- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Cisco ISE & WLC - WPA2-PSK WLAN: Per-Device Passphrase (IPSK)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
03-29-2018 02:36 PM - edited 07-30-2020 06:59 AM
This document describes how Cisco ISE and the Identity PSK feature on the Cisco WLC can support a unique passphrase for each device on a WPA2-PSK WLAN. To date, Identity PSK implementation guides focused on singular authorization policies; ISE endpoint identity groups for dynamic (device profiling) or static classification of wireless devices.
Identity PSK
To learn about Identity PSK, its benefits, and how to configure the Cisco WLC; please read the AireOS 8.5 Identity PSK Feature Deployment Guide.
Identity PSK requires the wireless client's MAC address to be registered or profiled on the ISE server. WLAN association enforcement occurs on the WLC by comparing the client provided passphrase to the passphrase returned as an attribute-value response from the ISE server. Cisco ISE can send additional controls to the WLC in the response, such as VLAN ID, TrustSec SGT, and AireOS ACL name.
Use Cases
Why use per-device passphrases instead of shared passphrases? For many environments, the grouping of devices into endpoint identity groups and using a group passphrase simplifies operations, but the following use cases may benefit from per-device passphrases:
- Higher-Education
- Student Dormitory - Video Game Consoles, Digital Personal Assistants
- Classroom - Audio/Video Equipment, IoT Devices
- Building Management Systems
- Healthcare
- Personal Biomedical Devices
- Long-term Care - Video Game Consoles, Audio/Video Equipment
- Encrypted Guest Internet Service
- Manufacturing
- Temporary Field Technician Access
Solution Elements
- WLC - AireOS 8.5 or newer
- Identity PSK feature introduced in AireOS 8.5.
- RADIUS - Identity Services Engine 2.3 or newer
- Evaluation of endpoint custom attributes within the RADIUS authorization profile introduced in ISE 2.3.
ISE Configuration Instructions
Endpoint Customization
-
Open the Endpoint Custom Attributes page
-
Click on the Top Menu: Administration > Identity Management > Settings
-
Click on the Left Menu: Endpoint Custom Attributes
-
-
Create a new Custom Attribute
-
This will create a new endpoint variable, used for the passphrase in the ISE database.
-
The example utilizes a custom attribute named: iPSK:
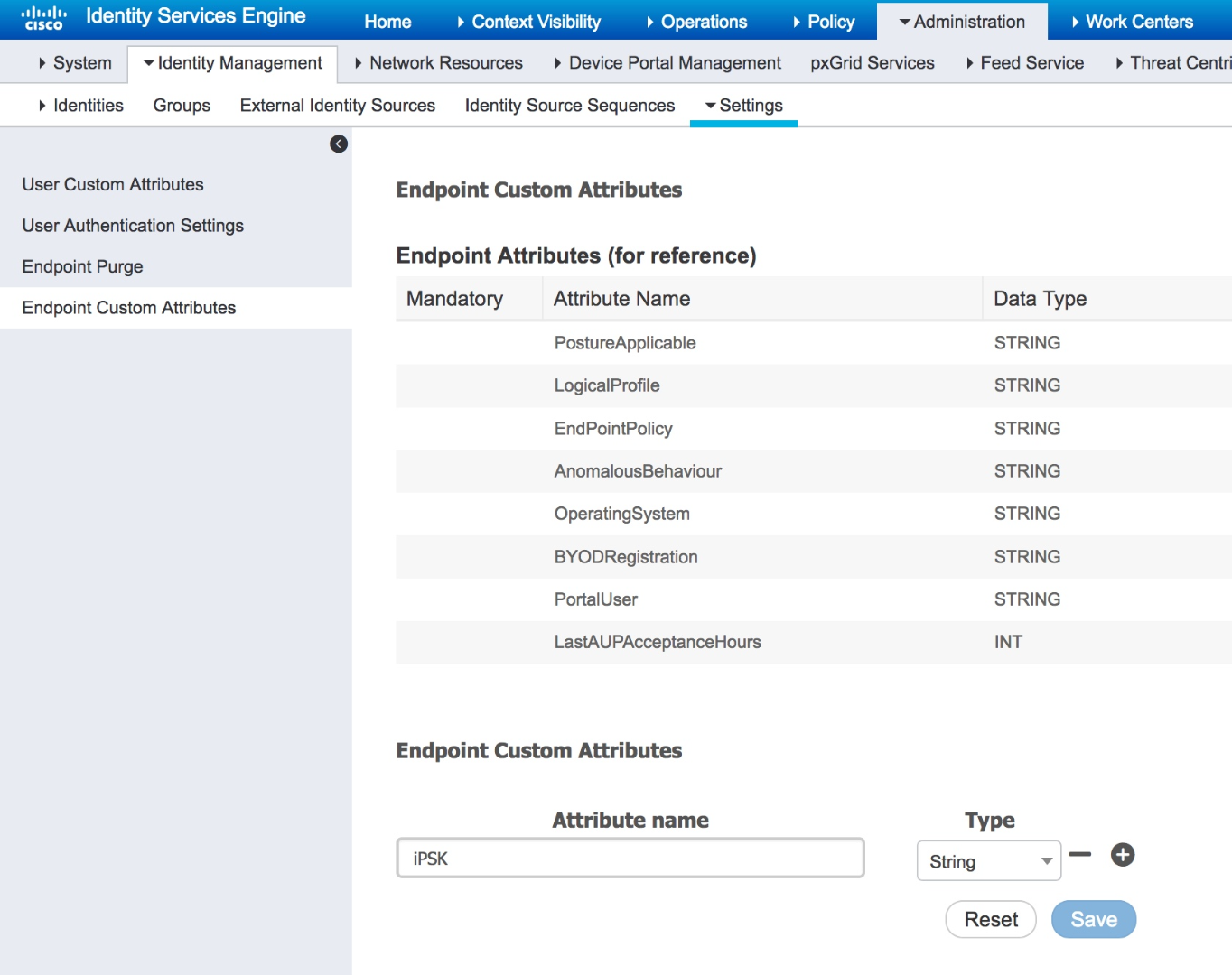
-
Be certain to cast the custom attribute as type "string."
-
-
Register the wireless endpoint using the ISE GUI
-
Click on the Top Menu: Context Visibility > Endpoints
-
Click on the "Plus Sign"
-
-
Input the endpoint's MAC address, then click Save.
- Assign a passphrase to an endpoint.
- Click on the newly created endpoint.
- Edit the endpoint
- Under the Custom Attribute section, add a passphrase to the endpoint. Prepend the passphrase with "psk=". The example utilizes "stacie12345" as the passphrase, and "psk=stacie12345" as the required response to the WLC:
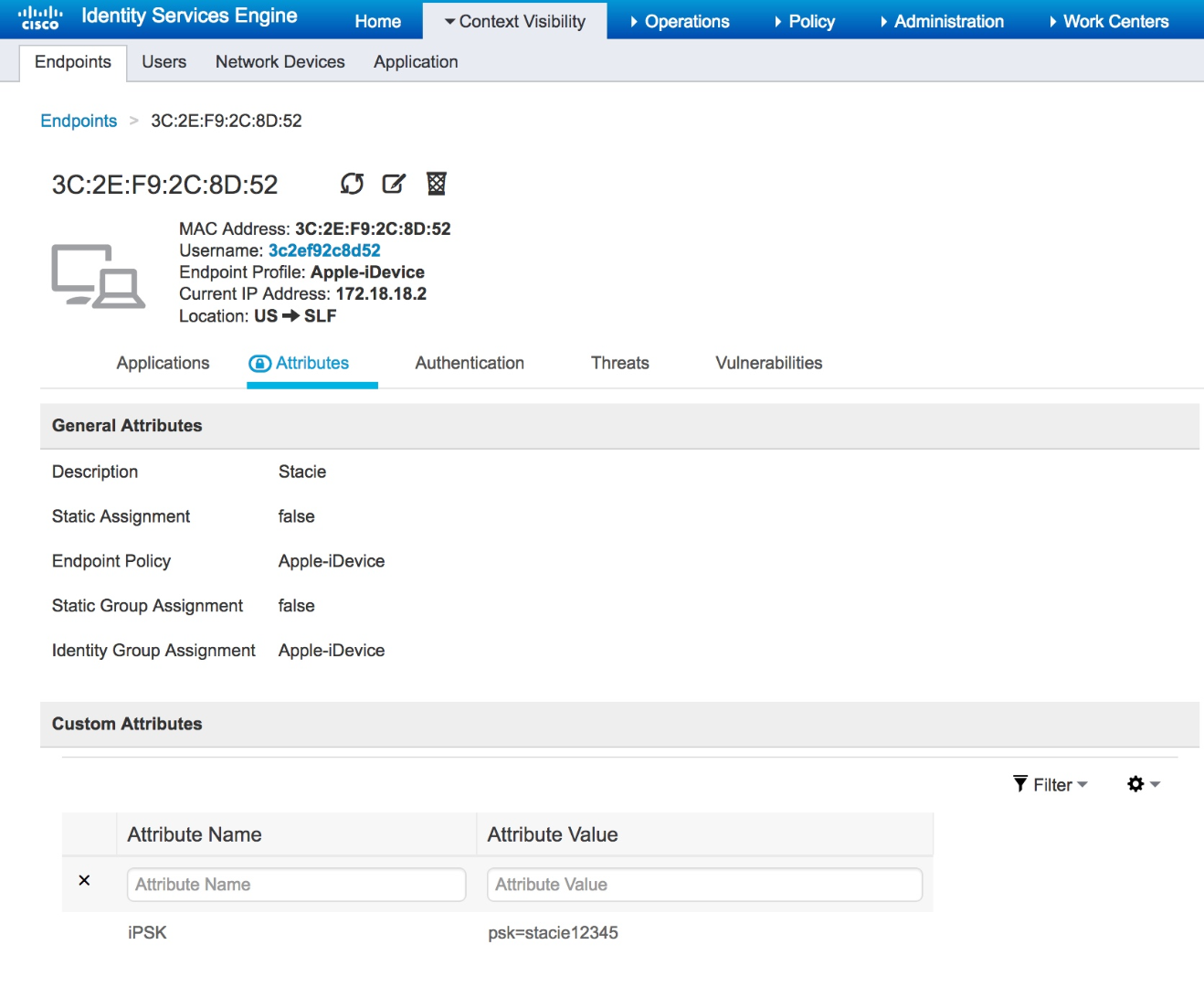
RADIUS Authorization Profile
- Locate the RADIUS Authorization Profiles
- Click on the Top Menu: Policy > Policy Elements > Results
- Click on the Left Menu: Authorization > Authorization Profile
- Create a new RADIUS Authorization Profile
- Click: Add
- Name the policy. The example uses the name: IdentityPSK
- Expand the Custom Attributes section.
- Create the first required response. This instructs the WLC to look for a ASCII passphrase.
- In the left-hand dropdown, search for: cisco-av-pair
- Select: cisco-av-pair--[1]
- In the right-hand dropdown, enter the following: psk-mode=ascii
- Create the second required response. This returns the endpoint passphrase created in previous section.
- In the left-hand dropdown, search for: cisco-av-pair
- Select: cisco-av-pair--[1]
- In the right-hand dropdown, select: EndPoints. Then select the custom endpoint attribute you created in the previous section. The example uses "iPSK" as the custom endpoint attribute:
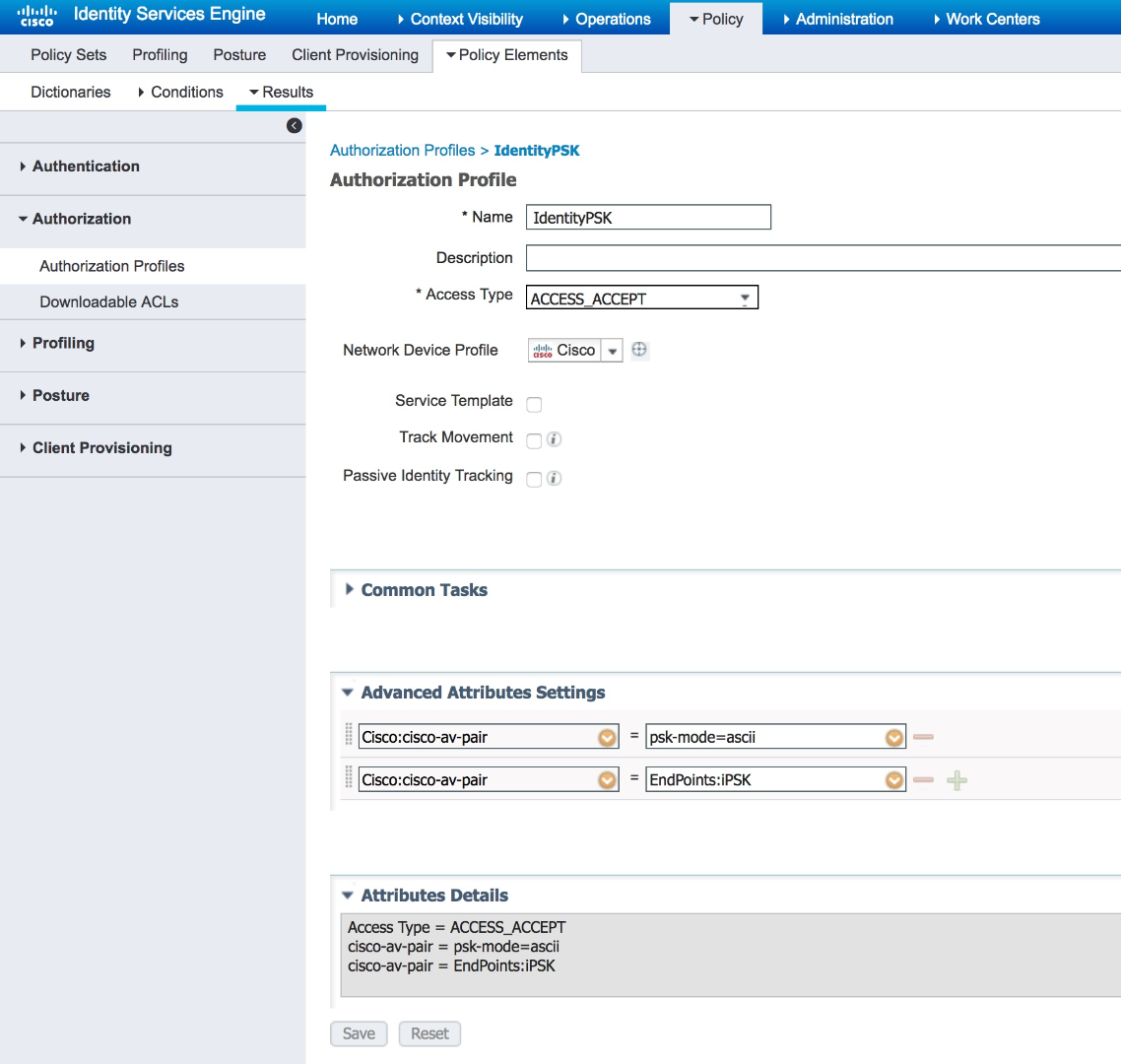
- Save the Authorization Profile.
RADIUS Authorization Policy
- Open the RADIUS Policy Set
- Click: Policy > Policy Set
- Select the Policy Set used for wireless authentication and authorization.
- Expand the Authorization Policy
- Create a new Authorization Policy
- Click on the "Plus Sign"
- Provide a meaningful rule name.
- Configure the match condition. The example utilizes the SSID name as the match condition:
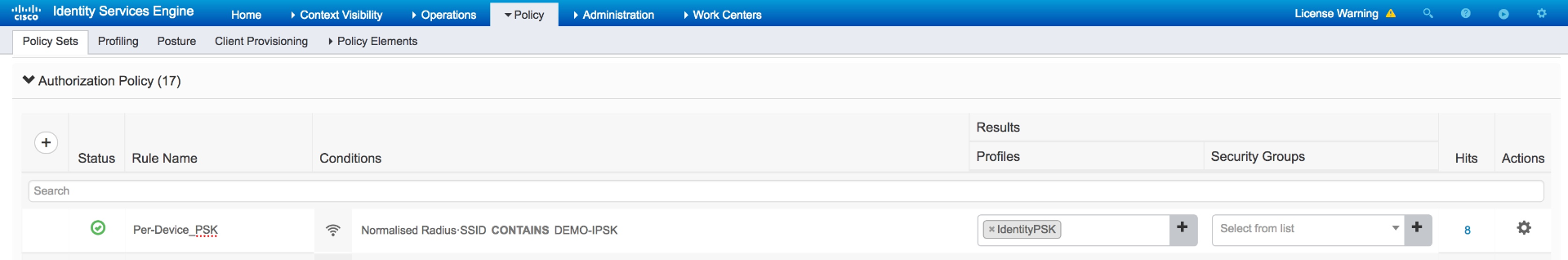
- Assign the newly created Authorization Profile as the RADIUS Result Profile.
- Save the Authorization Profile
Device Self-Registration
Access to the endpoint passphrase attribute via the Device Registration Portal on ISE is not supported.
To provide device self-registration, a custom web portal can be created - external to Cisco ISE. Cisco ISE provides a RESTful API, which can be used by the custom web portal to register a device and its unique passphrase using API calls.
Developing a custom web portal is outside the scope of this document. For more information regarding the Extensible RESTful Services (ERS) for Cisco ISE, please read about it here.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Just to confirm, are you saying that the minimum OS version for ISE has to be 2.3 in order to run IPSK?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
As a reminder, this is a special use case. Please review the AireOS 8.5 Identity PSK Feature Deployment Guide for guidance on typical use. When used in this manner, there isn't a version requirement for Cisco ISE. As a reminder, Identity PSK on the WLC integrates with most RADIUS servers, not just Cisco ISE.
This article requires Cisco ISE 2.3 or newer is to accomplish the special use case: Per-Device PSK. Cisco ISE 2.3 added the capability build a dynamic RADIUS AVP response using a variable (endpoint custom attribute). This simplifies our RADIUS authorization policies. Without it, we would have to create an authorization policy per-endpoint.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
... Cisco ISE 2.3 added the capability build a dynamic RADIUS AVP response using a variable (endpoint custom attribute). This simplifies our RADIUS authorization policies. ...
The custom attributes for internal endpoints are there since ISE 2.1. It appears working fine with an authorization profile with an endpoint custom attribute assigned to Cisco AVP, when I tried it with ISE 2.2 Patch 9.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks to you both for your quick feedback and clarification! Creating a policy or even an authZ rule for every every endpoint would be very impractical and tough to manage especially for large customers. Glad to hear that ISE 2.3 can do this dynamically. via RADIUS AVP response.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Another question. Has IPSK been tested with ISE 2.4? If not, is there any plans to test it with ISE 2.4?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Is iPSK supported for an AP running in FlexConnect mode/ local switching/ central authentication?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@kahsieh as mentioned in the beginning its for 2.3 and higher. For iPSK support you should check with the wireless team, however you can also see this information:
According to 8.8mr1 RN Flex + iPSK + p2p blocking is supported:
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

