- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Dual SSID BYOD with Apple Captive Network Assistant (CNA) Browser
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
02-01-2017 11:43 AM - edited 03-23-2020 02:35 PM
Please reference this table for defect info
Apple CNA (Captive Network Assistant, AKA Apple mini browser) is a Apple iOS feature that allows a browser like window to pop-up whenever network access is needed and the CNA determines that the network requires user interaction to gain full network access. This typically happens when the user associates to an open wireless LAN and even though an IP address is provided to the device, the network still restricts the user to take further actions, such as accepting an AUP, providing a shared password, or logging in as a guest user. This enhances user experience as it saves the user from manually opening up a Safari browser window. It also provides assistance even during non-initial association to the WLAN. For instance, if the endpoint device goes into sleep mode and the session is torn down on the WLC and subsequently the user tries to use a non-web browser application that requires network connectivity, the iOS device can sense that the device is in captive portal state and pop-up the mini browser for user to take further action to gain network access. As one can see having the iOS CNA feature operate on a guest network is a good idea, however, when BYOD is enabled on the same WLAN, as is the case with ISE dual-SSID flow, the CNA breaks the ISE BYOD process. One of the reason for that is due to ISE BYOD process forcing the CNA mini browser to go into the background as it asks the end user to accept the iOS profiles, which includes CA certificate and enrollment package, and when the CNA mini browser is moved to the background it immediately disconnects the device from the WLAN, which in turn breaks the BYOD process.
Prior to ISE 2.2, the ISE was setup to warn the user that the browser is not supported and user had no easy way aside from reporting it to the network administrator and subsequently the administrator had to enable captive bypass on the WLC which disabled the pop-up of the CNA mini browser on the controller level. Unfortunately, the captive bypass feature on WLC 8.3 and below required to be ran controller wide, which meant that all of the WLANs that the controller was servicing disabled the apple CNA. Cisco ISE version 2.2 is the first version to support Dual-SSID BYOD flow through Apple CNA. This document explains how to configure the ISE and Cisco WLC to provide Dual-SSID BYOD even when the captive portal bypass feature is disabled on the WLC. For other options on how to deal with Apple CNA, please go to: Dealing with Apple CNA (AKA Mini browser) for ISE BYOD
This document will leverage pre-defined policy rules and elements for dual SSID BYOD configuration. Also, this document assumes that the WLC is already configured with baseline WLC configuration for ISE. For more information on the baseline WLC ocnfiguration please refer to: How To: Universal Wireless Controller (WLC) Configuration for ISE
User experience:
- User associates to OPEN SSID
- Apple CNA mini browser pop-up
- User enters employee ID (ISE recognizes non guest accounts to be employee users)
- User is asked to wait for ‘Done’ in the upper right corner and click the link which pops up the full Safari browser to continue with BYOD process
- User starts BYOD flow and enters description for the device
- Downloads root CA certificate & enrollment profile (Certificate + WiFi settings)
- User is asked to connect to secure SSID
- User has Full network access
Components:
Cisco ISE version 2.2+
Cisco WLC 7.6+ for DNS ACL feature; not possible with FlexConnect local switching WLAN as DNS ACL is not supported for locally switched traffic
Note: If running WLC 8.4+ code then the captive portal bypass can be enabled per WLAN instead of globally. It still does not allow administrator to use a single WLAN for both CNA enabled guest access and employee BYOD, but allows them to enable captive portal bypass selectively per WLAN instead of controller wide.
Cisco WLC:
(Optional) Disable captive portal bypass
- If previously enabled, go to the CLI of the WLC and disable captive portal bypass by running 'config network web-auth captive-bypass disable'
- Save config
- Reset system for the settings to take affect
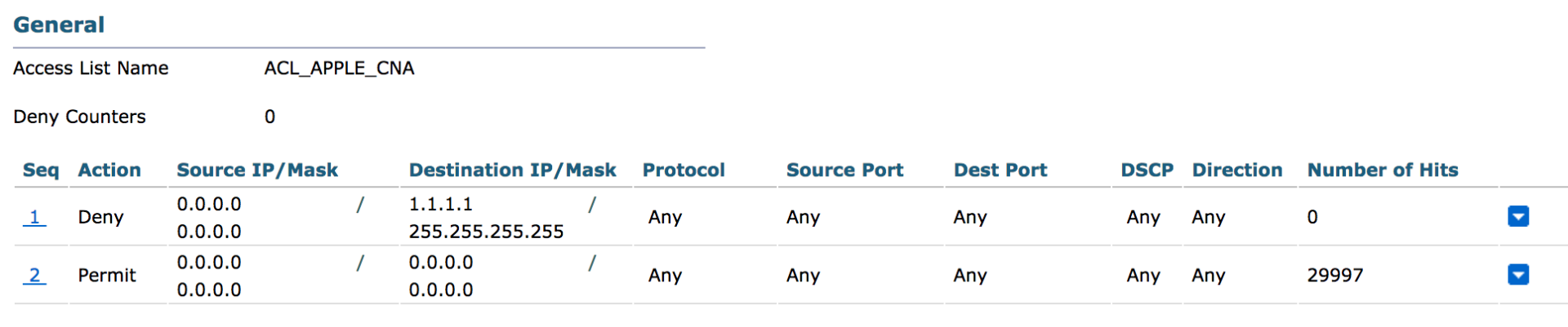
Create Additional ACL for Apple iOS devices to provide ‘Done’ on the CNA mini browser (Note: This ACL provides full network access for the endpoint temporarily during BYOD process. This is necessary to suppress Apple CNA)
- Go to WLC GUI and navigate to SECURITY > Access Control Lists > Access Control Lists
- Click 'New...' in the upper right corner
- Name the new ACL ' ACL_APPLE_CNA'
- Add Deny any IP traffic to 1.1.1.1/255.255.255.255
- Add Permit any IP traffic to any
- Example shown below
ISE:
Perform Posture Update (Required for ISE to recognize the OS)
- Go to ISE GUI and navigate to Administration > System > Settings
- On the left hand menu, click on Posture > Updates
- Click on 'Update Now' (Will take about 20 minutes to update, you can navigate away and perform rest of the steps below)
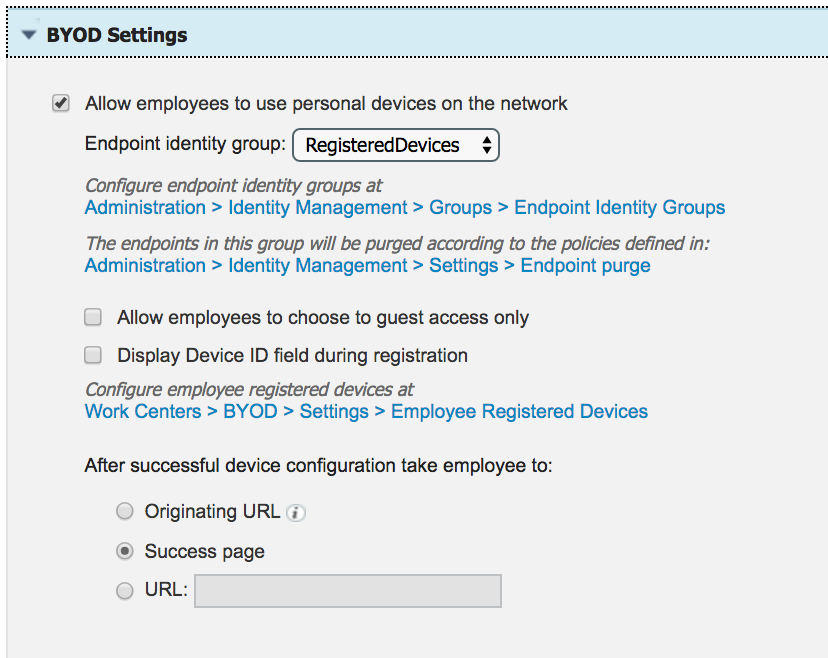
Configure Guest portal to provide BYOD for employee users
- Go to ISE GUI and navigate to Work Centers > Guest Access > Portals & Components
- Click on the 'Self-Registered Guest Portal (default)' (Or the portal that is going to be used for dual-SSID BYOD flow)
- Click on 'BYOD Settings' and enable 'Allow employees to use personal devices on the network' option
- Click 'Save'
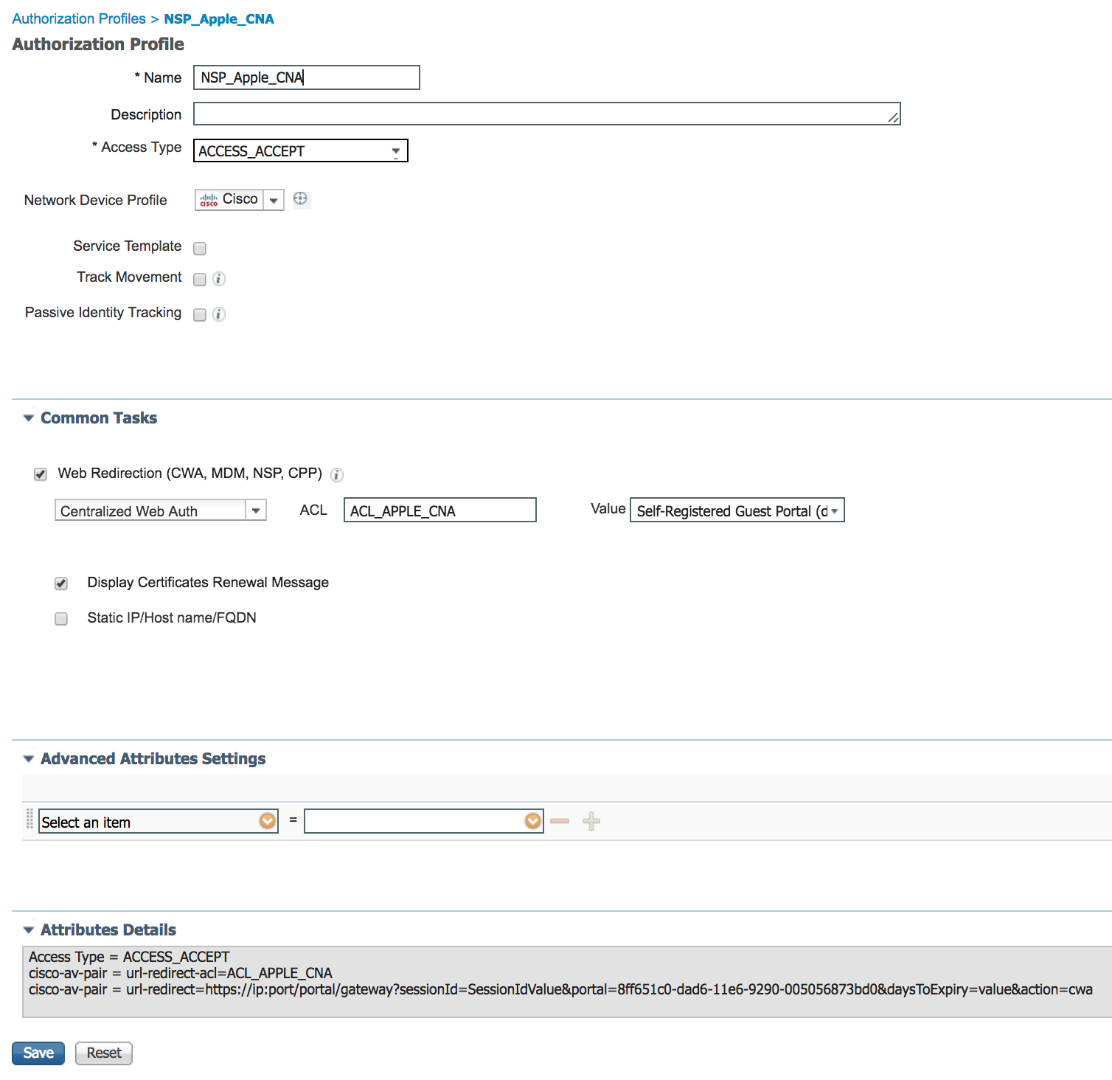
Create Additional Authorization profile to redirect any traffic that matches destination of 1.1.1.1
- Navigate to Policy > Results > Authorization > Authorization Profiles
- Click 'Add' to add a new AuthZ profile
- Enter 'NSP_Apple_CNA' as name
- Under Common Tasks section check 'Web Redirection (CWA, MDM, NSP, CPP)' and select Centralized Web Auth, enter 'ACL_APPLE_CNA' for ACL, and select 'Self-Registered Guest Portal (default)' from the list
- Click 'Save'
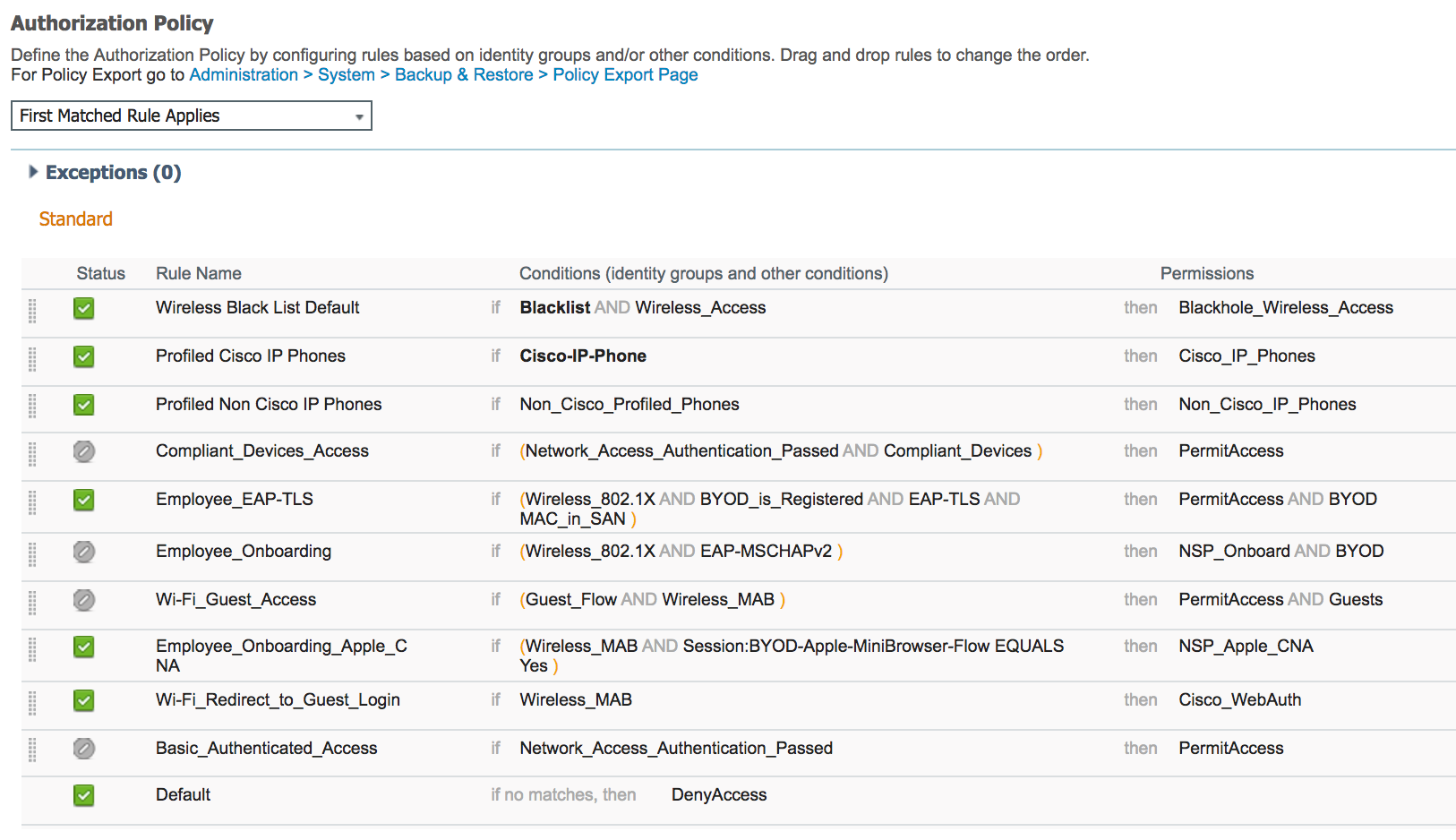
Create Authorization policy rule for Apple iOS device
- Navigate to Policy > Authorization
- Insert a New Rule Above the 'Wifi_Redirect_to_Guest_Login' and create a policy rule named 'Employee_Onboarding_Apple_CNA'
- For the condition of the rule, select 'Add Condition from Library' and then select Compound Conditions > Wireless_MAB
- Add another condition using 'Add Attribute/Value' and then select Sessions > BYOD-Apple-MiniBrowser-Flow, select 'Equals' then 'Yes'
- For the Permissions, select 'Standard' > 'NSP_Apple_CNA'
- Click 'Done' for the policy rule
- Click 'Save' on the bottom to save the policy
ISE Live Log:
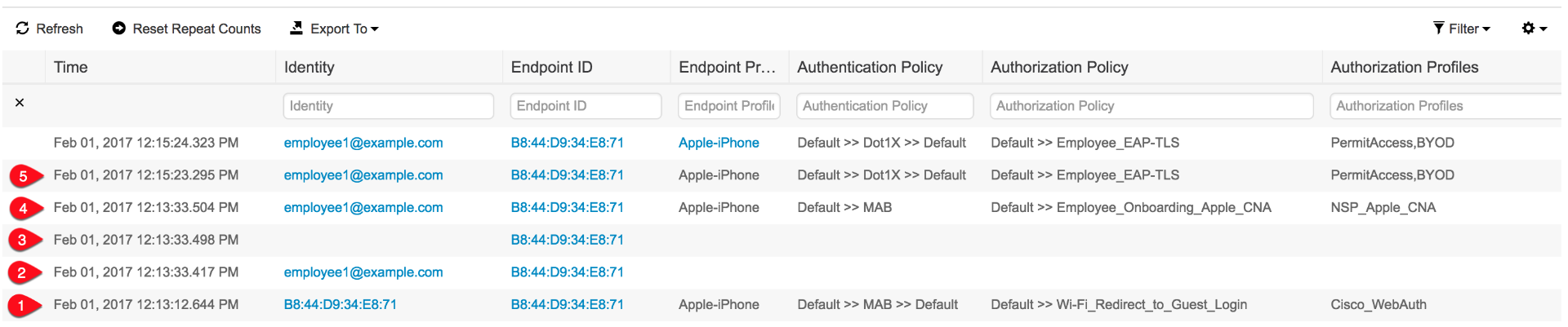
- User associates to open SSID and ISE assigns 'Cisco_WebAuth' Authorization Profile that redirects any web request to ISE WebAuth portal page
- User enters employee user ID ' employee1' and password on the WebAuth portal
- A successful login triggers CoA (Change of Authorization)
- After CoA endpoint is assigned 'NSP_Apple_CNA' which permits temporary web access so the Apple CNA is no longer enforced. At this stage only traffic to 1.1.1.1 is redirected and used to guide user through BYOD process using full browser
- Once BYOD process is completed, user connects to secured SSID and gets 'PermitAccess' Authorization Profile
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi,
thank you for your description how to handle this issue in ISE 2.2. unfortunately, it seem not to be working because the Attribute Sessions:BYOD-Apple-MiniBrowser-Flow is missing in the current version of ISE 2.2. It's simply not available to select (respectively not available in the "Session" Dictionary). We've seen that on two different Installations where we upgraded from 2.1 to 2.2.
Can you please doubecheck that? From which Version do you capture the screenshot you show us in you post?
cheers,
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Known upgrade bug - CSCvd18121 - ISE 2.2 upgrade missing the dictionary entry "Session:BYOD-Apple-MiniBrowser-Flow”
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you for the detailed setup guide. We have recently upgraded to 2.2 and are trying to get the apple mini browser setup configured. In our case the flow seems to be working as described above, but when we get to step 4 under the ISE Log section, the provisioning continues in the apple mini browser and we get a "browser not supported" error. The ACL is configured as above and gets applied, the 1.1.1.1 redirect just does not seem to open Safari to continue.
Any thoughts?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Can you describe the user experience when you say 'provisioning continues in the apple mini browser'? You should be seeing what shows up 20 seconds in to the video above where you can either click the hyperlink or done button in the mini browser.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
When the process gets to the page indicating click here when you see done, I click the hyperlink. Instead of opening and continuing in Safari, the process continues in the mini browser, and get the unsupported browser error.
Actually, it seems to be related to the iOS version. The iPad I am testing with is version 10.3.1, but I found one in our storage closet running 8.X and the process seems to work fine. It would appear that Apple has changed the behavior of the mini browser in the newest release.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks for letting us know. I also tried with iPhone running 10.3.1 and running into issues. Will let you know once we figure out a fix.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
We are running into the same issue as Stephen. When "Done" is shown in the upper right corner and the user is prompted to click the link on the page to start Safari, the BYOD flow just continues in the minibrowser instead of opening Safari.
Happens on both iPad and iPhone running version 10.3.1
The only way to get around it that I have found is to close the minibrowser but remain on the SSID by selecting Cancel and then Use Without Internet. Lastly, the user has to start the real browser, Safari, and visit any HTTP-site to trigger the BYOD portal.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks you for letting us know. We have reproduced the issue in house as well and will work on addressing the issue.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Being tracked by CSCve39167
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thank you for the update! I hope there will be a solution soon considering how hard this error is hitting BYOD customers.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Recommend looking into alternative flows for BYOD as a stop gap
Unfortunately apples a moving target here
if dual SSID is required
use 8.4 WLC code to allow mini browser for guest flows
Onboarding open
Guest open
Use single SSID flow for byod
Sent from my iPhone
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I'm testing 2.2 for a client and they are using single SSID BYOD and I'm getting the "your browser is currently unsupported" error message from the mini browser as well. Has this already been reported as well? Is the bug effecting single and dual SSID for onboarding?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
For single SSID you would suppress the mini browser
https://communities.cisco.com/docs/DOC-71469
https://communities.cisco.com/docs/DOC-71122
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Doesn’t that defeat the purpose of the new feature “Cisco ISE now supports Apple Captive Network Assistant (CNA) mini-browser for Guest and BYOD flows” that the client was highly interested in?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
No please look through the pros and cons page I sent you, please also review how it works in the dual ssid scenario. it doesn’t make sense to use the mini-browser to only suppress it 1 step later. The mini-browser from apple doesn’t support onboarding flow regardless.
We shouldn’t have a discussion on this post document If you would like more discussion post a new one.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:



