- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Basic site to site VPN Template / Example ASA 8.4+ (IKEv1)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 11-20-2013 09:38 AM
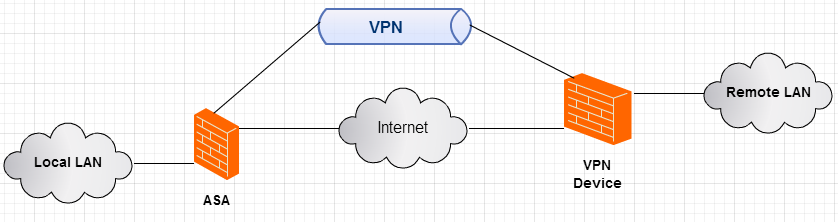
This will be for a basic setup, no policy NAT, no backup peers, using preshared keys having a similar topology to the one below:
!--find and replace <name> with the endpoint name/identifier, typicaly the site if it is a part of your organization, or company name if it is a partner
!--find and replace <peer ip address> with the remote end's public address
!--find and replace <key> with the pre-shared key
!--find and replace <crypto map name> with the name that is configured on your external interface (typicaly the interface will be named "outside"). You can verify the name by using the command "show run crypto map | in interface". If there are no crypto maps configured, you can use any name, but remember this will not only be for one tunnel but for all so try going with something generic, like <interface name>_crypto_map or just vpn.
!--find and replace <next avialable sequence number> with the lowest unused sequence number (see the output of the command "show run crypto map" to determine it), obviously if there is no cryptomap, you can use 1, or even better, use increments of 10 (start on 10, then 20, 30, etc).
!--find and replace <internal interface name> with the "nameif" of the interface going to your LAN, although it will typicaly be "inside" use the command "show ip" to verify (it may also be a DMZ depending on your needs)
!--find and replace <external interface name> with the "nameif" of the interface going to internet (or private circuit).
object-group network vpn-<name>-source
network-object <local network and subnet mask>
!-- add as many as needed
exit
object-group network vpn-<name>-destination
network-object <remote network and subnet mask>
!-- add as many as needed
exit
route <external interface name> <remote network and subnet mask> <next hop/default gate way ip of the external interface>
nat (<internal interface name>,<external interface name>) source static vpn-<name>-source vpn-<name>-source destination static vpn-<name>-destination vpn-<name>-destination route-lookup
access-list vpn-<name> permit ip object-group vpn-<name>-source object-group vpn-<name>-destination
!-- Note: The VPN filter is optional, so this part is not mandatory.
!-- Note 2: Remember that the filter ACL is configured as and inbound ACL on the external interface, so the source would be the remote network and your local one, the destination. The ACL then is applied bidirectionaly.
!-- use this format to limit the ports that your end can access on the other network:
access-list vpn-<name>-filter permit <tcp or udp> (remote host or subnet) eq <port> (local host or subnet)
!-- use this format to limit the ports that the remote end can access on your network:
access-list vpn-<name>-filter permit <tcp or udp> (remote host or subnet) (local host or subnet) eq <port>
!-- use this format to limit by hosts:
access-list vpn-<name>-filter permit ip (remote host or subnet) (local host or subnet)
group-policy gp<peer ip address> internal
group-policy gp<peer ip address> attributes
vpn-tunnel-protocol ikev1
!-- if no filter is to be used, use the command "vpn-filter none"
vpn-filter value vpn-<name>-filter
exit
tunnel-group <peer ip address> type ipsec-l2l
tunnel-group <peer ip address> general-attributes
default-group-policy gp<peer ip address>
tunnel-group <peer ip address> type ipsec-l2l
ikev1 pre-shared-key <key>
exit
!---Note: instead of creating one for each tunnel it would be better to see if you have one that matches the negotiated phase 2 parameters and use that have been agreed upon, use the command "show run crypto ipsec" to determine that.
crypto ipsec ikev1 transform-set <name> esp-<encryption algorithim can be: des, 3des, aes, aes-192 or aes-256> esp-<hashing algorithm, can be sha or md5>-hmac
crypto map <crypto map name> <next avialable sequence number> set peer <peer ip address>
crypto map <crypto map name> <next avialable sequence number> set ikev1 transform-set <name>
crypto map <crypto map name> <next avialable sequence number> match address vpn-<name>
!-- If PFS is to be used:
crypto map <crypto map name> <next avialable sequence number> set pfs group<agreed group can be 1,2, or 5; 2 is the default and just "set pfs" will set it to use it>
!-- If there is no crypto map on your external interface yet:
crypto map <crypto map name> interface <external interface name>
!--for the phase 1 settings, first check the command "show run crypto ikev1" for a policy that matches the agreed parameters, if there isn't one available, enter it this way:
crypto ikev1 policy <lowest available number>
ecryption <encryption algorithim can be: des, 3des, aes, aes-192 or aes-256>
hash <hashing algorithm, can be sha or md5>
group <Diffie-Hellman group selected, can be 1,2, or 5>
authentication pre-share
exit
!--if the "show run crypto ikev1" is blank, you will also need to enable it on the external interface:
crypto ikev1 enable <external interface name>
Without coments (to copy and paste on a text editor):
object-group network vpn-<name>-source
network-object <local network and subnet mask>
!-- add as many as needed
exit
object-group network vpn-<name>-destination
network-object <remote network and subnet mask>
!-- add as many as needed
exit
route <external interface name> <remote network and subnet mask> <next hop/default gate way ip of the external interface>
nat (<internal interface name>,<external interface name>) source static vpn-<name>-source vpn-<name>-source destination static vpn-<name>-destination vpn-<name>-destination route-lookup
access-list vpn-<name> permit ip object-group vpn-<name>-source object-group vpn-<name>-destination
access-list vpn-<name>-filter permit <tcp or udp> (remote host or subnet) eq <port> (local host or subnet)
access-list vpn-<name>-filter permit <tcp or udp> (remote host or subnet) (local host or subnet) eq <port>
access-list vpn-<name>-filter permit ip (remote host or subnet) (local host or subnet)
group-policy gp<peer ip address> internal
group-policy gp<peer ip address> attributes
vpn-tunnel-protocol ikev1
vpn-filter value vpn-<name>-filter
exit
tunnel-group <peer ip address> type ipsec-l2l
tunnel-group <peer ip address> general-attributes
default-group-policy gp<peer ip address>
tunnel-group <peer ip address> type ipsec-l2l
ikev1 pre-shared-key <key>
exit
crypto ipsec ikev1 transform-set <name> esp-<encryption algorithim can be: des, 3des, aes, aes-192 or aes-256> esp-<hashing algorithm, can be sha or md5>-hmac
crypto map <crypto map name> <next avialable sequence number> set peer <peer ip address>
crypto map <crypto map name> <next avialable sequence number> set ikev1 transform-set <name>
crypto map <crypto map name> <next avialable sequence number> match address vpn-<name>
crypto map <crypto map name> <next avialable sequence number> set pfs group<agreed group can be 1,2, or 5; 2 is the default and just "set pfs" will set it to use it>
crypto map <crypto map name> interface <external interface name>
crypto ikev1 policy <lowest available number>
ecryption <encryption algorithim can be: des, 3des, aes, aes-192 or aes-256>
hash <hashing algorithm, can be sha or md5>
group <Diffie-Hellman group selected, can be 1,2, or 5>
authentication pre-share
exit
crypto ikev1 enable <external interface name>
Configuration example based on the above template:
Asume that you are building a VPN to Google's public DNS (for some odd reason that we won't discuss) 8.8.8.8 with these specifications (I got the IPs by pinging Google's sites names):
| Your Company | ||
|---|---|---|
| Public IP | 1.1.1.1 | 8.8.8.8 |
| Phase 1 | AES 256, SHA, Group 2 | AES 256, SHA, Group 2 |
| Phase 2 | AES 256, SHA | AES 256, SHA |
| PFS | No | No |
| Networks | 192.168.10.0/24 10.10.10.0/24 | 8.8.8.8/32 74.125.224.128/25 |
| Ports | 192.168.10.10:3389 (TCP) 10.10.10.15:80 (TCP) 10.10.10.15:443 (TCP) | 8.8.8.8:53 (UDP) 74.125.224.182:443 (TCP) 74.125.224.167:443 (TCP) 74.125.224.167:80 (TCP) |
| Key | ASA2Google | ASA2Google |
Let's asume that your ASA's default gateway is 1.1.1.2 and when you run the suggested show commands you get:
asa# show ip
System IP Addresses:
Interface Name IP address Subnet mask Method
GigabitEthernet0/0 outside 1.1.1.1 255.255.255.252 CONFIG
GigabitEthernet0/1 inside 192.168.10.1 255.255.255.0 CONFIG
Current IP Addresses:
Interface Name IP address Subnet mask Method
GigabitEthernet0/0 outside 1.1.1.1 255.255.255.252 CONFIG
GigabitEthernet0/1 inside 192.168.10.1 255.255.255.0 CONFIG
asa#
asa#
asa# show run crypto map
crypto map vpn 10 set peer 208.87.35.103
crypto map vpn 10 set ikev1 transform-set ESP-3DES-SHA
crypto map vpn 10 match address vpn-random.com
crypto map vpn interface outside
asa#
asa#
asa# show run crypto ipsec
crypto ipsec ikev1 transform-set ESP-3DES-SHA esp-3des esp-sha-hmac
asa#
asa#
asa#
asa# show run crypto ikev1
crypto ikev1 enable outside
crypto ikev1 policy 5
authentication pre-share
encryption 3des
hash sha
group 2
lifetime 86400
asa#
Based on this output and the information given above you the find and replace with your text editor:
<name> to Google
<peer ip address> to 8.8.8.8
<key> to ASA2Google
<crypto map name> to vpn
<next avialable sequence number> to 20 (Following the increments of 10 thought)
<internal interface name> to inside
<external interface name> to outside
And you end up with something like this on your editor:
object-group network vpn-Google-source
network-object <local network and subnet mask>
!-- add as many as needed
exit
object-group network vpn-Google-destination
network-object <remote network and subnet mask>
!-- add as many as needed
exit
route outside <remote network and subnet mask> <next hop/default gate way ip of the external interface>
nat (inside,outside) source static vpn-Google-source vpn-Google-source destination static vpn-Google-destination vpn-Google-destination route-lookup
access-list vpn-Google permit ip object-group vpn-Google-source object-group vpn-Google-destination
access-list vpn-Google-filter permit <tcp or udp> (remote host or subnet) eq <port> (local host or subnet)
access-list vpn-Google-filter permit <tcp or udp> (remote host or subnet) (local host or subnet) eq <port>
access-list vpn-Google-filter permit ip (remote host or subnet) (local host or subnet)
group-policy gp8.8.8.8 internal
group-policy gp8.8.8.8 attributes
vpn-tunnel-protocol ikev1
vpn-filter value vpn-Google-filter
exit
tunnel-group 8.8.8.8 type ipsec-l2l
tunnel-group 8.8.8.8 general-attributes
default-group-policy gp8.8.8.8
tunnel-group 8.8.8.8 type ipsec-l2l
ikev1 pre-shared-key ASA2Google
exit
crypto ipsec ikev1 transform-set Google esp-<encryption algorithim can be: des, 3des, aes, aes-192 or aes-256> esp-<hashing algorithm, can be sha or md5>-hmac
crypto map vpn 20 set peer 8.8.8.8
crypto map vpn 20 set ikev1 transform-set Google
crypto map vpn 20 match address vpn-Google
crypto map vpn 20 set pfs group<agreed group can be 1,2, or 5; 2 is the default and just "set pfs" will set it to use it>
crypto map vpn interface outside
crypto ikev1 policy <lowest available number>
ecryption <encryption algorithim can be: des, 3des, aes, aes-192 or aes-256>
hash <hashing algorithm, can be sha or md5>
group <Diffie-Hellman group selected, can be 1,2, or 5>
authentication pre-shared
exit
crypto ikev1 enable outside
Next you delete the lines that you won't need from the editor, based on this scenario:
crypto map vpn 20 set pfs group<agreed group can be 1,2, or 5; 2 is the default and just "set pfs" will set it to use it>
crypto map vpn interface outside
crypto ikev1 enable outside
Now you add the information that is still missing based on your scenario (encryption and hash settings, IP addresses, etc):
object-group network vpn-Google-source
network-object 192.168.10.0 255.255.255.0
network-object 10.10.10.0 255.255.255.0
exit
object-group network vpn-Google-destination
network-object host 8.8.8.8
network-object 74.125.224.128 255.255.255.128
exit
route outside 74.125.224.128 255.255.255.128 1.1.1.2
route outside 8.8.8.8 255.255.255.255 1.1.1.2
access-list vpn-Google-filter permit udp host 8.8.8.8 eq 53 object-group vpn-Google-source
access-list vpn-Google-filter permit tcp host 74.125.224.182 eq 443 object-group vpn-Google-source
access-list vpn-Google-filter permit tcp host 74.125.224.167 eq 80 object-group vpn-Google-source
access-list vpn-Google-filter permit tcp host 74.125.224.167 eq 443 object-group vpn-Google-source
access-list vpn-Google-filter permit tcp object-group vpn-Google-destination host 192.168.10.10 eq 3389
access-list vpn-Google-filter permit tcp object-group vpn-Google-destination host 10.10.10.15 eq 80
access-list vpn-Google-filter permit tcp object-group vpn-Google-destination host 10.10.10.15 eq 443
crypto ipsec ikev1 transform-set Google esp-aes-256 esp-sha-hmac
crypto ikev1 policy 1
ecryption aes-256
hash sha
group 2
authentication pre-share
exit
In the end based on the parameters defined by the example and the sample configuration, the configuration on the text editor should be ready to copy and paste to the ASA, but before you enter it, and as a quick reminder, you should be on global configuration mode:
asa>
asa> enable
password: ********
asa#
asa# configure terminal
asa(config)#
Now that you've made sure that you are on global configuration mode, the configuration should look like this:
object-group network vpn-Google-source
network-object 192.168.10.0 255.255.255.0
network-object 10.10.10.0 255.255.255.0
exit
object-group network vpn-Google-destination
network-object host 8.8.8.8
network-object 74.125.224.128 255.255.255.128
exit
route outside 74.125.224.128 255.255.255.128 1.1.1.2
route outside 8.8.8.8 255.255.255.255 1.1.1.2
nat (inside,outside) source static vpn-Google-source vpn-Google-source destination static vpn-Google-destination vpn-Google-destination route-lookup
access-list vpn-Google permit ip object-group vpn-Google-source object-group vpn-Google-destination
access-list vpn-Google-filter permit udp host 8.8.8.8 eq 53 object-group vpn-Google-source
access-list vpn-Google-filter permit tcp host 74.125.224.182 eq 443 object-group vpn-Google-source
access-list vpn-Google-filter permit tcp host 74.125.224.167 eq 80 object-group vpn-Google-source
access-list vpn-Google-filter permit tcp host 74.125.224.167 eq 443 object-group vpn-Google-source
access-list vpn-Google-filter permit tcp object-group vpn-Google-destination host 192.168.10.10 eq 3389
access-list vpn-Google-filter permit tcp object-group vpn-Google-destination host 10.10.10.15 eq 80
access-list vpn-Google-filter permit tcp object-group vpn-Google-destination host 10.10.10.15 eq 443
group-policy gp8.8.8.8 internal
group-policy gp8.8.8.8 attributes
vpn-tunnel-protocol ikev1
vpn-filter value vpn-Google-filter
exit
tunnel-group 8.8.8.8 type ipsec-l2l
tunnel-group 8.8.8.8 general-attributes
default-group-policy gp8.8.8.8
tunnel-group 8.8.8.8 type ipsec-l2l
ikev1 pre-shared-key ASA2Google
exit
crypto ipsec ikev1 transform-set Google esp-aes-256 esp-sha-hmac
crypto map vpn 20 set peer 8.8.8.8
crypto map vpn 20 set ikev1 transform-set Google
crypto map vpn 20 match address vpn-Google
crypto ikev1 policy 1
ecryption aes-256
hash sha
group 2
authentication pre-share
exit
I hope that this example helps you make your VPN configuration without any issues, but please try not to put the final configurations of the example on your actual ASA! (most of the public IP addresses are valid and obtained through pings/nslookup)!
Just to wrap up, something very important that I almost missed. when you end your configuration:
asa# write memory
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for your info about VPN
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great post. Thanks for the template.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: