- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Evolving IOT from MAB to 802.1x
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 04-07-2025 06:34 AM
Objective
The objective of this Article is to propose suggestions for the evolution of Network Authentication from MAB to 802.1x in IoT Devices, with the aim of mitigating the exploitation of Layer 2 Attacks such as MAC-Address Cloning and Man in the Middle. It is worth remembering that this evolution does not eliminate the need for Segmentation, whether done by ACL, Firewall between VLANs or ServiceTag.
Scenario
Currently, most IoT devices support the 802.1x Protocol, therefore, Cameras, DRVs, Printers, Telephones, Temperature and Light Controllers, among others, already have in their firmware the possibility of working in a better way (not MAB) with Networks protected with NAC.
 Imagem das configurações de 8021.x para um determinado DVR
Imagem das configurações de 8021.x para um determinado DVR
The most common Protocol options for implementing 802.1x on a Wired Network are:
- EAP-MD5 using Credentials, but this is the least secure option.
- EAP-PEAP using Credentials and a Certificate from a CA that the NAC trusts. PEAP encapsulates EAP packets in an Encrypted and Authenticated Transport Layer Security (TLS) tunnel.
- EAP-TLS using a Digital Certificate. EAP-TLS is known for its strong security and is widely used in environments that require high security, such as Corporate Wireless Networks and VPNs.
Proposal
Sometimes, due to the lack of a Digital Certificate auto-enrollment system in the IoT software, the challenge of keeping Digital Certificates updated will have a high operational cost depending on their validity period. As a result of this absence, we chose to use Credentials from a Directory Service together with the CA Certificate, both trusted by the NAC. This way, we will have Encryption and Security in storing Credentials.
Therefore, we will use EAP-PEAP using the CA certificate that the NAC trusts and a Service Account in the Directory (AD or LDAP).
Important: If you use this Directory Service to provide access to other Network equipment such as Workstations, take measures to ensure that this Account does not log in to the Workstations and that it is also not possible to escalate privileges from it. This is due to the risk of Data (Credentials) being extracted from the IoT after it has been configured in the event of theft, for example.
NAC Rules (Cisco ISE)
Verify that NAC can understand the PEAP protocol (at Policy > Policy Elements > Authentication > Allowed Protocols) and is connected to External Identity Sources (at Administration > Identity Management > External Identity Sources), such as Active Directory:
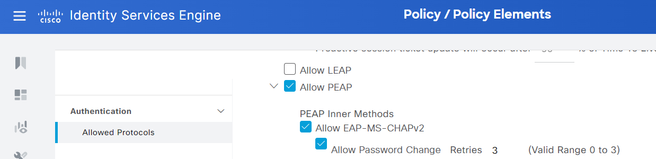
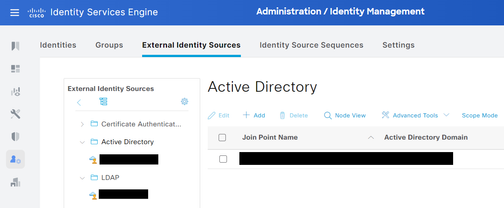
Verify that the Authentication Policy of your Policy Set points to the chosen Directory Service.
The Authorization Policy is as shown in the image below:
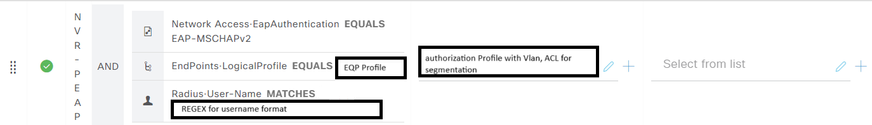
Automation Suggestion
To automate this process we will need:
- Password vault with API support
- IOT with remote configuration API
- Access to the ISE API
Given the prerequisites met, a script can be developed according to the flow in the image below:
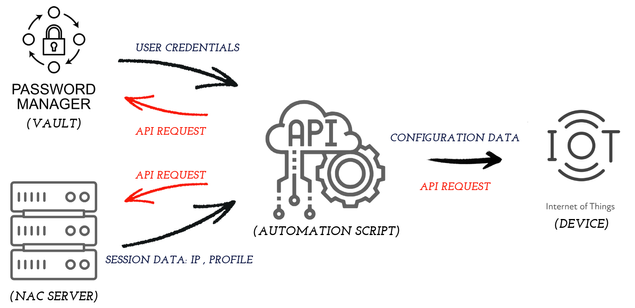
The credentials will be provided by the Password vault via API.
The Session Data such as IP for remote connection and Device Profile, to know which API will be used by the IoT device, will be queried via the REST API of the NAC controls – Cisco ISE.
Note: In this step, a temporary MAB assignment must be assigned for the initial entry of this device into the network.
With the Credentials obtained from the vault and the Network Data obtained from ISE, the API language for which the IoT device should be configured is selected and this process is started.
Once configured, a check on ISE can confirm whether authentication has evolved to 802.1x.
With these suggestions, I hope to have helped create an additional layer of Network Protection, especially focusing on these Devices that are increasingly growing in number on Corporate Networks.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Renato Guardia ... thanks for sharing !!!
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Very helpful! Thanks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
@Leonardo Almeida thanks
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:
