- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Dynamic L2L VPN tunnel with Route Hairpin and Discontinuous subnets.
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 10-01-2012 02:44 AM
Dynamic L2L
Dynamic crypto maps gives us the opportunity to create a L2L tunnels where the remote peer's address is unknown.
The ASA configuration we have built a group called DefaultL2LGroup. If you do not configure any other matchowania to tunnel-group that is also where you will land a dynamic peer.
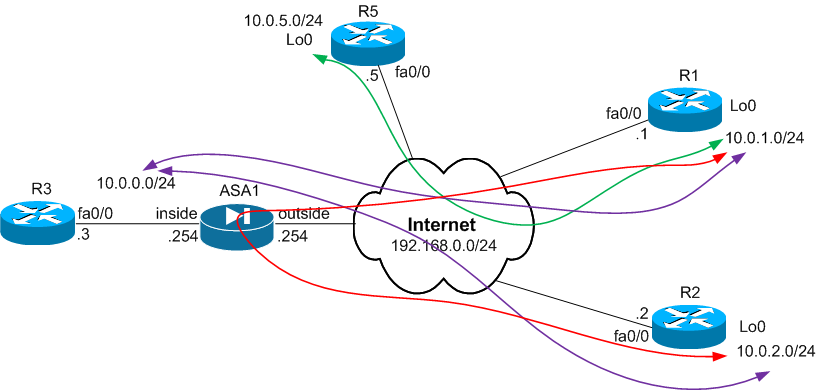
W tym przypadku będziemy szyfrować traffic pomiędzy R1 i R2. Obydwa peery maja zmieniajace sie dynamiczne IP. Uzyjemy ASA jako hub aby hairpin traffic pomiedzy nimi (czerwona linia).
Na R1 i R2 stworzymy crypto-mape zawierajaca 10.0.0.0/16 subnet.
In this case, we will encrypt the traffic between R1 and R2. Both peers may changing dynamic IP. We'll use ASA as a hub for traffic between them hairpin (red line).
Required configuration:
ASA1 will be HUB:
| ASA1 |
|---|
interface GigabitEthernet0/0 nameif outside security-level 0 ip address 192.168.0.254 255.255.255.0 ! interface GigabitEthernet0/1 nameif inside security-level 100 ip address 10.0.0.254 255.255.255.0
To grant the Route hairpin or otherwise u-turn:
same-security-traffic permit intra-interface
Create a dynamic map and binds it to static:
crypto ipsec transform-set Tr_Set esp-3des esp-sha-hmac crypto ipsec security-association lifetime seconds 28800 crypto ipsec security-association lifetime kilobytes 4608000 crypto dynamic-map Dyn_Map 10 set transform-set Tr_Set crypto dynamic-map Dyn_Map 10 set reverse-route crypto map VPN 10 ipsec-isakmp dynamic Dyn_Map crypto map VPN interface outside crypto isakmp enable outside crypto isakmp policy 10 authentication pre-share encryption 3des hash sha group 2 lifetime 86400
Remote dynamic peer will land here so I set the password:
tunnel-group DefaultL2LGroup ipsec-attributes pre-shared-key Cisco123
For demonstration purposes permit ping:
policy-map global_policy class inspection_default inspect icmp |
Configure the remote routers R1 and R2. (for dynamic related companies usually configure L2L VPN tunnel):
| R1 |
|---|
interface FastEthernet0/0 ip address 192.168.0.1 255.255.255.0 duplex auto speed auto crypto map VPN
interface Loopback0 ip address 10.0.1.1 255.255.255.0
Basic L2L configuration:
crypto isakmp policy 10 encr 3des authentication pre-share group 2 crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0 ! crypto ipsec transform-set Tr_Set esp-3des esp-sha-hmac ! crypto map VPN 10 ipsec-isakmp set peer 192.168.0.254 set transform-set Tr_Set match address VPN
Crypto map consist networks behind ASA and R2:
ip access-list extended VPN permit ip 10.0.1.0 0.0.0.255 10.0.0.0 0.0.255.255
We add routes, so router knows which interface to send traffic out:
ip route 0.0.0.0 0.0.0.0 192.168.0.254 |
| R2 |
interface Loopback0 ip address 10.0.2.2 255.255.255.0 ! interface FastEthernet0/0 ip address 192.168.0.2 255.255.255.0 duplex auto speed auto crypto map VPN
Basic L2L configuration:
crypto isakmp policy 10 encr 3des authentication pre-share group 2 crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0 ! crypto ipsec transform-set Tr_Set esp-3des esp-sha-hmac ! crypto map VPN 10 ipsec-isakmp set peer 192.168.0.254 set transform-set Tr_Set match address VPN
ip access-list extended VPN permit ip 10.0.2.0 0.0.0.255 10.0.0.0 0.0.255.255
ip route 0.0.0.0 0.0.0.0 192.168.0.254 |
| R3 |
interface FastEthernet0/1 ip address 10.0.0.3 255.255.255.0
Here, for demonstration purposes, configure IP and route:
ip route 0.0.0.0 0.0.0.0 10.0.0.254 |
Let's try to pick up a tunnel between R1 and ASA:
R1#ping 10.0.0.3 source lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.0.3, timeout is 2 seconds: Packet sent with a source address of 10.0.1.1 .!!!! |
ASA1# show crypto ipsec sa interface: outside Crypto map tag: Dyn_Map, seq num: 10, local addr: 192.168.0.254
local ident (addr/mask/prot/port): (10.0.0.0/255.255.0.0/0/0) remote ident (addr/mask/prot/port): (10.0.1.0/255.255.255.0/0/0) current_peer: 192.168.0.1
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4 #pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
local crypto endpt.: 192.168.0.254, remote crypto endpt.: 192.168.0.1 |
R1#ping 10.0.2.2 source lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.2.2, timeout is 2 seconds: Packet sent with a source address of 10.0.1.1 ..... |
We can see that the packets destined to R2 reach ASA firewall but does not know where to send:
ASA1# show crypto ipsec sa
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4 #pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9 |
Lets bridge the tunnel up between R2 and ASA:
R2#ping 10.0.0.3 source lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.0.3, timeout is 2 seconds: Packet sent with a source address of 10.0.2.2 .!!!! |
ASA1# show crypto ipsec sa
Crypto map tag: Dyn_Map, seq num: 10, local addr: 192.168.0.254
local ident (addr/mask/prot/port): (10.0.0.0/255.255.0.0/0/0) remote ident (addr/mask/prot/port): (10.0.2.0/255.255.255.0/0/0) current_peer: 192.168.0.2
#pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4 #pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
local crypto endpt.: 192.168.0.254, remote crypto endpt.: 192.168.0.2 |
We see you're using our dynamic map Dyn_Map, we used split tunneling option and we sent their proposals to the network between which you want to encrypt traffic. ASA and accept it because the option will add a reverse-route remote network to the routing table:
ASA1# sh route S 10.0.2.0 255.255.255.0 [1/0] via 192.168.0.2, outside S 10.0.1.0 255.255.255.0 [1/0] via 192.168.0.1, outside |
Now we can freely communicate between R1 and R2:
R1#ping 10.0.2.2 source lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.2.2, timeout is 2 seconds: Packet sent with a source address of 10.0.1.1 !!!!! |
For confirmation, we can look at the counters:
ASA1# sh cry ips sa interface: outside Crypto map tag: Dyn_Map, seq num: 10, local addr: 192.168.0.254
local ident (addr/mask/prot/port): (10.0.0.0/255.255.0.0/0/0) remote ident (addr/mask/prot/port): (10.0.1.0/255.255.255.0/0/0) current_peer: 192.168.0.1
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9 #pkts decaps: 14, #pkts decrypt: 14, #pkts verify: 14
local crypto endpt.: 192.168.0.254, remote crypto endpt.: 192.168.0.1
Crypto map tag: Dyn_Map, seq num: 10, local addr: 192.168.0.254
local ident (addr/mask/prot/port): (10.0.0.0/255.255.0.0/0/0) remote ident (addr/mask/prot/port): (10.0.2.0/255.255.255.0/0/0) current_peer: 192.168.0.2
#pkts encaps: 9, #pkts encrypt: 9, #pkts digest: 9 #pkts decaps: 9, #pkts decrypt: 9, #pkts verify: 9 |
Discontinuous subnets.
We now add the L2L tunnel between R1 and R5 (green line).
Observe that previously defined the alread traffic between 10.0.0.0/16 we must pay attention to the order will attach crypto maps.
Required configuration:
| R1 |
|---|
crypto map VPN 5 ipsec-isakmp set peer 192.168.0.5 set transform-set Tr_Set match address L2L_VPN
ip access-list extended L2L_VPN permit ip 10.0.1.0 0.0.0.255 10.0.5.0 0.0.0.255 |
| R5 |
interface Loopback0 ip address 10.0.5.5 255.255.255.0 ! interface FastEthernet0/1 ip address 192.168.0.5 255.255.255.0 crypto map VPN
Basic L2L configuration:
crypto isakmp policy 10 encr 3des authentication pre-share group 2 crypto isakmp key cisco123 address 0.0.0.0 0.0.0.0 ! ! crypto ipsec transform-set Tr_Set esp-3des esp-sha-hmac ! crypto ipsec profile DMVPN set transform-set Tr_Set ! crypto gdoi group GDOI identity number 1 server address ipv4 10.0.105.1 ! ! crypto map VPN 5 ipsec-isakmp set peer 192.168.0.1 set transform-set Tr_Set match address L2L_VPN We define interesting traffic between R1 and R5:
ip access-list extended L2L_VPN permit ip 10.0.5.0 0.0.0.255 10.0.1.0 0.0.0.255
And of course we must condemn the interface:
ip route 0.0.0.0 0.0.0.0 192.168.0.254 |
Let's raise our first Pre-configured dynamic tunnels between ASA and R1:
R1#ping 10.0.0.3 so lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.0.3, timeout is 2 seconds: Packet sent with a source address of 10.0.1.1 .!!!! |
R1#show crypto ipsec sa
interface: FastEthernet0/1 Crypto map tag: VPN, local addr 192.168.0.1
protected vrf: (none) local ident (addr/mask/prot/port): (10.0.1.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (10.0.0.0/255.255.0.0/0/0) current_peer 192.168.0.254 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4 #pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4 |
Let's try now initiate traffic from R1 to R5. You'll notice that we already have the SPI for the traffic (between R1 and ASA). Adding additional crypto map number 5 because we used an additional tunnel will be raised:
R1#ping 10.0.5.5 so lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.5.5, timeout is 2 seconds: Packet sent with a source address of 10.0.1.1 .!!!! |
R1#show crypto ipsec sa
interface: FastEthernet0/1 Crypto map tag: VPN, local addr 192.168.0.1
protected vrf: (none) local ident (addr/mask/prot/port): (10.0.1.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (10.0.0.0/255.255.0.0/0/0) current_peer 192.168.0.254 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4 #pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4
local crypto endpt.: 192.168.0.1, remote crypto endpt.: 192.168.0.254 path mtu 1500, ip mtu 1500, ip mtu idb FastEthernet0/1 current outbound spi: 0xD269F443(3530159171)
protected vrf: (none) local ident (addr/mask/prot/port): (10.0.1.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (10.0.5.0/255.255.255.0/0/0) current_peer 192.168.0.5 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4 #pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4 |
It will be also operated game will be initiated traffic R5 to R1.
R5#ping 10.0.1.1 so lo0 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.1.1, timeout is 2 seconds: Packet sent with a source address of 10.0.5.5 .!!!! |
Proper crypto map is used on R1:
R1#show crypto ipsec sa
interface: FastEthernet0/1 Crypto map tag: VPN, local addr 192.168.0.1
protected vrf: (none) local ident (addr/mask/prot/port): (10.0.1.0/255.255.255.0/0/0) remote ident (addr/mask/prot/port): (10.0.5.0/255.255.255.0/0/0) current_peer 192.168.0.5 port 500 PERMIT, flags={origin_is_acl,} #pkts encaps: 4, #pkts encrypt: 4, #pkts digest: 4 #pkts decaps: 4, #pkts decrypt: 4, #pkts verify: 4 |
Scenario 2
Problem:
User need to set up L2L VPN between two devices.The VPN needs to pass traffic for several sub-nets.There are routers behind all the equipment, so routing isn't a problem, and I understand how to do the traffic matching ACLs so that we get the correct traffic sent over the link.
Background info, this is a CME router that's portable in a case, and is designed to operate either off a satellite link or a direct Ethernet link to some public Internet access.
The router does an IPSec L2L VPN back to home, and allows an H.323 trunk to permit calling between the phones on the remote system and the main phone system at the head end site.
- Main site is an ASA 5505 with a static public IP.
- Remote site is a 2911 router
- The router has a fixed IP address on a satellite link (FastEthernet 0/1)
- That link is connected to a satellite modem.
- The router also has FastEthernet 0/0 set up as DHCP.
The Cisco document states that the IPSec L2L tunnels require static IP addressing on each end - "tunnel-group 172.17.1.1 type ipsec-l2l
!--- In order to create and manage the database of connection-specific
!--- records for ipsec-l2l—IPsec (LAN-to-LAN) tunnels, use the command
!--- tunnel-group in global configuration mode.
!--- For L2L connections the name of the tunnel group MUST be the IP
!--- address of the IPsec peer.
tunnel-group 172.17.1.1 ipsec-attributes
pre-shared-key *
!--- Enter the pre-shared-key in order to configure the
!--- authentication method".
I asked the vendor for the CME equipment about just using EasyVPN in NEM mode, since I know that would route networks, but he said that won't work for multiple subnets behind routers behind the VPN-endpoints.
Is it in fact possible to establish an IPSec L2L VPN tunnel between an ASA with a fixed IP and a remote 29XX router with a dynamic IP address, and route several subnets over that link?
Well actually to establish a L2L from a unknown IP address, you have two options:
1- Use the DefaultL2LGroup.
2- Use certificate authentication.
If a connection arrives as a L2L and the ASA does not have either a crypto map or a tunnel-group, the connection will be landed on the DefaultL2LGroup and the correct dynamic-map.
So, please check this out:
Dynamic IPsec Tunnel Between a Statically Addressed ASA and a Dynamically Addressed Cisco IOS Router
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a0080b3d511.shtml
You can have multiple subnets behind the inside interface of an EasyVPN remote. The feature is named "Multiple Subnet Support" and is described in the configuration-guide:
Source Discussion:
https://supportforums.cisco.com/discussion/11559901/2900-router-asa-l2l-vpn-router-side-dynamic-ip
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: