- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Cisco TC-NAC with ISE and Tenable Security Center
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
04-25-2017
12:42 PM
- edited on
03-17-2022
09:25 AM
by
Jason Kunst
![]()
Contents
- Introduction
- Demo
- High Level Flow Diagram
- Configure Tenable Security Center and Nessus Scanner
- Configure Cisco Identity Services Engine
- Verify
- Cisco Identity Services Engine
- Tenable.sc
- Troubleshoot
- Support
- References
- Demo
Updated March 2022 in detail
Introduction
This document describes how to configure Threat-Centric NAC with Tenable Security Center on Identity Services Engine (ISE). Threat Centric Network Access Control (TC-NAC) feature enables you to create authorization policies based on the threat and vulnerability attributes received from the threat and vulnerability adapters.
Cisco recommends that you have basic knowledge of these topics:
- Cisco Identity Service Engine
- Tenable Security Center
- Tenable Nessus - trial software
Demo
The dCloud team is working on adding Tenable.sc TC-NAC to the ISE Enterprise Security & Ecosystems demo, please see cs.co/selling-ise-demos for more information. This should be released end of April 2022.
This document was lately verified with ISE 3.1. Please make sure your environment is on the latest recommended release.
High Level Flow Diagram
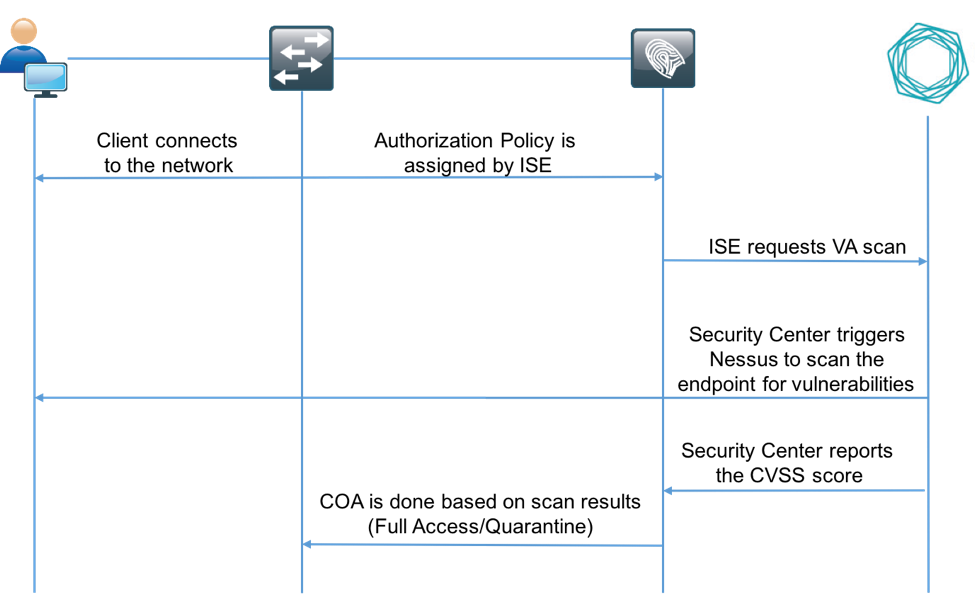
This is the flow:
1. Client connects to the network; limited access is given and profile with Assess
Vulnerabilities checkbox enabled is assigned.
2. PSN node sends Syslog message to MNT node confirming authentication took place and VA
Scan was the result of Authorization Policy.
3. MNT node submits SCAN to TC-NAC node (using Admin WebApp) using this data:
- MAC Address
- IP Address
- Scan Interval
- Periodic Scan Enabled
- Originating PSN
4. Tenable TC-NAC (encapsulated in Docker Container) communicates with Tenable Security Center (via REST API) to trigger scan if needed.
5. Tenable Security Center instructs Tenable Nessus Vulnerability Scanner to scan the endpoint.
6. Tenable Nessus Vulnerability Scanner sends the results of the scan to the Tenable Security Center.
7. Results of the scan are sent back to TC-NAC:
- MAC Address
- All CVSS Scores
- All Vulnerabilities (PluginID, title, CVEIDs)
8. TC-NAC updates PAN with all the data from the step 7.
9. CoA is triggered if needed according to Authorization Policy configured.
Configure Tenable Security Center and Nessus Scanner
Prerequisite: You must have Tenable.sc installed and at least one Tenable Nessus Vulnerability scanner installed. When registering the Tenable Nessus Vulnerability Scanner ensure that you choose managed by Security Center during registration.
Please follow Tenable getting started work flow for a complete guide of setup parameters
Note there are two accounts used on tenable.
1. The admin account to configure the system
2. a tenable security manager account used to setup scans, policies and other config. This account is also used on ISE for the TC-NAC configuration. Don't use the generic admin account (#1)
In order for ISE and Tenable to communicate they will need to trust each other via certificate SSL communication.
Export the System and Root Certificates from Tenable.sc
SSH to the Security Center and login as admin. The self-signed certificates are located in the /opt/sc/support/conf/ directory. The Root Certificate is named TenableCA.crt and the System Certificate is name SecurityCenter.crt. You will need to copy these files to your PC for later use. If you using Linux or a Mac, you can use the below syntax from the Security Center CLI.
If using windows, you can use a program like WinSCP or PSCP to copy the files.
sudo scp /opt/sc/support/conf/TenableCA.crt [username]@[your ip address]:TenableCA.crt
sudo scp /opt/sc/support/conf/SecurityCenter.crt [username]@[your ip address]:SecurityCenter.crt
Configure Cisco Identity Services Engine
Note: These screens are utilizing the 2.x UI and ISE 3.x looks slightly different, using the search capability of 3.x helps find the items quickly as well
Step 1. Enable Threat Centric NAC Service
To configure vulnerability and threat adapters, you must first enable the Threat Centric NAC service. This service can be enabled on only one Policy Service Node in your deployment.
Browse to Administration > System > Deployment
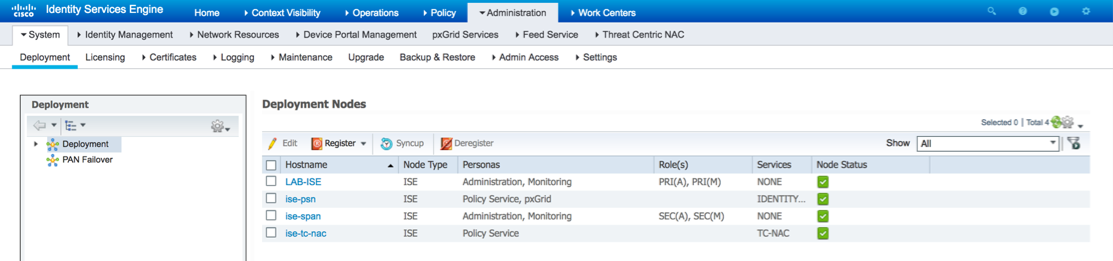
Select the PSN you wish to enable the Threat Centric NAC Service on and click edit.
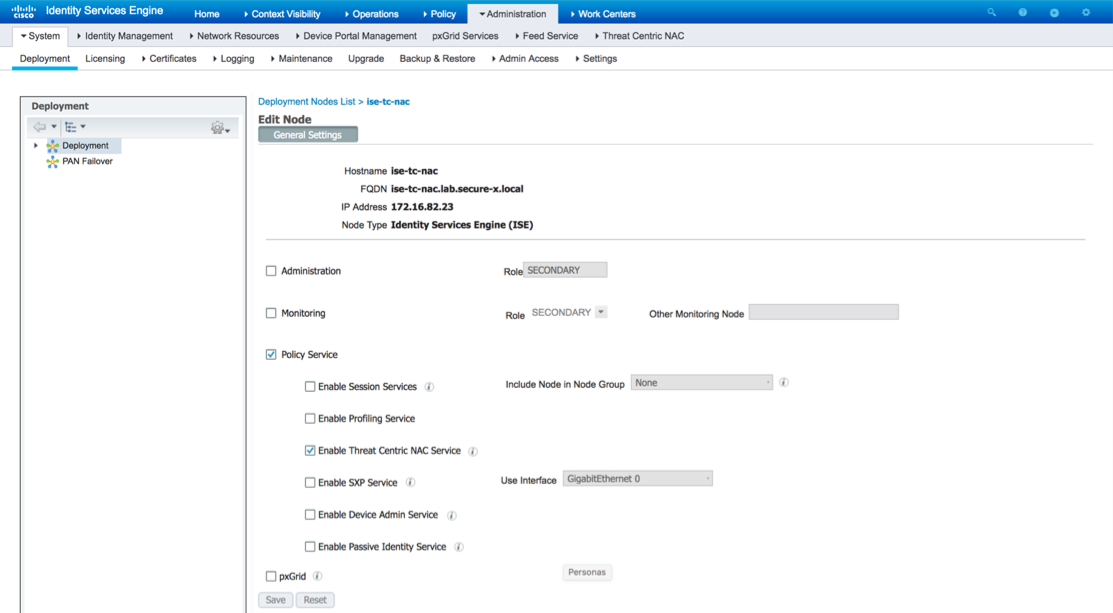
Select Enable Threat Centric NAC Service and click save.
Step 2. Import Tenable.sc Center Certificates
Browse to Administration > Certificates > Trusted Certificates. Select Import.
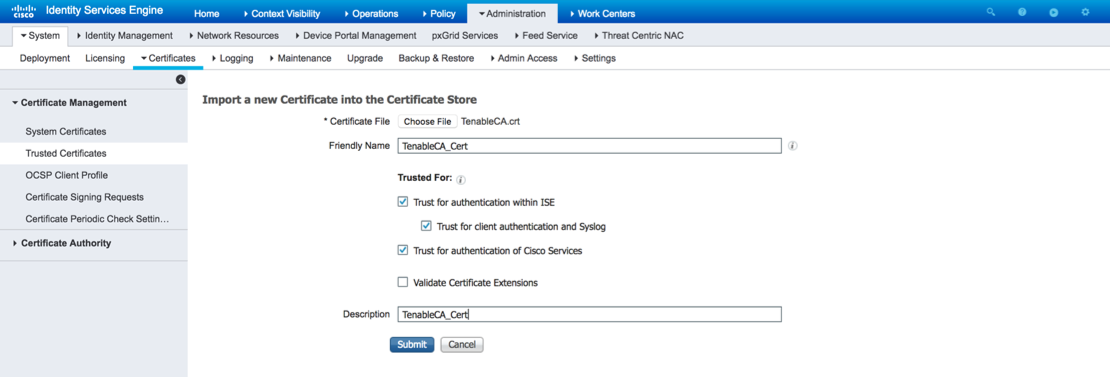
Repeat this procedure for the Security Center certificate.
Step 3. Configure Tenable Adapter
Browse to Administration > Threat Centric NAC > Third Party Vendors
Click Add.
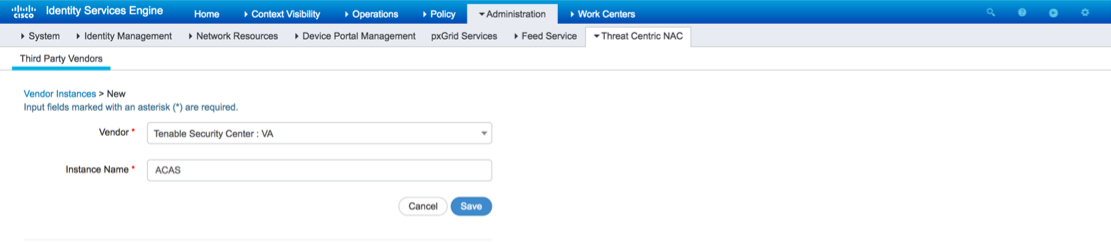
From the Vendor drop down menu select “Tenable.sc: VA”.
Give the adapter a custom instance name and click Save.
Refresh the Vendor Instances listing page. The status for the newly added Tenable Adapter should change to Ready to Configure.
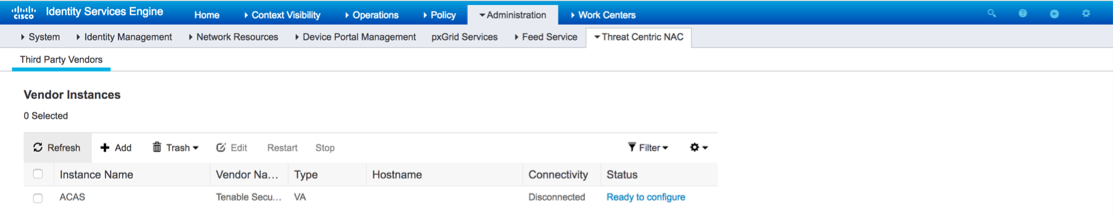
Click Ready to Configure.
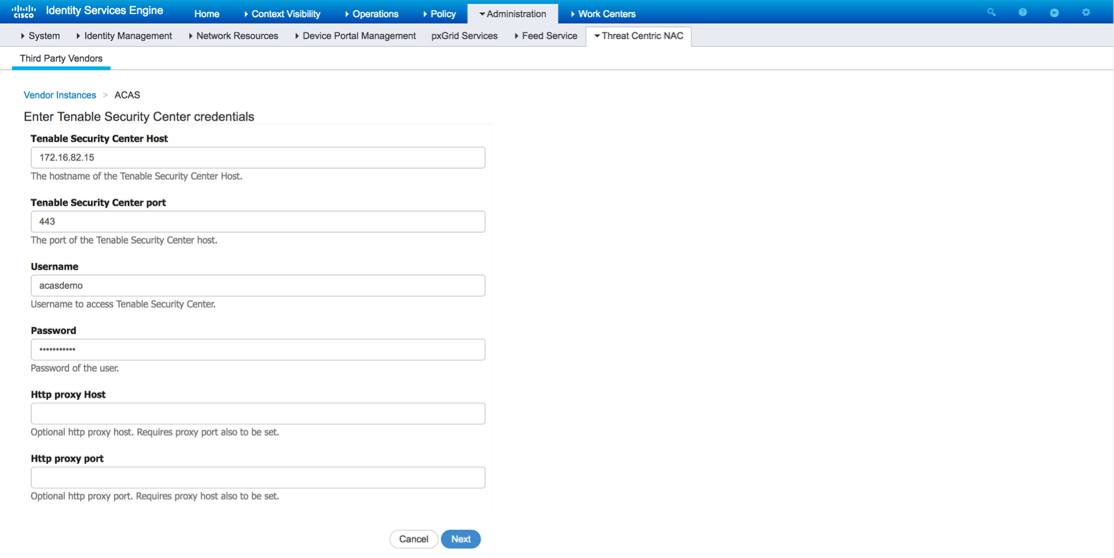
Enter the following information for the Tenable.sc.
- Tenable.sc Host: IP address or hostname
- Tenable.sc Center Port: 443
- Username: Security Manager account. Do not use an admin account.
- Password: Password for Security Manager account.
- HTTP Proxy Host: IP address or hostname of proxy if proxy is being used.
- HTTP Proxy Port: Port of proxy if proxy is being used.
Click next.
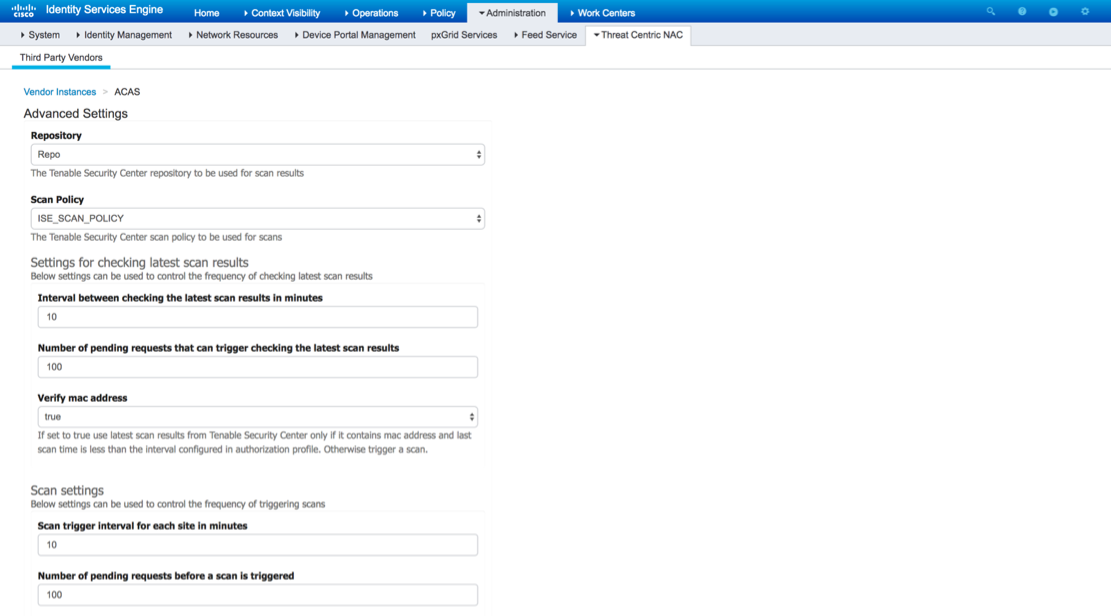
From the Repository drop down menu select the previously configured Tenable.sc Repository.
From the Scan Policy drop down menu select the previously configured Tenable.sc Scan Policy.
Setting for checking latest scan results and Scan settings are configurable per the needs of your environment. In this example, we are using the default setting.
Click next.
Under the Vendor Instances screen you should now see the newly configured Tenable Adapter is connected and active.
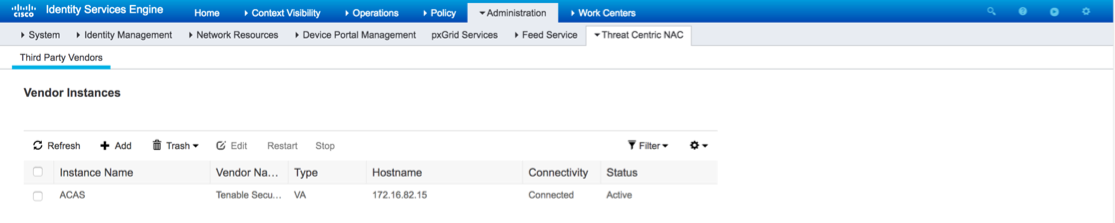
Step 4. Configure Authorization Profile
Browse to Policy > Policy Elements > Results
Select Authorization > Authorization Profiles from the menu on the left.
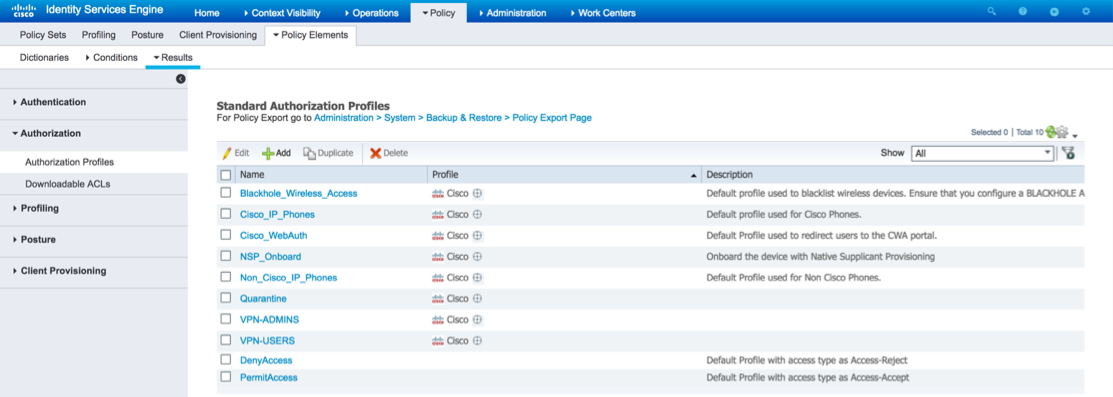
Click Add.
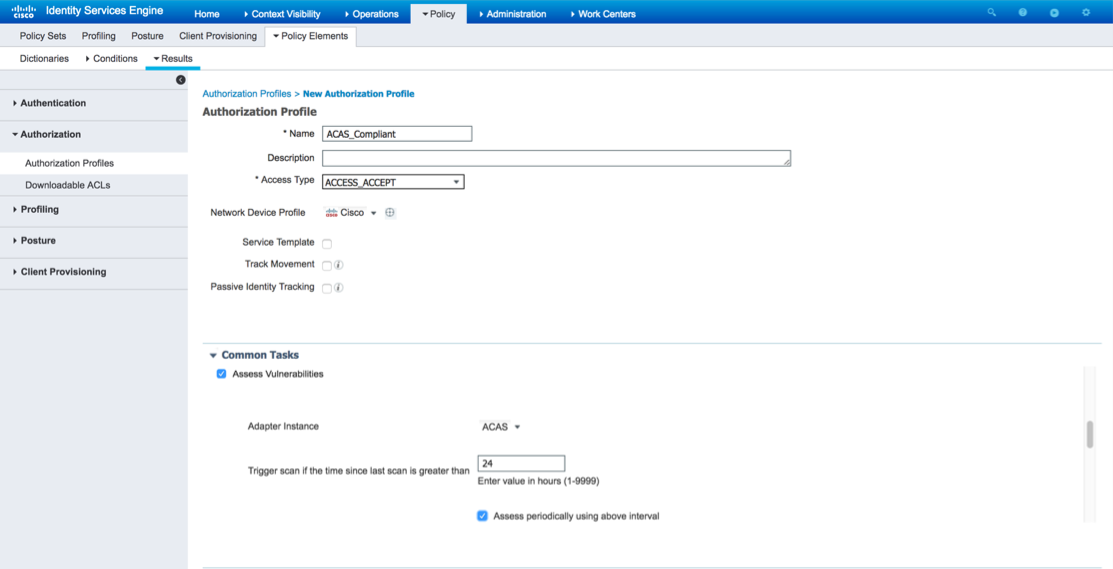
Name the Authorization profile. Under Common Tasks select Assess Vulnerabilities. From the Adapter Instance drop down select the previously configured Tenable Adapter instance. Configure the Trigger scan time in hours and click submit.
Step 5. Configure an Exception Rule to Quarantine a vulnerable endpoint.
Browse to Policy > Policy Sets
Select Global Exceptions from the menu on the left.
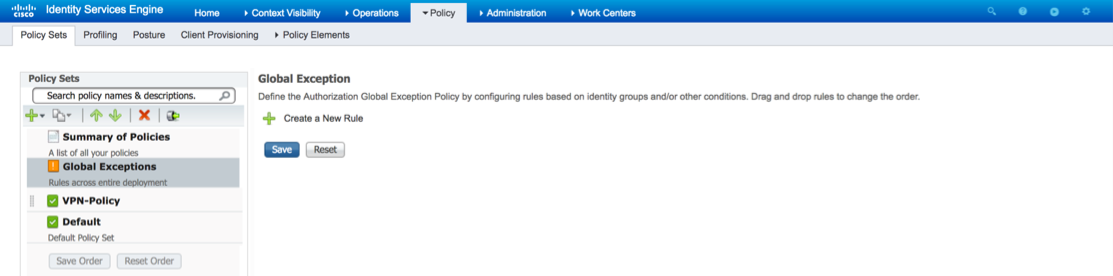
Select Create a New Rule
Name the rule. Create a condition to check for the Tenable CVSS score and assign the appropriate authorization profile. For example: Any Identity Group & Threat:Tenable.sc-CVSS_Base_Score > 5 > Quarantine (authorization profile). Click Save.
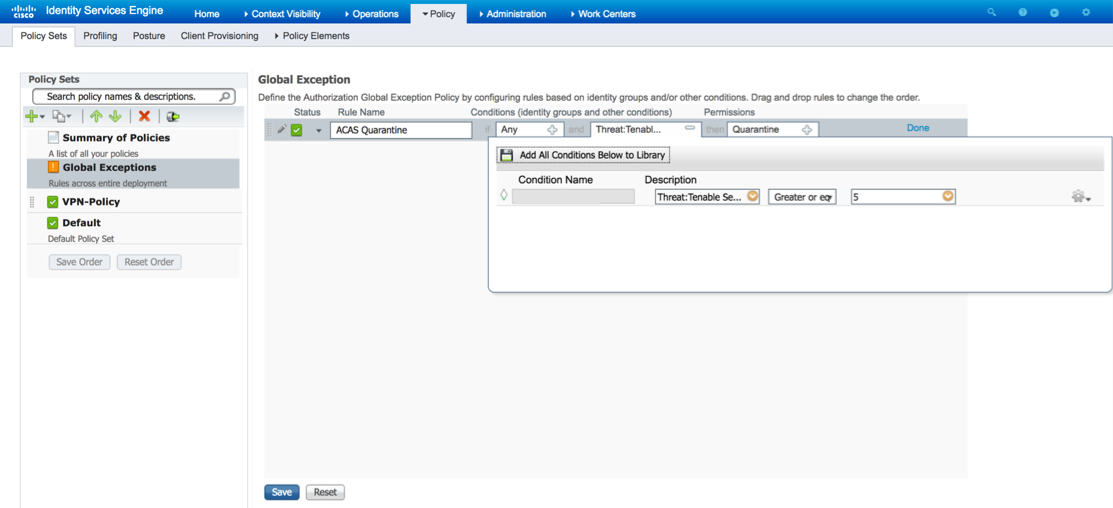
Step 6. Configure Authorization Policy
Browse to Policy > Policy Sets. From the menu on the left-hand side select default. Locate the Basic_Authenticated_Access rule and click edit. Change the permissions from permit access to the newly created Authorization Profile.
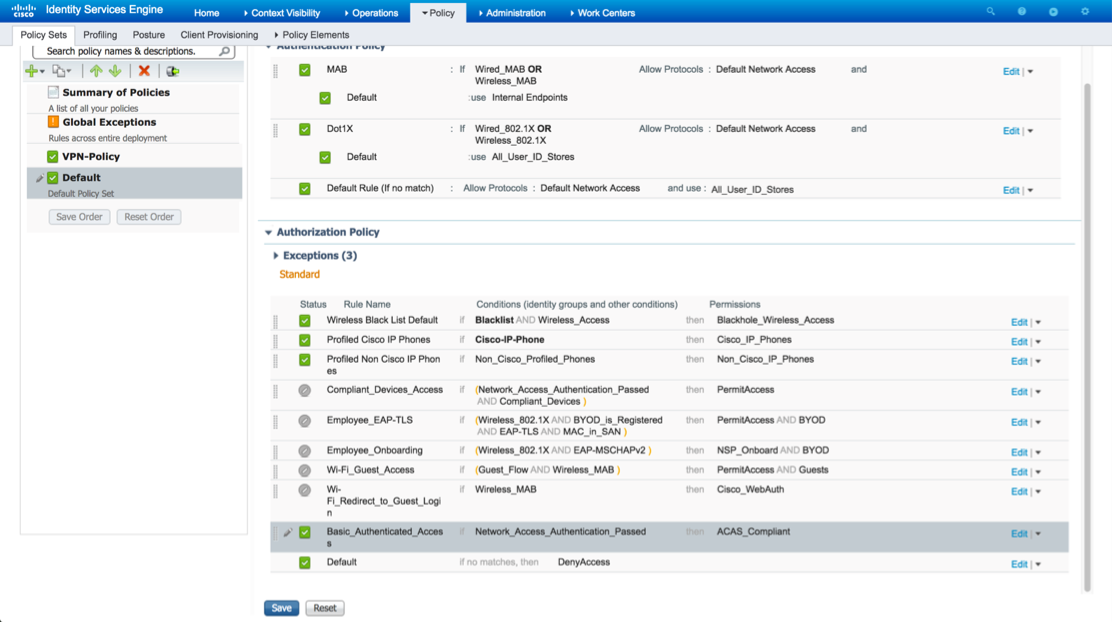
Verify
Cisco Identity Services Engine
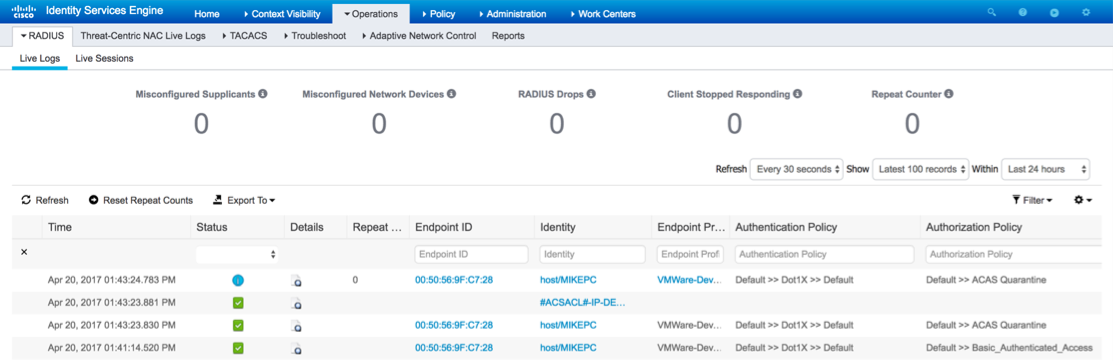
The first connection triggers a VA Scan. When the scan is finished, CoA is triggered to apply the new policy if it is matched.
In order to verify which vulnerabilities were detected, navigate to Context Visibility > Endpoints > Vulnerable Endpoints. Check per endpoint Vulnerabilities with the Scores given to it by Security Center.
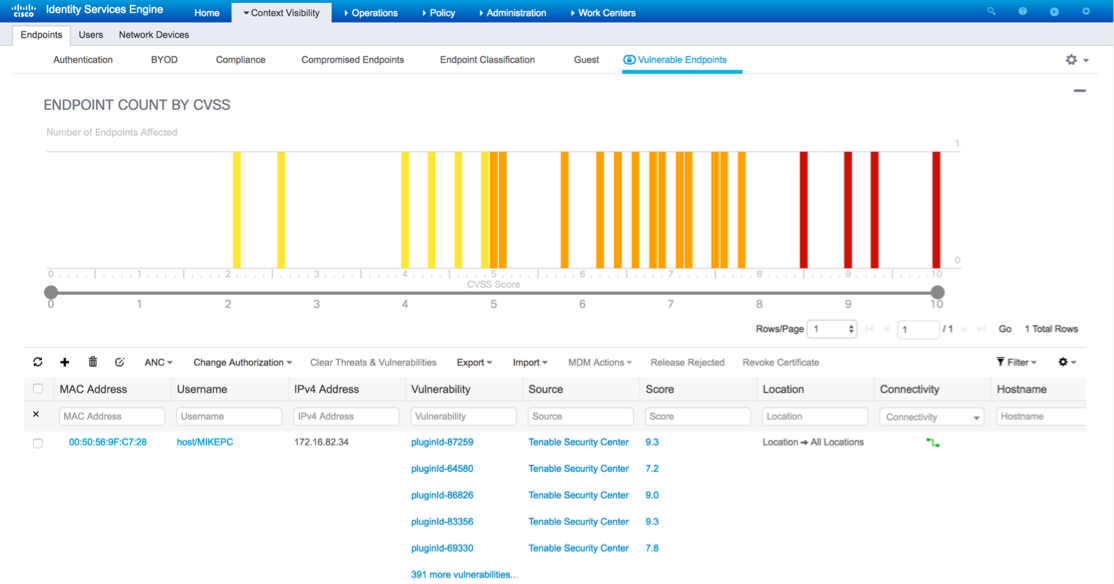
When selecting a particular endpoint, by clicking on the MAC address, more details about each Vulnerability appears, including PluginID, Title, CVSS Score, and CVEID's.
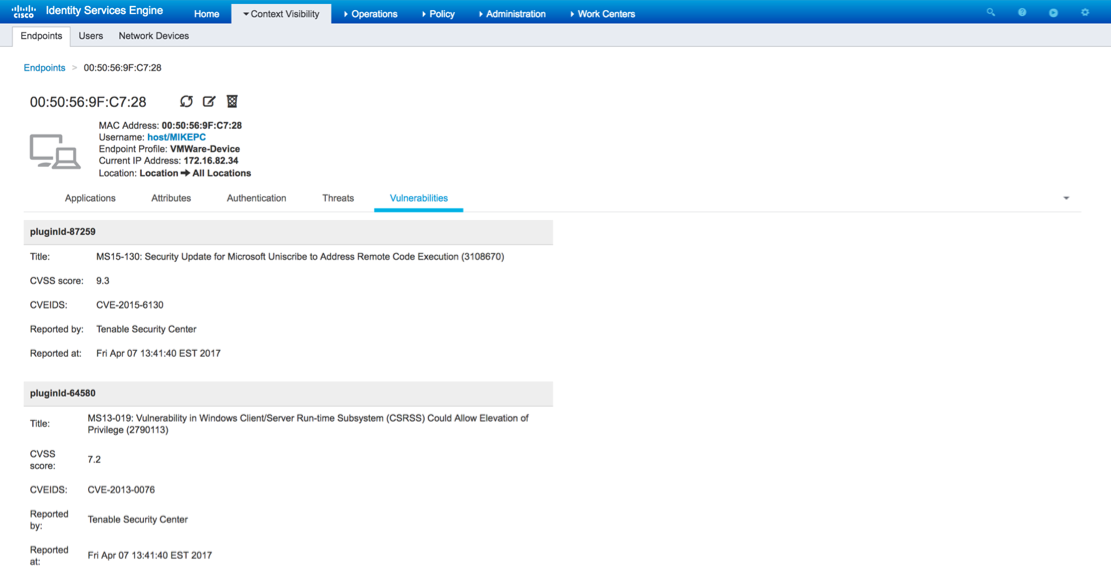
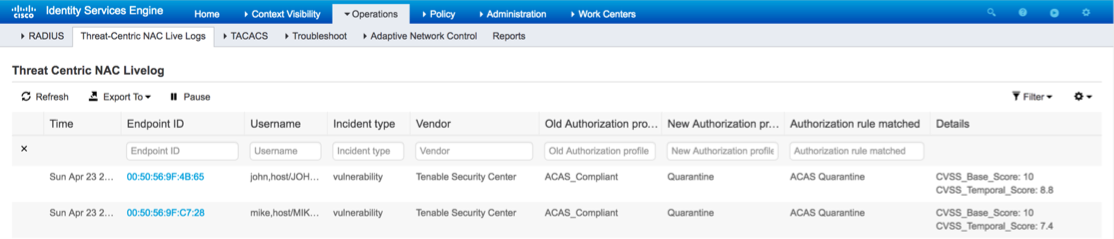
In Operations > TC-NAC Live Logs, you can see Old vs New authorization policies applied and details on CVSS_Base_Score. Note: Authorization conditions are done based on CVSS_Base_Score, which equals to the highest Vulnerability Score detected on the endpoint.
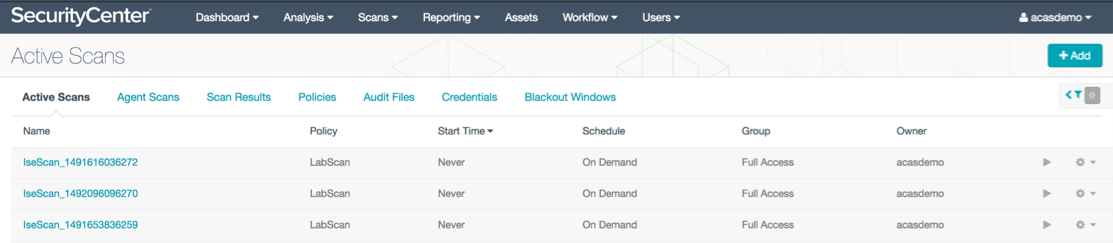
Tenable.sc
When the VA Scan is triggered by TC-NAC Tenable.sc queues the Scan, it can be viewed at Scans > Active Scans.
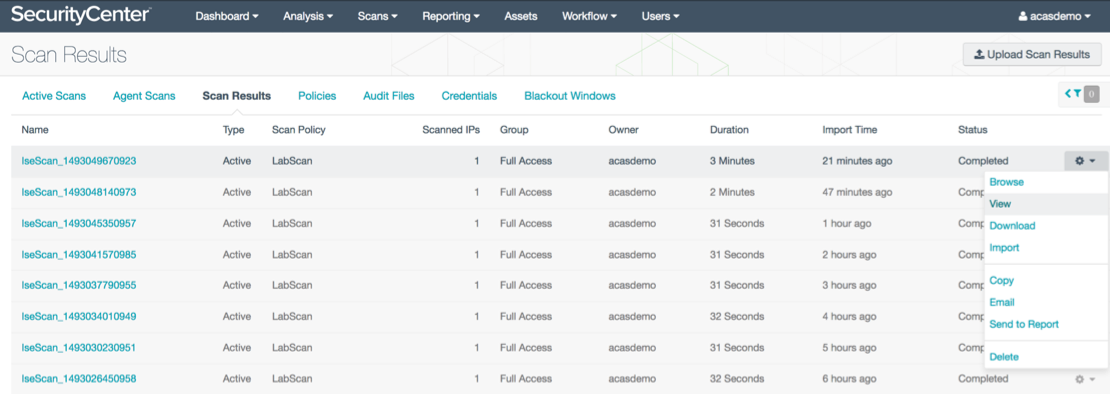
Once the scan completes it can be viewed under Scans > Scan Results.
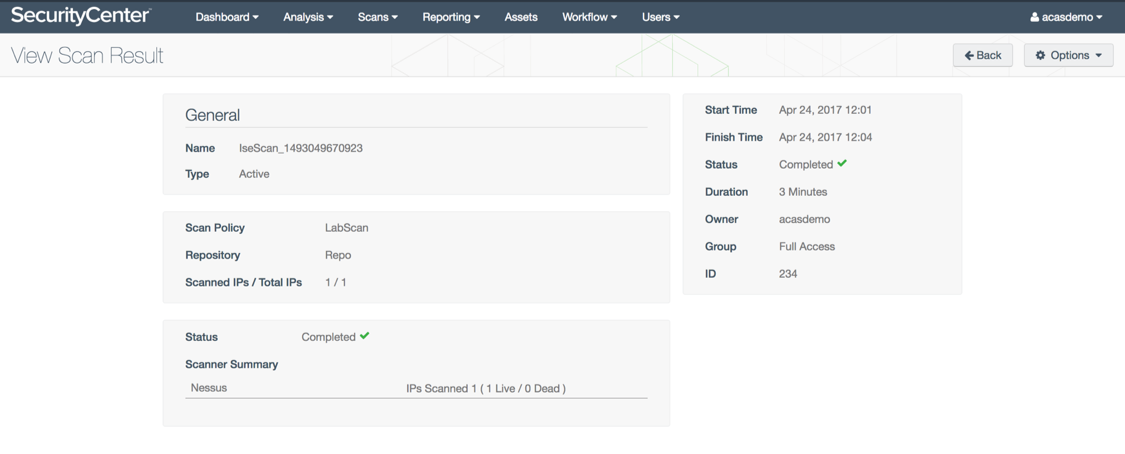
Navigate to the Analysis > Vulnerabilities page. From the drop-down menu select IP summary. This will give you a summary of all of the IP addresses that have vulnerabilities.
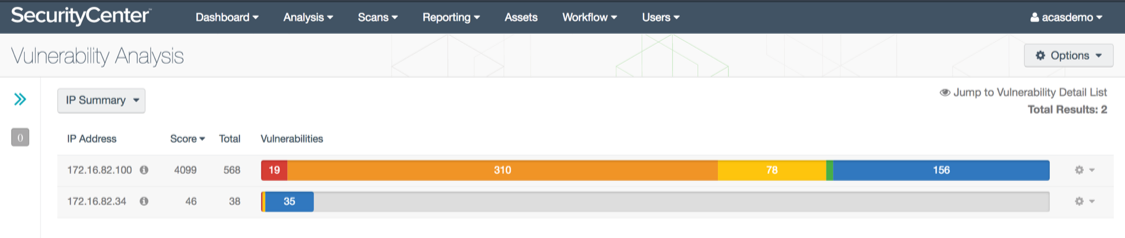
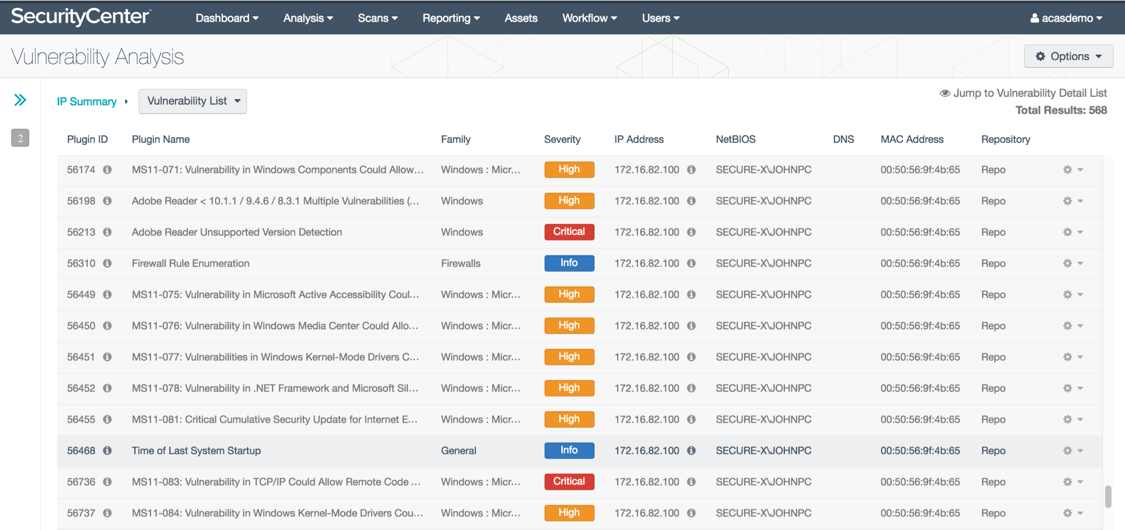
Click on one of the IP addresses for a detailed list of exact vulnerabilities. Note that you can also view these vulnerabilities from Cisco ISE under Context Visibility > Endpoints > Vulnerable Endpoints.
Troubleshoot
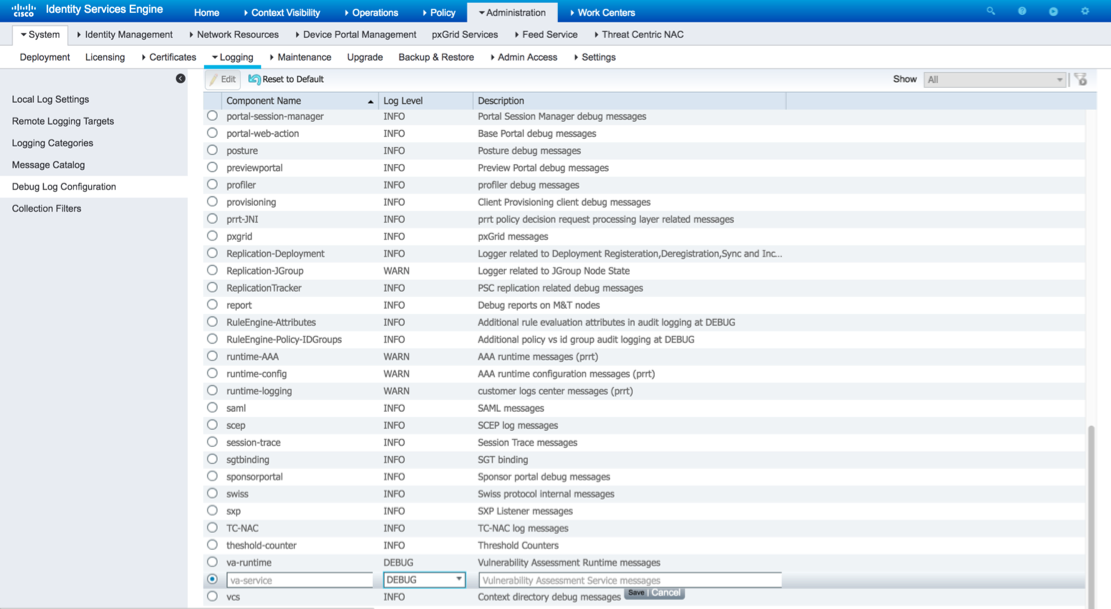
In order to enable debugs on ISE navigate to Administration > System > Logging > Debug Log Configuration, select TC-NAC Node and change the Log Level va-runtime and va-service component to DEBUG.
Logs to be checked: varuntime.log.
You can tail it directly from ISE CLI:
ISE21-3ek/admin# show logging application varuntime.log tail
TC-NAC Docker received instruction to perform Scan for particular endpoint.
2017-04-24 15:14:27,982 DEBUG [admin-http-pool204][] va.runtime.admin.vaservice.VaServiceRemotingHandler -:::::- VA: received data from Mnt:{"operationType":1,"macAddress":"00:50:56:9F:C7:28","ipAddress":"172.16.82.34","ondemandScanInterval":"1","isPeriodicScanEnabled":false,"periodicScanEnabledString":"1","vendorInstance":"894469e0-1734-4159-aad4-46155c8aa6fb","psnHostName":"ise-psn","heartBeatTime":0,"lastScanTime":0}
Once the result is received it stores all Vulnerability data in the Context DB.
2017-04-24 12:04:06,849 DEBUG [admin-http-pool69][] va.runtime.admin.vaservice.VaServiceRemotingHandler -:::::- VA: received data from Mnt: {"operationType":2,"isPeriodicScanEnabled":false,"heartBeatTime":1493053445792,"lastScanTime":0}
2017-04-24 12:04:17,440 DEBUG [pool-39-thread-12][] va.runtime.admin.vaservice.VaServiceMessageListener -:::::- Got message from VaService: [{"macAddress":"00:50:56:9F:C7:28","ipAddress":"172.16.82.34","lastScanTime":1493048318000,"vulnerabilities":["{\"vulnerabilityId\":\"pluginId-97833\",\"cveIds\":\"CVE-2017-0143,CVE-2017-0144,CVE-2017-0145,CVE-2017-0146,CVE-2017-0147,CVE-2017-0148\",\"cvssBaseScore\":\"10.0\",\"cvssTemporalScore\":\"7.4\",\"vulnerabilityTitle\":\"MS17-010: Security Update for Microsoft Windows SMB Server (4013389) (uncredentialed check)\",\"vulnerabilityVendor\":\"Tenable Security Center\"}","{\"vulnerabilityId\":\"pluginId-57608\",\"cveIds\":\"\",\"cvssBaseScore\":\"5.0\",\"cvssTemporalScore\":\"3.7\",\"vulnerabilityTitle\":\"SMB Signing Disabled\",\"vulnerabilityVendor\":\"Tenable Security Center\"}","{\"vulnerabilityId\":\"pluginId-90510\",\"cveIds\":\"CVE-2016-0128\",\"cvssBaseScore\":\"6.8\",\"cvssTemporalScore\":\"5.6\
////Output Omitted///
"48)\",\"vulnerabilityVendor\":\"Tenable Security Center\"}","{\"vulnerabilityId\":\"pluginId-65210\",\"cveIds\":\"CVE-2013-0087,CVE-2013-0088,CVE-2013-0089,CVE-2013-0090,CVE-2013-0091,CVE-2013-0092,CVE-2013-0093,CVE-2013-0094,CVE-2013-1288\",\"cvssBaseScore\":\"9.3\",\"cvssTemporalScore\":\"7.7\",\"vulnerabilityTitle\":\"MS13-021: Security Update for Internet Explorer (2809289)\",\"vulnerabilityVendor\":\"Tenable Security Center\"}","{\"vulnerabilityId\":\"pluginId-57043\",\"cveIds\":\"CVE-2011-2462,CVE-2011-4369\",\"cvssBaseScore\":\"9.3\",\"cvssTemporalScore\":\"7.3\",\"vulnerabilityTitle\":\"Adobe Reader \\u003c 9.4.7 Multiple Memory Corruption Vulnerabilities (APSB11-30)\",\"vulnerabilityVendor\":\"Tenable Security Center\"}","{\"vulnerabilityId\":\"pluginId-59040\",\"cveIds\":\"CVE-2012-0174,CVE-2012-0179\",\"cvssBaseScore\":\"6.9\",\"cvssTemporalScore\":\"5.7\",\"vulnerabilityTitle\":\"MS12-032:Vulnerability in TCP/IP Could Allow Elevation of Privilege (2688338)\",\"vulnerabilityVendor\":\"Tenable Security Center\"}","{\"vulnerabilityId\":\"pluginId-80490\",\"cveIds\":\"CVE-2015-0002\",\"cvssBaseScore\":\"7.2\",\"cvssTemporalScore\":\"5.6\",\"vulnerabilityTitle\":\"MS15-001: Vulnerability in Windows Application Compatibility Cache Could Allow Elevation of Privilege (3023266)\",\"vulnerabilityVendor\":\"Tenable Security Center\"}","{\"vulnerabilityId\":\"pluginId-95768\",\"cveIds\":\"CVE-2016-7259,CVE-2016-7260\",\"cvssBaseScore\":\"7.2\",\"cvssTemporalScore\":\"5.6\",\"vulnerabilityTitle\":\"MS16-151: Security Update for Windows Kernel-Mode Drivers (3205651)\",\"vulnerabilityVendor\":\"Tenable Security Center\"}","{\"vulnerabilityId\":\"pluginId-62464\",\"cveIds\":\"CVE-2012-2551\",\"cvssBaseScore\":\"4.3\",\"cvssTemporalScore\":\"3.2\",\"vulnerabilityTitle\":\"MS12-069: Vulnerability in Kerberos Could Allow Denial of Service (2743555)\",\"vulnerabilityVendor\":\"Tenable Security Center\"}"]}]
2017-04-24 12:14:47,583 DEBUG [pool-39-thread-8][] va.runtime.admin.vaservice.VaServiceMessageListener -:::::- VA: Save to context db, lastscantime: 1493048318000, mac: 00:50:56:9F:C7:28
Logs to be checked: vaservice.log.
You can tail it directly from ISE CLI:
ISE21-3ek/admin# show logging application vaservice.log tail
Vulnerability Assessment Request Submitted to Adapter.
2017-04-23 21:13:34,509 DEBUG [endpointPollerScheduler-4][] cpm.va.service.util.VaServiceUtil -:::::- VA SendSyslog systemMsg : [{"systemMsg":"91019","isAutoInsertSelfAcsInstance":true,"attributes":["TC-NAC.ServiceName","Vulnerability Assessment Service","TC-NAC.Status","VA request submitted to adapter","TC-NAC.Details","VA request submitted to adapter for processing","TC-NAC.MACAddress","00:50:56:9F:C7:28","TC-NAC.IpAddress","172.16.82.34","TC-NAC.AdapterInstanceUuid","894469e0-1734-4159-aad4-46155c8aa6fb","TC-NAC.VendorName","Tenable Security Center","TC-NAC.AdapterInstanceName","ACAS"]}]
AdapterMessageListener checks each 5 minutes the status of the scan, until it is finished.
2017-04-24 16:58:11,646 DEBUG [endpointPollerScheduler-4][] cpm.va.service.util.VaServiceUtil -:::::- VA SendSyslog systemMsg : [{"systemMsg":"91019","isAutoInsertSelfAcsInstance":true,"attributes":["TC-NAC.ServiceName","Vulnerability Assessment Service","TC-NAC.Status","Adapter Statistics","TC-NAC.Details","Number of endpoints queued for checking scan results: 2, Number of endpoints queued for scan: 0, Number of endpoints for which the scan is in progress: 0","TC-NAC.AdapterInstanceUuid","c1feca7d-2d1d-4f0f-9f72-cc369c57fba1","TC-NAC.VendorName","Tenable Security Center","TC-NAC.AdapterInstanceName","ACAS"]}]
2017-04-24 17:03:11,541 DEBUG [SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -:::::- Message from adapter : {"AdapterInstanceName":"ACAS","AdapterInstanceUid":"c1feca7d-2d1d-4f0f-9f72-cc369c57fba1","VendorName":"Tenable Security Center","OperationMessageText":"Number of endpoints queued for checking scan results: 1, Number of endpoints queued for scan: 0, Number of endpoints for which the scan is in progress: 1"}
2017-04-24 17:08:11,542 DEBUG [SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -:::::- Message from adapter : {"AdapterInstanceName":"ACAS","AdapterInstanceUid":"c1feca7d-2d1d-4f0f-9f72-cc369c57fba1","VendorName":"Tenable Security Center","OperationMessageText":"Number of endpoints queued for checking scan results: 1, Number of endpoints queued for scan: 0, Number of endpoints for which the scan is in progress: 1"}
Adapter gets PluginID’s, CVEID's, along with the CVSS Scores.
2017-04-24 17:08:47,298 DEBUG [SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -:::::- Message from adapter : {"returnedMacAddress":"00:50:56:9f:c7:28","requestedMacAddress":"00:50:56:9F:C7:28","scanStatus":"ASSESSMENT_SUCCESS","lastScanTimeLong":1493048318000,"ipAddress":"172.16.82.34","vulnerabilities":[{"vulnerabilityId":"pluginId-57608","cveIds":"","cvssBaseScore":"5.0","cvssTemporalScore":"3.7","vulnerabilityTitle":"SMB Signing Disabled","vulnerabilityVendor":"Tenable Security Center"},{"vulnerabilityId":"pluginId-90510","cveIds":"CVE-2016-0128","cvssBaseScore":"6.8","cvssTemporalScore":"5.6","vulnerabilityTitle":"MS16-047: Security Update for SAM and LSAD Remote Protocols (3148527) (Badlock) (uncredentialed check)","vulnerabilityVendor":"Tenable Security Center"},{"vulnerabilityId":"pluginId-19506","cveIds":"","cvssBaseScore":"","cvssTemporalScore":"","vulnerabilityTitle":"Nessus Scan Information","vulnerabilityVendor":"Tenable Security Center"},{"vulnerabilityId":"pluginId-97833","cveIds":"CVE-2017-0143,CVE-2017-0144,CVE-2017-0145,CVE-2017-0146,CVE-2017-0147,CVE-2017-0148","cvssBaseScore":"10.0","cvssTemporalScore":"7.4","vulnerabilityTitle":"MS17-010: Security Update for Microsoft Windows SMB Server (4013389) (uncredentialed check)","vulnerabilityVendor":"Tenable Security Center"}]}
2017-04-24 17:08:47,300 INFO [SimpleAsyncTaskExecutor-2][] cpm.va.service.processor.AdapterMessageListener -:::::- Endpoint Details sent to IRF is {"00:50:56:9F:C7:28":[{"vulnerability":{"CVSS_Base_Score":10.0,"CVSS_Temporal_Score":7.4},"time-stamp":1493048318000,"title":"Vulnerability","vendor":"Tenable Security Center"}]}
Support
Please work with the respective vendor and/or TAC to isolate the issue. If its leaning on ISE use the TAC first.
References
Cisco Identity Services Engine Administrator Guide, Release 2.2 - Cisco
Demo
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@KaigeG you need to export the certificate from tenable and install in trusted certificates on ISE and vice versa
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

