- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Cisco Secure Client 5.x (AnyConnect) with SecureX Cloud Management
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 03-16-2023 06:46 AM
Paul Carco – Leader Technical Marketing Engineer
Cisco Secure Client
CSC (Cisco Secure Client)
Unified Agent
Cisco Secure Client v5.x is the rebranded AnyConnect Client that now offers the ability to be Cloud deployed and managed
via Cisco SecureX. CSC also now includes Cisco Secure Endpoint as a fully integrated module and functional tile in the new CSC UI. In addition, the rebrand and the cloud management option we now have a true unified agent with an immutable endpoint ID.
SecureX
The Platform
Cisco SecureX is the broadest, most integrated security approach that connects the breadth of Cisco's integrated security portfolio and the customer's infrastructure for a consistent experience. It unifies visibility, enables automation, and strengthens your security across network, endpoints, cloud, and applications—all without replacing your current security infrastructure or layering on new technology.
Source: What Is SecureX? - Cisco
Device Insights
With the increasingly distributed and complex nature of customers’ security environments, visibility has become an even bigger challenge. With a focus on security resilience and expanding visibility, this new device insights feature is designed to consolidate, discover, normalize, and work with their device inventory within SecureX.
SecureX device insights provides you with a unified view of the devices in your organization by consolidating inventories from integrated data sources.
Cisco Secure Client when deployed with Cloud Management is a source for Device Insights therefor your endpoints are added to the SxDI inventory for unprecedented visibility especially when combined with other integrated sources.
Figure 1 Available Integration modules for Device Insights
Cisco Secure Client Architecture
Overview
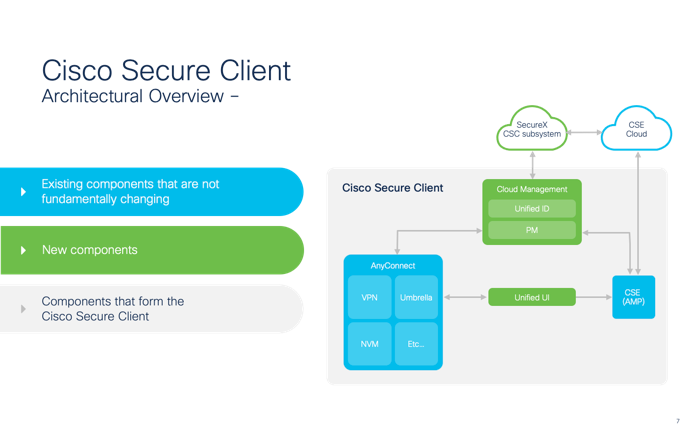
Here is an overview of the new Architecture. The components in Blue have existed for quite some time but the green is what we want to focus on since its new with initial CSC release.
What we have done is utilized SecureX and created a CSC subsystem where customers can now create what are called deployments to deploy CSC to the users and manage those deployments from the cloud.
This is very different than how it’s been done for over 15 years where after the initial deployment probably via SCCM or built into a corporate image the client was kept up to date by our headends; ASA, FTD or ISE.
A SecureX deployment would still be distributed initially in the same manner however if Cloud Management with the Package Manager is in place and the endpoint has access to the Cloud they will be kept up to date. No longer need to wait for VPN to establish or for the endpoint to show up in the office on the local network.
It’s here that we have created a Unified ID and finally the Unified UI – Cisco Secure Endpoint (formerly AMP) is now in the CSC UI.
Note: Cisco Secure Client 5.x when deployed from the Cloud is only supported on Windows 10/11 at the time this document was written. MAC and Linux support is soon to follow.
Figure 2 High level Cisco Secure Client Architecture
Cisco Secure Client (formerly AnyConnect)
Deployment Overview - History
Until recently the options to deploy the former AnyConnect were as follows:
- Pre-deploy—New installations and upgrades are done either by the end user, or by using an enterprise software management system (SMS). This deployment option offers no cloud management.
- Web Deploy—The Cisco Secure Client package is loaded on the headend, which is either a Secure Firewall ASA, Secure Firewall Threat Defense, or an ISE server. When the user connects to a firewall or to ISE, Cisco Secure Client is deployed to the client. This deployment option offers no cloud management.
- For new installations, the user connects to a headend to download Cisco Secure Client. The client is either installed manually or automatically (web-launch).
- Updates are done by Cisco Secure Client running on a system where Cisco Secure Client is already installed, or by directing the user to the Secure Firewall ASA clientless portal.
The methods mentioned above are of course still an option since we know not everyone will or can adopt the cloud as a deployment method. The rebranded AnyConnect – Cisco Secure Client 5.x is available on CCO which stands for Cisco Connection Online, however these packages do not include Cloud Management and should be treated like AnyConnect 5.0 – nothing changed but the name and some colors in the UI. You will notice that of course MAC and Linux are supported just as they always have been just without Cloud Management. Also, if you download the Windows version from CCO that comes without Cloud Management. Cloud Management comes from SecureX.
Figure 3 CCO Software Download page
Deployment Overview – New
SecureX Cloud Management Deployment
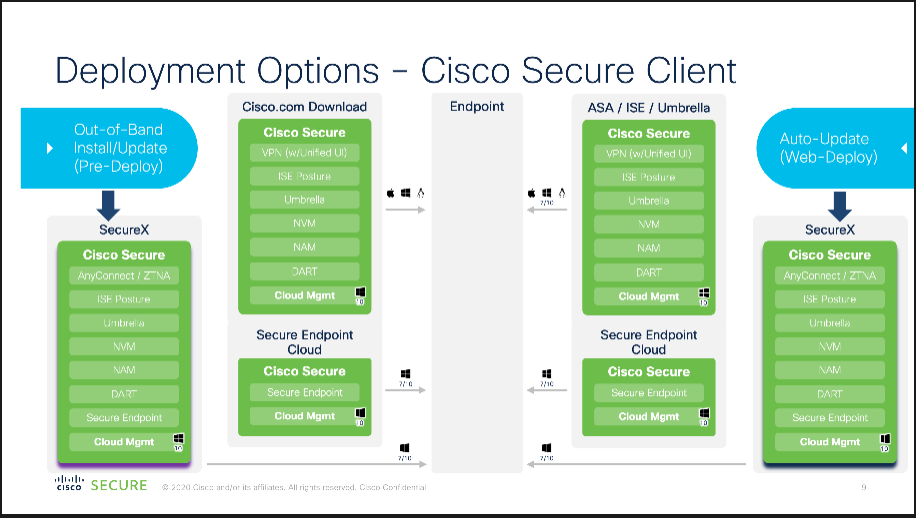
Figure 4 Cisco Secure Client Deployment Options
When deploying from SecureX the new package manager is the component that takes care of initial deployment of CSC Modules and Profiles and keeps them up to date. The Cloud Management component is what facilitates the communication between the endpoint and the SecureX Cloud.
When an Endpoint has Cloud Management installed, this endpoint will be available in the Device Insights Inventory and easily located using the single click in SxDI to sort only on endpoints with Cisco Secure Client.
SecureX Deployment Requirements - Cisco Secure Client
- SecureX Access
- Cisco Secure Client Enabled
- SecureX Device Insights Enabled
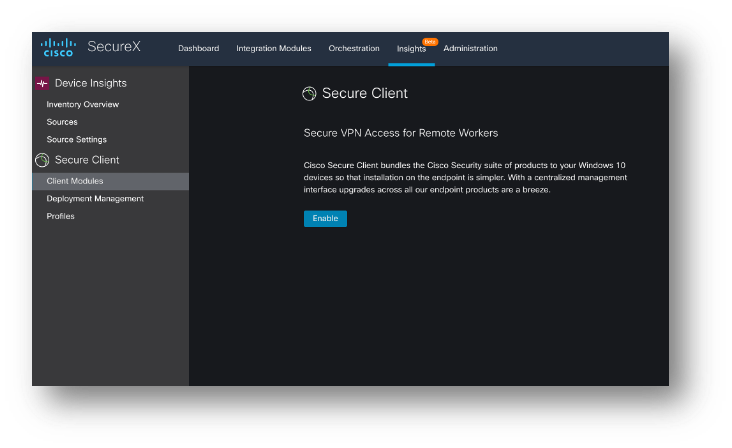
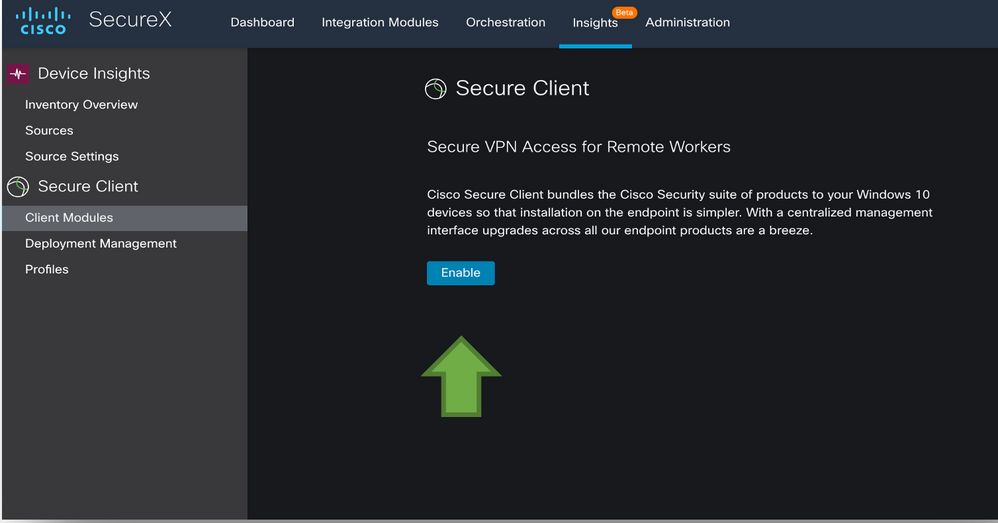
Figure 5 Enable Secure Client once in SecureX.
Currently within Device Insights
- Click Enable
- This starts the process of spinning up your CSC Sub-system.
SecureX Deployment Use cases
Deployment Overview
Using SecureX Cloud Management Deployment there are two possible use cases.
The first use case would be Cloud Management only and no package manager, this would at the very least give the customer visibility into their endpoints. A customer may choose this option if they are not ready to make the leap to the cloud and deploy and manage Cisco Secure Client. They would have CM with no package manager which means any module and profile updates would continue to be updated by the headends or out of band.
Cloud Registration w/o Package Management
- Use CM for inventory, but not for package delivery/management.
- Customer wants/needs the UID; especially important for XDR use-cases.
- Create a Deployment with only CM module defined.
- The rest of the software comes from the CCO downloaded pkg’s hosted on the ASA or ISE, SE Cloud, etc.
The second use case would be Full Cloud Management which in addition to Cloud Management includes Package Manager. The customer would no longer allow the headends; ASA, FTD or ISE to handle any of the updates and instead leave it up to SecureX. It’s this use case we will spend the majority of document discussing in terms of best practices when migrating.
Full Cloud-Management
- Using either the network or full installer for the endpoints.
- CM Module handles package management and the cloud identity.
- Allows for Cloud Configuration of profiles & module management
CSC (Cisco Secure Client) Migration
Deployment and Profile Overview
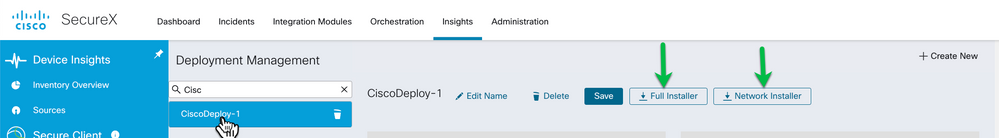
A Deployment built in SecureX results in an installation package that is ultimately installed on the Endpoints available for download from SecureX. There are two options a Full Installer or Network Installer. A Deployment is comprised of 3 sections.
- Cloud Management
- Cisco Secure Endpoint
- AnyConnect/ZTNA VPN & Cisco Secure Client Modules i.e.., Umbrella, NVM, etc.
Figure 6 Cisco Secure Client Deployment page overview
Network Installer - A lightweight installer that contains only the cloud management client. When deploying the network installer, it fetches the rest of the installers configured on the deployment in the background.
Full installer - A bundle of all the installers and profiles that have been configured for a deployment, larger in size than the network installer. When the user installs a full installer, the cloud management client and all the packages from the deployment are installed.
Source: https://docs.securex.security.cisco.com/Secure-Client-Help/Content/sc-deployment-management.html
Profiles
Profiles are associated with Modules and is the configuration source for each module. Historically with enterprise initial deployments typically the team that operates the software management tools or is responsible for building a corporate image would deploy the client package and then the profiles to the correct file location on the endpoint. Profiles and Modules can be deployed and updated by the headends this is specified in the ASA/FTD Group Policy
Now Customers have the option using SecureX to create the deployments with Profiles and download either a Full or Network installer to get the endpoint deployed with the correct modules and profiles included.
SecureX Profile Editor
Figure 7 SecureX CSC Profile Editor
ASDM Profile Editor
Figure 8 Cisco ASDM Profile Editor
- Profiles act as the main source for client configuration and each module has its own profile.
- Core/VPN: admindefined.xml (aka the vpn profile)
AnyConectLocalPolicy.xml*
CustomerExperience_Feedback.xml*
- NVM: NVM_ServiceProfile.xml
- Umbrella. Orginfo.json
- ISE Posture: admindefined.xml
- NAM: Configuration.xml
- Mgmt. Tunnel: VpnMgmtTunProfile.xml
- Cloud Mgmt.* bs.json
cm_config.json
+AnyConnectLocalPolicy.xml is optional but present by default. This is where FIPs compliance is configured as an example.
*Customer feedback enabled by default; deploy profile to disable
* Cloud Management bs.json links endpoint with SecureX business_id and cm_config.json instructs the endpoint how to interact with the SecureX Cloud
Note: admin defined (VPN and ISE Posture) means you can name it anything you wish, the other profiles have strict naming requirements.
Profiles when deployed from a headend such as ASA/FTD are pushed according to the Group-Policy assigned.
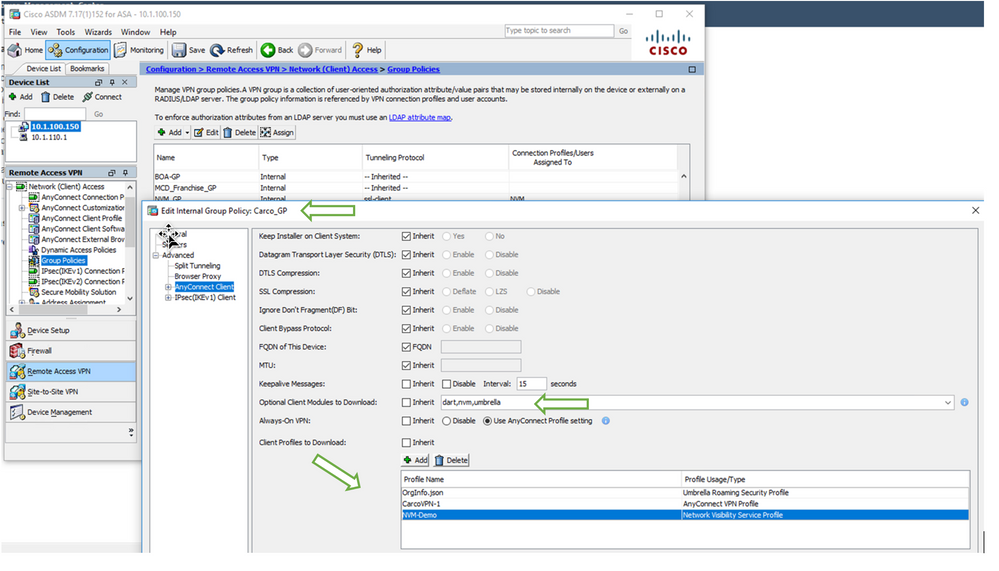
Figure 9 ASA Group-Policy example in ASDM
SecureX Cloud Managed deployment packages contain the module and associated profiles.
Figure 10 Deployments & Profiles
CSC Onboarding Overview
Cisco Secure Client (SC) is a feature within SecureX When this feature is active customers can:
· List/search/filter devices via Insights
· Manage deployment settings for client modules
· Manage configuration/profiles for client modules
· Select client modules to be deployed to the endpoints, select software version channel for the Client; Latest, Recommended, Alpha/Beta
· Download and manage installers
· Move deployments
Figure 11 SecureX Device Insights
Deployment Requirements - Cisco Secure Client
- SecureX Access
- Cisco Secure Client Enabled
- SecureX Device Insights Enabled
Currently within Device Insights
• Click Enable
• This starts the process of spinning up your CSC Sub-system
Figure 12 Step 1 of a deployment – Enable Cisco Secure Client
SecureX Deployment Use cases
Full Cloud Managed Deployment Example – New Install (No AC or SE currently)
- Using either the network or full installer for the endpoints.
- CM Module handles package management and the cloud identity.
- Allows for Cloud Configuration of profiles & module management.
In this example of a possible customer use case, we are going to step through a new deployment that has the following requirements:
- Cloud Management
- Secure Endpoint
- AnyConnect/ZTNA VPN
- Umbrella
Note: If the Administrator decides later that another module is necessary the Administrator would just simply edit the deployment and during a client check-in the module would be added to the client. Alternatively, if the Administrator determines a subset of users require and additional module then a new deployment could be created, the Move Deployment feature can be used to update the subset of user’s endpoints.
Step 1. Create or upload the profiles required for CM, AnyConnect/ZTNA and Umbrella.
In this deployment we need to create Cloud Management and AnyConnect/ZTNA VPN profile and upload an Umbrella profile (Orginfo.json). It is not possible to create the Umbrella profile so as an administrator you would access the Umbrella Dashboard and download the profile that will then be uploaded to SecureX. Handling the profiles up front avoids the need to pivot from the actual Deployment configuration to create or upload a profile.
Cloud Management Profile
Navigate to: Insights > Secure Client > Profiles > Cloud Management
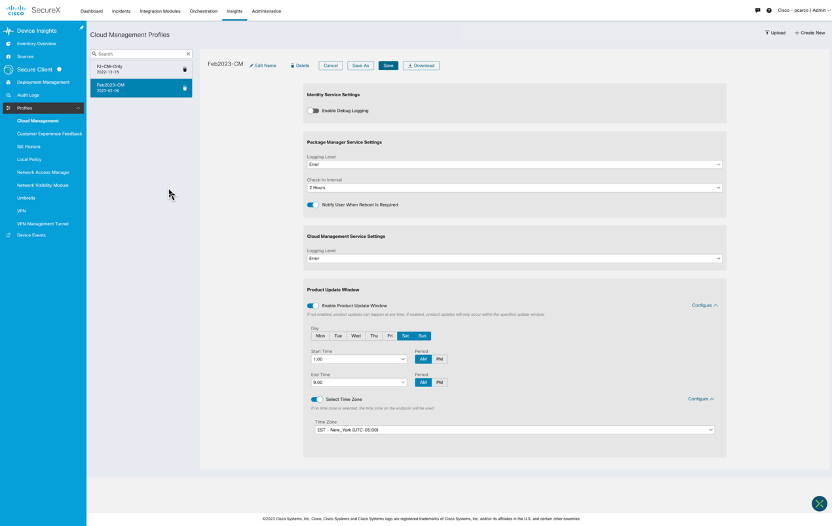
There are two options with most all profiles; Upload an existing profile or create new. Shown below is a completed Cloud Management Profile ready to be added to a Secure Client Deployment. This profile instructs the endpoint on how to interact with the cloud. We have set a 2-hour check-in time meaning that this endpoint will attempt to check-in with the cloud every 2 hours if online. Further down and optional is the ability to specify the acceptable times for an update.
Figure 13 Cloud Management Profile
AnyConnect/ZTNA Profile
Navigate to Insights > Secure Client > Profiles > VPN
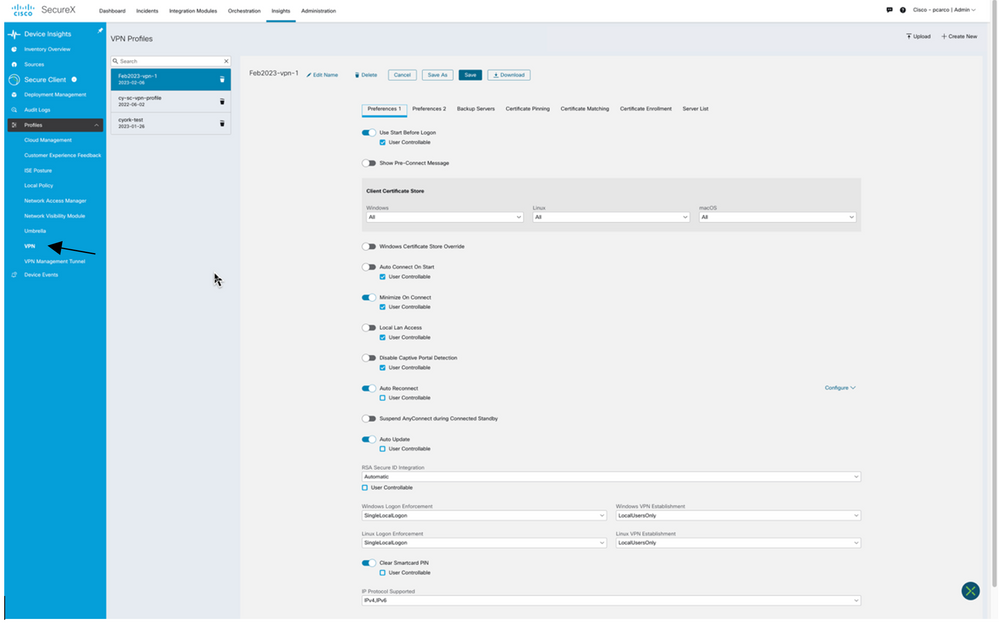
Figure 14 Cisco Secure Client VPN/ZTNA Profile
The VPN Profile editor in SecureX looks very similar to ASDM and the Stand-alone editor used to create profiles. Once again, the Administrator has the option to upload an existing VPN profile that they may have been using and exported from the VPN headend which is good practice to avoid the having the profiles mismatch with the headends and be replaced.
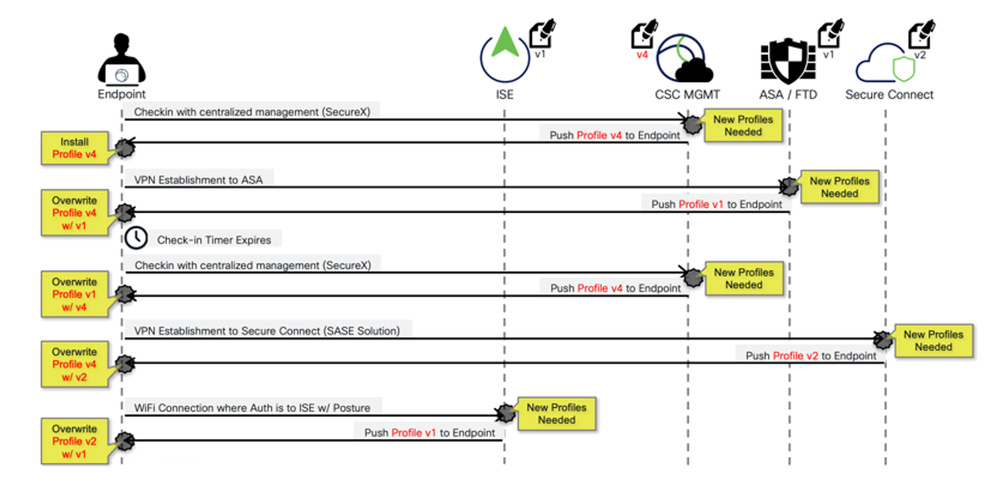
We refer to this as the problem associated with multiple control points. The headends will always do a check using the downloader process to ensure the client attempting a connection to the ASA/FTD has the correct profile configured in the Group-Policy and if it does not match, the headend will push down the profile and then permit the connection based on the configuration of the profile. Now the Client checks-in with the Cloud and the deployment determines using the Package manager that the client does not have the configured profile and the update takes care of this and again replaces the profile. It is strongly advised that the administrator keeps the profiles on the headends in sync with the cloud.
Figure 15 Possible multiple control point issue
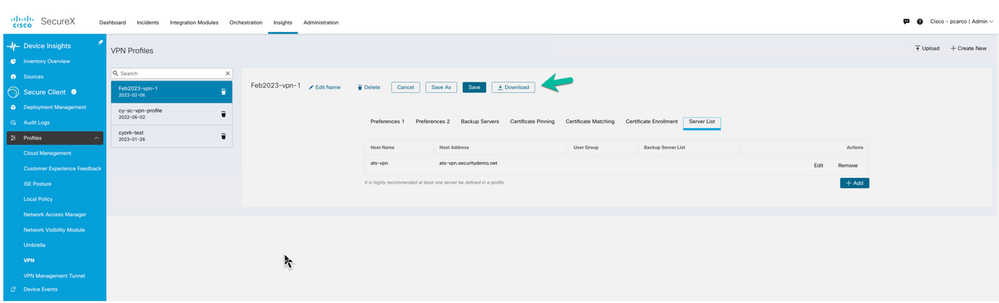
If this is a new VPN profile then simply use the SecureX VPN Profile editor screen, create the profile, Save and Download it before moving on to creating a deployment. The administrator would then access the headends and in the case of and ASA or FTD the group-policy the user is expected to be assigned would be updated with the new Profile configured in SecureX.
Figure 16 Download Profile from SecureX
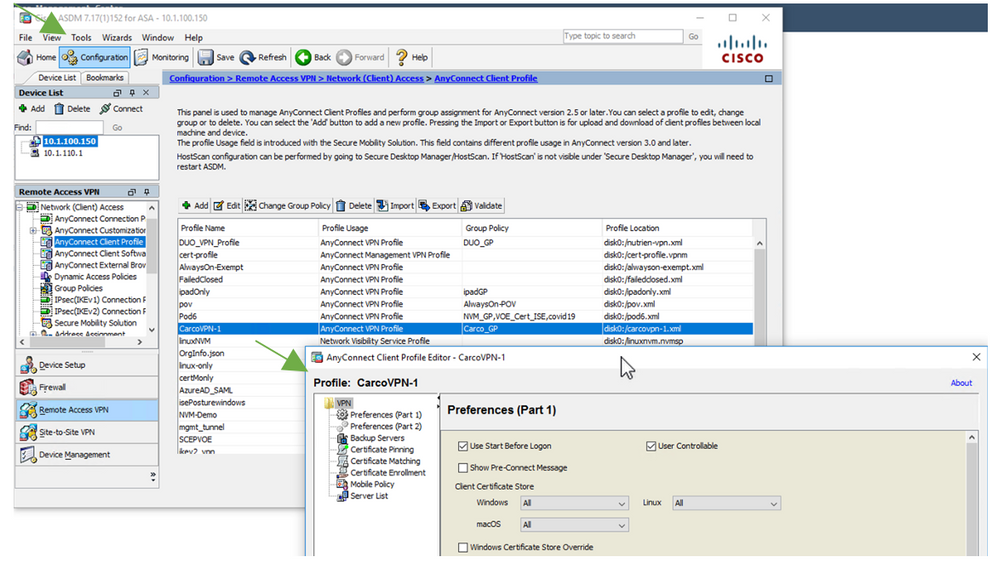
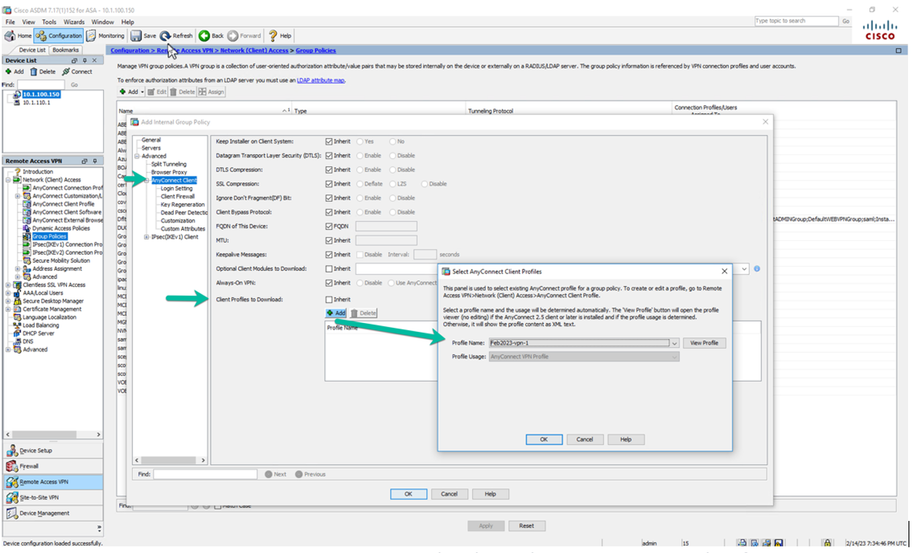
The following is an example of assigning the new Profile ‘Feb2023-vpn-1.xml’ created in SecureX and assigning it to a Group-Policy on the ASA using ASDM. As the Administrator you would ensure that the group-policy assigned to your VPN users contains the same profile that the Cloud will ensure is present.
Figure 17 Importing and assigning the profile from SecureX to the ASA GP example.
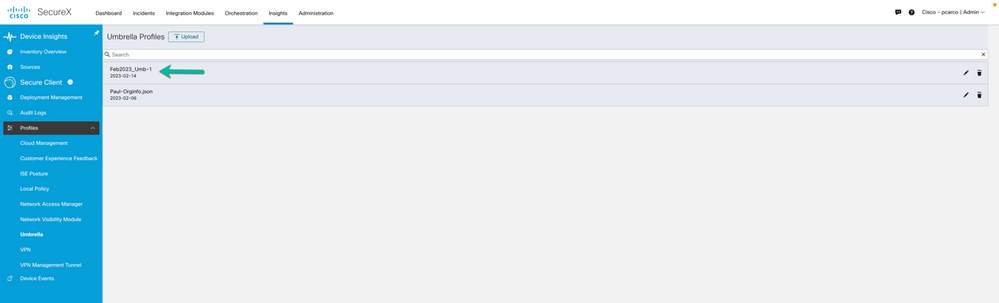
Umbrella Profile (Orginfo.json)
It is not possible to create an Umbrella Profile (Orginfo.json), this profile needs to be obtained from the Umbrella dashboard and uploaded to SecureX. This has always been the case with the ASA and FTD. You obtain the profile from Umbrella and upload for use on the headends.
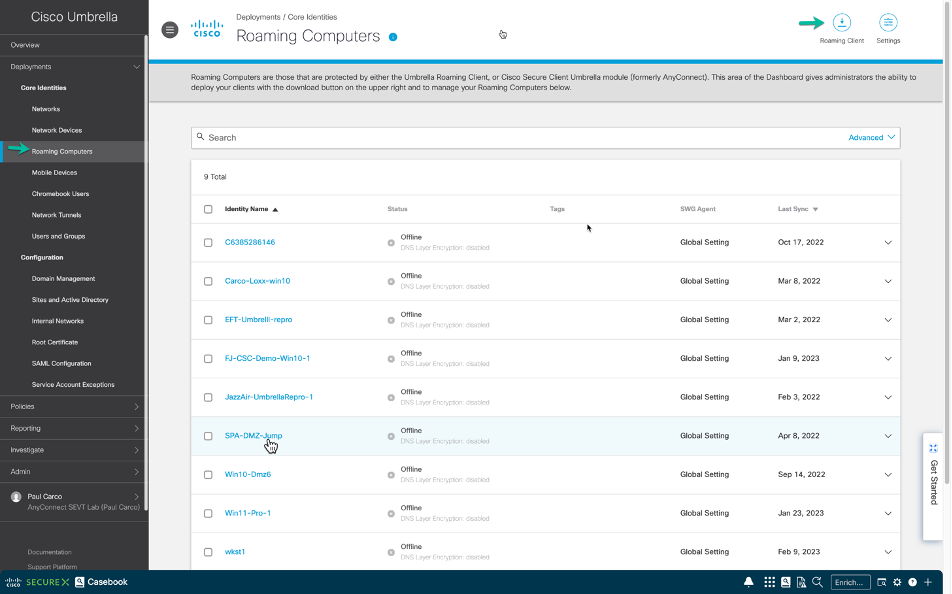
Login to the Umbrella Dashboard and Navigate to ‘Roaming Computers’ and then click on ‘Roaming Client’. This will allow you to download the Orginfo.json profile associated with the Umbrella Organization.
Figure 18 Accessing the Umbrella Console.
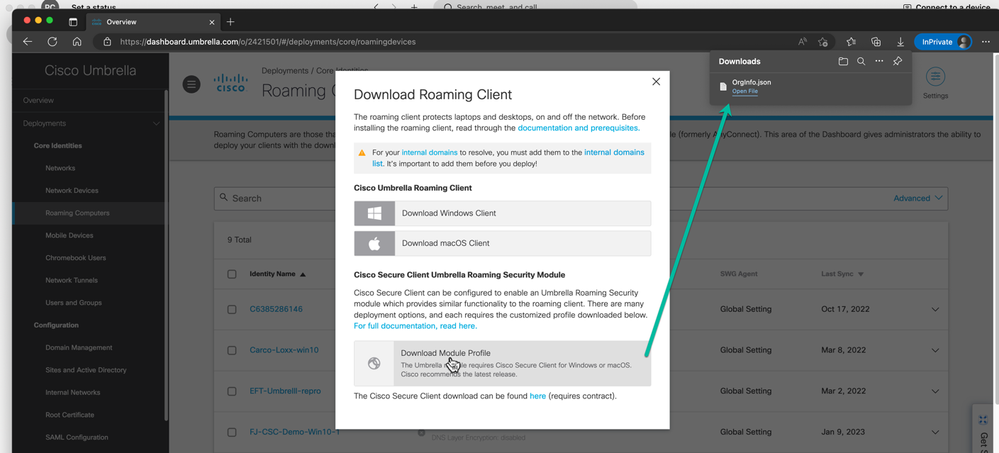
Be certain to download only the Module Profile in the Cisco Secure Client Umbrella Roaming Security Module section.
Figure 19 Download the Umbrella Orginfo.json profile.
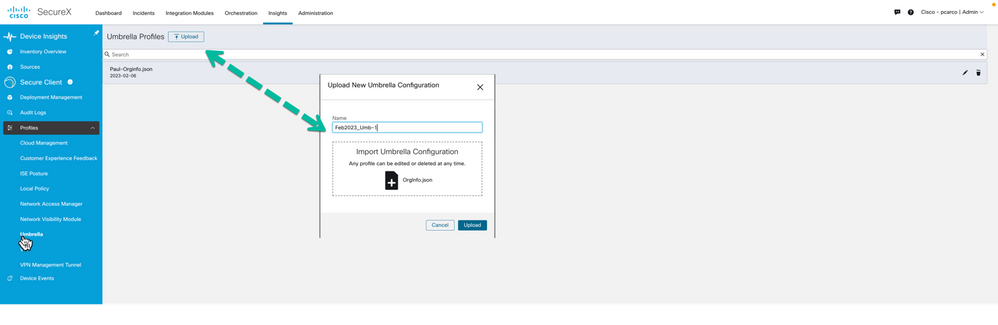
Return to SecureX: Insights > Secure Client > Profiles > Umbrella
Use the Upload option and provide a friendly name to the Umbrella Orginfo.json profile.
Figure 20 Upload the Orginfo.json profile to SecureX for use in deployments.
The result is that the new profile is now in the list and available to be used in a deployment.
Figure 21 Orginfo.json profile now available for assignment to deployments.
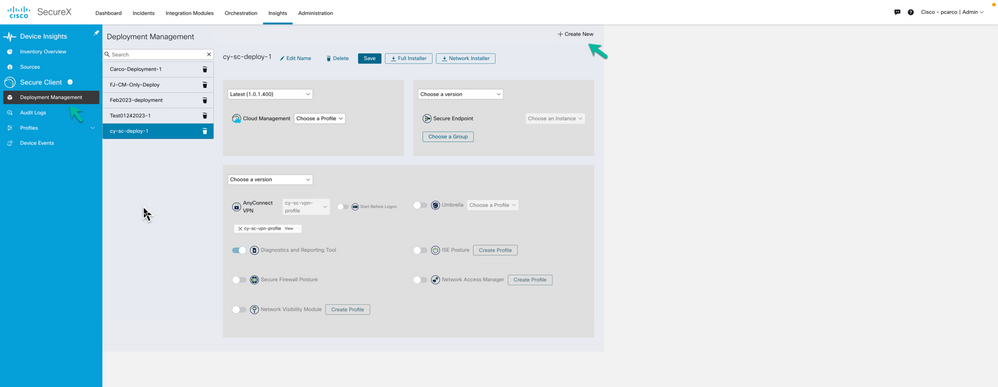
Step 2. Create a New Deployment
The Deployment Management page allows users with administrator privileges to define a list of all packages/modules and related profiles that must be installed on the endpoints in a specific deployment within an organization. An Administrator may determine they need specific deployments for specific groups of users, Engineering, Marketing, Sales etc. Administrators familiar with configuring the headends such as ASA or FTD can compare this to configuring specific Group-Policies that specify what modules and profiles the endpoint must have based on the Group-Policy assigned when creating a session.
Once you have created and saved a deployment the installers are generated, and the Administrator can choose to download a Full or Network installer.

Full Installer: All selected Modules & their configurations. Network Installer: Installs Cloud Management first, then PM pulls the manifest from deployment and installs each module and configuration one at a time. Running the full or network installer on a device associates it with the deployment from which the installer was generated. Each time the device checks in to the cloud, the list of installed packages is compared with the deployment requirements, and the packages and profiles will be updated to ensure they match the current deployment assigned. Note: installed packages that have a higher version than what is in the deployment will not be downgraded. This can occur if someone upgrades the headends with a newer version or if they downloaded a newer package from CCO and installed directly over what was installed by SecureX.
|
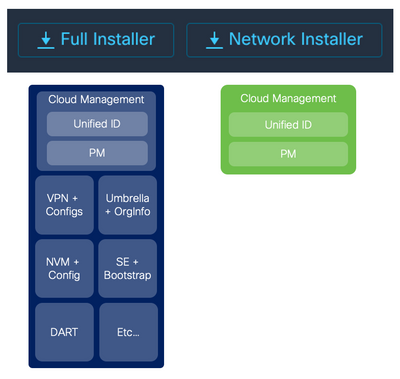
Figure 22 CSC Installer options
|
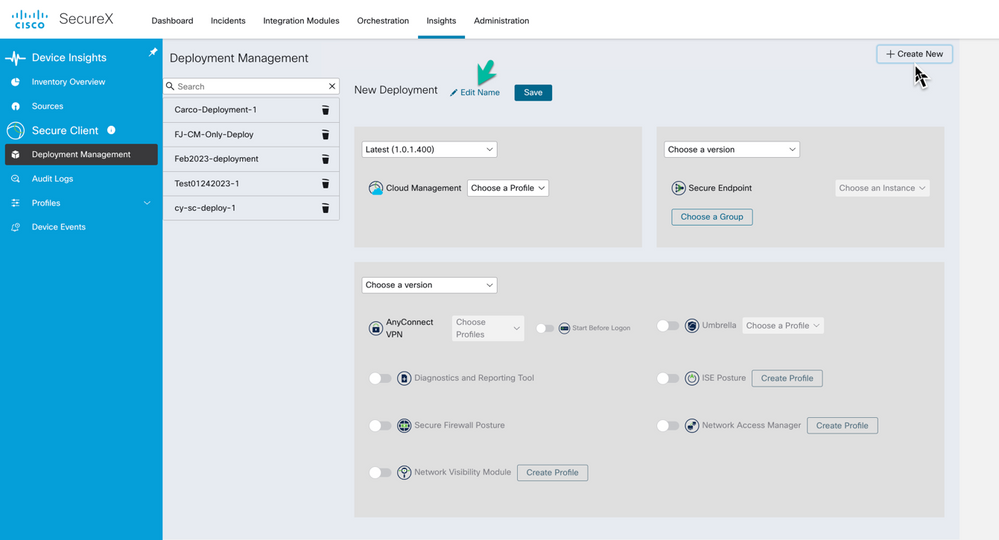
Navigate to Insights > Secure Client > Deployment Management
Use the + Create New option to begin configuring the new Deployment.
Edit the Name and Save before moving to the sections below
Figure 23 Creating a new Deployment.
Deployment Configuration – Cloud Management
Summary of steps
- Select the version and update channel.
- Select the CM profile from the pull-down. The profile was created earlier.
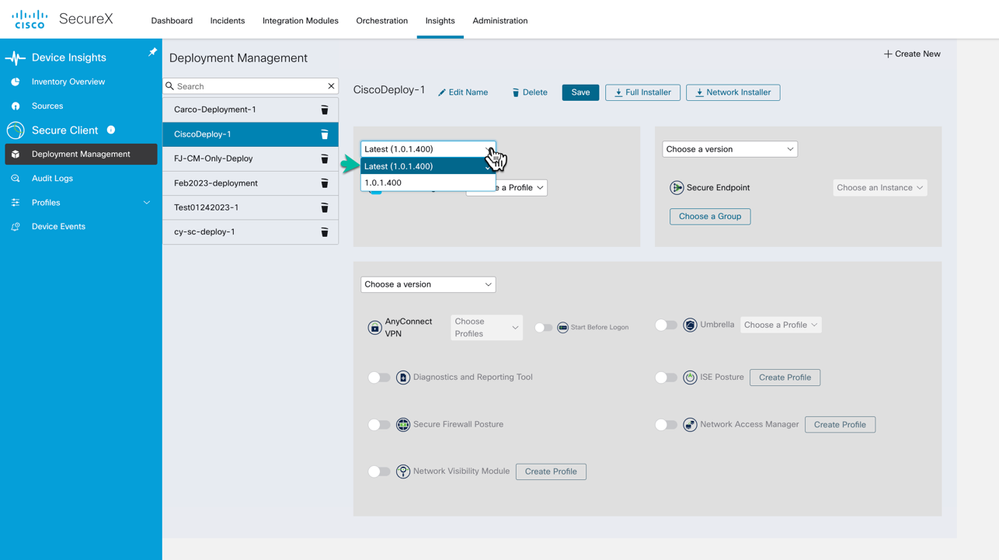
With the new deployment named we first want to configure the Cloud Management and select the software version for Cloud Management. We are going to use the Latest published on SecureX.
Figure 24 Cloud Management software version selection.
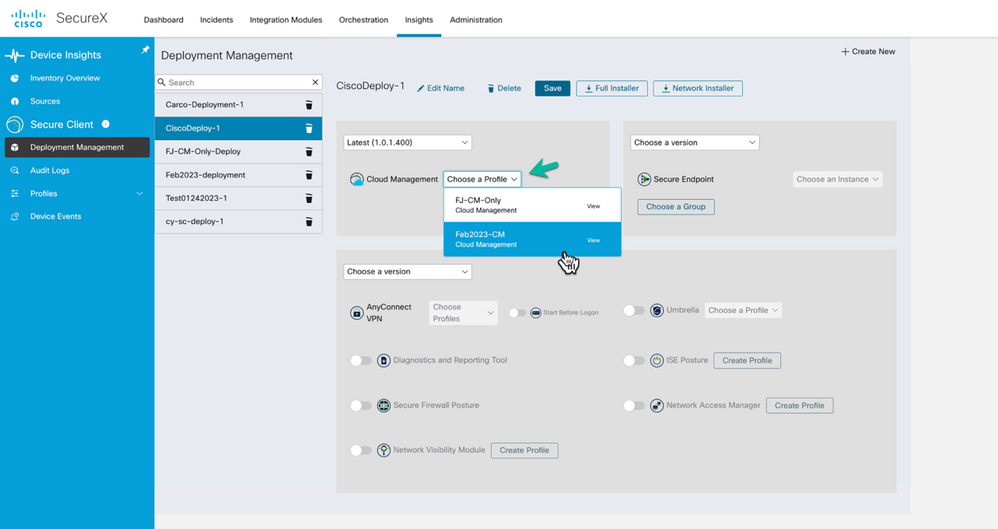
The next step in the Cloud Management section is now choose the CM profile we configured earlier; Feb2023-CM and Click Save and move to the Cisco Secure Client modules section below.
Figure 25 Select and assign Cloud Management Profile to the Deployment.
Deployment Configuration – CISCO SECURE CLIENT / ANYCONNECT
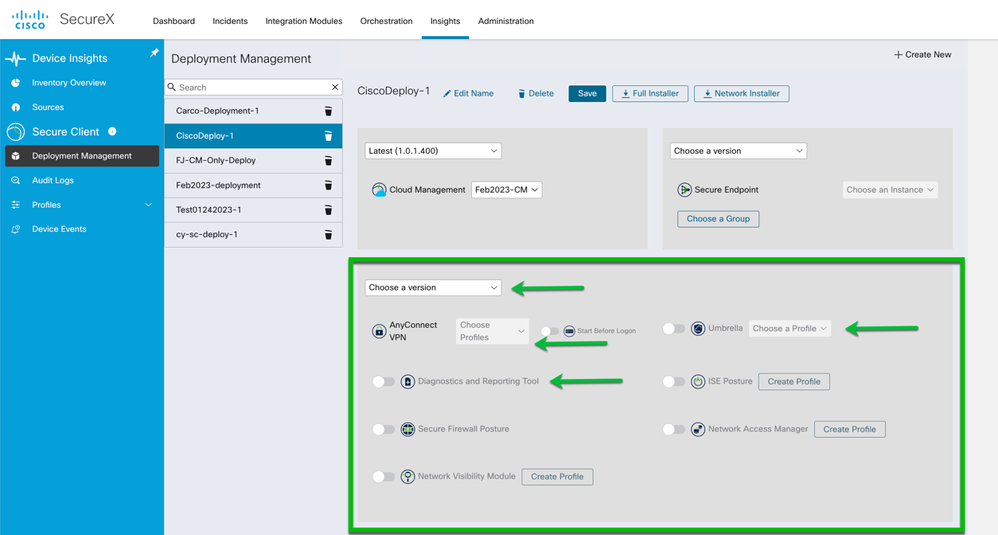
Now move down to the section shown below to configure the CSC/AC modules and profiles.
Summary of steps
- Select the version and update channel.
- Select the VPN profile from the pull-down. The profile was created earlier.
- Select the Umbrella profile from the pull-down. The profile was uploaded earlier.
- Use the slider to Enable the Diagnostics and Reporting Tool (DART)
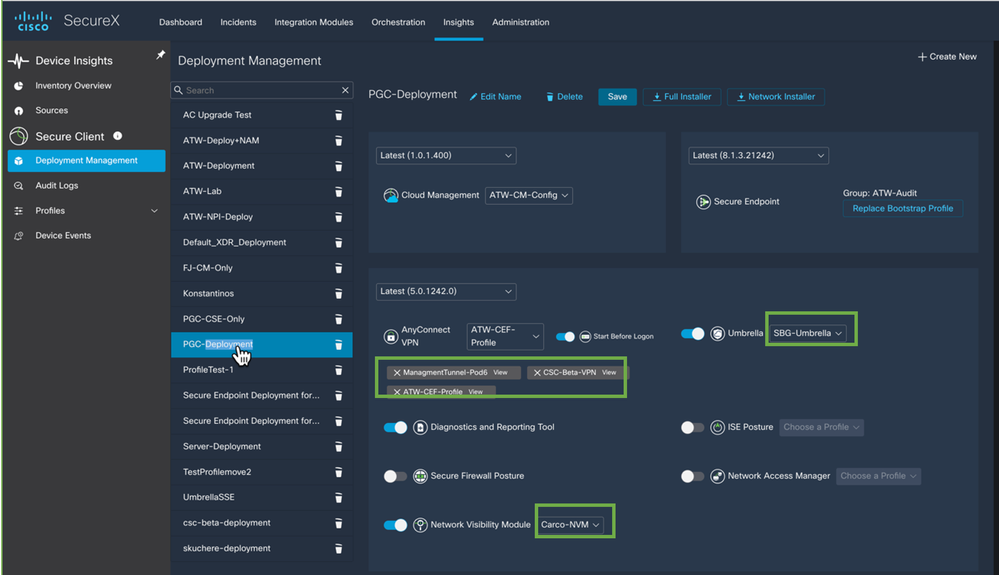
Figure 26 Configure the CSC Module section.
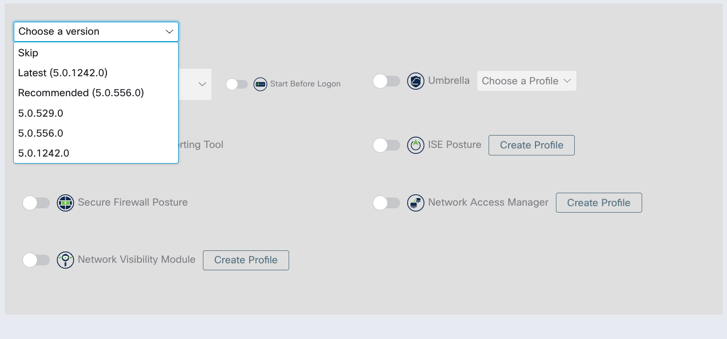
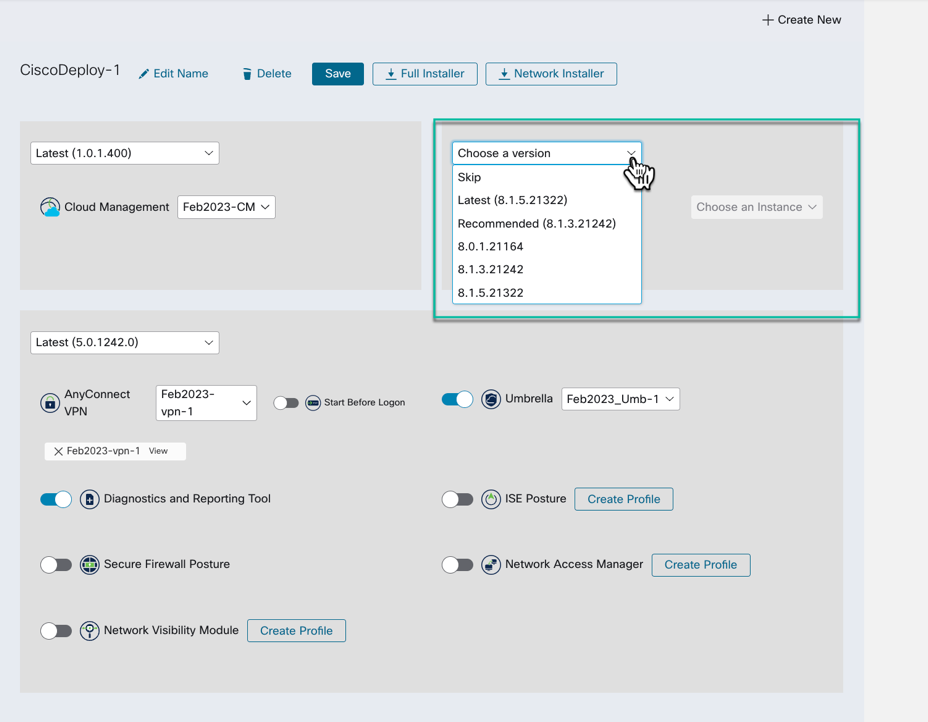
For Each Deployment, specify which channel you want the software to update from:
- Hard-Code the specific version (version lock)
- Skip (never upgrade version)
- Recommended
- Alpha / Beta -Allows you to have “early testers” set of endpoints, etc.
Note: Recommended and any Alpha/Beta version (if listed/shown) will automatically upgrade when Cisco publishes new version to the channel.
Figure 27 Choose the Software version and update channel.
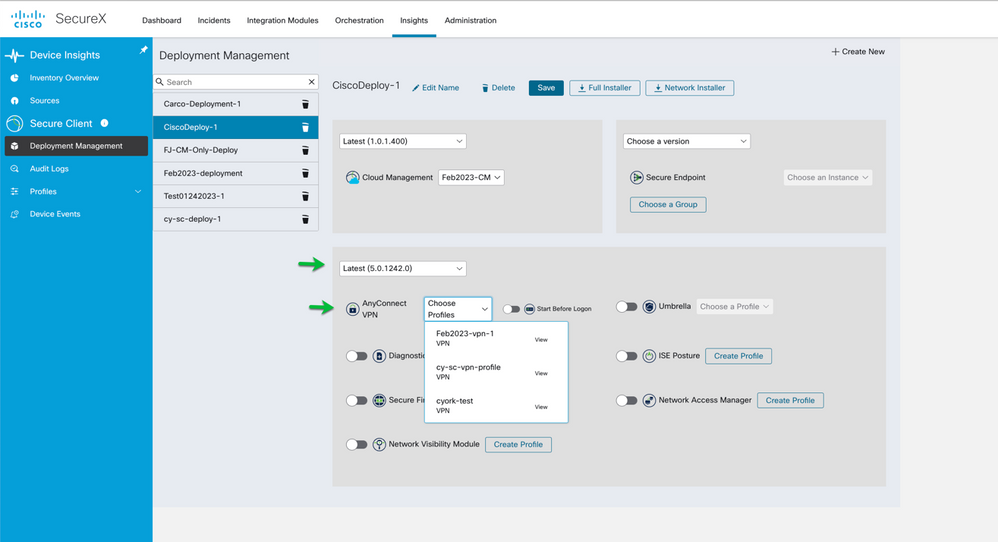
We have chosen to deploy with the latest version in the channel and using the Choose Profile pull-down we will select the Feb2023-vpn-1 profile created earlier.
Figure 28 Choose and assign the VPN/ZTNA Profile to the Deployment.
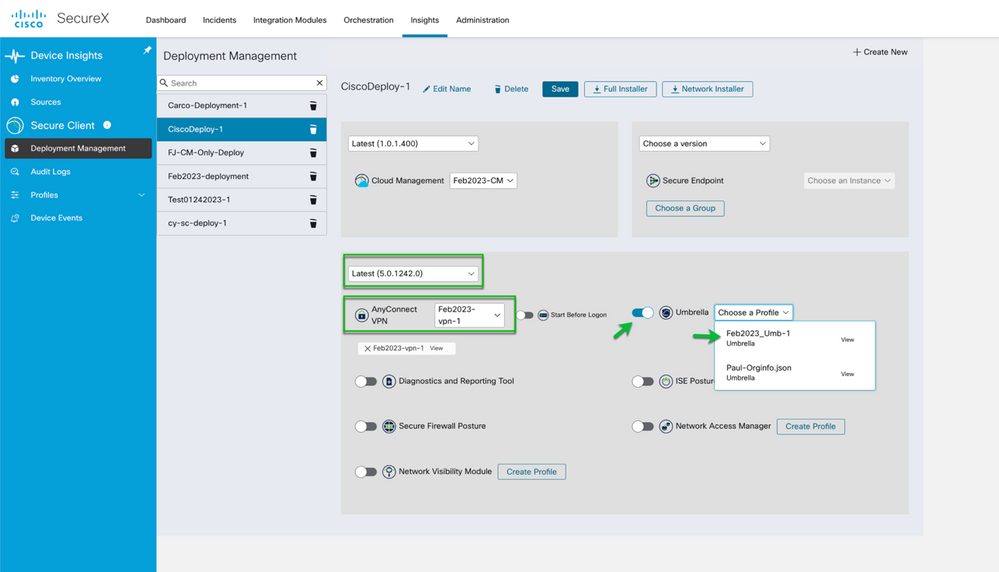
Now we move to Umbrella and toggle the module to active and again using the pull-down select the Umbrella profile we uploaded to SecureX earlier.
Figure 29 Select the Umbrella Orginfo.json profile to be used in the Deployment.
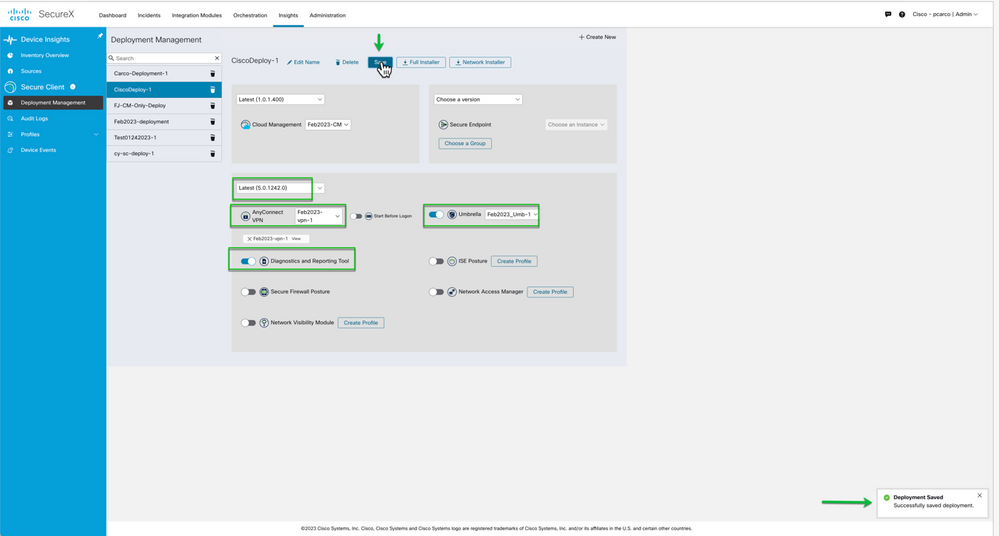
After selecting the Umbrella Profile it’s a good idea to always enable DART for troubleshooting. Hit Save before we finalize this deployment with CSE. Look at bottom right portion of screen to confirm save was successful.
Figure 30 Enable DART and Save the Deployment.
At this point we have a Cloud deployment that will install AnyConnect VPN and Umbrella and since we have Cloud Management of course the endpoints with this deployment will be in the SecureX Device insights inventory. We have one final piece and that is to configure the deployment for Cisco Secure Endpoint (AMP for Endpoints).
Deployment Configuration – CISCO SECURE Endpoint (AMP)
To finalize this deployment, we will configure Cisco Secure Endpoint. Once again with Cisco Secure Client 5.x we have a true unified client as CSE is now a fully functioning module with functioning tile in the CSC UI.
Cisco Secure Endpoint will need to be linked to SecureX Organization. It’s possible to have multiple Cisco Secure Endpoint “Businesses” linked to a single SecureX Organization. When Cisco Secure Endpoint is linked to SecureX the Administrator can assign a Cisco Secure Endpoint Group with its policy to a Cisco Secure Client Deployment. SecureX is not replacing the need to configure Cisco Secure Endpoint in the CSE Cloud it is just simply providing a bootstrap configuration to get CSE into CSC on the endpoint.
- All group & policy control of the SE module comes from SE Cloud.
- SE group changes, software updates, etc...
- SecureX can still update software versions through deployment.
Summary of steps to configure CSE in SecureX CSC
- Select SE version.
- Select SE Instance (business)
- Select SE Group
Requirements
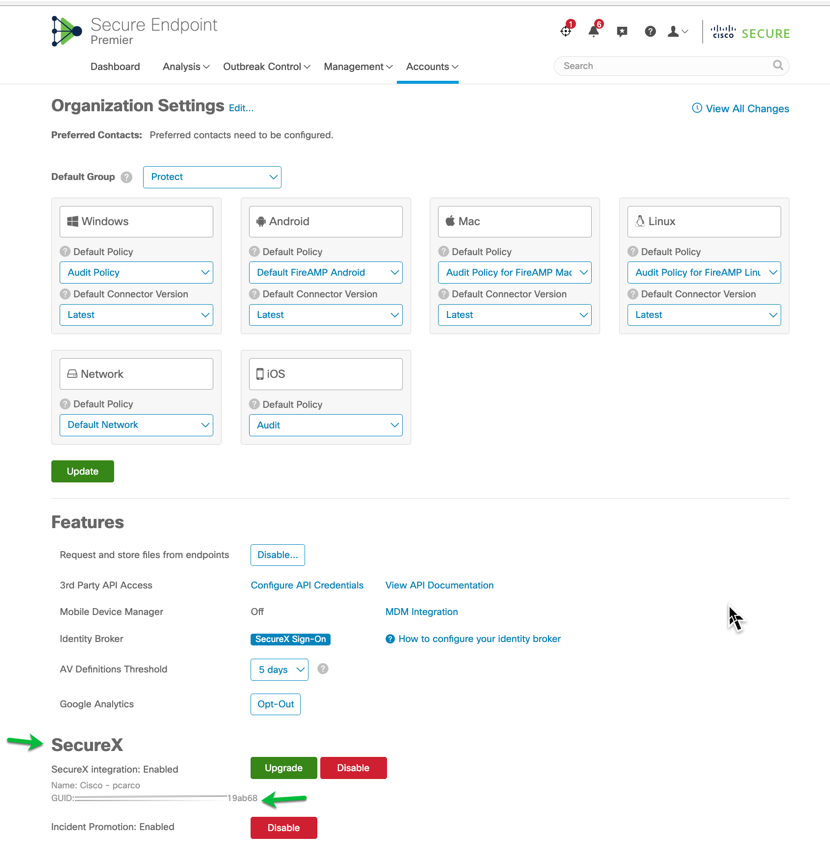
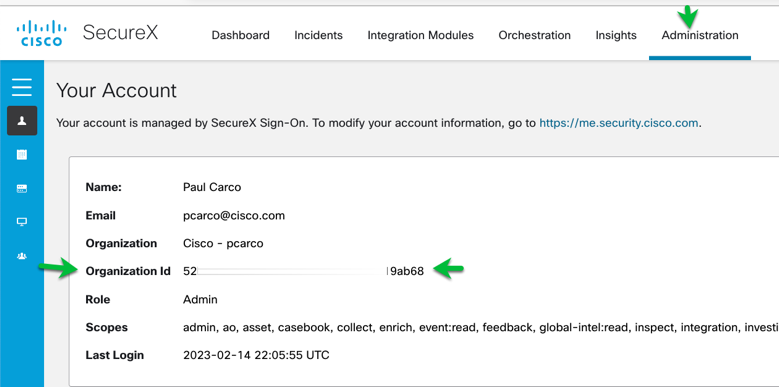
Cisco Secure Endpoint must be linked to the SecureX Organization that is being used to deploy Cisco Secure Client
Shown below Cisco Secure Endpoint is linked currently to SecureX.
|
|
Figure 31 Cisco Secure Endpoint linkage to SecureX Organization.
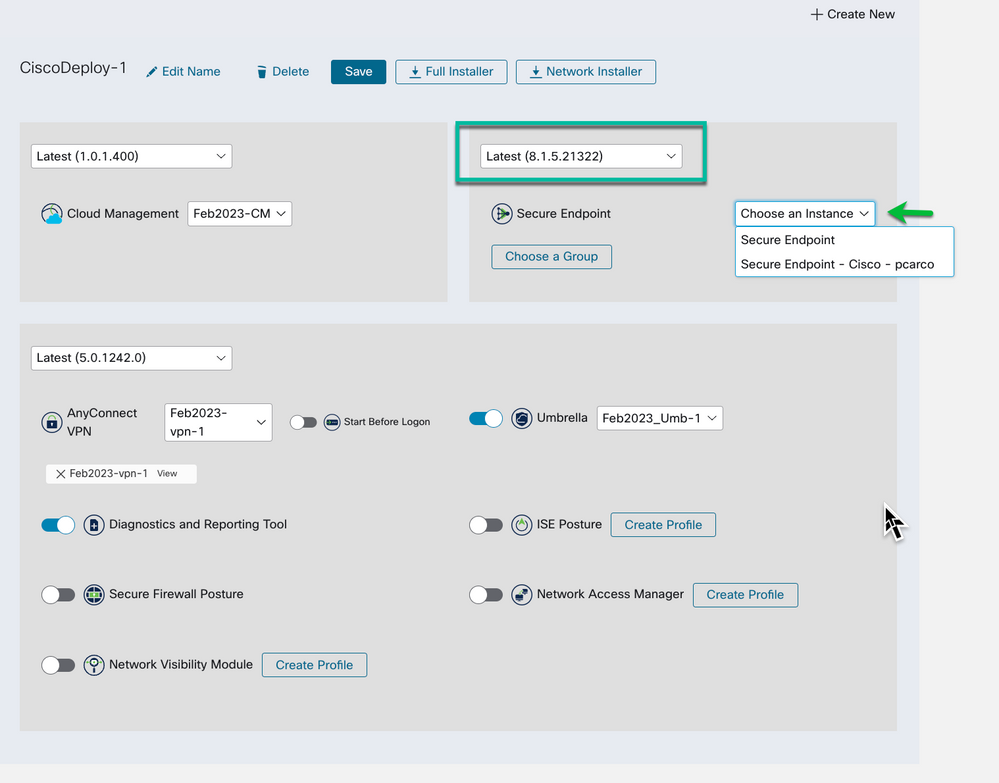
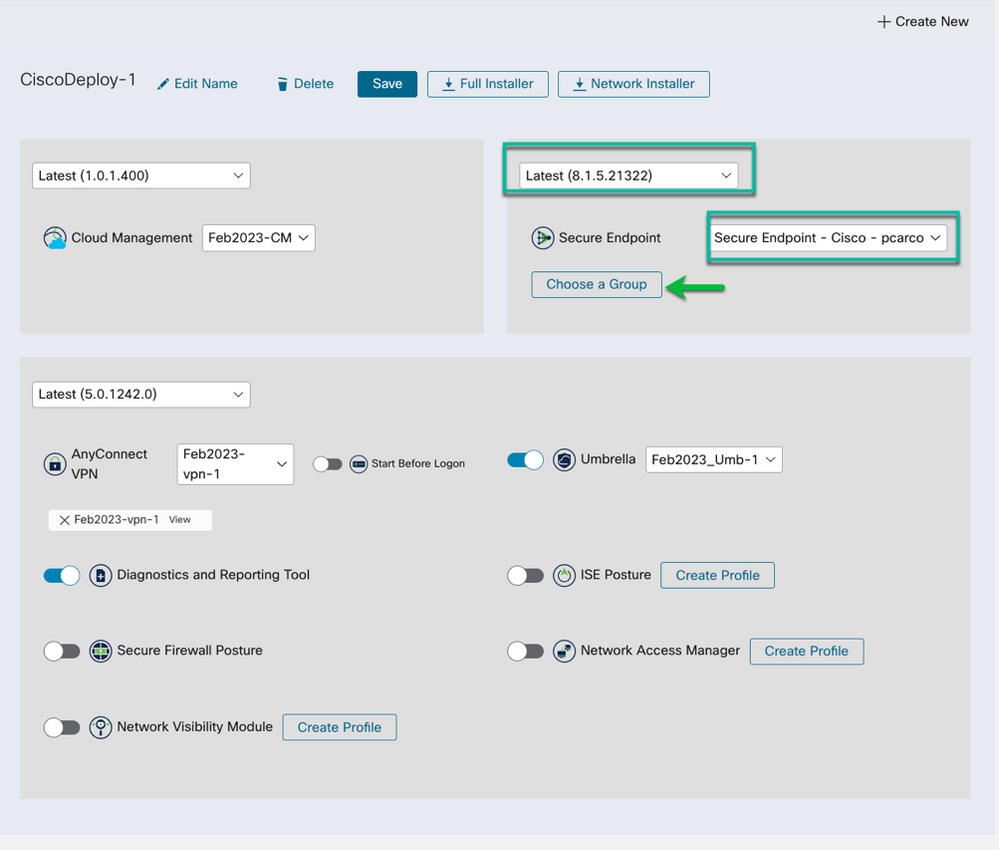
In the deployment as with all the other sections the first step is to choose a SE version and update channel. Keep in mind that SE can be upgraded by the SE Cloud if the SE Policy is edited, and a higher version is chosen after the fact. This is an initial bootstrap to get SE integrated in CSC.
Figure 32 Select the Cisco Secure Endpoint software version and Update channel.
An Instance needs to be selected and in a lot of cases there will only a single instance. The instance is the SE Business that is linked to SecureX. There could be situations where multiple instances of SE are linked to your SecureX Organization thus available for use in CSC Deployments.
Figure 33 Lates software selected & select the Cisco Secure Endpoint instance to use.
Once the instance of SE is chosen the last step is to select the SE group that will be assigned to users that have this deployment installed. The groups would have already been configured in SE and available.
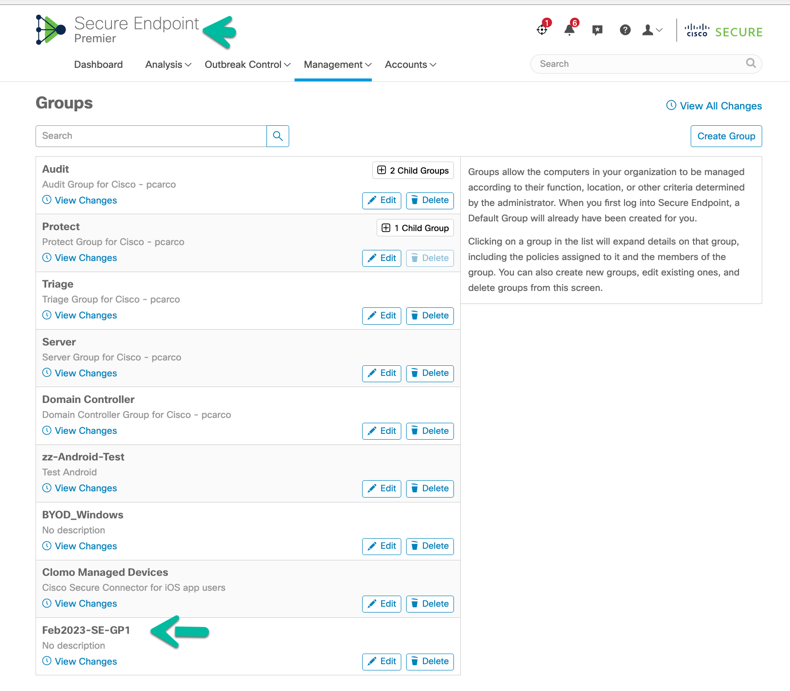
Figure 34 Cisco Secure Endpoint Groups available in the Cisco Secure Endpoint Console.
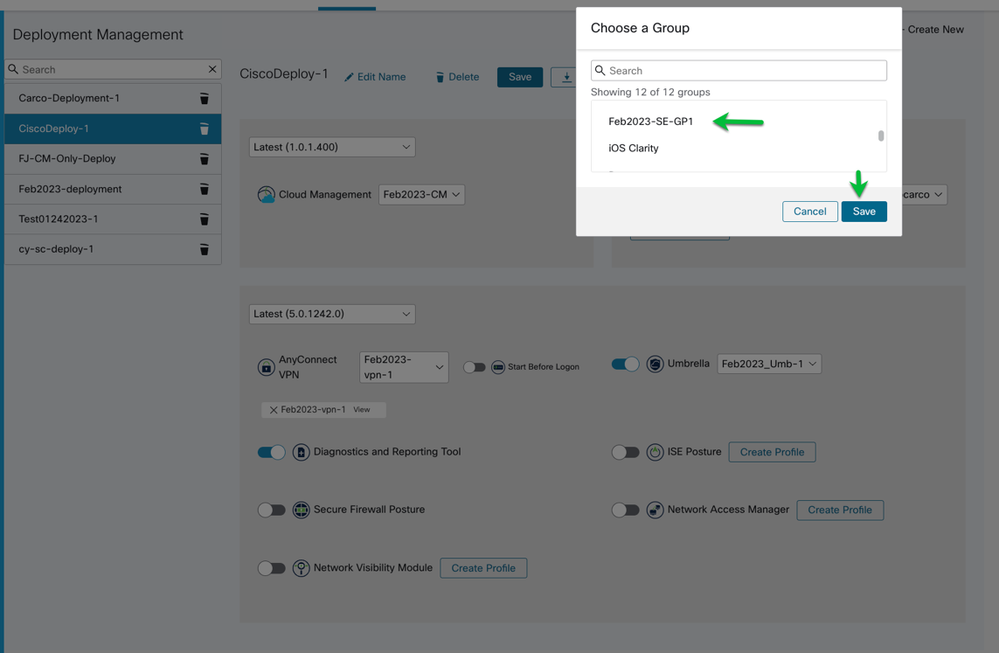
Use the Choose a Group button to bring up a window to choose the group. We are looking for the Group Feb2023-SE-GP1 shown above in SE’s group list.
Figure 35 Select the CSE Group and assign to the Deployment.
Search on the Group Name or scroll to locate the group, select, and save.
Figure 36 Groups are pulled directly from the CSE Console.
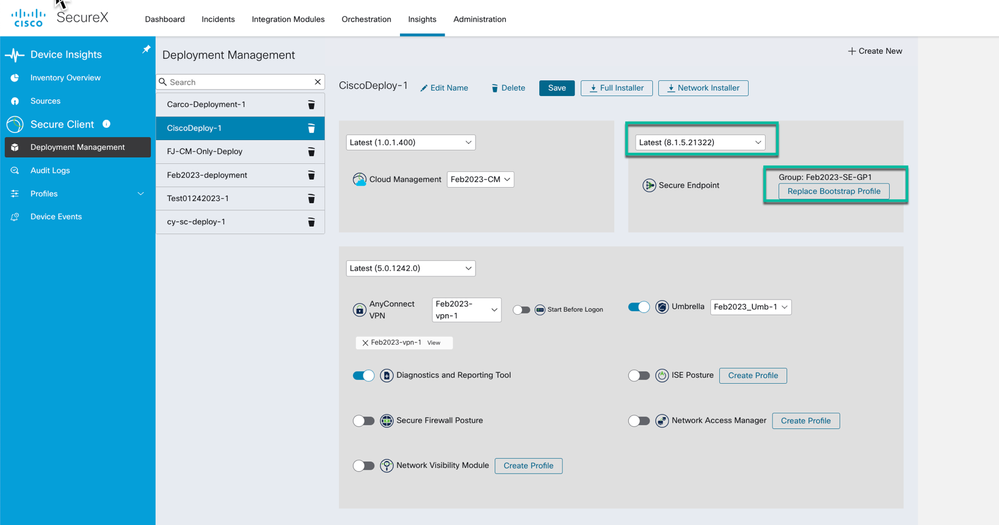
After the Group has been selected and saved you may need to save the deployment and refresh the screen so that the SecureX UI shows the actual group name in the deployment
Figure 37 Cisco Secure Endpoint section completed.
This concludes the Secure Endpoint configuration in the deployment and the deployment CiscoDeploy-1 is now ready to be downloaded, distributed, and installed.
installing the deployment
Figure 38 Select an Installer.
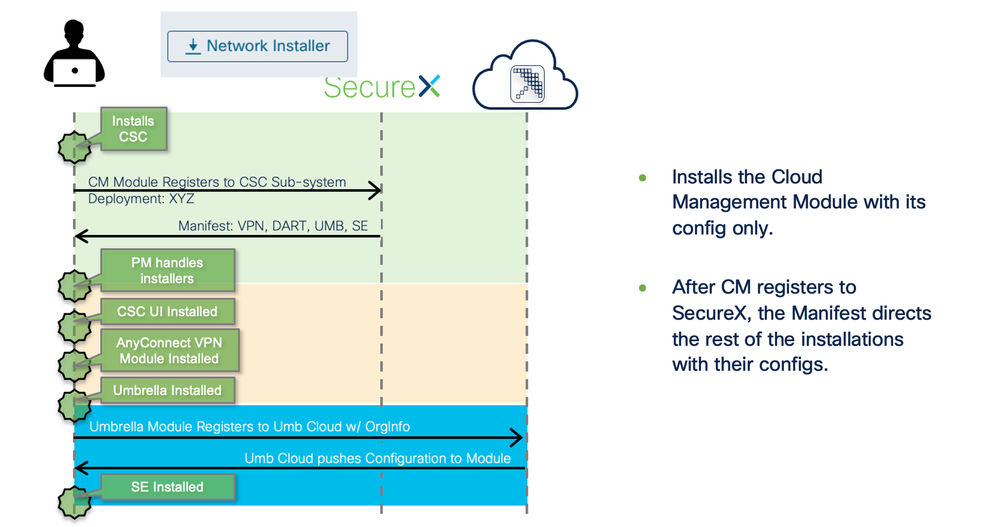
As explained earlier there are two options for the installer: Full or Network In either case we need one of the installers on the endpoint using one of the methods listed below.
- Using a Device Manager
- Using your own endpoint software manager
- However, your company normally pushes software.
Deployment INSTALLATION – CISCO SECURE CLIENT using The Network Installer
We will do a manual installation of the Network Installer and show the progress and the final installation result and point out the file (Profiles) locations on the endpoint. The Full Installer would behave like how AnyConnect has always been installed using the MSI from a product like SCCM or similar.
Figure 39 Network Installer Flow
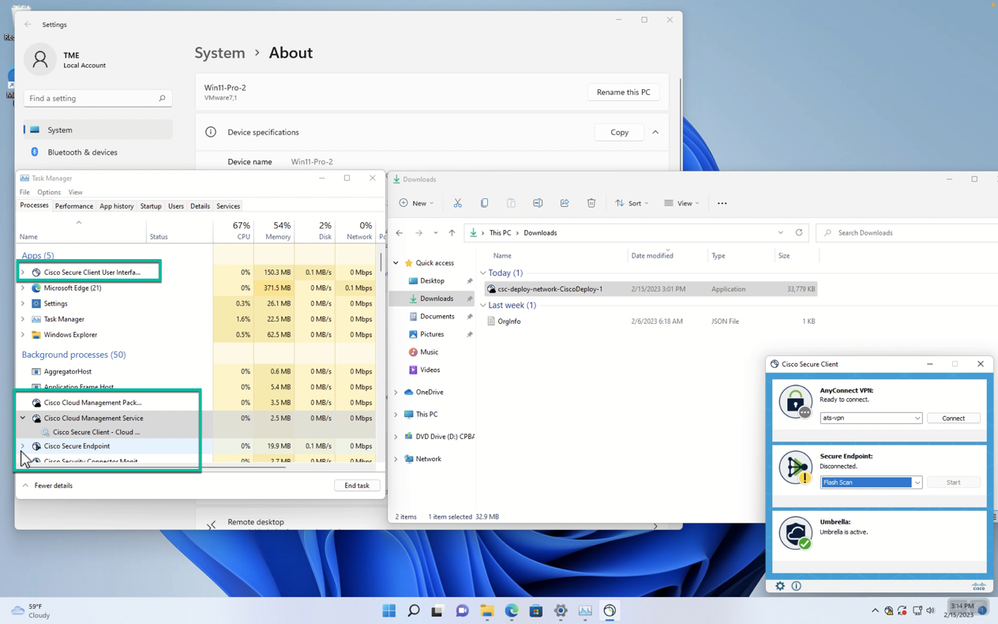
Since this is a manual install of the Deployment package the executable is run directly with Admin rights. Task Manager open to view the processes created during the install.
Figure 40 Installer in progress
Not long after the deployment tool is completed the Cloud Management reaches out to SecureX and based on the manifest installs the deployment and the new UI appears for the first time. Secure Endpoint is always installed last and will be in a disconnected state until it successfully syncs with the Secure Endpoint Cloud.
Figure 41 Monitoring Task Manager during install.
- After Secure Endpoint Has Connected, we are running an initial scan so that we can verify in the Secure Endpoint Cloud. Note the flyout window for the status of the scan occurring.
Figure 42 Initial Cisco Secure Endpoint Scan from the new CSC UI
- After you have deployed the connector, the installed-on endpoints will begin to appear on the computers screen.
- Navigate to Management > Computers. The computer list shows all the endpoints that have installed the connector.
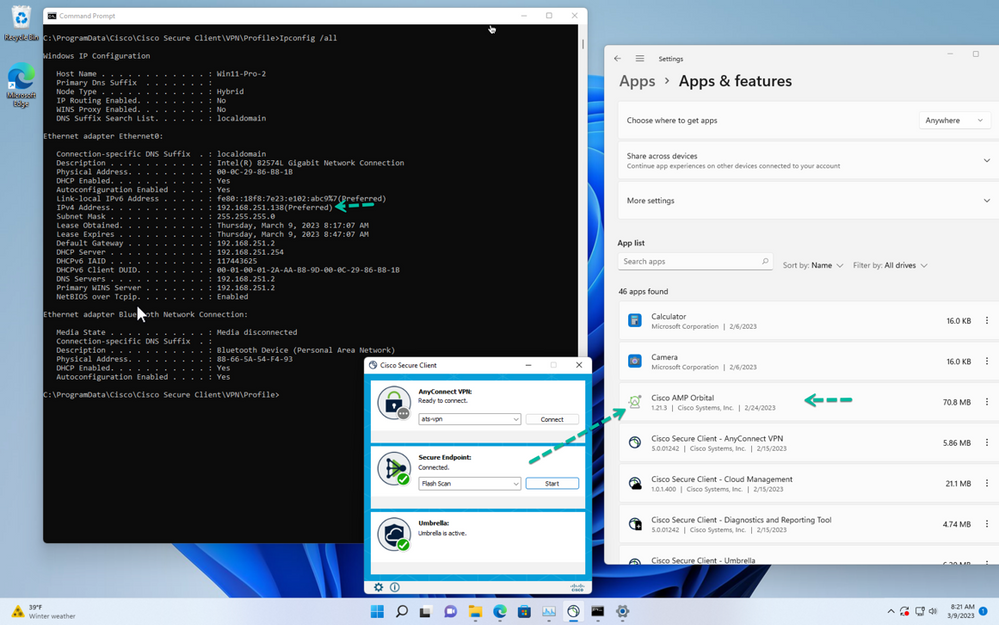
- The top of the page displays a summary of some key computer metrics, such as how many computers require AV and connector updates, and how many computers have faults requiring attention. In our case we are looking for the Win11-Pro-2 device.
Figure 43 Cisco Secure Endpoint Console > Computers
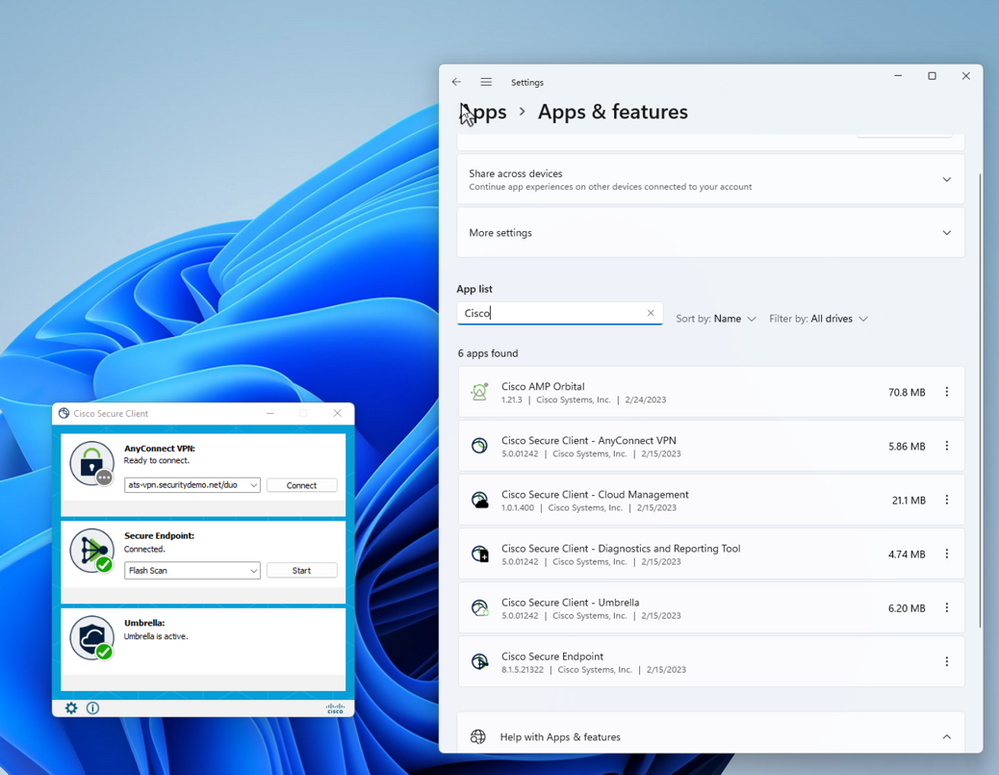
Although we did not directly configure and install Orbital up above it was in fact installed on the endpoint since the Cisco Secure Endpoint Policy specified that endpoints assigned the policy get Orbital.
Orbital is a service that uses osquery to provide you with information about your hosts.
“osquery exposes an entire operating system as a relational database that you can query with SQL to gather information about the host. Orbital can be used by both Cisco customers and their applications to query their computers wherever Orbital has been deployed.”
Orbital which operates in near real time also provides an API that can be used to drive queries. Customer apps would be built against those APIs for investigative purposes. Orbital includes hundreds of tested queries but flexible to allow you to create your own custom queries.
Figure 44 Orbital installed by Cisco Secure Endpoint.
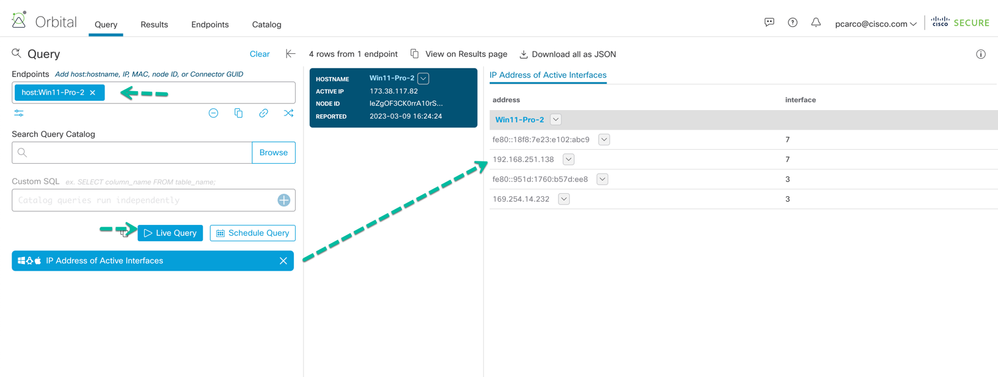
As an Orbital Administrator you can search for endpoints that have Orbital installed and run a live query from one of the may pre-defined queries. Just as an example we are performing a simple query to determine the IP addresses and active interfaces on the endpoint.
Figure 45 Orbital Live query results
Verification of the endpoint in SecureX Device Insights
Now that we have fully deployed Cisco Secure Client to the endpoint, we will take a look at the SecureX Inventory to get visibility into the endpoint. As mentioned earlier SecureX device insights provides you with a unified view of the devices in your organization by consolidating inventories from integrated data sources.
Cisco Secure Client when deployed with Cloud Management is a source for Device Insights therefor your endpoints are added to the SxDI inventory for unprecedented visibility especially when combined with other integrated sources.
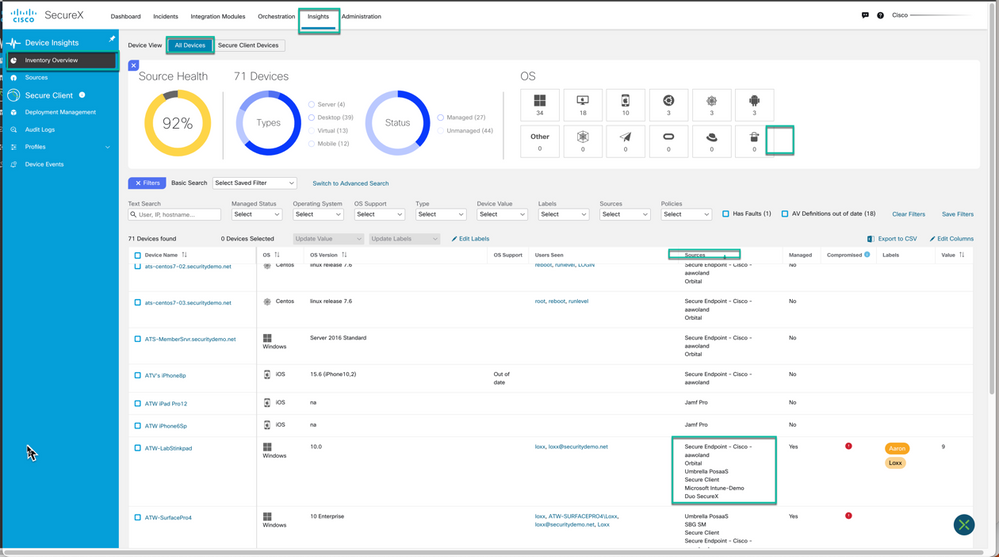
When an Admin first visits the Device Insight inventory, this inventory includes an unfiltered view of the entire asset inventory based on the integrated sources that have been configured. Device Insights offers very flexible filtering options to help the administrator sort the inventory.
Figure 46 Unfiltered Asset Inventory
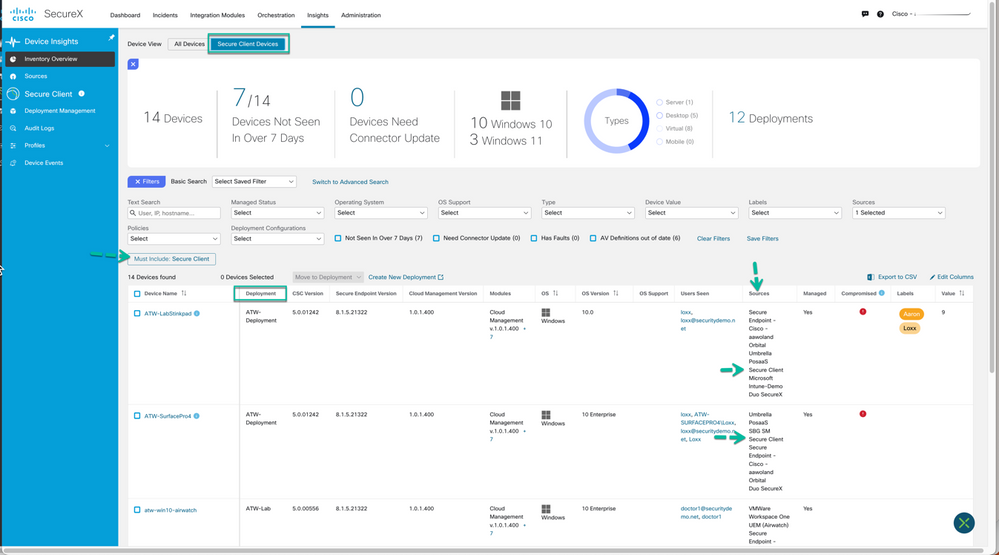
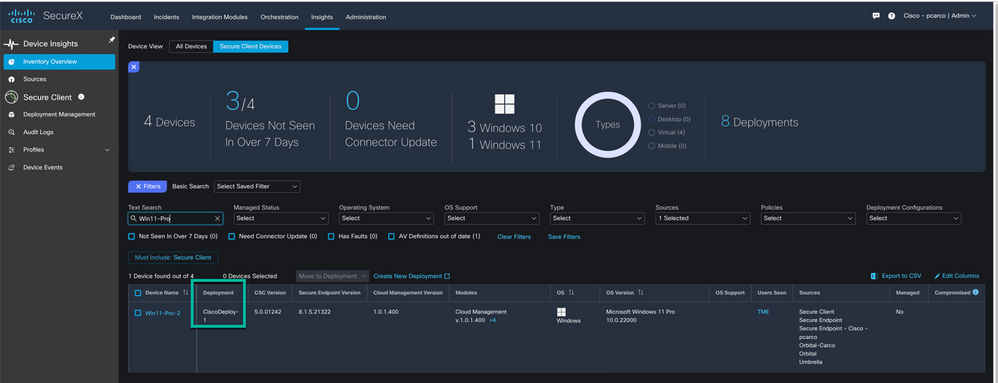
To simplify sorting on endpoints that you have deployed Cisco Secure Client on we have made sorting it as simple as clicking the ‘Secure Client Devices’ button to the right of ‘All Devices’ which will present you with only the endpoints that include but not limited to Cisco Secure Client. Some of the key pieces of information the admin would expect to see is Device Name, Deployment, CSC Version Secure Endpoint Version, Cloud Management Version, Modules etc.
A key capability of an action you can take on the inventory is the ability to move and endpoint from one deployment to another. A good example of when you might do this is, you have deployed using a single deployment with Cloud Management, Secure Endpoint, VPN and Umbrella and now you have a subset of users that require the Network Visibility Module you would create a new deployment that has all of what they have now plus NVM. You then would identify the endpoints in the inventory, place a check next to the endpoints and select move deployment and the new deployment you wish to use. When the endpoint checks in next, they will be updated.
Figure 47 Inventory sorted on Secure Client Devices
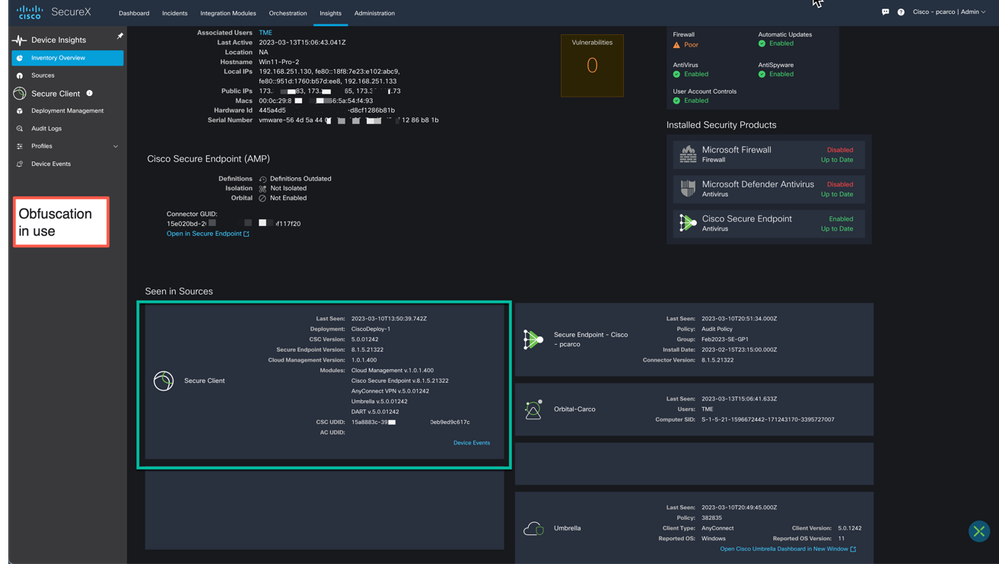
Now let’s drill down on and endpoint that has Cisco Secure Client deployed and is cloud managed by SecureX. Shown below we have drilled down a specific endpoint in the inventory to highlight the visibility you now have in SecureX by using Device Insights with multiple configured sources including Cisco Secure Client.
Figure 48 CSC source card in Device Insights
Move Deployment Feature
As mentioned earlier the abiiity to move endpoints to a new deployment from the inventory is a simple task. We initially deployed this endpoint shown below with, Cloud Management, Secure Endpoint, AnyConnect VPN and Umbrella. We are going to create a new deployment and move this endpoint to add another module not originally deployed and not intended for every endpoint in the current deployment.
Figure 49 Endpoint with Initial deployment
The target endpoint of the deployment move is currently configured to use the deployment ‘CiscoDeploy-1’ with modules mentioned above.
Figure 50 Current Deployment assigned.
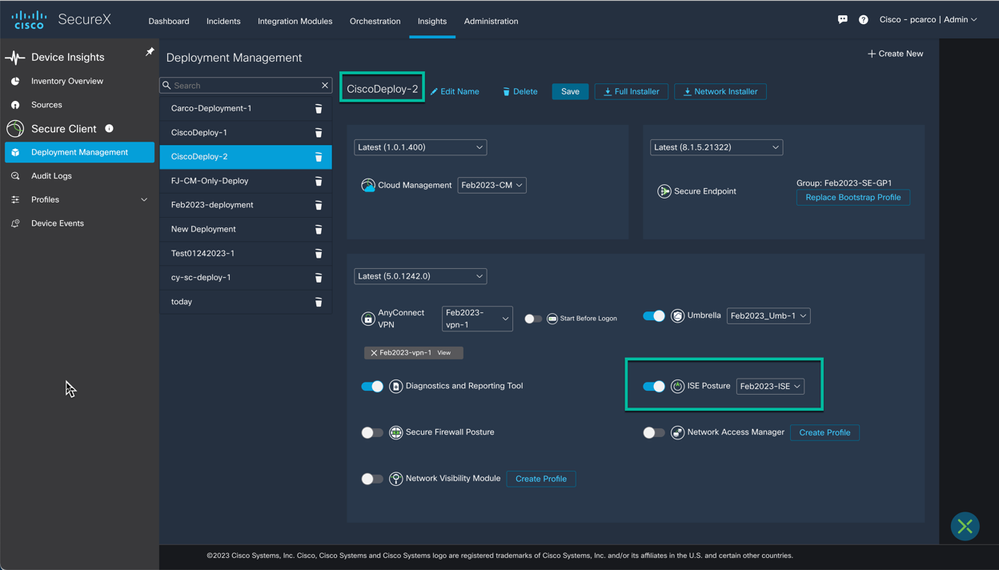
We have created a new deployment ‘CiscoDeploy-2’ and in addition to Cloud Management, Secure Endpoint, AnyConnect VPN and Umbrella the endpoints that are added or moved to this deployment will also have the ISE posture module and profile installed.
Figure 51 New Deployment
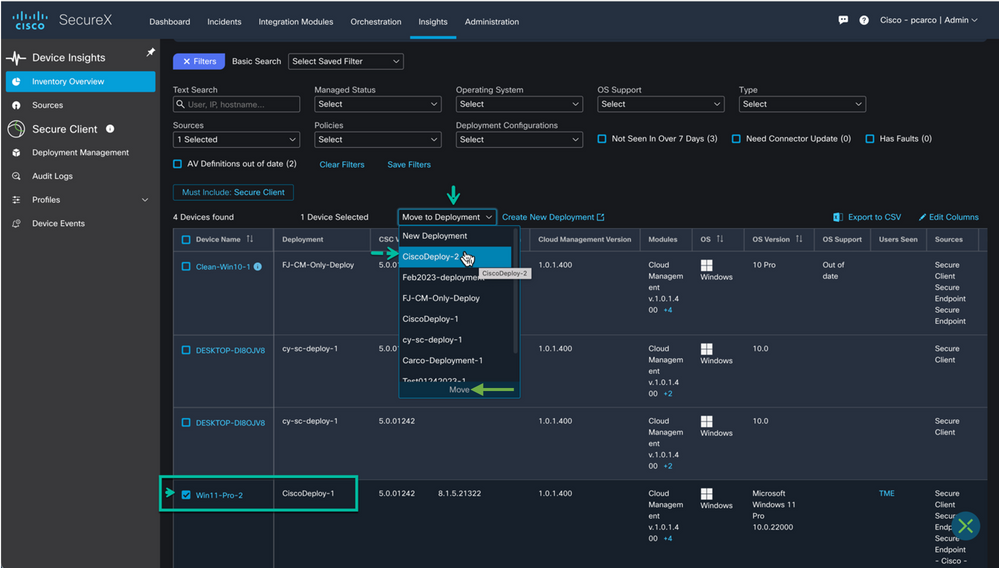
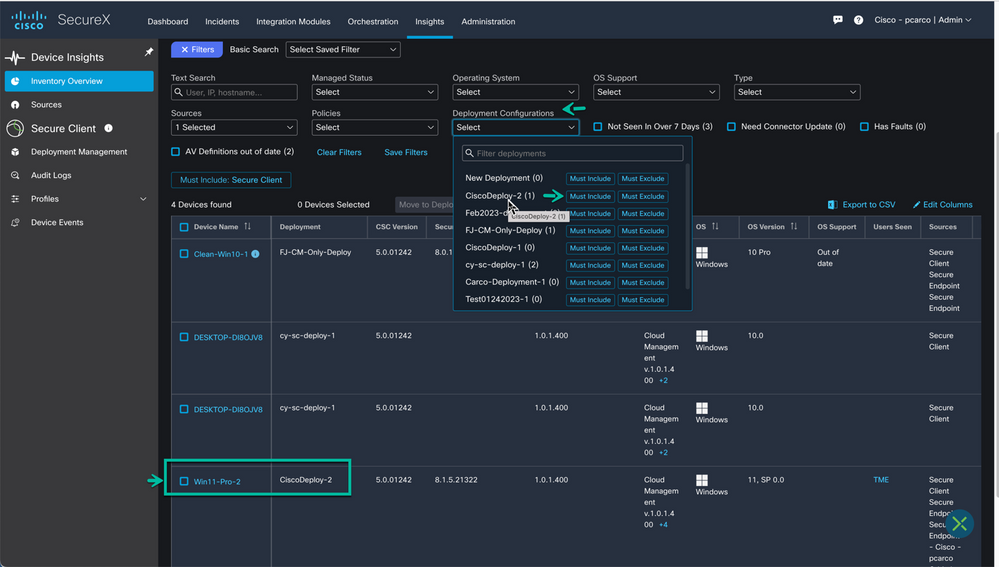
Identify the endpoint (device) you want to move and place a check next to the Device Name. Use the ‘Move to Deployment’ button and choose from the list of available deployments the new deployment ‘CiscoDeploy-2’ and hit ‘Move’
Figure 52 Move the deployment.
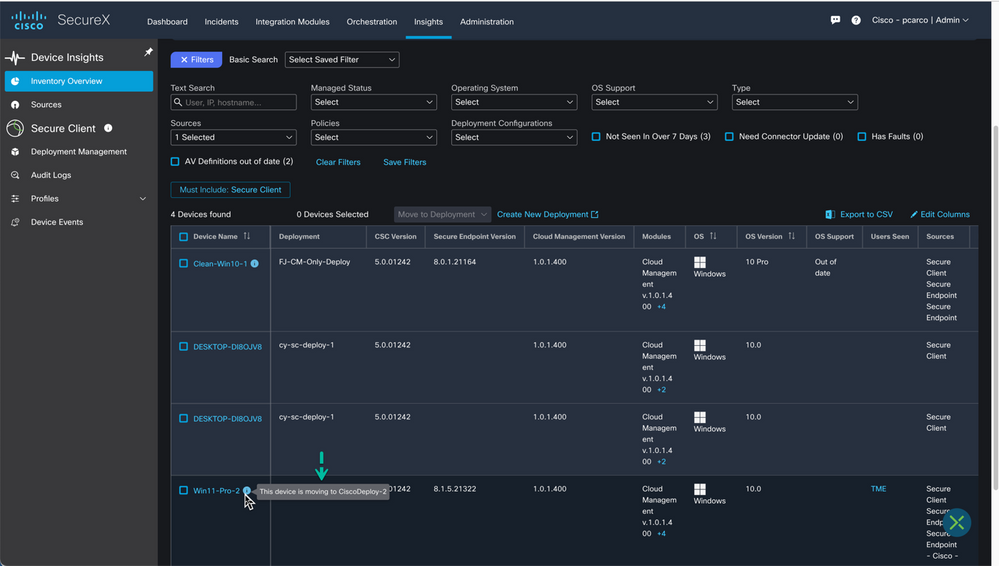
After confirming the move to a new deployment, the status on the endpoint(s) will indicate that a move is pending waiting for the device to check in with the cloud which at that time the device will receive the new deployment ‘CiscoDeploy-2’
Figure 53 Pending Deployment move.
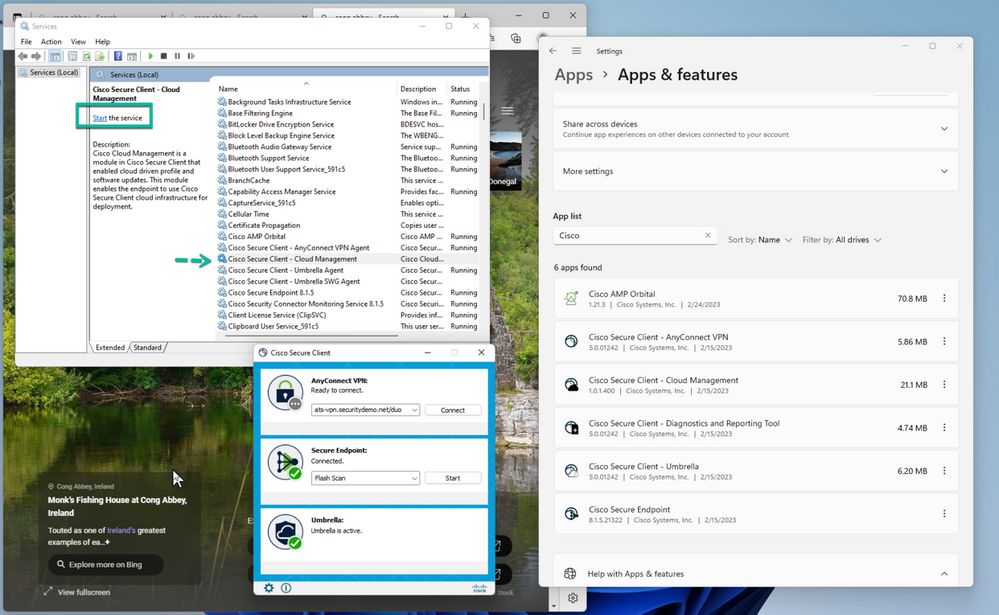
For the purposes of a demo here, we have stopped the CM service and a restart will cause the device to immediately attempt to reach out to the cloud. If we didn’t do this, we would need to wait 2 hours for endpoint to reach out which is the frequency configured in the Cloud Management Profile.
Figure 54 Cloud Management Service Stopped
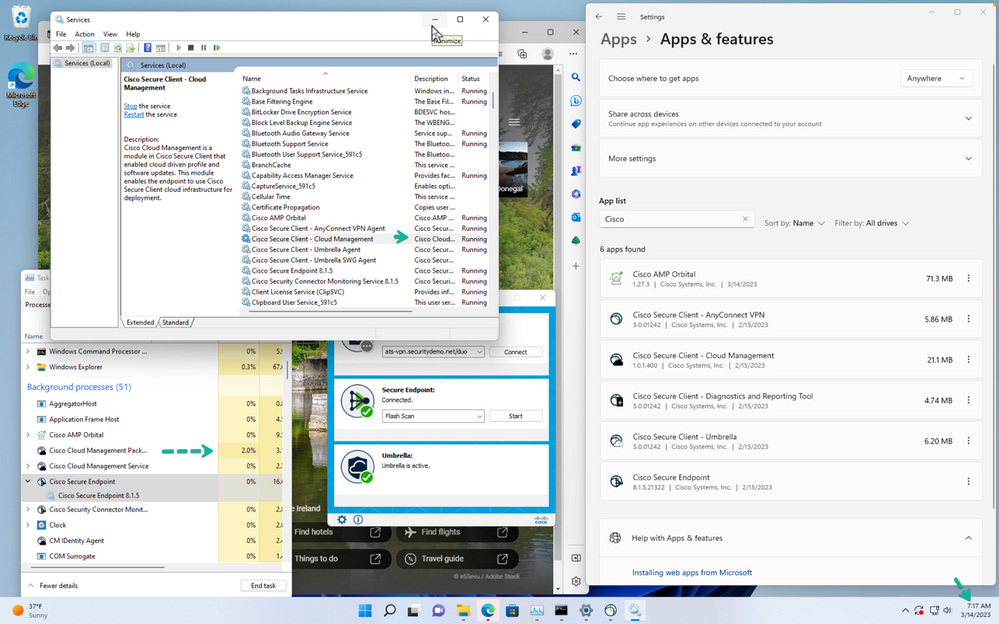
We have restarted the Cloud Management service and notice immediately looking at the Task Manager that it is running and expect the device is checking in with the Cloud.
Figure 55 Cloud Management Restarted.
Not long after Cloud Management reaches out the endpoint has received the new deployment with the new module configured in the CiscoDeploy-1 deployment.
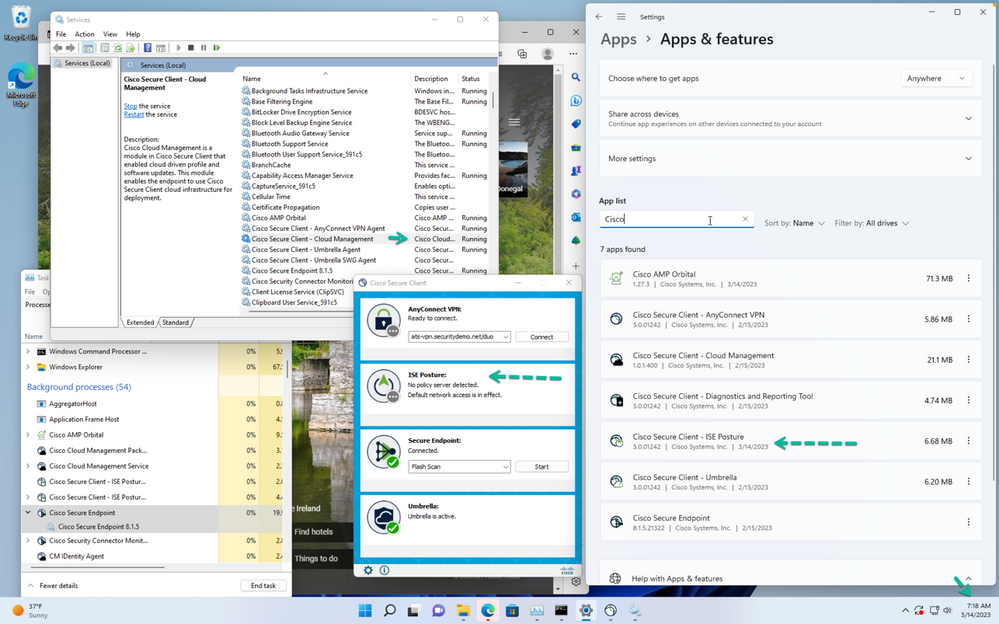
Figure 56 New Module added.
We now return to the SecureX Device Insights inventory to view the device now listed as having the new CiscoDeploy-2 deployment.
Figure 57 New Deployment assigned
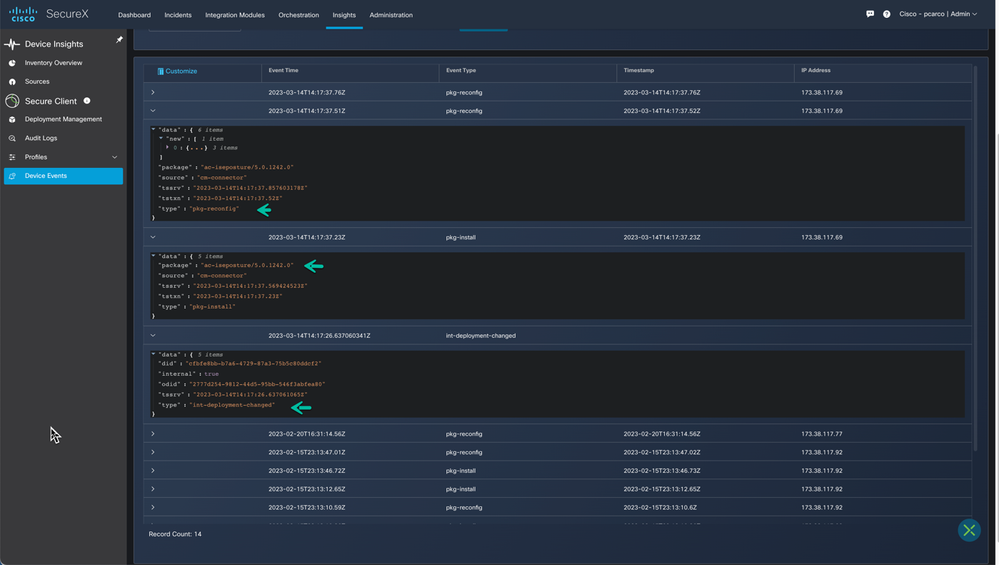
Device Events provides both a record of Devices leveraging the Cloud Management feature in Secure Client on the SecureX platform and Deployment activity for those devices. In our case we are filtered on Win11-Pro-2 to view the events specific to this device.
Figure 58 Device Events
Drill down on the specific event to get more details regarding the event(s). In this case we can see that events were specific to the deployment change and the ISE Posture module being installed with a profile.
Figure 59 Device Event Drill down.
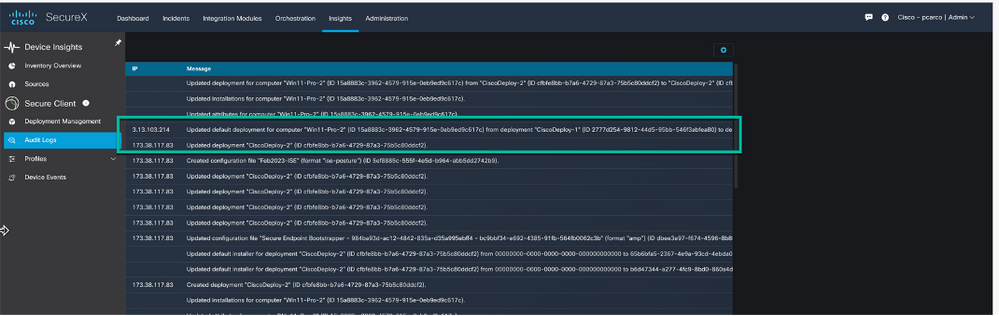
Audit logs provide a record of creation, modification, or deletion tasks performed by Secure Client users on the SecureX platform. In this case we are looking at the logs specific to the new deployment.
Figure 60 Audit logs.
END
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: