- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Cisco Secure Firewall Device Manager - SNMP configuration using API
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-06-2021 04:23 AM - edited 11-08-2023 12:03 AM
Problem:
SNMP on FDM was introduced in version 6.7. As of now, we only have the option to push via API. The current method is time-consuming, and knowledge of API is needed.
Here is the current guide we have.
https://www.cisco.com/c/en/us/support/docs/security/firepower-ngfw/216551-configure-and-troubleshoot-snmp-on-firep.html
Solution
@Dinesh Verma and I created a script that automates the entire workflow using Python. You only need to enter the details pertaining to SNMPv2/SNMPv3; the script takes care of everything else. The script is available in the following GitHub repository.
https://github.com/anupamx47/FDM-SNMP/tree/main
1) Preparation:
1.Download the Script:
- Go to the script's GitHub page: fdm-snmp.py.
- Click the "Download Zip" button, under "code" to download the Python script to your computer.
2.Install Python:
- Make sure you have Python installed on your computer. You can download and install the latest version of Python from the official Python website: Python Downloads. Follow the installation instructions for your operating system.
3.Install Required Dependencies:
- Open a command prompt or terminal.
- Navigate to the directory where you downloaded the script.
- Run the following command to install the necessary dependencies:
pip3 install -r requirements.txt
4.Execute the Script:
- Open a command prompt or terminal.
- Navigate to the directory where you downloaded the script using the cd command.
- Run the script using Python:
python3 fdm-snmp.py
****************************************************************************************************
2) Create SNMPv2 Host
| C:\Users\anpavith\OneDrive\Desktop\scripts\FDM-SNMP> python3 fdm-snmp.py ########################################################### # CONFIGURE SNMP ON FDM # ########################################################### Enter the device IP address: 10.106.55.56 Enter the username of the FTD: admin Enter the password of the FTD: ########################################################### Auth-Status code is 200 Successfully Authenticated Would you like to configure (1) SNMPv2 or (2) SNMPv3 : 1 Enter the SNMP Server object name : solar22 Enter the SNMP Server object IP : 22.22.22.22 Enter SNMPv2 community string : cisco123 ########################################################### 1 diagnostic Management0/0 2 dmz GigabitEthernet0/2 3 inside GigabitEthernet0/1 4 outside GigabitEthernet0/0 Select the interface (Integer value only) : 4 Enter SNMP host object name : snmp22 ########################################################### Successfully Created, please deploy and check SNMP config ########################################################### |
3) Create SNMPv3 Host along with SNMPv3 user
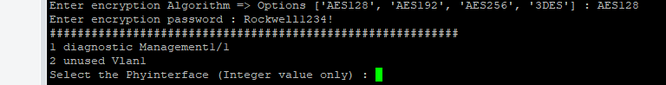
| C:\Users\anpavith\OneDrive\Desktop\scripts\FDM-SNMP> python3 .\fdm-snmp.py ########################################################### # CONFIGURE SNMP ON FDM # ########################################################### Enter the device IP address: 10.106.55.56 Enter the username of the FTD: admin Enter the password of the FTD: ########################################################### Auth-Status code is 200 Successfully Authenticated Would you like to configure (1) SNMPv2 or (2) SNMPv3 : 2 Enter the SNMP Server object name : solar21 Enter the SNMP Server object IP : 21.21.21.21 Enter SNMPv3 username : cisco21 Enter Security Level => Options ['AUTH', 'NOAUTH', 'PRIV'] : PRIV Enter authentication Algorithm => Options ['SHA', 'SHA256'] : SHA Enter authentication password : cisco123 Enter encryption Algorithm => Options ['AES128', 'AES192', 'AES256', '3DES'] : AES128 Enter encryption password : cisco123 ########################################################### 1 diagnostic Management0/0 2 dmz GigabitEthernet0/2 3 inside GigabitEthernet0/1 4 outside GigabitEthernet0/0 Select the interface (Integer value only) : 4 Enter SNMP host object name : host21 ########################################################### Successfully Created, please deploy and check SNMP config ########################################################### |
Please use the script and provide us with any feedback.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@MSJ1 in FDM make sure you have assigned an address to the diagnostic interface. Then create a static route tied to that interface.
Regarding script execution it should not require you do anything special to the file on windows. I used Visual Studio code on my Windows 10 PC to run and debug the script just fine without having to modify file permissions .
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I was able to run the script directly on the FDM device itself using python3 by just search and replacing the raw_input( ) python functions with just input( )
admin@ftd.ip.address's password: [enter password]
Cisco Firepower Extensible Operating System (FX-OS) v2.10.1 (build 159)
Cisco Firepower 1010 Threat Defense v7.0.0.1 (build 15)
> expert
admin@MyFtd:~$ sudo su
Password: [enter password]
root@MyFtd:/home/admin# vi fdm-snmp-onbox.py
i <-- "Insert" mode in vi
[now paste the py file, first changing "raw_input" to "input"]
:s! <-- this saves the file in vi
:q <-- quit vi
root@MyFtd:/home/admin# python3 ./fdm-snmp-onbox.py
###########################################################
# CONFIGURE SNMP ON FDM #
###########################################################
Enter the username of the FTD:
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have been trying this for a while now, and when i open the script from cli using python, or using visual studio code it just errors out on "Import requests"
ModuleNotFoundError: No module named 'requests'
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Anupam Pavithran Is there anyway to get this to work with subinterfaces? our management subnet is a subinterface on our FDM, if I choose the inside interface which all the subinterfaces are on it doesn't work. Our Management port also has a IP thats on the same subnet as the subinterface that I would need to monitor it from. I attempted to give the diagnostic interface an IP on the same subnet but it tells me it can't because it overlaps with a subinterface.
EXAMPLE:
Subinterface 1/2.10 IP 172.30.110.1/24 standby unit 172.30.110.2/24
Management interface 172.30.110.7/24 standby unit 172.30.110.8/24
Diagnostic NO IP
if I try to give the Diag port 172.30.110.11/24 standby 172.30.110.12/24 it says no
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@jsellarshave a look at this: python - ImportError: No module named requests - Stack Overflow
It workerd for me.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Experts,
I am trying to test the script, but all the inside and outside interfaces are not showing. I am having subinterface in my environment, how can I get those.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi All, Thx guys for these scripts.
Just a very naive question, I´m trying to use the scripts but I receive the answer "auth_token not found", is there any configuration to do in FDM before running the script ?
Thx in advance,
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
How are you getting the script onto the box and what directory does it need to be in?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@codewize the script runs on your local computer and uses the REST API to access features and functions of the firewall,
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Marvin Rhoads Hi sir, please help me this case, I run the script release ver 1.3, however my internal FDM interface using etherchannel (Port-Channel), so the script can not show the internal interface, any helps for this case sir please. Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@TimBS I would defer to @Anupam Pavithran as he is the author of the script. Otherwise you may have to take apart the code and modify it on your own.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@TimBS , I've added an update version "fdm-snmp_1.3-1.py" which supports port-channel. Please try and let me know if it works for you.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Anupam Pavithran Hi, sorry but may I know the link to download the ver sion 13.1-1? the original post not yet updated. Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I'm having an issue on Firepower 1010s where if I remove my now depreciated FlexConfig SNMP config I can't get it to work.
the script seems to run fine but doesn't enable the SNMP-server but when I look at the config with "show running-config snmp-server" I see the config below:
snmp-server group AUTH v3 auth
snmp-server group PRIV v3 priv
snmp-server group NOAUTH v3 noauth
snmp-server user crtech PRIV v3 engineID 80000009fe027acad6ddffbc522093b24cfe1016ed33cd11e1 encrypted auth sha 25:0c:7d:79:c1:e4:89:93:aa:24:b6:e3:2e:67:1d:0c:e0:73:24:4b priv aes 128 25:0c:7d:79:c1:e4:89:93:aa:24:b6:e3:2e:67:1d:0c
snmp-server host diagnostic xxx.xxx.xxx.xxx community ***** version 2c
snmp-server host diagnostic xxx.xxx.xxx.xxx community ***** version 2c
snmp-server host outside xxx.xxx.xxx.xxx version 3 crtech
snmp-server location null
snmp-server contact null
snmp-server community *****
no snmp-server enable <- This seems to be the issue.
Also would there be a way to remove these configs from the FDM?
My old flexconfig that worked looked like this
snmp-server enable
snmp-server group SNMP_RO_GROUP v3 priv
snmp-server user SNMP_RO_USER SNMP_RO_GROUP v3 auth sha cisco321 priv aes 128 cisco123
snmp-server host ngfw-management xxx.xxx.xxx.xxx version 3 SNMP_RO_USER
Also is it possible that we can get the ngfw-management interface added to the physical interfaces? as Cisco TAC told me that is the name of the port we would need to use to get it to come from the management interface IP like I previously had and not the diagnostic port.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: