/US/partner/products/ps6120/prod_configuration_examples_list.html
Here's an example:
ASA 8.x: AnyConnect SSL VPN CAC-Smart Cards Configuration for Windows
Source Discussion
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
This works greate except if you're using SCEP certificate enrollment. I'm currently tracking a bug that forces me to go back to the legacy 'ssl certificate-authentication interface...' command when using SCEP.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for this info.
Once thing i have noticed that is annoying me is that once you enable certificate authentication it must be used for all interfaces.
If you enable certificate and you wish to also use username and password this can also not be done on a per interface basis. If i want certificate only on inside and certificate and username and password via AAA for the outside interface i can't.
Even if you enable per interface AAA it doesn't work unless you enable Certificate and AAA globally in which case all interfaces use AAA.
Anyone know a work around for this.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I am having issues trying to create/deploy a user certificate. Is there any documentation on how to create the user certificate? What attributes do I provide to the user certificate.
I am using Microsoft Active Directory Certificate Services on Windows 208 R2. The Microsoft CA has authority and has issued a cert to the ASA. When I login using a remote access VPN with AAA, the user is asked to accept the ASA certificate issued by the microsoft CA. I am able to login successfully using that remote access vpn. However, trying to configure a different RA-VPN using certificate only auth results in a "Certificate Validation Failure" message.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have an SSL certificate alarm from PRTG that correctly highlights the "Unable to check revocation status"
with <sh crypto ca certificates> I can see that the issuing or root certificate authority or the root certificate authority is available to be queried.
I can also see the certificate via Cisco ASDM
>Configuration>VPN remote access>Certificate management>CA certificates.
I don't understand why I've been getting this alarm for a week on 3 of the 20 ASA firewalls.
I use the following command on the firewall in the CLI and if I import a firewall rule from the firewall and then perform a deployment, the parameter is overwritten: ssl trustp-point My_trustpoint
conf t
dynamic-access-policy-confi activate
vpn-addr-assign local reuse-delay 0
no ssl trust-point <My_trustpoint>
I don't understand why (CSM) Cisco Security Manager keeps deleting the last command line and unfortunately, I haven't found the corner of the CSM where this is configured....
This is probably the reason why messages appear in the prtg, because the verified certificate authority is not the right one or it is, by default, self-signed certificates on firewalls.
Unfortunately, the chain is not routed to the Internet". Unable to resolve the domain name" is the message I received from ssllabs.com.
Is there a way to validate or compare my parameters?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: