- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- How to configure Site-to-Site VPN with Hairpinning on Cisco ASA Firewall.
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 01-18-2016 05:56 PM
Objective:
Traffic between Branch 1 and Branch 2 should be able to talk across the existing IPSec VPN on headquarters ASA (HQ).
Concepts:
Hairpinning (U-turn Traffic): Hairpinning is a term to describe traffic that is routed out of the same interface from which it entered.
Requirements:
Cisco ASA firewall running 8.3 code or above.
Topology:
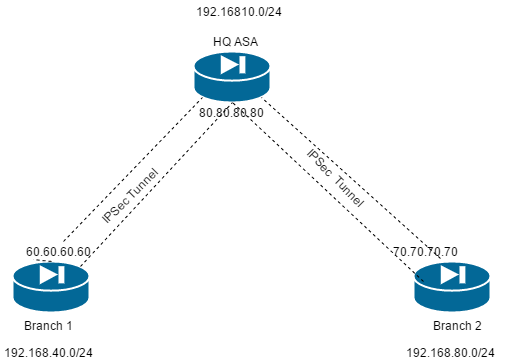
Configuration Steps:
Configure a standard IPSec VPN between Branch 1 and HQ and Branch 2 and HQ.
HQ ASA Configuration
------------------ Configure required network objects ------------------
Object-group network Local-HQ-Network
network-object 192.168.10.0 255.255.255.0
Object-group network Branch1-networks
network-object 192.168.40.0 255.255.255.0
Object-group network Branch2-networks
network-object 192.168.80.0 255.255.255.0
------------------ Configure the NO-NAT rules for the interesting traffic ------------------
NAT (inside,outside) 1 source static Local-HQ-Network Local-HQ-Network destination static Branch1-networks Branch1-networks route-lookup
NAT(inside,outside) 2 source static Local-HQ-Network Local-HQ-Network destination static Branch2-networks Branch2-networks route-lookup
------------------ Configure the ACL for the Interesting Traffic ------------------
Access-list VPN-to-Branch1 permit ip object-group Local-HQ-Network object-group Branch1-networks
Access-list VPN-to-Branch2 permit ip object-group Local-HQ-Network object-group Branch2-networks
------------------Configure the Site-to-Site VPN ------------------
Crypto ikev1 policy 1
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
crypto ikev1 enable outside
Crypto ipsec ikev1 transform-set Cisco esp-aes-256 esp-sha-hmac
Crypto map IPSec_VPN 1 match address VPN-to-Branch1
Crypto map IPSec_VPN 1 set peer 60.60.60.60
Crypto map IPSec_VPN 1 set ikev1 transform-set Cisco
Crypto map IPSec_VPN 2 match address VPN-to-Branch2
Crypto map IPSec_VPN 2 set peer 70.70.70.70
Crypto map IPSec_VPN 2 set ikev1 transform-set Cisco
Crypto map IPSec_VPN enable outside
tunnel-group 60.60.60.60 type ipsec-l2l
tunnel-group 60.60.60.60 ipsec-attributes
ikev1 pre-shared key My_$3cr#t
tunnel-group 70.70.70.70 type ipsec-l2l
tunnel-group 70.70.70.70 ipsec-attributes
ikev1 pre-shared key My_$3cr#t
/////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////
Branch 1 ASA Configuration
------------------ Configure required network objects ------------------
Object-group network Local-HQ-Network
network-object 192.168.10.0 255.255.255.0
Object-group network Branch1-networks
network-object 192.168.40.0 255.255.255.0
------------------ Configure the NO-NAT rule for the interesting traffic ------------------
Nat (inside,outside) 1 source static Branch1-networks Branch1-networks destination static Local-HQ-Network Local-HQ-Network route-lookup
------------------ Configure the ACL for the Interesting Traffic ------------------
Access-list Branch-to-HQ permit ip object-group Branch1-networks object-group Local-HQ-Network
------------------ Configure the Site-to-Site VPN ------------------
Crypto ikev1 policy 1
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
crypto ikev1 enable outside
Crypto ipsec ikev1 transform-set Cisco esp-aes-256 esp-sha-hmac
Crypto map IPSec_VPN 1 match address Branch-to-HQ
Crypto map IPSec_VPN 1 set peer 80.80.80.80
Crypto map IPSec_VPN 1 set ikev1 transform-set Cisco
Crypto map IPSec_VPN enable outside
tunnel-group 80.80.80.80 type ipsec-l2l
tunnel-group 80.80.80.80 ipsec-attributes
ikev1 pre-shared key My_$3cr#t
/////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////
Branch 2 Configuration
------------------ Configure required network objects ------------------
Object-group network Local-HQ-Network
network-object 192.168.10.0 255.255.255.0
Object-group network Branch2-networks
network-object 192.168.80.0 255.255.255.0
------------------ Configure the No-NAT rule for the interesting traffic ------------------
Nat (inside,outside) 1 source static Branch2-networks Branch2-networks destination static Local-HQ-Network Local-HQ-Network route-lookup
------------------ Configure the ACL for the Interesting Traffic ------------------
Access-list Branch-to-HQ permit ip object-group Branch2-networks object-group Local-HQ-Network
------------------ Configure the Site-to-Site VPN ------------------
Crypto ikev1 policy 1
authentication pre-share
encryption aes-256
hash sha
group 5
lifetime 86400
crypto ikev1 enable outside
Crypto ipsec ikev1 transform-set Cisco esp-aes-256 esp-sha-hmac
Crypto map IPSec_VPN 1 match address Branch-to-HQ
Crypto map IPSec_VPN 1 set peer 80.80.80.80
Crypto map IPSec_VPN 1 set ikev1 transform-set Cisco
Crypto map IPSec_VPN enable outside
tunnel-group 80.80.80.80 type ipsec-l2l
tunnel-group 80.80.80.80 ipsec-attributes
ikev1 pre-shared key My_$3cr#t
/////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////
/////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////
Configure the Hairpining (U Turn) on HQ ASA.
------------------ Turn on hairpining ------------------
same-security-traffic permit intra-interface
------------ Add the subnet from Branch 2 to the crypto map for Branch 1 -------------
Access-list VPN-to-Branch1 permit ip object-group Branch1-networks object-group Branch2-networks
------------ Add the subnet from Branch 1 to the crypto map for Branch 2 -------------
Access-list VPN-to-Branch2 permit ip object-group Branch2-networks object-group Branch1-networks
--- Outside NAT to avoid the VPN traffic to be translated to the device public IP ----
NAT (outside,outside) source static Branch1-networks Branch1-networks destination static Branch2-networks Branch2-networks route-lookup
------------ Allow the traffic on the Outside ACL ------------
access-list outside-access-in permit ip 192.168.40.0 255.255.255.0 192.168.80.0 255.255.255.0
access-list outside-access-in permit ip 192.168.80.0 255.255.255.0 192.168.40.0 255.255.255.0
access-group outside-access-in in
/////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////
Branch 1 ASA Modifications.
------------ Configure a network objects for Branch 2 networks ------------
Object-group network Branch2-networks
network-object 192.168.80.0 255.255.255.0
------------ Add the NO-NAT for the VPN traffic to the Branch 2 network ------------
Nat (inside,outside) 1 source static Branch1-networks Branch1-networks destination static Branch2-networks Branch2-networks route-lookup
------------ Include the branch 2 networks , into the existing interesting traffic ------------
Access-list Branch-to-HQ permit ip object-group Branch1-networks object-group Branch2-networks
/////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////////
Branch 2 ASA Modifications.
------------ Configure a network object for the Branch 1 networks ------------
Object-group network Branch1-networks
network-object 192.168.40.0 255.255.255.0
------------ Add the NO-NAT for the VPN traffic for Branch 1 network ------------
Nat (inside,outside) 1 source static Branch2-networks Branch2-networks destination static Branch1-networks Branch1-networks route-lookup
------------ Include the branch 1 network, into the existing interesting traffic ------------
Access-list Branch-to-HQ permit ip object-group Branch2-networks object-group Branch1-networks
You might also see:
Hope it helps
-Randy-
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Randy,
What a nice how-to, Randy. I really appreciate it. It looks like this is exactly what I needed for one of the implementations I work on.
Thank you!
Best regards,
Jaro
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Shoudn't these ACL be otherway around ? Because traffic from Branch 2 to HQ to Branch1 to will have Branch 2 as source and Branch 1 as destination in crypto of HQ for VPN to branch 1. Please correct me if i am wrong.
------------ Add the subnet from Branch 2 to the crypto map for Branch 1 -------------
Access-list VPN-to-Branch1 permit ip object-group Branch1-networks object-group Branch2-networks
Access-list VPN-to-Branch1 permit ip object-group Branch2-networks object-group Branch1-networks
same goes below
------------ Add the subnet from Branch 1 to the crypto map for Branch 2 -------------
Access-list VPN-to-Branch2 permit ip object-group Branch2-networks object-group Branch1-networks
Access-list VPN-to-Branch2 permit ip object-group Branch1-networks object-group Branch2-networks
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: