Introduction
This document has information about Cisco Wide Area Application Services (WAAS) integration with ACS 5.x, so that users could authenticate to WAAS using tacacs credentials and have administrative access.
Components Used
Example from Datasheet:

Configuration on ACS
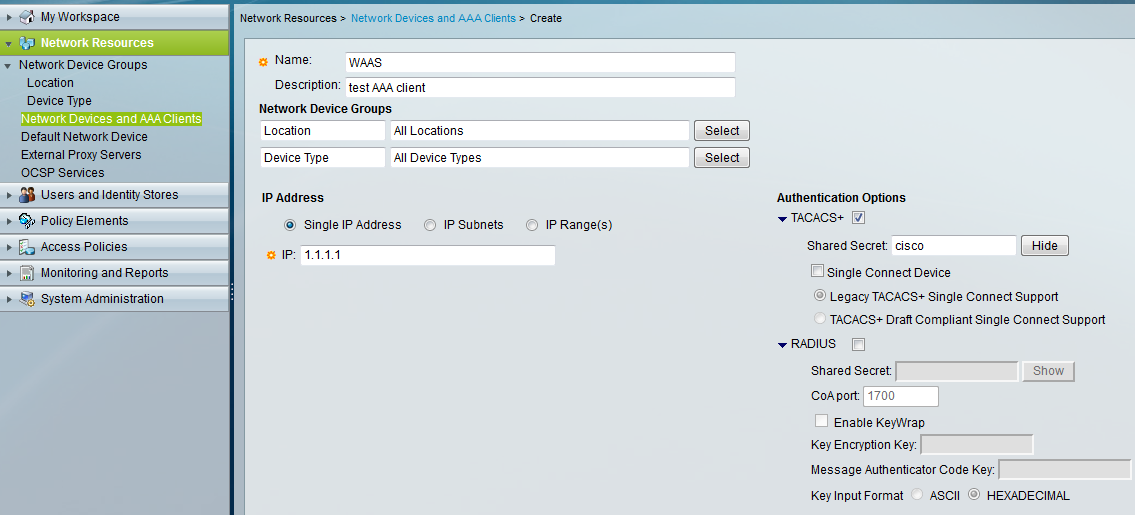
Step1: Define a AAA client on ACS 5
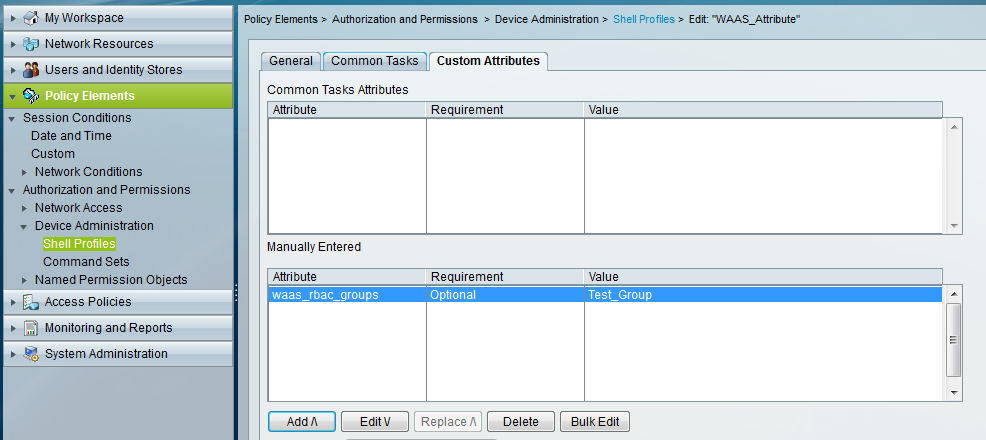
Step 2: Define a shell profile under, ACS GUI > Policy Elements > Authorization and Permissions > Device Administration > Shell Profiles
Step 3: Define a command set to allow all commands.

Step 4: Since this example uses tacacs, the default service selected is "default device admin", now point the identity to correct identity source (Internal Users/ AD / Identity store sequence).

Step 5: Create an authorization rule, which checks for the requests from WAAS (for this document I am specifically using device IP as a condition, but this can change based on one's requirement) and applies the shell profile and command set that we had created in step 2 and step 3.


Configuration on WAAS
Step 6:
Define a TACACS+ Server by selecting your Central Manager device under the device list and configure TACACS+:
Devices > [Central Manager System name] > Configure > Security > AAA > TACACS+

Step 7:
You will also need to modify the authentication and authorization methods in this screen to allow TACACS+ access.
Devices > [Central Manager System name] > Configure > Security > AAA > Authentication Methods

Step 8:
Browse to the following location and add the group name that matches the custom attribute "value" (created in ACS) in WAAS:
Home > Admin > AAA > User Groups

Step 9:
Then assign this group (Test_Group) “admin” level rights in Role Management. The “admin” role on the Central Manager is pre-configured.

After this when the user logs in to WAAS, they can authenticate using tacacs credentials and will have admin rights to WAAS.
Additional Information
Configuring a User
The first step in setting up your WAAS Express device and Central Manager to communicate is to configure the same user on the WAAS Express device and the Central Manager.
To configure an external TACACS+ user on the WAAS Express device, use the following configuration commands on the WAAS Express device:
waas-express#config t
Enter configuration commands, one per line. End with CNTL/Z.
waas-express(config)#aaa new-model
waas-express(config)#aaa authentication login default group tacacs+
waas-express(config)#aaa authorization exec default group tacacs+
waas-express(config)#tacacs-server host host-ip
waas-express(config)#tacacs-server key keyword
To configure an external RADIUS user on the WAAS Express device, use the following configuration commands on the WAAS Express device:
waas-express#config t
Enter configuration commands, one per line. End with CNTL/Z.
waas-express(config)#aaa new-model
waas-express(config)#aaa authentication login default group radius
waas-express(config)#aaa authorization exec default group radius
waas-express(config)#radius-server host host-ip
waas-express(config)#radius-server key keyword
Reference
The external authentication server for TACACS+ or RADIUS must be Cisco ACS 4.x or 5.x. For detailed information on Configuring a User section of
Cisco Wide Area Application Services Configuration Guide
Please feel free to comment in case of any query.