- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Duo MFA Integration with ISE for TACACS+ Device Administration with Microsoft Active Directory Users
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
07-02-2019 06:27 PM - edited 11-21-2019 07:11 PM
Overview:
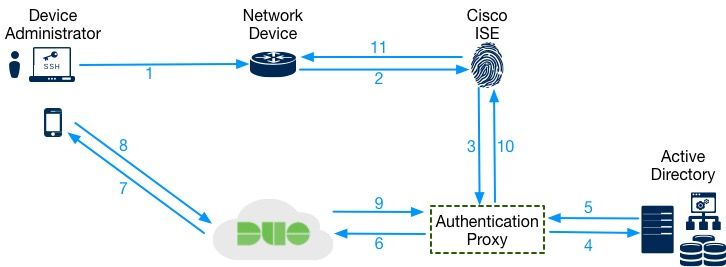
In this setup, ISE will forward the TACACS+ authentication requests to the Duo Authentication proxy. The proxy will check AD and if the authentication is successful, the end user/admin will be send a "Duo Push." If the AD authentication fails, then the process will stop and no "Duo Push" will occur.
Note: For integration with Duo, ISE and local (ISE) datastore, please visit the following link:
Detailed Steps:
- Admin user initiates a shell connection to a network device where he/she uses Active Directory based credentials
- Network device forwards the request to the TACACS+ server (ISE)
- ISE sends the authentication request to Duo's Authentication Proxy
- The proxy forwards the request to Active Directory for the 1st factor authentication
- Active Directory informs the Authentication Proxy if the authentication was successful
- Upon successful AD authentication, the Authentication Proxy sends an authentication request to Duo cloud for 2nd factor authentication
- Duo cloud sends a "push" to the admin user
- Admin user "approves" the "push"
- Duo informs the Authentication Proxy of the successful push
- Authentication proxy informs ISE of a successful Authentication
- ISE Authorizes the admin user
Assumptions:
- You have good/solid understanding of AAA concepts and configurations
- Your network access devices (Routers, Switches, Firewalls, etc) are already configured for AAA (TACACS+) with ISE
- The ISE deployment is already integrated with Active Directory
- The ISE deployment is properly licensed
Components Used:
- Active Directory running on Microsoft Server 2016
- Cisco ISE running on version 2.6 - patch-1
- Duo Authentication Proxy version 3.0.0 running on Windows 10 and Ubuntu 18
Step-1 - Duo System Configuration
- Login to your Duo account and click on "Applications"
- Search for "RADIUS" and click "Protect This Application"
- In a notepad copy and paste your Integration Key, Secret Key and API Hostname
Step-2 - Download, Install and Configure Duo's Authentication Proxy
- Download the latest Duo Authentication Proxy from this URL:
- https://duo.com/docs/authproxy-reference
- Install the authentication proxy on your Windows or Linux machine (Installation Instructions are available in the link above). In this example, I have installed the primary Authentication Proxy on a Windows 10 machine while the secondary was installed on Ubuntu
- Configure the proxy by editing the authproxy.cfg file:
[ad_client]
host=1.2.3.4 >>> IP Address/FQDN of Primary AD Server
host_2=4.3.2.1 >>> IP Address/FQDN of Secondary AD Server
service_account_username=duoservice >>> AD Service Account
service_account_password=password1 >>> AD Service Account Password
search_dn=DC=example,DC=com >>> AD Base information
!
[radius_server_auto]
ikey=xxxxxxxxxxxxxx >>> Your integration key (Step-1)
skey=xxxxxxxxxxxxxx >>> Same as above
api_host=xxxxxxxxxxxxxx >>> Same as above
radius_ip_1=10.1.1.1 >>> IP address of primary ISE PSN
radius_secret_1=xxxx >>> AAA secret
radius_ip_2=10.1.1.2 >>> IP address of secondary ISE PSN
radius_secret_2=xxxx >>> AAA secret
failmode=safe
client=ad_client >>> Instructs the proxy to use AD for 1st factor authentication
port=1812 >>> RADIUS Port
- Start the proxy server(s) and check the proxy logs for any configuration/connectivity errors:
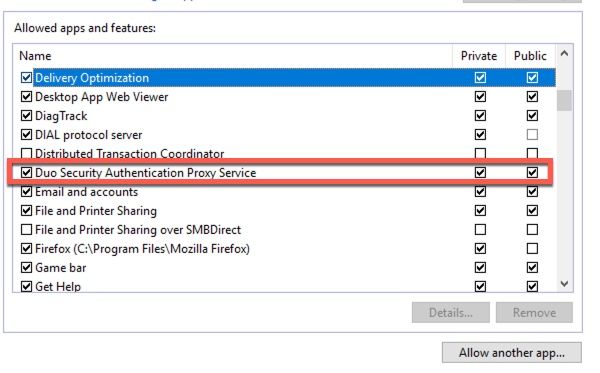
- Note: In Windows installations, make sure that the Windows Firewall is configured to allow connections for the authentication proxy:
Step-3-Configuring ISE:
Add Duo's Authentication Proxies
- Go to Administration > Identity Management > External Identity Sources > RADIUS Token > Click Add
- Give it a name
- Under the "Connection" tab, add the information from the Duo Primary and Secondary (If applicable) Authentication Proxies
- Make sure that the "Shared Secret" matches what you defined in Step-2
- Change the "Server Timeout" to a value of 30 seconds or greater in order to avoid RADIUS timeouts
- Click "Submit"
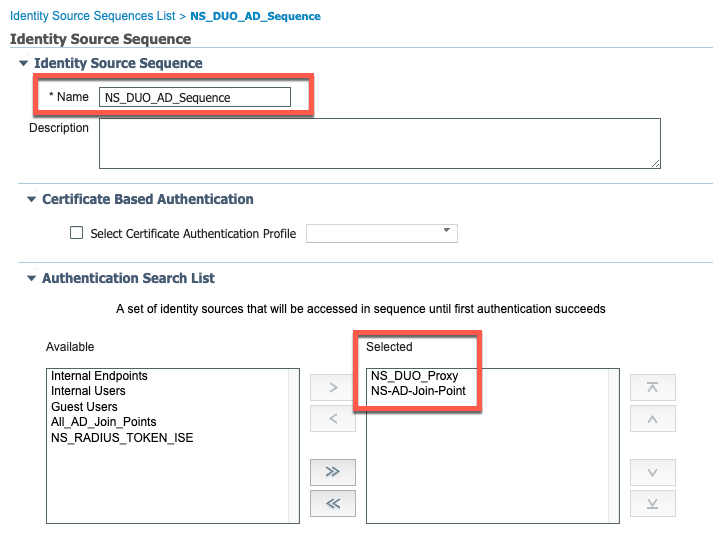
Create Identity Source Sequence
- While on the same page, click on "Identity Source Sequences" and then click "Add"
- Give it a name
- Add the newly created RADIUS Token Server and your AD-Joint point to the "Selected" column in the "Authentication Search List"
- Click "Save"
Create Device Admin Policies
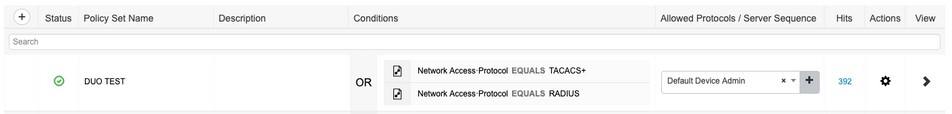
- Navigate to "Work Centers > Device Administration > Device Admin Policy Sets"
- In this example, I have created a Policy Set that matches on both protocols (RADIUS and TACACS+) with the "Allowed Protocols" set to "Default Device Admin"
- Inside my policy set, I have the following policies:
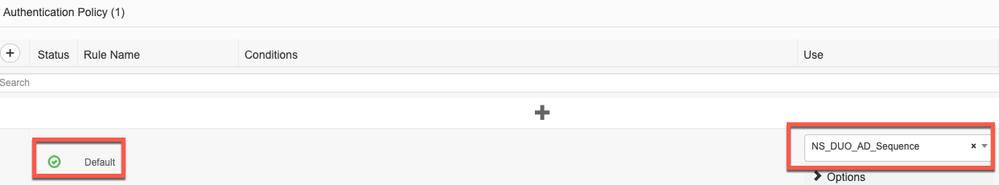
- Authentication:
- Default rule set to check the "Identity Source Sequence" that we defined in the steps above which contains the RADIUS Token Servers (Duo Authentication Proxies) and Active Directory:
- Authentication:
-
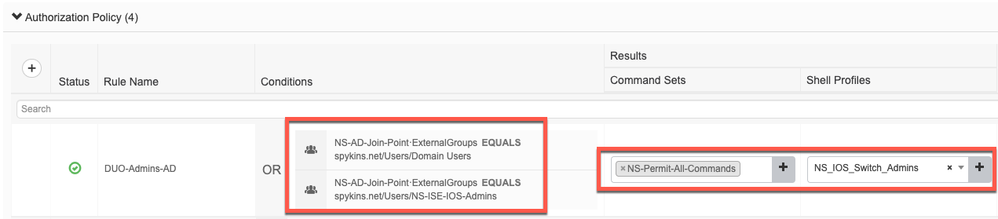
- Authorization:
- Here I have a rule that checks if the authenticated user belongs either the "Domain Users" or "NS-ISE-IOS-Admins" groups that I have configured in AD. If the user belongs to one of these groups then I am returning back my pre-configured "Command Sets" and "Shell Profile."
- Authorization:
Step-4-Add and onboard users in Duo
- Here you can configure Duo automatically sync with your Active Directory. However, this is out of scope for this document and the process that I am showing here is for manual creation of the user
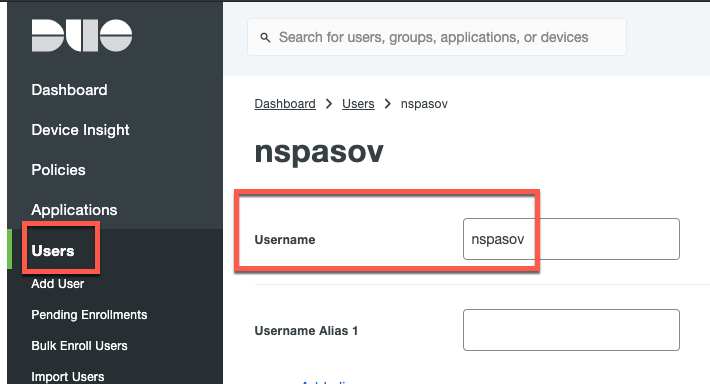
- In the Duo console go to "Users > Add Users"
- The username here must match the username that exist in your Active Directory. In my example here, I am working with the username of "nspasov"
- After the user is added, you need to enroll the user with Duo. For more information on that you can reference Duo's documentation:
Step-5-Testing
- Initiate connection (ssh or telnet) from a network device that is already added in ISE
- Use the AD credentials for the admin user
- Upon successful authentication, confirm that the user received a Duo Push
- After approving the Duo Push, the admin user should be now authenticated and authorized
- Your TACACS+ live logs in ISE should show Authentication requests against the Duo Authentication Proxies
- You can check the "authproxy" log file in your Authentication Proxy for any errors/issues
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@nspasov - great article. Thanks for creating and sharing it.
I followed your steps and got it working in my lab pretty quickly. I made a few notes that you might want to consider incorporating in the guide:
On windows, Duo Authentication Proxy installs at:
C:\Program Files (x86)\Duo Security Authentication Proxy\conf
Your text editor must be run as Administrator to edit the authproxy.cfg file
The ad_client host can be an FQDN
The radius_ip entries must be IP address format
Logs will be in:
C:\Program Files (x86)\Duo Security Authentication Proxy\log
Look at connectivity_tool.log and authproxy.log files
We click "Submit" (not "Save") when adding Duo Authentication as a RADIUS Token server to ISE and when adding the Identity Source sequence
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Than you for the feedback Marvin! I incorporated some of the changes that you suggested. The things that I left out are the windows related paths since proxy can be installed in Windows, and many flavors of Linux. Let me know what you think.
Neno
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: