Cisco ETA feature (Encrypted Traffic Analysis) is a method of analysing encrypted data to detect malicious content and malware without decryption using machine learning.
To understand the process.
Two pieces are used in encrypted data to detect if there is malware carried inside the TLS Tunnel.
1--Initial Data Packet IDP: This element provides informations of the TLS handshake negociation between a client and a server.
The TLS Handshake messages are exchanged in clear text so they are unencrypted such as:
- TLS Version
- Ciphers
- Digital Certificates
- Public key of the server
ETA feature can use these informations as an indication of anormal activities. Self-Signed certificate can indicate a non-trusted server which can be a malicious website or C2C server.
2--Sequence of Packet Lengths and Times (SPLT): this element provides the lengths of packet exchanged between the client and the server, and the inter-arrival times of those packets.
ETA can create a reports with the packet lengths and times to analyse encrypted traffic and detect malicious activities.
By combining the IDP and SPLT informations. ETA can detect legitimate or normal traffic and anormal traffic with reports representing the TLS handshake negocation using IDP and packet lengths/arrival times which can indicate a connection from a C2C server.
Analyze IDP informations:
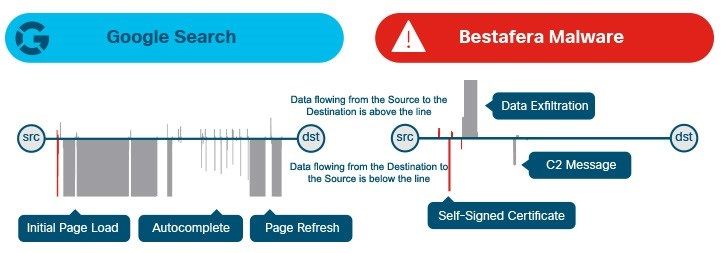
A normal encrypted traffic uses a digital certificate signed by legitimate CA (Certification of Authority) -> Google search at the right.
Anormal encrypted traffic uses a self-signed certificate -> graph at the left for Bestafera Malware.
Analyze SPLT informations:
The report for google search at the right -> displays few packets sent by the client to the server (above the horizontal line). The server responds back many packets containing the search results (below the horizontal line).
The report of anormal traffic at the left -> displays a lot of traffic sent by the client to the server (above the horizontal line), indicating anormal activities for outbound traffic which can indicate possible data exfiltration.
The next sequence of few packets is sent by the server to the client (below the horizontal line) with different interval time compared to the outbound traffic.
Mapping between the arrival times and packet sizes in both inbound and outbound and TLS handshake provide the ETA feature useful informations to differentiate between legitimate traffic and malicious data.