- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Configuring eduroam on Cisco Identity Services Engine (ISE) 2.1
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-25-2017 01:05 PM - edited 07-27-2018 05:05 AM
- Purpose
- Prerequisites
- eduroam
- Wireless LAN Controller
- Policy Sets
- Active Directory
- eduroam Configuration
- Add eduroam RADIUS servers
- Create the eduroam Policy Conditions
- Create the eduroam Policy Set
- References
Purpose
This document details the steps for using ISE to authenticate eduroam users.
Three rules cover the authentication scenarios which will be encountered:
Rule 1: User is not a member of the home institution. Authentication will be proxied to eduroam RADIUS Servers.
Rule 2: User is a member of the home institution but is located at another institution. Authentication will be sourced from the eduroam RADIUS Servers.
Rule 3: User is a member of the home institution and the request will be sourced locally.
Regarding authorization, we are simply aiming for PermitAccess, but will break the Authorization rules down to give granularity to the reporting.
Prerequisites
eduroam
Register the IP Addresses of your Policy Service Nodes as AAA Servers with eduroam.
Wireless LAN Controller
On all Wireless LAN Controllers (WLC) configured to offer the SSID 'eduroam' to AP Groups, make sure that WLAN ID is the same on all WLCs and that all ISE Policy Service Nodes (PSN) are being used for authentication.
Policy Sets
This guide shows the configuration of eduroam with the use of Policy Sets. If you are currently not using them, the configuration can be done without the use of Policy Sets. If you would like to enable Policy Sets, navigate to Administration > System > Settings > Policy Sets. Select Enabled and Save.
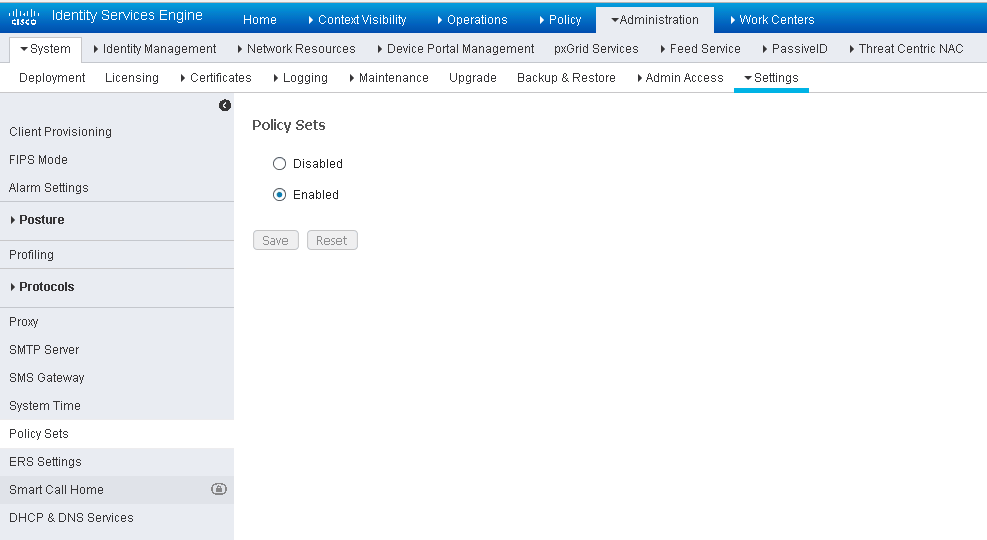
You will be logged out of ISE. Once you log back in, you will notice the Policy menu is different. There is an option for Policy Sets while the Authentication and Authorization entries are no longer there. Any policies you had already created are in the Default Policy Set.
Active Directory
ISE needs to be joined to your Active Directory Domain to authenticate local users. Of course you can use any of the Identity Sources supported by ISE, but for this document we will focus on Active Directory (AD).
If you have not already joined ISE to you Active Directory Domain, do so now by navigating to Administration > Identity Management > External Identity Sources > Active Directory.
Create a service account in AD and use it to create a connection to your AD Domain.

eduroam Configuration
Add eduroam RADIUS servers
Eduroam External User Server Setup
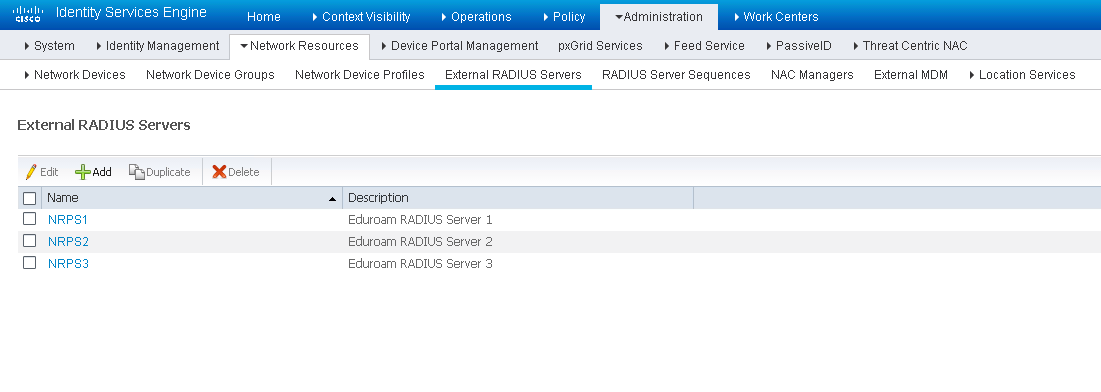
In this step, we will configure the external eduraom RADIUS Servers to which ISE will authenticate users that are visiting the Home Institution. First, navigate to Administration > Network Resources > External RADIUS sources.
Configure each of the eduroam RADIUS Servers which will be used for authenticating users from external realms. The specific IP Address and Shared Secret will be provided to you by eduroam. You can name these entries however you would like.
Then, navigate to Administration > Network Resources > Network Device List > RADIUS Server Sequences.
This is where you create a sequence which lists the access order of the external eduroam RADIUS servers.
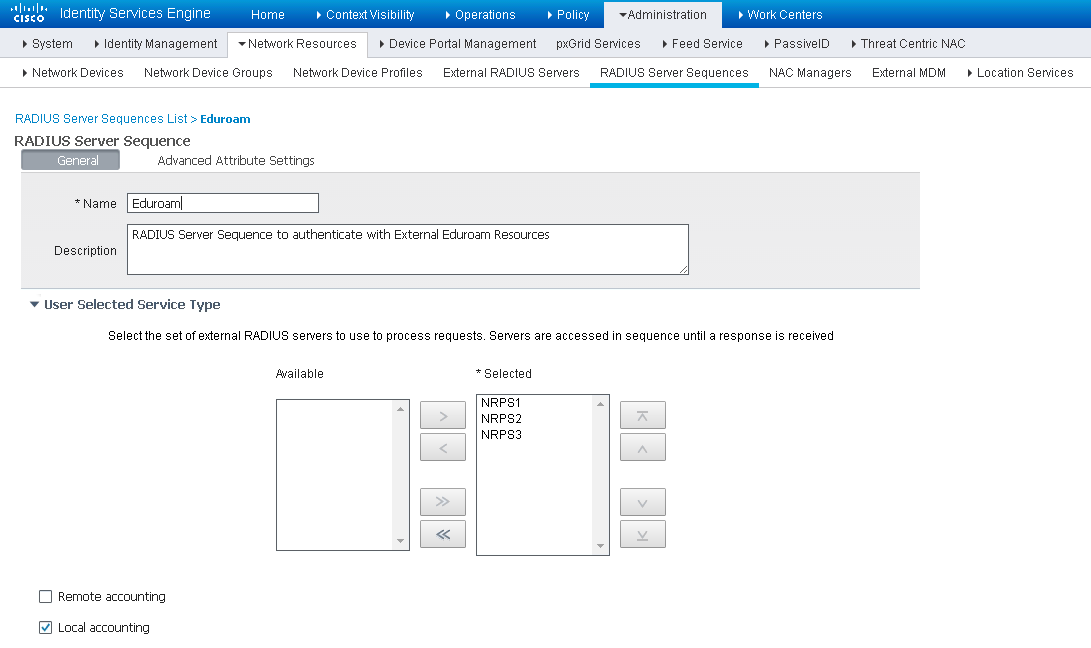
Eduroam Internal User Server Setup
Now we will configure the access for internal users that are visiting a different eduroam member Institution. Navigate to Administration > Network Resources > Network Device Groups.
Under All Device Types, create a group for the eduroam RADIUS Servers and for your Wireless Controllers. In the figure below they are named 'eduroam' and 'WLC' accordingly.
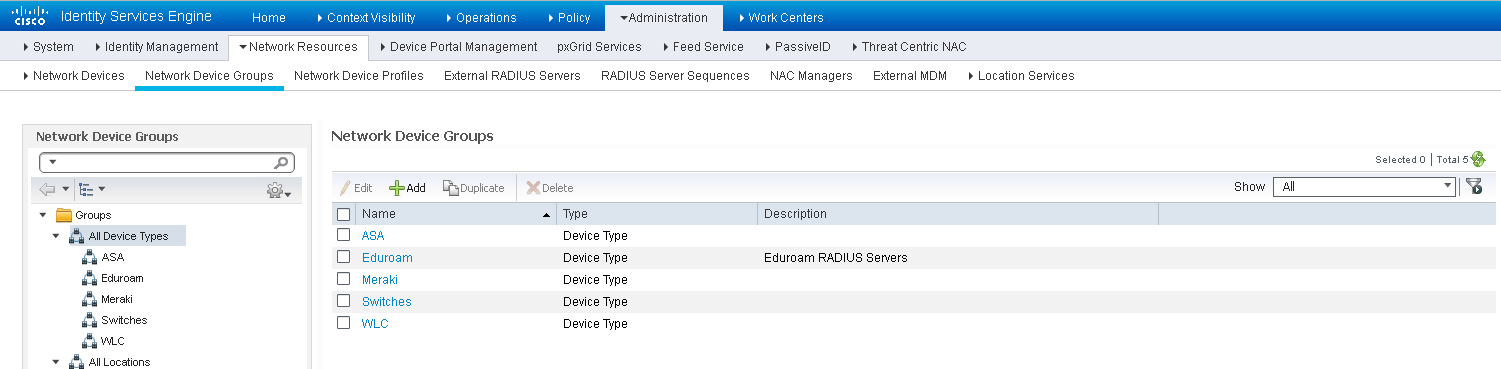
Now that the groups are created, go to Administration > Network Resources > Network Devices to add the eduroam RADIUS Servers and Wireless Controllers to ISE.
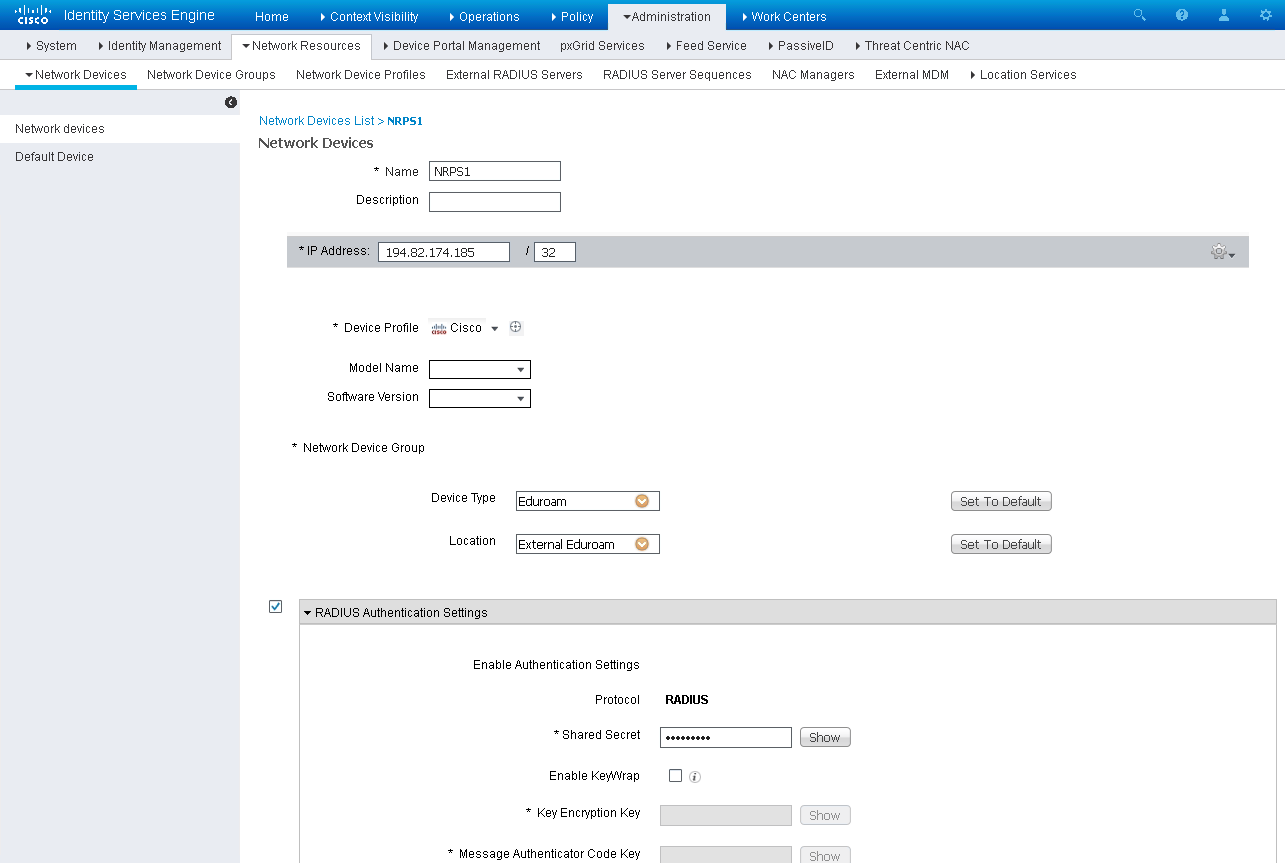
Remember to ensure your WLCs are part of the group WLC, and the eduroam RADIUS Servers servers are part of the Eduroam group. This is done in the Network Device Group section.
Create the eduroam Policy Conditions
Authentication Conditions
This step will create the conditions used to authenticate through the eduroam system while keeping your Authentication Policy clean. Navigate to Policy > Policy Elements > Conditions > Authentication > Compound Conditions.
Create a new condition, eg: 'Eduroam_User_External', this will be used to identify RADIUS requests that need to be handed off to the eduroam RADIUS Servers. In the event of receiving just a username we want to be able to handle that. We will make the assumption that such a user belongs to our own AD. As such we need to ensure that a 'foreign' username does not contain our realm but does contain the '@' symbol which we will infer means an alternative domain is provided.
Configure the following attributes:
Radius: User-Name NOT ENDS WITH @<your_domain> AND
Radius: User-Name CONTAINS @ AND
Radius: Service-Type EQUALS Framed AND
Radius: NAS-Port-Type EQUALS Wireless – IEEE 802.11
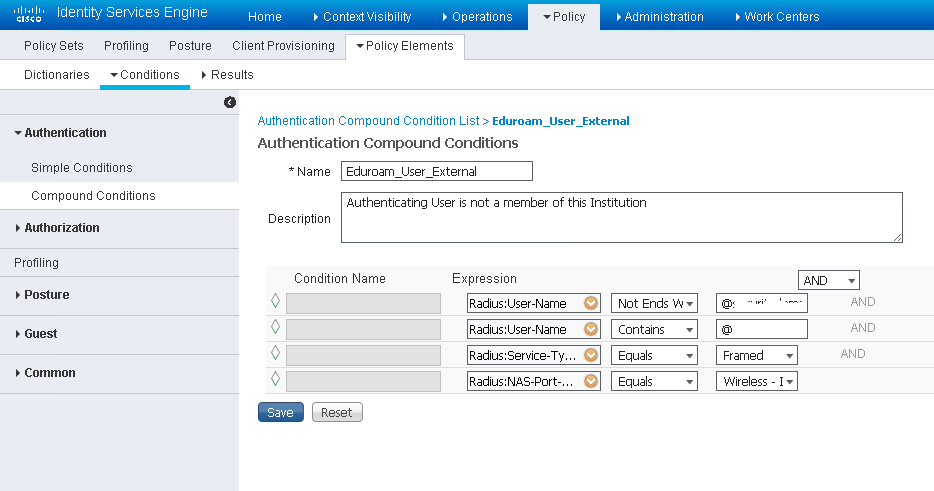
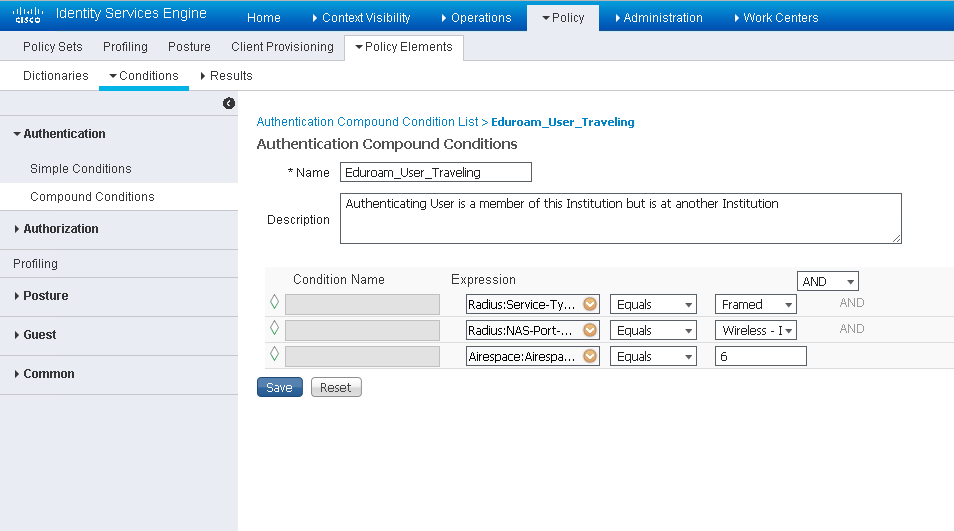
Create another condition 'Eduroam_User_Traveling' similar to the condition created above, but without the User-Name element. Since this condition will be used to identify eduroam traffic that must be sent to the eduroam RADIUS Servers, we will include a check for the WLAN-ID (this document uses WLAN ID of 6, please ensure you are using the WLAN ID that corresponds to your eduroam SSID):
Radius: Service-Type EQUALS Framed AND
Radius: NAS-Port-Type EQUALS Wireless – IEEE 802.11 AND
Airespace: Airespace-Wlan EQUALS 6
Authorization Condition
This step will create the conditions used to authorize local users at their Home Institution through the eduroam system while keeping your Authorization Policy clean. Navigate to Policy > Policy Elements > Conditions > Authorization > Compound Conditions
Identify Authorization requests coming from the eduroam SSID and check the user names against AD. Name it 'Eduroam_User_Local':
Radius: Service-Type EQUALS Framed AND
Radius: NAS-Port-Type EQUALS Wireless – IEEE 802.11 AND
Airespace: Airespace-Wlan EQUALS 6
AD1:ExternalGroups EQUALS <your_domain>/Users/Domain Users

Create the eduroam Policy Set
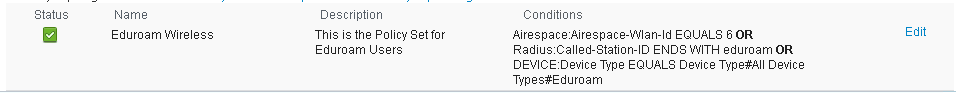
Navigate to Policy > Policy Sets and create a new Policy Set named 'Eduroam Wireless'
Set the Policy Set filter as:
Airespace:Airespace-Wlan-Id EQUALS 6 OR
Radius:Called-Station-ID ENDS WITH eduroam OR
DEVICE:Device Type EQUALS Device Type#All Device Types#Eduroam
Authentication Policy
Create three rules to handle the different authentication directions: inbound, outbound, and local.
|
Name |
If |
Allow Protocols |
Default |
|---|---|---|---|
|
Eduroam External User |
Eduroam_User_External |
Use Proxy Service: Eduroam |
|
|
Eduroam Traveling User |
DEVICE:Device Type EQUALS Device Type#All Device Types#Eduroam |
PEAP-Auth |
AD1 |
|
Eduroam Local User |
Airespace:Airespace-Wlan_Id EQUALS 6 OR Radius:Called-Station-ID ENDS WITH eduroam |
PEAP-Auth |
AD1 |

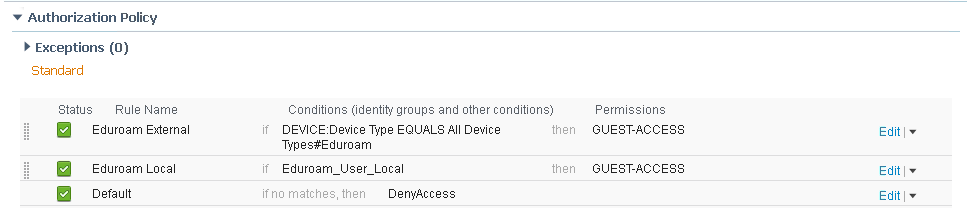
Authorization Policy
Create two rules to handle the different authorization methods: external and local.
|
Rule Name |
Conditions |
Permissions |
|---|---|---|
|
Eduroam External |
DEVICE:Device Type EQUALS All Device Types#Eduroam |
GUEST-ACCESS |
|
Eduroam Local |
Eduroam_User_Local |
GUEST-ACCESS |
References
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Just the cookbook I was looking for.
But a question on the policy set creation, the 2nd and 3rd lines show the values being set to "eduroam", but I don't see those values as options, where do those need to be created so they are selectable for those two lines of the policy set?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
If you are talking about the Authentication Policy:
For the Eduroam Traveling User, this is shown in the section titled Eduroam Internal User Server Setup.
For the Eduroam Local User, you type in the name of the SSID, which, in this case, is eduroam.
I hope this helps.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Actually, the section right above that;

- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
The answers are the same, though. Radius:Called-Station-ID ENDS WITH and then in the dropdown, just type eduroam
The Device Type is set as noted, but is listed in a manner that might catch you off guard.
You had to have created the Device Group and placed the Eduroam Servers in it to be effective.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
How can I use ISE as eduroam FLR? I think I should use the same concept of external RADIUS server.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Great article. Can you expand a little on how to register ISE as our RADIUS server with the external RADIUS servers & does this mean ISE needs to be accessible from the internet?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hi @Jason Weids,
usually you dont connect your RADIUS to other RADIUS servers outside of your organization. instead you get a proxy RADIUS server which is facing the internet and forwards/receives the requests from eduroam partners to you.
this proxy is the one added with eduroam people so they know where you are and traffic the requests to you when needed.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi, Can you advise on how you do the authentication policy on v2.3.
In the example above when creating the 3 rules for the authentication of external, travelling & local user it says set the Allowed Protocols to use proxy service: eduroam & PEAP-Auth but in v2.3 the authentication policy has the "Use" field where you can select internal endpoints, users & ID stores.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
Just a little question.
This integration is supposed to be applied to a Guest access enviroment. So, with Base licenses is enough to do it o do I need another license?
Thank you.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Usually Thisis an 802.1x SSID
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
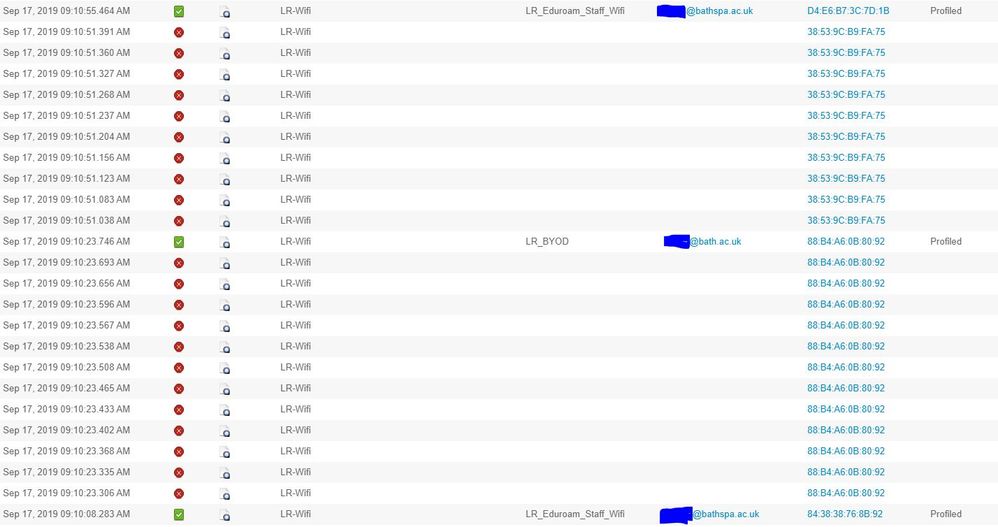
I have followed this guide & everything appears to be working but can anyone explain why we are seeing multiple authentication failures in the radius logs followed by a successful one for the same device/s
All the failures are due to the endpoint abandoned EAP session & started new. Is there a setting or something that would prevent this?
Steps
| 11001 | Received RADIUS Access-Request | |
| 11017 | RADIUS created a new session | |
| 11117 | Generated a new session ID | |
| 15049 | Evaluating Policy Group | |
| 15008 | Evaluating Service Selection Policy | |
| 15048 | Queried PIP - DEVICE.Location | |
| 15048 | Queried PIP - Airespace.Airespace-Wlan-Id | |
| 15048 | Queried PIP - Radius.Called-Station-ID | |
| 15048 | Queried PIP - DEVICE.Device Type | |
| 15048 | Queried PIP - Radius.User-Name | |
| 15048 | Queried PIP - Normalised Radius.SSID | |
| 11358 | Received request for RADIUS server sequence. | |
| 11361 | Valid incoming authentication request | |
| 11355 | Start forwarding request to remote RADIUS server | |
| 11365 | Modify attributes before sending request to external radius server | |
| 11100 | RADIUS-Client about to send request - ( port = 1812 ) | |
| 11101 | RADIUS-Client received response | |
| 11357 | Successfully forwarded request to current remote RADIUS server | |
| 11006 | Returned RADIUS Access-Challenge | |
| 5440 | Endpoint abandoned EAP session and started new |
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Jason Weids,
Did you find a solution to the issue you were seeing with multiple abandoned EAP sessions? I've got the same problem and I'm struggling to find a solution.
Thanks!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi @Loupins,
The majority of what we were seeing seems to be normal wireless behavior. Having not used ISE before for authenticating users this was something we were not used to seeing.
We did have some other issues that were also compounding this in the logs. Our environment is divided in that not all of our locations are using ISE to authenticate wireless users. In some locations, this is done by FreeRadius servers. It appeared that users who had registered & authenticated first in one location via our FreeRad servers, when they turned up at our site that was using ISE, they would fail to authenticate & the EAP session would be abandoned because the certificate on our ISE was different to the FreeRad server. By importing the cert from FreeRad server into ISE & using it for EAP auth fixed this.
We do still see some abandoned sessions, this tends to be from visitors from other education organisations where we see multiple abandoned sessions before a successful one. It is impossible to tell if these are from people walking past the location in question & their device/s are trying to connect as they pass or if they are actually onsite, either way, it is not causing any known users issues.
Are your users failing to connect after the multiple abandoned sessions or do they succeed?
Have you recently began authenticating wireless users in ISE? Could users devices still be using a different certificate from a different Radius server?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for getting back to me!
We've been using NPS to proxy eduroam authentications to our local university for several years but I'm in the process of moving authentications to ISE and eduroam radius servers. I've got it working but for every successful authentication on ISE there are nine abandoned EAP sessions. The abandoned sessions and successful authentication all happen within milliseconds of each other. I've checked the eduroam management portal and there are no failed authentications.
We are already using ISE to authenticate users on another SSID. We see occasional abandoned EAP sessions but not several for every client. We get thousands eduroam clients each day and I'm concerned about the impact the abandoned EAP sessions might have on our ISE deployment.
I've checked the certificates on the proxy server and it's using our root CA which is already installed on ISE.
Any other ideas?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Yes, I think I would be concerned too with that many. We do still get it ourselves but it is only the clients that are from visiting education organisations that we proxy the request to our FreeRadius servers which are sent to the NPS. We only see the odd one from our locally authenticated clients.
You say you are proxying the requests to eduroam servers, do you not use a local active directory or is your other SSID using a local active directory?
It seems to me, like us, you are seeing the same thing with clients that are using an external identity source. Fortunately for us, that is not many but I would still like to get to the bottom of it myself. My feeling is that it may be a short timeout configured somewhere but like you, we see about 10-12 abandoned attempts within milliseconds. The only consistent thing is that it happens with all clients using an external identity source. Is this the same for you?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: