- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ASR-VASI: Step by Step Configuration
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
11-04-2013
11:50 AM
- edited on
09-03-2017
09:27 PM
by
Akshay Raghoji
![]()
[toc:faq]
Documentation
This configuration example is meant to be interpreted with the aid of the official documentation from the configuration guide located here
http://www.cisco.com/en/US/docs/ios-xml/ios/sec_data_zbf/configuration/xe-3s/asr1000/conf-vasi.html
Prerequisite
Cisco IOS XE Release 2.6
Limitation
- Multiprotocol Label Switching (MPLS) traffic over VRF-Aware Software Infrastructure (VASI) interfaces is not supported.
- IPv4 and IPv6 multicast traffic is not supported.
-
VASI interfaces do not support the attachment of queue-based features. The following commands are not supported on Modular QoS CLI (MQC) policies that are attached to VASI interfaces:
- bandwidth (policy-map class)
- fair-queue
- priority
- queue-limit
- random-detect
- shape
- VASI 2000 pairs are not supported on Open Shortest Path First (OSPF).
Why VASI
When there is a need to apply services like FW, IPSec and NAT to traffic that flows across different VRF instances you need VASI. Essentially we are creating two HOPS within the router.
Topology

How VASI works
When an inter-VRF VASI is configured on the same device, the packet flow happens in the following order:
- A packet enters the physical interface that belongs to VRF1 (Gigabit Ethernet 0/0/0).
- Before forwarding the packet, a forwarding lookup is done in the VRF Green routing table. vasileft1 is chosen as the next hop, and the TTL value is decremented from the packet. The packet is sent to the egress path of vasileft1 and then automatically sent to the vasiright1 ingress path.
- When the packet enters vasiright1, a forwarding lookup is done in the VRF Red routing table, and the TTL is decremented again (second time for this packet).
- VRF Green forwards the packet to the physical interface, Gigabit Ethernet 0/0/2.
Case 1 - NAT/FW on a stick with VASI
"On a stick" means using just one interface on the router for the task. Now, how can we configure NAT/FW with one interface? We need an "ip nat inside" and "ip nat outside" interface right? With just one physical interface how can we configure NAT and FW. With VASI and PBR we can.
Topology
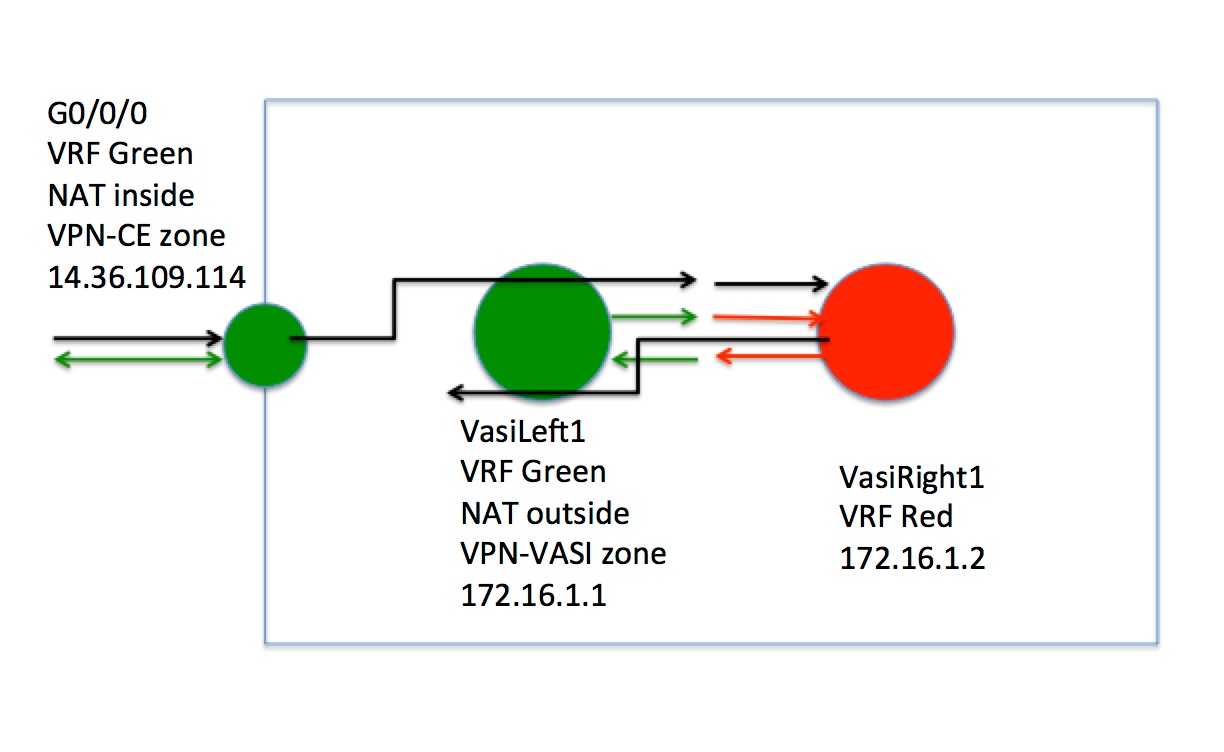
Step by Step Configuration
Create VRF defenition
ip vrf Green
rd 200:200
ip vrf Red
rd 100:100
Configure ZBF
Configure class-map and policy-map
class-map type inspect match-any CE-VASI-CL
match protocol tcp
match protocol udp
match protocol ftp
match protocol icmp
policy-map type inspect CE-VASI-POL
class type inspect CE-VASI-CL
inspect
class class-default
drop
Configure zones and zone pairs
In this case we are allowing all traffic from inside to outside as well as from outside to inside.
zone security VPN-CE
zone security VPN-VASI
zone-pair security CE-VASI source VPN-CE destination VPN-VASI
service-policy type inspect CE-VASI-POL
zone-pair security CE-VASI source VPN-VASI destination VPN-CE
service-policy type inspect CE-VASI-PO
Configure NAT
The inside interface is G0/0/0 and the outside interface is vasileft1 and NAT will be applied on these two interfaces before packets hit vasiright1 interface.
access-l 101 permit ip 10.10.10.0 0.0.0.255 10.10.10.0 0.0.0.255
ip nat pool POOL 20.20.20.1 20.20.20.255 netmask 255.255.255.0
ip nat inside source list 101 pool POOL vrf Green
Configure PBR
Using the same ACL that is used for NAT for configure the next-hop for the traffic hitting the physical G0/0/0 interface.
route-map CE-VASI permit 10
match ip address 101
set interface vasileft1
Configure the vasileft1 interface and add it to the zone
vasileft and vasiright are logical interface pairs, bonded using the idex values. Packets that hit vasileft1 automatically moves to the vasiright1 interface.
interface vasileft1
ip vrf forwarding Green
ip address 172.16.1.1 255.255.255.0
ip nat outside
no keepalive
zone security VPN-VASI
Configure the physical interface and add it to the zone and apply PBR
interface GigabitEthernet0/0/0
ip vrf forwarding Green
ip address 14.36.109.114 255.255.0.0
ip nat inside
ip policy route-map CE-VASI
zone-member security VPN-CE
negotiation auto
Configure the vasiright1 interface
interface vasiright1
ip vrf forwarding Red
ip address 172.16.1.2 255.255.255.0
no keepalive
Configure Route
The default route on VRF Green is pointing to a device outside of this router. This is the reason for applying a route-map to set the next-hop as vasileft1.
ip route vrf Green 0.0.0.0 0.0.0.0 14.36.109.1
ip route vrf Red 0.0.0.0 0.0.0.0 vasiright1
Show Commands
show vasi pair
kusankar-ASR1002#show vasi pair status 1
Pair name Left state Right state Pair state
------------------------------------------------------------------------------
VASIPair1 up up up
kusankar-ASR1002#
show run int
kusankar-ASR1002#sh run int vasiright1
Building configuration...
Current configuration : 102 bytes
!
interface vasiright1
ip vrf forwarding Red
ip address 172.16.1.2 255.255.255.0
no keepalive
end
show ip int
kusankar-ASR1002#sh ip interface vasileft1
vasileft1 is up, line protocol is up
Internet address is 172.16.1.1/24
Broadcast address is 255.255.255.255
Address determined by setup command
MTU is 9216 bytes
Helper address is not set
Directed broadcast forwarding is disabled
Multicast reserved groups joined: 224.0.0.251
Outgoing Common access list is not set
Outgoing access list is not set
Inbound Common access list is not set
Inbound access list is not set
Proxy ARP is enabled
Local Proxy ARP is disabled
Security level is default
Split horizon is enabled
ICMP redirects are always sent
ICMP unreachables are always sent
ICMP mask replies are never sent
IP fast switching is disabled
IP Flow switching is disabled
IP CEF switching is disabled
IP Null turbo vector
IP Null turbo vector
VPN Routing/Forwarding "Green"
Associated unicast routing topologies:
Topology "base", operation state is UP
IP multicast fast switching is enabled
IP multicast distributed fast switching is disabled
IP route-cache flags are Fast, CEF
Router Discovery is disabled
IP output packet accounting is disabled
IP access violation accounting is disabled
TCP/IP header compression is disabled
RTP/IP header compression is disabled
Probe proxy name replies are disabled
Policy routing is disabled
Network address translation is enabled, interface in domain outside
BGP Policy Mapping is disabled
Input features: Virtual Fragment Reassembly, NAT Outside, MCI Check
Output features: Post-routing NAT Outside
IPv4 WCCP Redirect outbound is disabled
IPv4 WCCP Redirect inbound is disabled
IPv4 WCCP Redirect exclude is disabled
Debug Commands
debug vasi events
debug vasi packets
debug vasi state
debug vasi elog
debug interface vasileft1
debug interface vasiright1
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
