The following guide shows how to return a TACACS attribute in ACS 5 defining the role a user should be placed into on Nexus 5K switches that use Role Based Access Control (RBAC).
This guide makes the following assumptions:
- You are using the TACACS protocol to authenticate RBAC users on a Nexus 5000 switch.
- Your ACS service selection rules direct all TACACS requests to the "Default Device Admin" access service.
- The switch is aleady added as a network device in a network device group specifically for Nexus switches.
- Users are already mapped to an Identity Group on ACS that will then map to their role on Nexus.
Step 1:
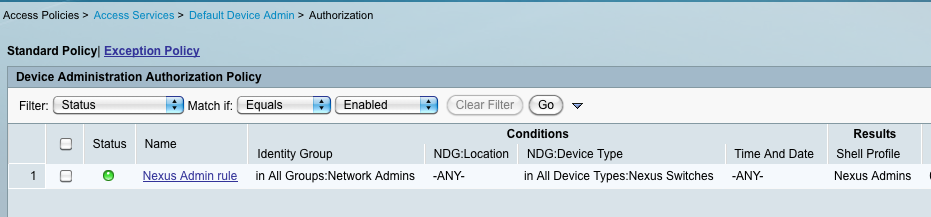
Create an Authorization Policy rule to match the user and device criteria as shown below:
Step 2:
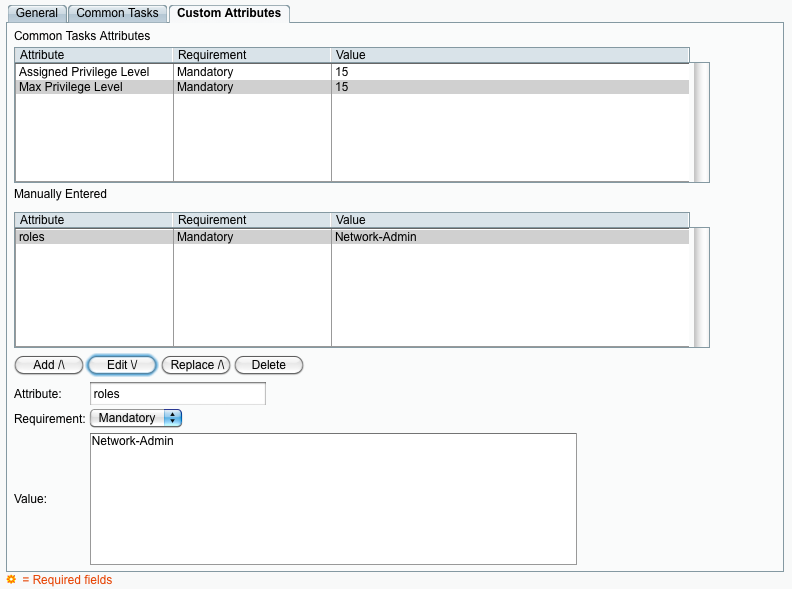
Create a Shell Profile to return the required attributes. In the following example the user will be placed into the "Network-Admin" role:
Step 3:
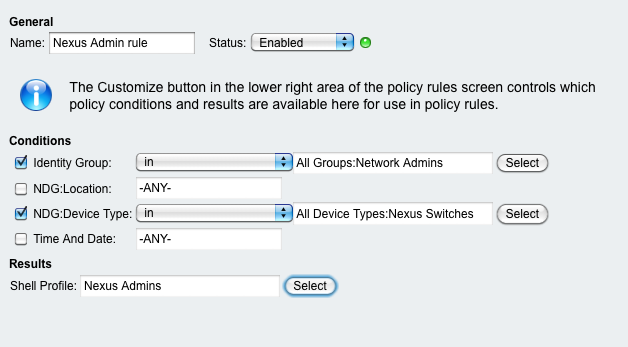
Map the Shell Profile to the Authorization Policy rule:
Step 4:
Log into the Nexus switch. To confirm that the rule has been successfully matched, check the hit count next to the rule. Note you may need to refresh the hit count status by clicking on the hit count button on the bottom right hand corner, and then refresh.