- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 10-22-2024 05:55 AM
Hairpinning on Cisco ASA Firewall
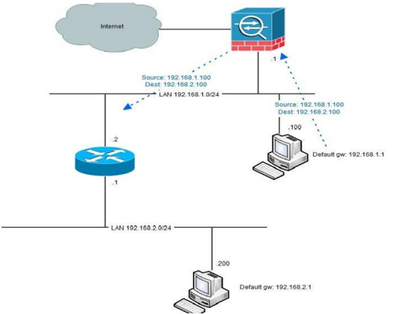
Hairpin Network Address Translation (NAT), also known as NAT loopback or NAT reflection, is a technique used in network routing whereby a device on a private network can access another device on the same private network via a public IP address.
This is used when a server is hosted behind a router, and you want to enable devices on the same local network as the server to access it using the public IP address (the one assigned to the router by the Internet Service Provider) just as an external device would.
The term hairpinning comes from the fact that the traffic comes from one source into a router or similar devices, makes a U-turn and goes back the same way it came. Visualize this and you see something that looks like a hairpin.
- Hairpinning is only relevant when the firewall is in routed mode since the “turnaround” of traffic is a routing decision. Also there needs to be another router involved.
- If the firewall is setup to only pass traffic between interfaces no hairpinning will be taking place.
- Typical hairpinning is done when there is a router inside of the firewall beyond which there is another network that needs to be reached to/from the inside network.
- Another fundament for hairpinning taking place is that not all network equipment has full knowledge of the network topology.
- Typically these are computers with only a default route (“default gateway”) to something but not aware of the fact that the remote network is reachable directly via the other router without taking the path via the firewall.
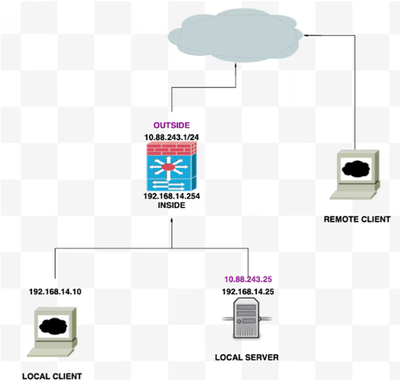
Lab Topology
Step 1. Create the Objects
- Internal network:192.168.14.10
- Web Server: 192.168.14.25
- Public Web Server: 10.88.243.25
- Port: 80
ciscoasa(config)# object network Local_Client
ciscoasa(config-network-object)# host 192.168.14.10
ciscoasa(config)# object network Web_Server
ciscoasa(config-network-object)# host 192.168.14.25
ciscoasa(config)# object network P_Web_Server
ciscoasa(config-network-object)# host 10.88.243.25
ciscoasa(config)# object service HTTP
ciscoasa(config-service-object)# service tcp destination eq 80
Step 2. Create the NAT
ciscoasa(config-service-object)# nat (Inside,Inside) source dynamic Local_Client interface destination static P_Web_Server Web_Server service HTTP HTTP
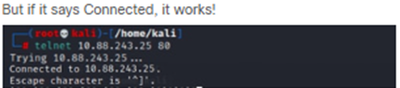
Verify
From the local client do a telnet destination IP with de destination port:
Thank you very much..!!