- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Cisco ISE Certificate Change - Considerations and Best Practices
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
03-01-2025 10:37 PM - edited 03-03-2025 02:43 AM
As an ISE administrator, you will inevitably encounter expiring ISE certificates. If your ISE server’s certificate expires, it can cause serious issues unless you replace it with a new, valid certificate. If the certificate used for 'EAP' expires, all authentications may fail because clients will no longer trust the ISE certificate. If the 'Admin' certificate expires, the ISE administrator will see warnings when accessing the ISE Admin UI, and the distributed deployment may stop functioning and replicating. The ISE administrator must install a new, valid certificate on the ISE before the current certificate expires. This proactive approach helps prevent or minimize downtime and avoids disruptions for end users. Once the new certificate becomes active, you can enable the EAP, Admin, or any other necessary role on it.
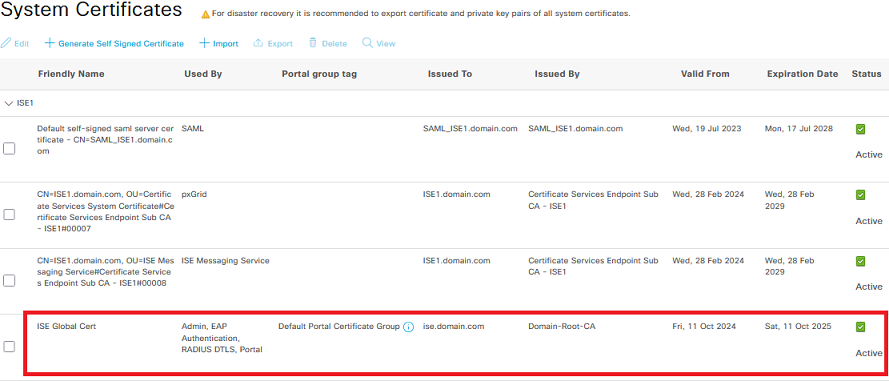
To view the currently installed certificate, navigate to Administration > System > Certificates > System Certificates in the ISE GUI, as shown in the following figure:
Before changing ISE certificates, consider the following important factors:
- Be aware that 'Admin' certificate changes require an ISE service restart, leading to a few minutes of downtime. Plan this change accordingly. In ISE 3.3 we have a new feature called "Scheduled Restart" which can minimize the effect of ISE service restart.
- 'EAP' certificate changes do not require a restart and can be implemented with minimal disruption.
- Install a new certificate before the existing one expires to avoid authentication failures and administrative access issues.
- ISE does not allow two certificates with the same subject. Uploading a new certificate with the same subject will replace the existing one. Before doing so, ensure you have a backup of the old certificate and key in case a rollback is needed.
- A certificate subject refers to the entity (individual, organization, or device) that the certificate is issued to and represents. It contains identifying information about the certificate holder, such as: Common Name (CN)--the name of the entity (e.g., domain name for websites or hostname for devices), Organization (O)--the name of the organization that owns the certificate, Organizational Unit (OU)--the department within the organization, Country (C)--the country code of the organization, State/Province (ST)--the state or province of the organization, and Locality (L)--the city or locality of the organization. This information is found in the Subject field of the certificate and helps verify the identity of the certificate holder.
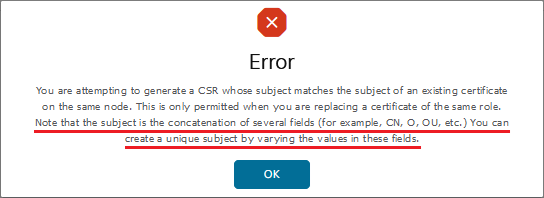
- As mentioned above, the Subject includes more than just the Common Name (CN); it consists of all the mentioned fields. Since ISE does not allow two certificates with the same subject, modify at least one field (e.g., Organizational Unit (OU) or Locality (L)) when generating a new certificate to maintain uniqueness. The following notification appears when you attempt to create a new Certificate Signing Request (CSR) with a certificate subject that is identical to an existing one in ISE:
- ISE does not support certificate staging. Certificate staging refers to the process of preloading and preparing a new certificate on a system before it replaces the existing one. This approach allows administrators to test and validate the new certificate without immediately applying it to active services, reducing the risk of disruptions.
- You must replace the certificate before it expires to allow sufficient time for planning the certificate swap and managing any potential downtime. In other words, obtain a new certificate with a start date that precedes the expiration date of the old certificate. The period between these two dates serves as the change window. The following figure displays information for a certificate that is nearing its expiration:
- Ensure that all ISE nodes are synchronized and not experiencing slow replication before making any certificate changes. You can check node status under Administration > System > Deployment to confirm that all nodes are operational and synchronized.
Base on the above facts, to replace your ISE certificate with a new one (based on a CA, not self-signed):
- Create a new CSR by modifying the OU, O, L, ST, or C field—OU is often the best candidate (e.g., 'IT-dep 2025').
- Have the CSR signed by your desired.
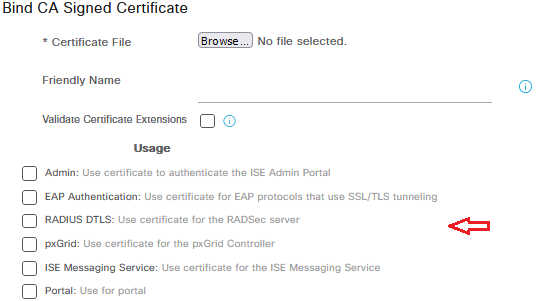
- Bind the certificate to the CSR without selecting any roles (as shown below). Then, log in directly to each node and navigate to the Certificates page. Verify that the certificate has been successfully replicated across all nodes (if the certificate has not replicated and you are using at least ISE 3.2, use the 'Syncup' option to force synchronization of the missing certificate on the node; for ISE 3.1 or earlier, delete the certificate, resolve any node issues, and try again. Alternatively, deregister the nodes, install a wildcard certificate, and then re-register the nodes together).
- Select the desired roles for the certificate. If 'Admin' is selected, all nodes will reboot. But as mentioned above, in ISE 3.3 and later, you can use the "Scheduled Restart" feature. Finally, delete the older certificate if everything looks good.
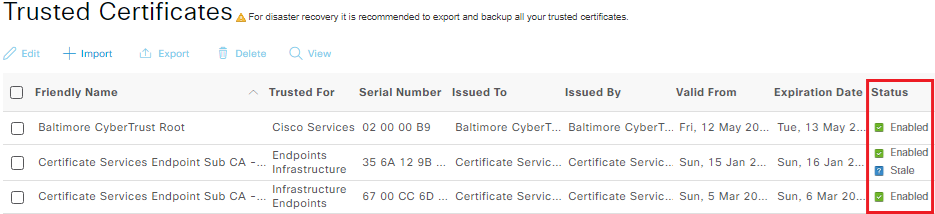
As you can see below, each certificate can have five different states (Enabled, Disabled, Warning, Stale, and Expired
A certificate with this status is no longer used in your deployment.
A certificate with this status is expiring soon.
Stale certificates are certificates that do not belong to any node in the deployment. The following checks are performed to identify Stale certificates:
- The Issued To field is checked to see if the hostname of any of the nodes in the deployment is a part of the issued system certificate. If there are no matches, the system certificate is considered to be stale.
- The SAN Extension field of an issued system certificate must match the FQDN of a node in the deployment. If there are no matches, the system certificate is considered to be stale.
Stale certificate checks are performed for certificates signed by third-party CAs, while self-signed certificates are exempt from these checks.
A certificate with this status has expired. As a security best practice, always delete expired certificates from the certificate store.
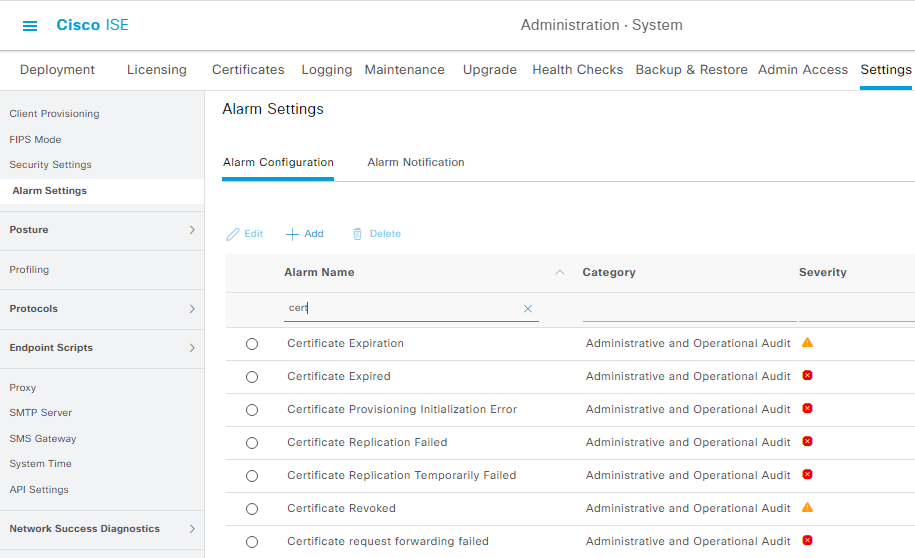
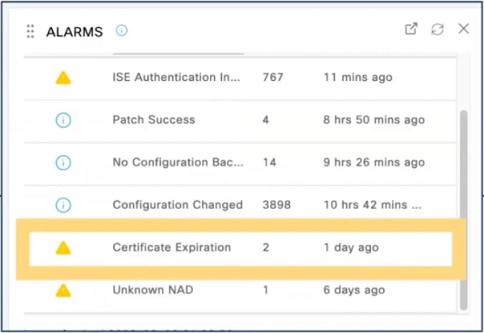
ISE has several alarms related to certificate expiry:
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: