- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Firepower Threat Defense (NGFWv) on UCS E-Series blade on ISR 4K - Routed Mode in HA
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
11-12-2017 09:26 PM - edited 03-08-2019 07:02 PM
- Documentation
- Code download links
- Goal
- Requirement
- Limitations
- Supported ISR and UCS-E Model
- Supported ISRG2 and UCS-E Blades:
- Supported ISR4K and UCS-E Blades:
- TopologyStep by Step Configuration
- Configure one of the connectivity options to access the Cisco IMC from the network
- Router Configuration for management
- Upgrade CIMC to the latest firmware
- Install the ESXi 5.5 or ESXi 6.0 on UCS-E via CMIC
- Configure the Vswitch and Port Groups with the appropriate VNIC
- FMC
- FTD
- Install the NGFWv (FTDv) on ESXi running on two different UCS-E modules
- Router Configuration for FTD in HA in Routed Mode
- Vmware ESXi host Network Configuration
- Configure the NGFWv High Availability between them through Firepower Management Center(FMC)
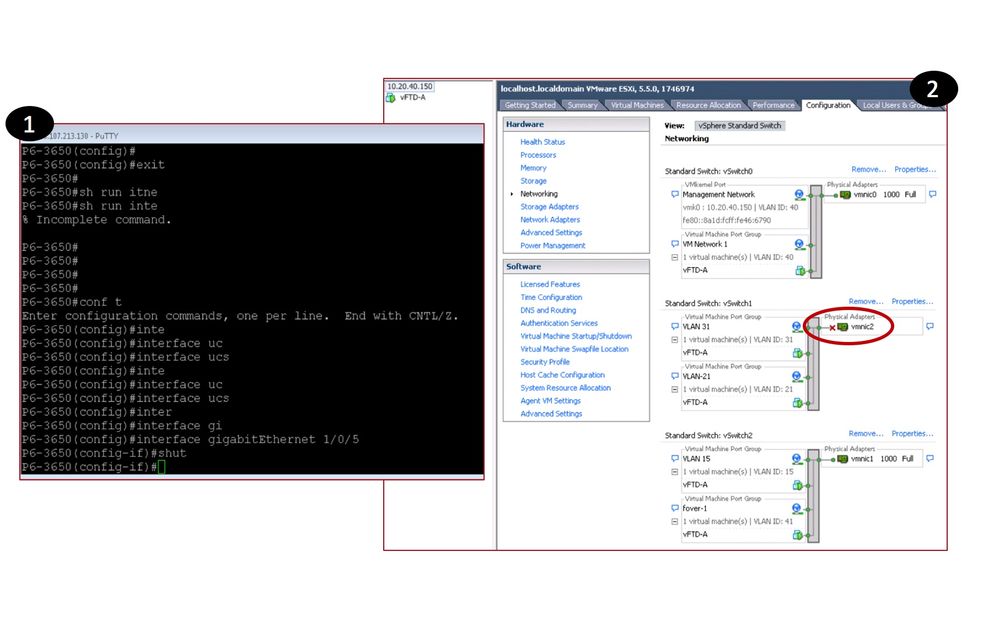
- NGFWv Interface Configuration and Status
- NGFWv HA Failover Function (External Link failure Testing)
- NGFWv HA Failover Function (Internal Link failure Testing)
- NGFWv HA failover not triggered during the internal interface failureNGFWv HA Failover Function
Documentation
UCS E-Series Configuration Guide:
http://www.cisco.com/c/en/us/td/docs/unified_computing/ucs/e/2-0/gs/guide/b_2_0_Getting_Started_Guide.html
Cisco UCS E-Series Getting Started Guide:
https://www.cisco.com/c/en/us/td/docs/unified_computing/ucs/e/3-1-1/gs/guide/b_Getting_Started_Guide.html#task_B4052C8757D74555A073C0BD759B211D
UCS E-Series Troubleshooting Guide:
http://www.cisco.com/c/en/us/td/docs/unified_computing/ucs/e/ts/guide/e_series_ts.html
Firepower Virtual Appliance and Defense Center Data Sheet:
https://na8.salesforce.com/sfc/p/#80000000dRH9KXPLJqkSwWBoW3e_vtLbnXOyiNg=
Firepower 3D System Virtual Installation Guide:
http://www.cisco.com/c/en/us/support/security/ngips-virtual-appliance/tsd-products-support-series-home.html
Firepower Management Center User Guide:
https://www.cisco.com/c/en/us/support/security/defense-center/products-installation-and-configuration-guides-list.html
Code download links
Firepower Management Center VM Download:
https://software.cisco.com/download/release.html?mdfid=286259687&softwareid=286271056&release=5.4.1.6&relind=AVAILABLE&rellifecycle=&reltype=latest
Firepower Sensor VM Download:
https://software.cisco.com/download/release.html?mdfid=286259690&softwareid=286271056&release=5.3.0.8&relind=AVAILABLE&rellifecycle=&reltype=latest
ESXi 5.0 or above. You can download VMWare customized image for Cisco here:
https://my.vmware.com/web/vmware/details?downloadGroup=CISCO-ESXI-5.1.0-GA-25SEP2012&productId=284
UCS E-Series Images:
https://software.cisco.com/download/navigator.html?mdfid=284467266
Download the latest CIMC HUU and upgrade the BIOS, CIMC and other firmware components per this link: http://www.cisco.com/c/en/us/td/docs/unified_computing/ucs/e/2-0/gs/guide/b_2_0_Getting_Started_Guide/b_2_0_Getting_Started_Guide_chapter_01010.html#task_B4052C8757D74555A073C0BD759B211D
Goal
To implement Firepower (NGFWv) in Routed High Availability Mode using two UCS-E blades on ISR 4K
Requirement
NGFW VM requirement is 8X4X40 (8 GB RAM, 4 vCPUs and 40 GB drive space). ESXi takes up 11 GB of space. So clearly a 50 GB drive is not sufficient.
Limitations
- Restrictions for Bridge Domain Interfaces
- Only 4096 bridge domain interfaces are supported per system.
- Bridge domain interfaces do not support the following features:
- Bidirectional Forwarding Detection (BFD) protocol
- Netflow
- QOS
- Network-Based Application Recognition (NBAR) or Advanced Video Coding (AVC)
- ZBF Refer: CSCui86271
- For a BDI, the maximum transmission unit (MTU) size can be configured between 1500 and 9216 bytes.
- Cryptographic VPNs are not supported in combination with BDI.
- MPLS is not supported on bridge domain interfaces.
- PPP over Ethernet (PPPoE)
Supported ISR and UCS-E Model
Supported ISRG2 and UCS-E Blades:
|
ISR Platform |
Cisco UCS EN140N |
Cisco UCS EN120S and E140S |
Cisco UCS E140D and E160D-M2 |
Cisco UCS E160D-M1 and E180D |
|
1921 |
No |
No |
No |
No |
|
1941 |
No |
No |
No |
No |
|
2901 |
No |
No |
No |
No |
|
2911 |
No |
1 |
No |
No |
|
2921 |
No |
1 |
1 |
No |
|
2951 |
No |
2 |
1 |
No |
|
3925 |
No |
2 |
1 |
1 |
|
3945 |
No |
4 |
1 |
1 |
|
3925E |
No |
2 |
1 |
1 |
|
3945E |
No |
4 |
1 |
1 |
Supported ISR4K and UCS-E Blades:
|
ISR Platform |
Cisco UCS EN120E |
Cisco UCS EN140N |
Cisco UCS EN120S and E140S |
Cisco UCS E140D and E160D-M2 |
Cisco UCS E160D-M1 and E180D |
|
4321 |
No |
2 |
No |
No |
No |
|
4331 |
No |
2* |
1 |
No |
No |
|
4351 |
No |
3* |
2 |
1 |
1 |
|
4431 |
No |
3 |
No |
No |
No |
|
4451 |
No |
3* |
2 |
1 |
1 |
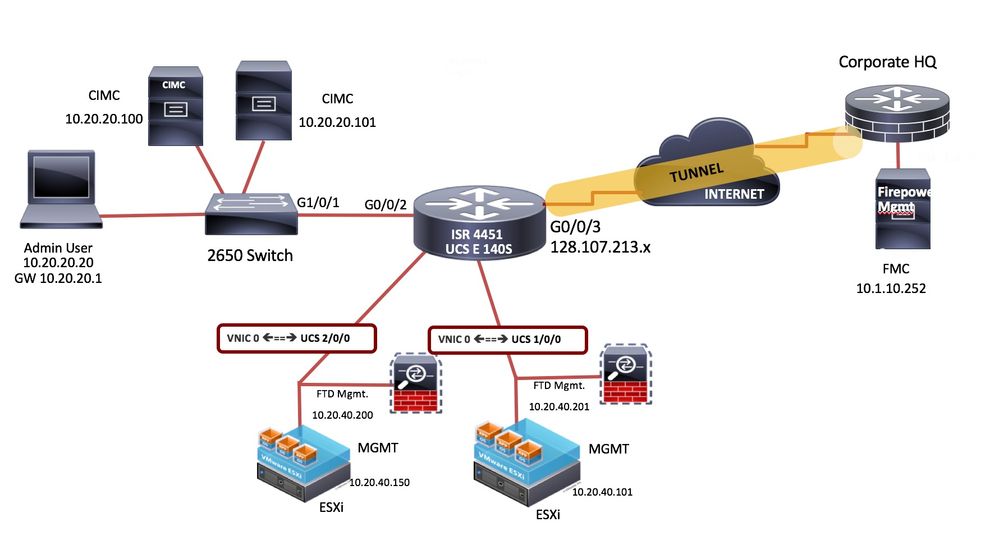
Topology Step by Step Configuration
Step by Step Configuration
Configure one of the connectivity options to access the Cisco IMC from the network
1. Dedicated Management Access
ISR4k(config)#ucse subslot 1/0
ISR4k(config-ucse)# imc access-port dedicated
ISR4k(config-ucse)# imc ip address 10.20.20.100 255.255.255.0 default-gateway 10.20.20.1
2. Shared Management Access with External ports
ISR4k(config)#ucse subslot 1/0
ISR4k(config-ucse)#imc access-port shared-lom GE2
ISR4k(config-ucse)# imc ip address 10.20.20.100 255.255.255.0 default-gateway 10.20.20.1
3. Shared Management Access with Internal ports
ISR4k(config)#ucse subslot 1/0
ISR4k(config-ucse)#imc access-port shared-lom console
ISR4k(config-ucse)# imc ip address 10.20.20.100 255.255.255.0 default-gateway 10.20.20.1
Router Configuration for management
bridge-domain 10
bridge-domain 40
interface GigabitEthernet0/0/2
no ip address
media-type rj45
negotiation auto
service instance 10 ethernet
encapsulation dot1q 10
rewrite ingress tag pop 1 symmetric
bridge-domain 10
!
service instance 40 ethernet
encapsulation dot1q 40
rewrite ingress tag pop 1 symmetric
bridge-domain 40
!
interface BDI10
vrf forwarding mgmt
ip address 10.20.20.1 255.255.255.0
!
interface ucse 1/0/0 and ucse 2/0/0
no ip address
no negotiation auto
service instance 40 ethernet
encapsulation dot1q 40
rewrite ingress tag pop 1 symmetric
bridge-domain 40
!
interface BDI40
vrf forwarding mgmt
ip address 10.20.40.1 255.255.255.0
Upgrade CIMC to the latest firmware
Get the latest XE, IOS and CIMC images
Download the latest CIMC HUU and upgrade the BIOS, CIMC and other firmware components per this link: http://www.cisco.com/c/en/us/td/docs/unified_computing/ucs/e/2-0/gs/guide/b_2_0_Getting_Started_Guide/b_2_0_Getting_Started_Guide_chapter_01010.html#task_B4052C8757D74555A073C0BD759B211D
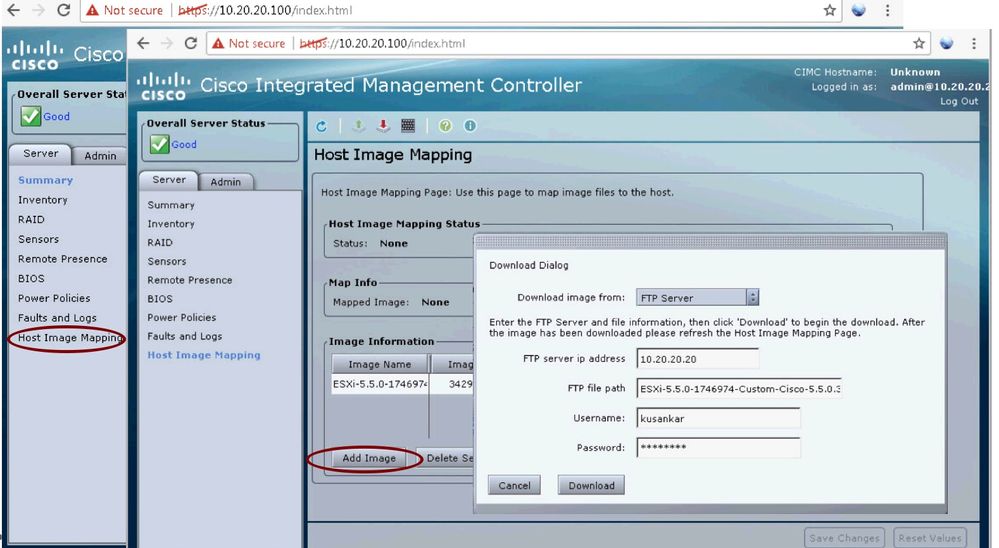
Install the ESXi 5.5 or ESXi 6.0 on UCS-E via CMIC
From the admin PC connect to CIMC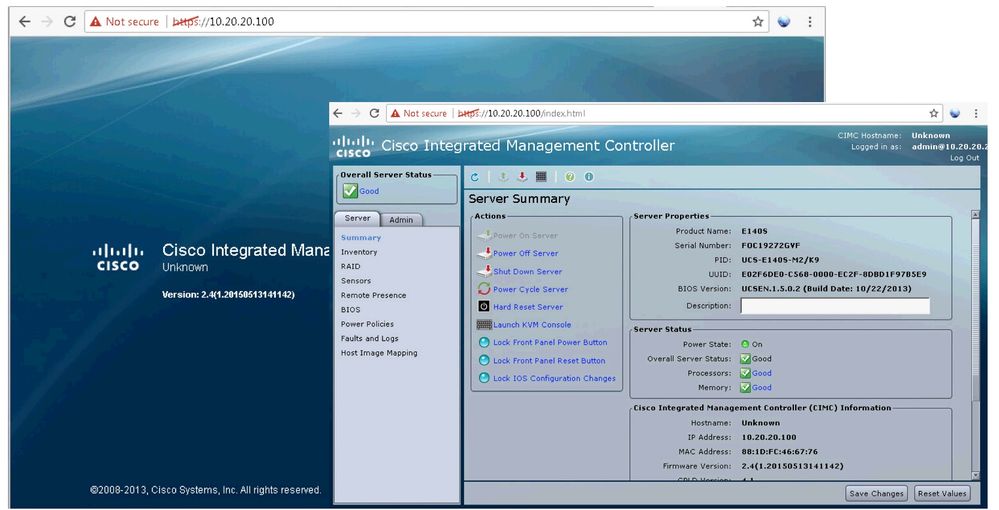
Map the ESXi image

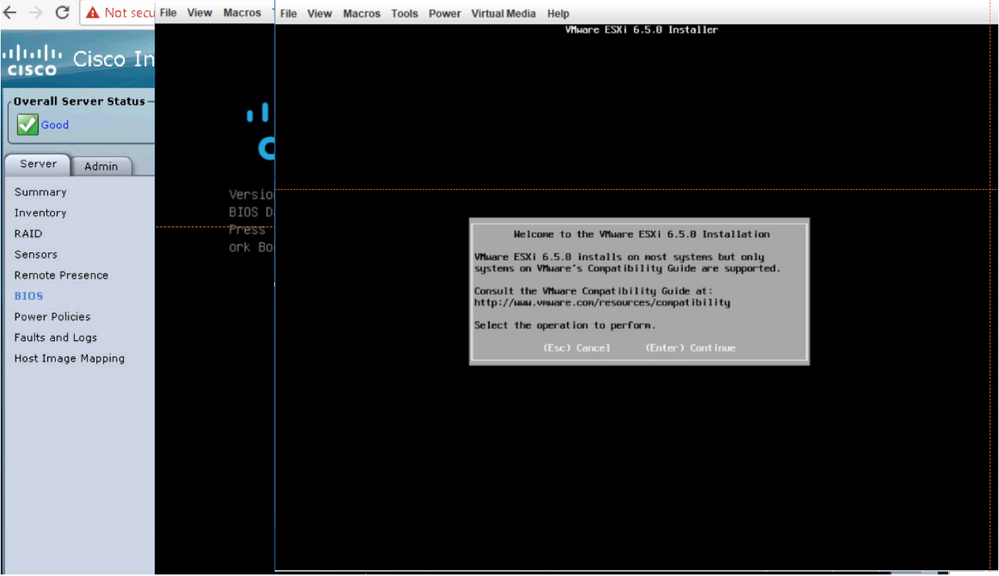
Change the boot order to boot into the mapped image
Continue installing ESXi

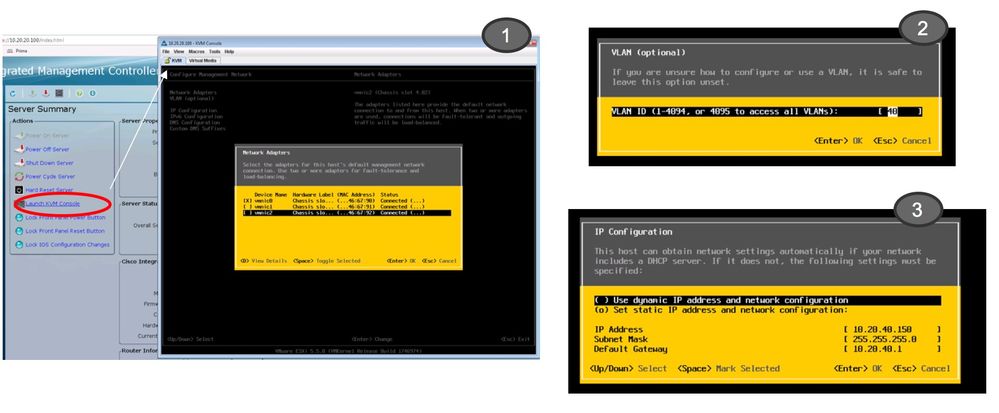
Configure the ESXi management settings to access it from the network
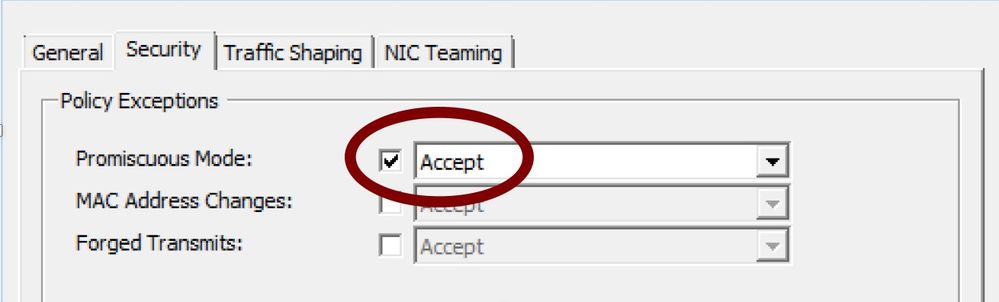
Configure the Vswitch and Port Groups with the appropriate VNIC 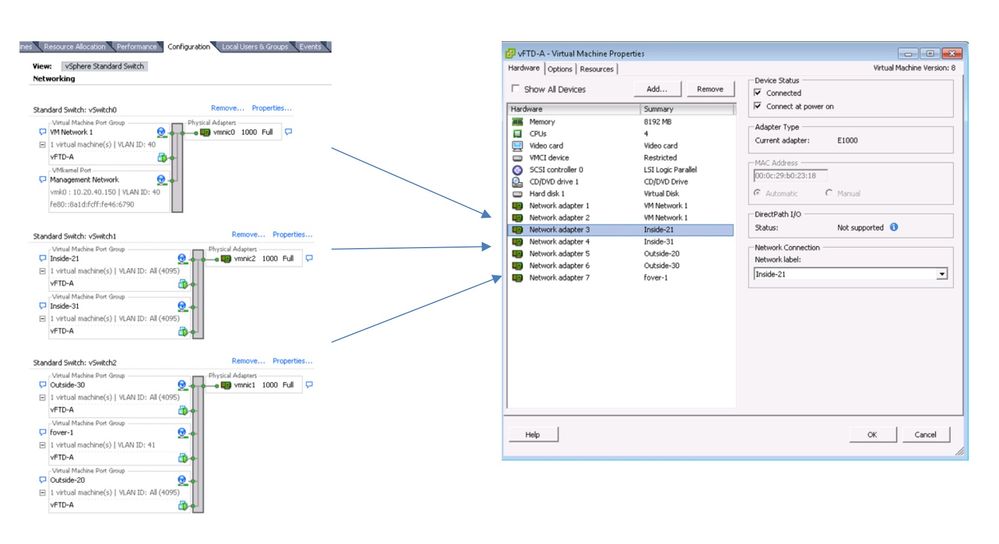
Make sure to set the network adapter to accept the following modes:
promiscuous, MAC address Changes and Forged Transmits.
FMC
Use sudo /usr/local/sf/bin/configure-network to configure the management settings
Configure Management IP, Subnet and Default Gateway
Open https GUI connection to add the NGFWv to FMC
FTD
User is prompted for EULA and post-boot configuration
configure manager add <manager ip> <user chosen id>
Install the NGFWv (FTDv) on ESXi running on two different UCS-E modules
Repeat the steps above on the second UCS-E blade if configuring HA.
Router Configuration for FTD in HA in Routed Mode
EVC Configuration in ISR 4451 For UCSE 1/0/1, UCSE 2/0/1 and static configuration
bridge-domain 41 (failover)
bridge-domain 15
interface ucse1/0/1 and ucse 2/0/1
no ip address
no negotiation auto
switchport mode trunk
service instance 15 ethernet
encapsulation dot1q 15
rewrite ingress tag pop 1 symmetric
bridge-domain 15
!
service instance 41 ethernet
encapsulation dot1q 41
rewrite ingress tag pop 1 symmetric
bridge-domain 41
!
interface BDI15
mac-address 0001.0001.0001
ip address 10.10.10.1 255.255.255.0
ip nat inside
!
ip route 10.20.20.0 255.255.255.0 10.10.10.10
ip route 10.20.30.0 255.255.255.0 10.10.10.10
!
ip route 0.0.0.0 0.0.0.0 128.107.213.129
ip route 128.107.213.192 255.255.255.255 10.10.10.10
!
ip nat inside source list NAT-ACL interface GigabitEthernet0/0/3 overload
UCS-E Exernal Ports (G2) for VLAN 21 and VLAN 31
No Configuration required in Router for the external interfaces connected to the Switch directly
The switch port connected to the UCS-E external ports should be enabled with the trunk port for VLANs ( in this use case vlan 21 and vlan 31)
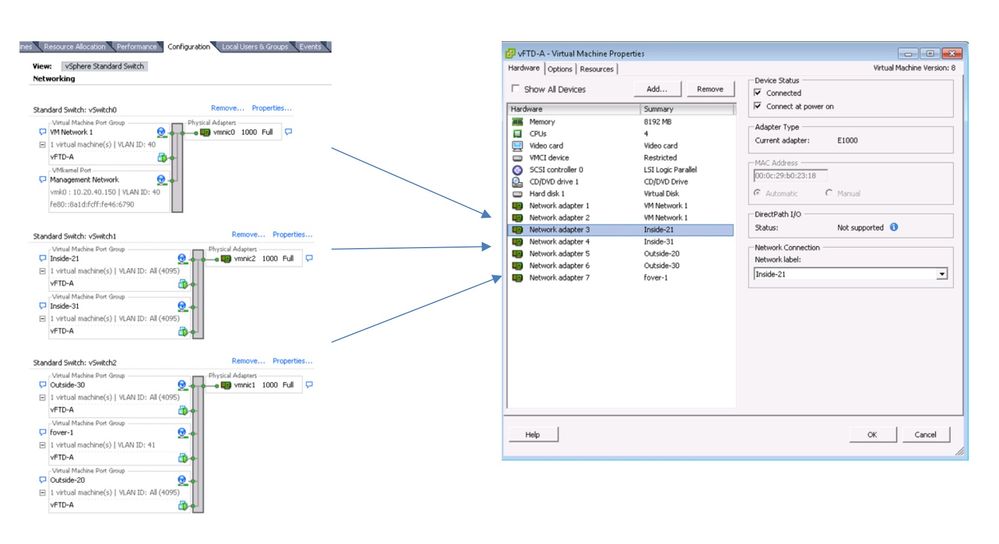
Vmware ESXi host Network Configuration
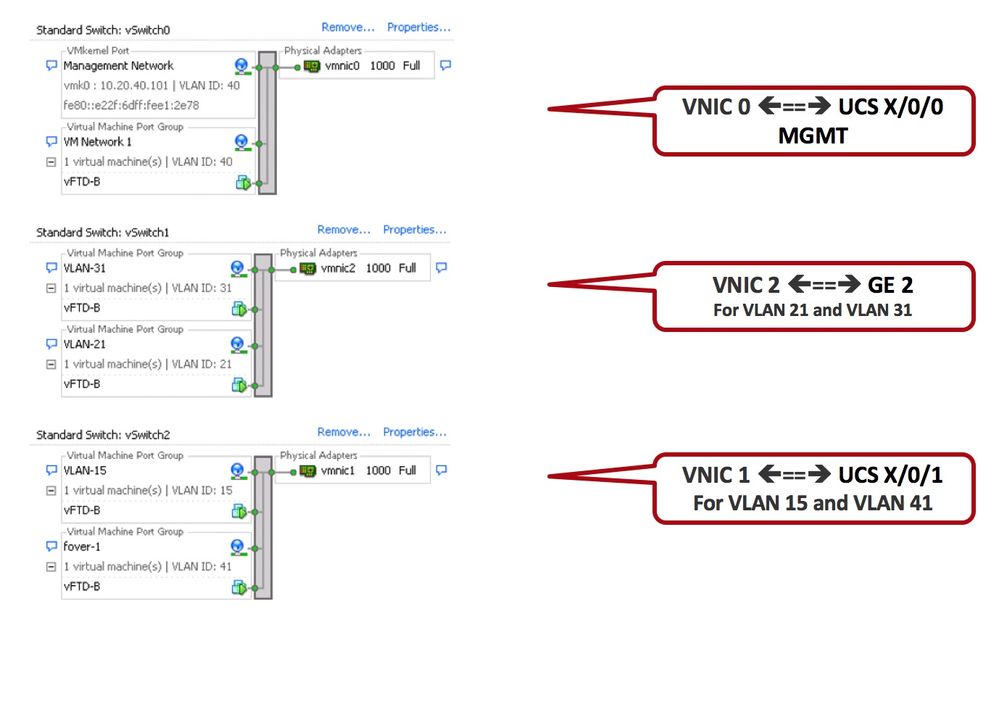
Note:
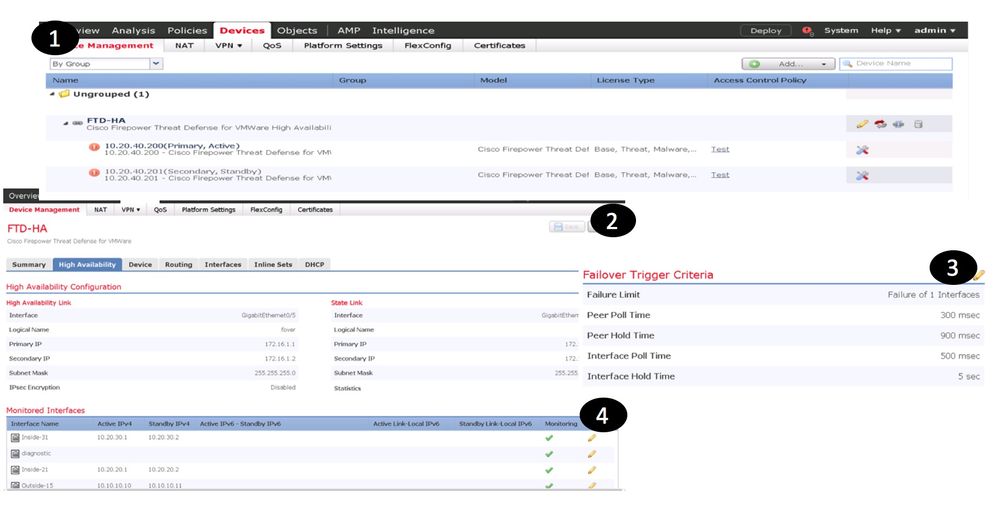
Configure the NGFWv High Availability between them through Firepower Management Center(FMC)
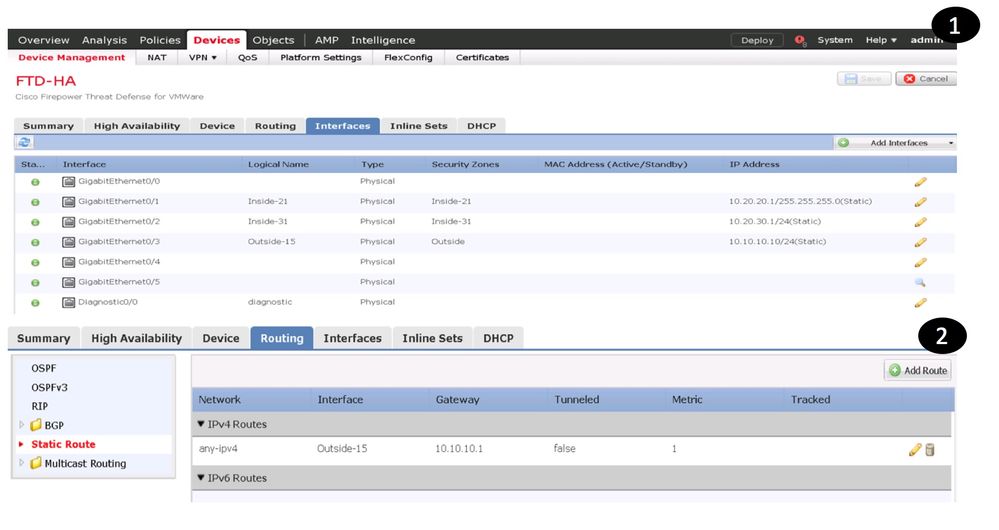
NGFWv Interface Configuration and Status
NGFWv HA Failover Function (External Link failure Testing)
NGFWv HA Failover Function (Internal Link failure Testing)
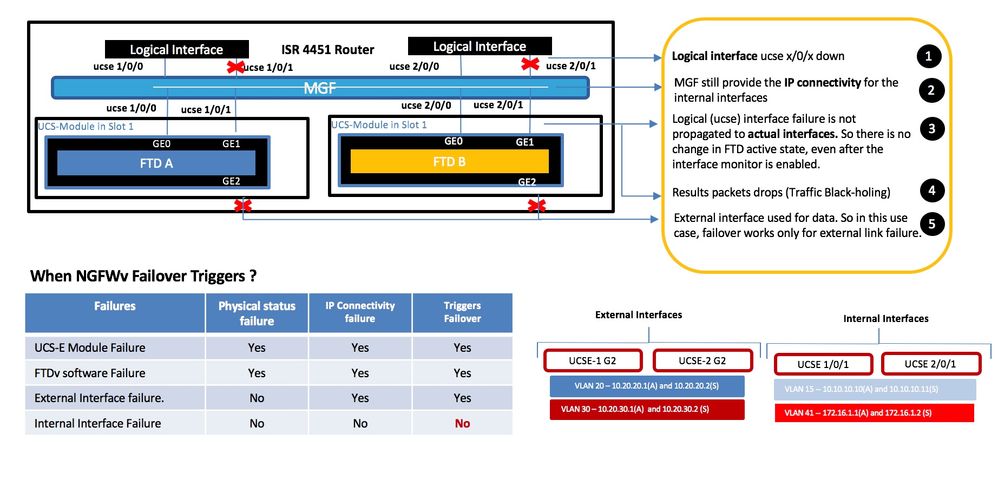
NGFWv HA failover not triggered during the internal interface failure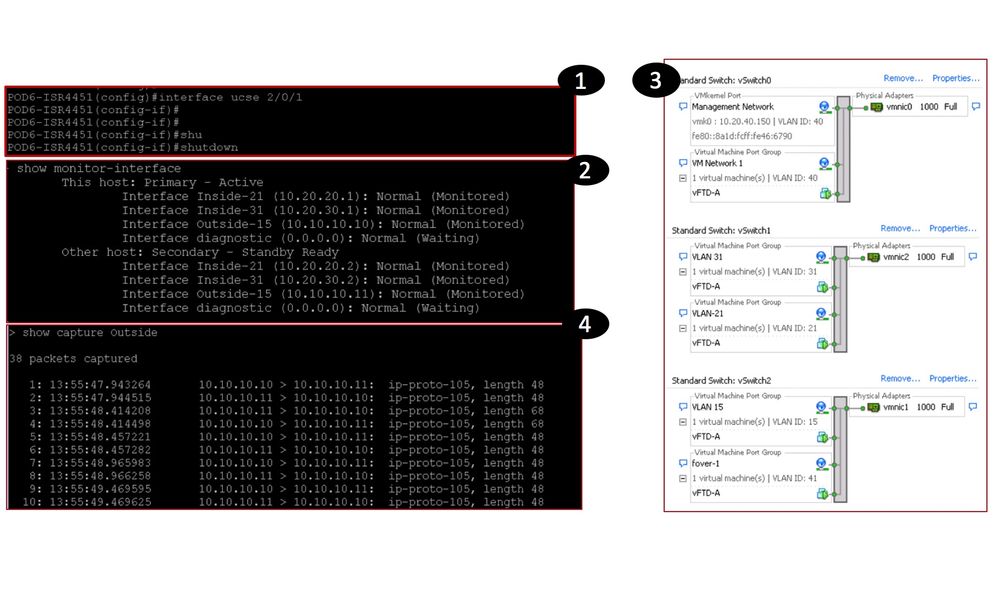
NGFWv HA Failover Function
When NGFWv Failover Triggers?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Kureli,
Wondering if Cisco has come with any solution for creating a HA between vNGFW running on 2 different ISR 4K boxes. Is there a work in progress by engineering team on this ??
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Kureli
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Kureli,
Can you please provide a link for configuring VRF on Firepower FTD running on Firepower 9300, thanks.
Umer
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Kureli,
What do the numbers in the "Supported ISR4K and UCS-E Blades" mean?
What do the * beside the numbers represent?
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello Kureli,
If I want to use ASAv instead of NGFW and want to do Site to Site VPN , will it be possible while BDI Interface is there at ISR ?
Can you advise ?
Subrun
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: