Introduction
This document describe how VPN client or anyconnect client can send both Intranet and Internet traffic via VPN tunnel.
home users(VPN Clients) ------ internet ------ ASA 5510----- CORP LAN
Components Used
- ASA with 7.X (For VPN Client) or above and 8.X (For Anyconnect) or Above
- VPN or Anyconnect Client
Network Diagram
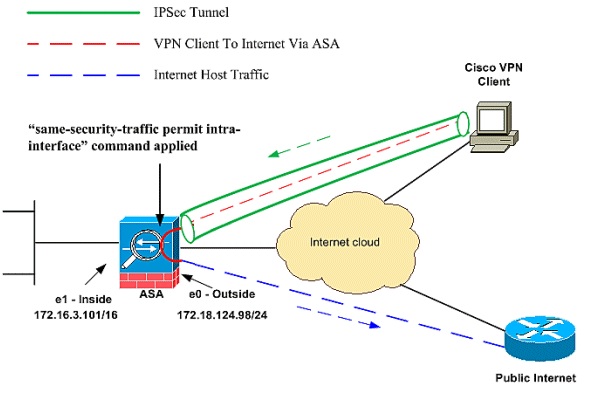
In the above diagram-----
- E0 is the outside interface
- E1 is the inside interface
- Pool subnet is 10.197.126.0
Configure
We need to keep few things in mind to configure this----
- In group-policy add split tunnel to tunnel all
- Configure NAT( For client Pool) on the outside interface to PAT to the same global address
- Configure "same-security-traffic permit intra-interface" so traffic from the VPN tunnel destined for the Internet can make a u-turn.
Configuration of PIX/ASA
interface Ethernet1
speed 100
duplex full
nameif inside
security-level 100
ip address 172.16.3.101 255.255.0.0
interface Ethernet0
nameif outside
security-level 0
ip address 172.18.124.98 255.255.255.0
same-security-traffic permit intra-interface
object-group network trusted_inside
network-object 172.16.0.0 255.255.0.0
object-group network APAC_IS_VPN_Networks
network-object 10.197.126.0 255.255.255.0
access-list VPN_ACL_NONAT extended permit ip object-group trusted_inside object-group APAC_IS_VPN_Networks
global (outside) 2 172.18.124.100 netmask 255.255.255.0
nat (inside) 0 access-list VPN_ACL_NONAT
nat (inside) 2 10.197.0.0 255.255.0.0
nat (outside) 2 10.197.126.0 255.255.255.0
route outside 0.0.0.0 0.0.0.0 172.18.124.99
route inside 172.16.0.0 255.255.0.0 172.16.3.102
webvpn
enable outside
anyconnect-essentials
svc image disk0:/anyconnect-win-2.5.1025-k9.pkg 1
svc image disk0:/anyconnect-macosx-i386-2.5.1025-k9.pkg 2
svc image disk0:/anyconnect-linux-2.5.1025-k9.pkg 3
svc profiles MSTRRemAccess2011 disk0:/MSTRRemAccess2011.xml
svc enable
tunnel-group-list enable
group-policy Test-AnyconnectPolicy internal
group-policy Test-AnyconnectPolicy attributes
split-tunnel-policy tunnelall
wins-server value X.X.X.X Y.Y.Y.Y
dns-server value X.X.X.X Y.Y.Y.Y
vpn-tunnel-protocol IPSec svc webvpn
split-tunnel-policy tunnelspecified
default-domain value xxx.com
split-dns value corp.xxx.com xxx.com labs.xxx.com
webvpn
svc dtls enable
svc keep-installer installed
svc keepalive 60
svc dpd-interval client 120
svc dpd-interval gateway 120
svc modules value vpngina
svc profiles value MSTRRemAccess2011
svc ask enable
tunnel-group Test_AnyConnect type remote-access
tunnel-group Test_AnyConnect general-attributes
authentication-server-group LOCAL-ACS
default-group-policy Test-AnyconnectPolicy
tunnel-group Test_AnyConnect webvpn-attributes
group-alias Test_Group enable
Hope this was informative and I want to thank you for your time.
Related Information
https://supportforums.cisco.com/thread/2087621?tstart=0
http://www.cisco.com/en/US/products/ps6120/products_configuration_example09186a0080972e4f.shtml?