- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Firepower drops RDP traffic after SRU Rule Update 2019-05-24-001
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-25-2019 10:45 AM - edited 06-03-2019 08:11 AM
- Introduction
- SRU Installs
- SRU2019-05-24-001
- SRU2019-05-25-001
- Workaround by Updating SRU
- Workaround without Updating by Disabling the SIDs
- Verification:
- If additional issues persist:
Introduction
This document describes TALOS Signature Rule Update 2019-05-24-001 and Cisco Bug CSCvp90060 which causes Remote Desktop Protocol (RDP) connections to fail.
Currently the recommendation for this is to install the new SRU to amend this issue.
RCA Documentation now attached to Community post.
Contributed by Jeff Jackson, Cisco Technical Consulting Engineer.
Edited by Cesar Lopez Zamarripa, Cisco Technical Consulting Engineer.
SRU Installs
In most environments, Firepower SRU installs are automatically set to be downloaded and installed periodically.
The advantage of this configuration is that this allows the device to be properly prepared for Urgent new Attacks and vectors.
Unfortunately, a recent SRU (2019-05-24-001) has been showed to have a rule that is causing unnecessary SRU drops for RDP traffic.
SRU 2019-05-24-001
On May 24th a new SRU was created which included the following SID's to be used for an RDP Vector.
You can find the full list of changes at the following location:
https://snort.org/advisories/talos-rules-2019-05-24
Inside this Rule update, the following SID's were added for RDP protection:
| SID | Rule Information | |
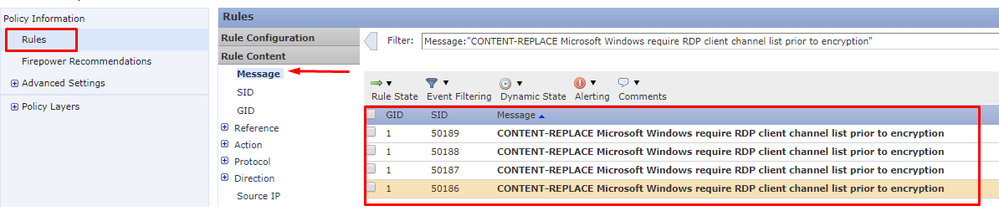
| 1:50186 | CONTENT-REPLACE Microsoft Windows require RDP client channel list prior to encryption (content-replace.rules) | |
| 1:50187 | CONTENT-REPLACE Microsoft Windows require RDP client channel list prior to encryption (content-replace.rules) | |
| 1:50188 | CONTENT-REPLACE Microsoft Windows require RDP client channel list prior to encryption (content-replace.rules) | |
| 1:50189 | CONTENT-REPLACE Microsoft Windows require RDP client channel list prior to encryption (content-replace.rules) | |
When installed, these rules may impose false positives blocking safe and controlled RDP connections.
In many environments, these rules can be temporarily disabled while this is amended.
SRU 2019-05-25-001
As of now, a new SRU has been released to automatically resolve this behavior.
You can find the full list of changes at the following location:
https://snort.org/advisories/talos-rules-2019-05-25
Inside this Rule update, the following SIDs in question for the RDP issue have been removed for now until the rules can be re-tuned.
Workaround by Updating SRU
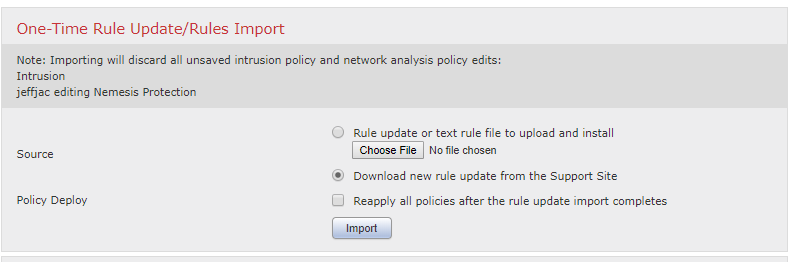
To install the new SRU, please go to your Management Center or Management GUI of your device and go to the updates page itself.
Once you are on the updates page, you can install this by using the following option:
Step 1: On the Rule section of the update page, please select Download new Rule from the support site or manually update the rule package.
Warning: If you select to Reapply all polices after the rule update, please note that this will cause a Snort Restart for your environment during the deploy which can cause a short outage due to the Inspection process restarting.
Step 2: Once the update is complete, you can verify that it is currently running by checking the Version on the top left corner. 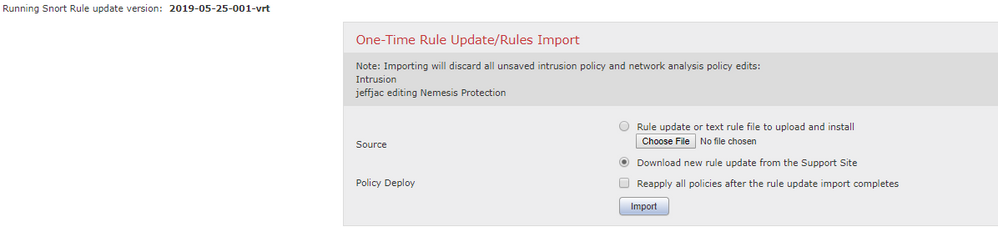
Step 3: If you did not decide to deploy when the download was completed, you will have to deploy this change out to devices.
Please note that upon deploy this will cause a snort restart similar to all other upgrades for the changing of the rules themselves.
Workaround without Updating by Disabling the SIDs
Currently, the best recommendation if you are affected is to disable the SID's themselves until the rules are released with the upcoming update.
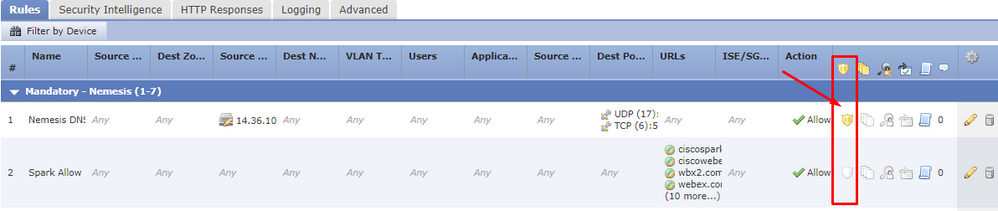
Step 1: Verify your IPS Policy Configured
In your Access Control Policy, you can see your IPS policies configured by following the yellow Shield Icon representing the protection.
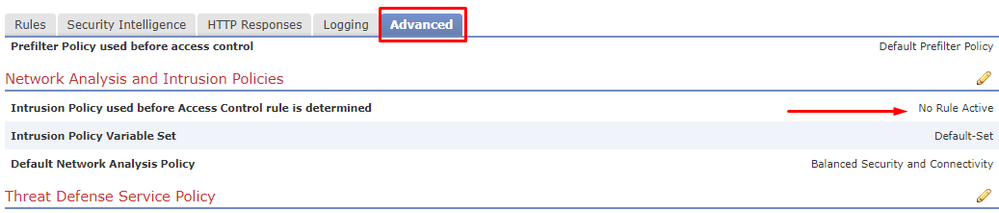
In some environments, you will see a section stated as "Intrusion Policy used before Access Control rule is determined" - This policy will also need to be edited if it is any other field than "No Rule Active"
Warning: If you are using the Default Policies labeled Maximum Detection, Connectivity Over Security, Balanced Security and Connectivity, and Security Over Connectivity, you will need to create a new IPS policy based upon these for editing individual rule criteria.
You can find more information on this in the Firepower Configuration Guide listed here: https://www.cisco.com/c/en/us/td/docs/security/firepower/630/fdm/fptd-fdm-config-guide-630/fptd-fdm-intrusion.html
Step 2: Locate the IPS Rules
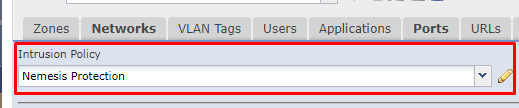
Once your IPS Policy is located by clicking on the shield, you will then need to edit and locate the rules.
Once you click on the edit pencil, it will take you to the Intrusion Policy Editor.
When you are at the editor itself, Click into the "Rules" Section and select the "Message" option in the Rule Content Box.
Inside the message popup, you will enter in the following content: "CONTENT-REPLACE Microsoft Windows require RDP client channel list prior to encryption"
This will present the four rules in question for Configuration
Step 3: Configuring the rules
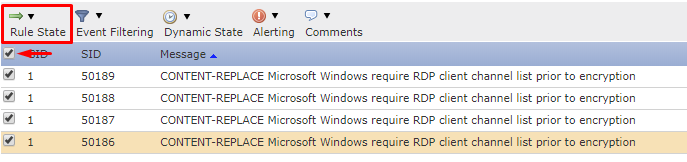
Once the rules are located, select their configuration icon and change them to disabled.
To do this, select the Check Box at the top which selects all rules and then utilize the rule state selectable option to change the rule state to 'Disable'
Step 4: Repeat to all Policies
As of now, until the rules are updated, you will need to utilize this across all policies on your Management Center itself.
Verification:
When at the rule section location, you can verify if these rules are enabled by monitoring the right-hand side of the rule which states its individual rule state.
If the rule itself shows a "Greyed out" green arrow, you can verify that the rule is disabled and not being utilized in your policy.
If the rule does not exist, this is due to you running the new install with this removed.
If additional issues persist:
In the event that you continue to face any issues, please reach out to TAC for continued assistance.
Root Cause Analysis report has been attached to the article as a PDF file.
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I wonder why we did not see the blocked connection in the connection event table or in the intrusion event table?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi gsturcotte,
The reason why events weren't genereated seems to be related to the fact of the rule been written not to drop a packet but to modify a flag inside of it. The root cause is still being investigated. Once there is a definitve statement, this document will be updated.
- Cesar
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
What about APPLE support software ARD (Apple Remote Desktop) ? Is this impacted?
Thanks
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: