- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- How to Integrate Cisco Identity Services Engine with IBM MaaS360 (MDM)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
05-29-2020 12:45 AM - edited 05-30-2020 02:08 AM
- Introduction
- Components
- IBM MaaS360 Configuration
- ISE Configuration
- Onboard and validating access from Windows Client
- Enrolling Windows 10 against IBM MaaS 360
Introduction
Cisco Identity Services Engine (ISE) gives you intelligent Integrated protection through intent-based policy and compliance solution. ISE supports external MDM vendor integration to help the customers to look for compliance of a devices being managed by MDM vendors like AirWatch, MobileIron, Microsoft Intune, JAMF Software, IBM MasS360 etc... Look at ISE ISE compatibility guide for the supported MDM vendors. This guide will help you to integrate IBM MaaS 360 with Cisco Identity service Engine in order to give definite access privileges of your endpoints managed by IBM Maas 360 based on compliance of your organization looking for.
Components
- Cisco Identity Services Engine (ISE)
- IBM MaaS360
IBM MaaS360 Configuration
IBM MaaS360 allows you to manage your mobile devices as well as Laptops/desktop device management. Below configuration would give provide an overview on how to configure your IBM MaaS 360 to enroll laptops and desktops management and give access to Windows devices.
- Login to MaaS360 and navigate to SETUP > Services. By default, “Laptop and Desktop Management” will not be enabled. Please enable to avail this service to manage Laptops and desktop in your organization.
- In background, IBM MaaS 360 will automatically create an MDM policy called “Default Windows MDM” for windows devices management.
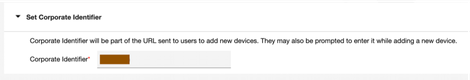
- Change the corporate identifier (optional). Navigate to Setup > Settings > Device Enrollment Settings > Basic > Set Corporate Identifier. Change the default corporate identifier to suit your organization.
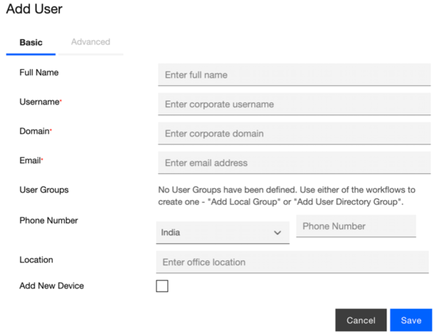
- Go to Users > Directory to add the local users. We will be using this user details to enroll the windows 10 device in later section. Provide Full Name, username, domain, email and other details. Click on “Save” to save the configuration.
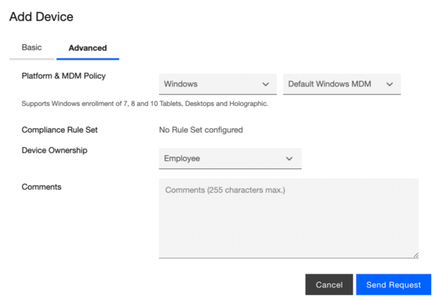
- Go to “Advanced” tab to add the device under this user. Choose “Windows” as the platform and default MDM policy which would have been already created during 2nd step above. Choose Device Ownership as “Employee”, “Personal”, “Corporate” as per your windows 10 devices being on-boarded with user created above.
- Click on “Send Request” to submit the request and get the MDM onboarding details.
- User will be notified with an email about the Mail address provided, URL and Passcode for onboarding windows 10 device. Optionally, you can use QR Code for enrollment too.
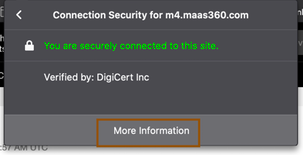
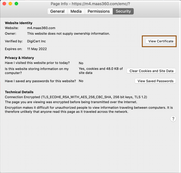
- In order to communicate to external MDM server, ISE has to trust the external MDM server certificate. Access https://login.maas360.com (IBM MaaS360 cloud service offers different cloud server based on your location. Based on APAC region, IBM MaaS360 gives me service from this server and hence I am using this) and try to export the certificate chain from the certificate offered by the above portal.
- Open the portal in browser and click on certificate and click on “More information”.
- download certificate chain of this portal to your desktop.
ISE Configuration
- Login to the ISE UI using the admin credentials that were created during setup.
- Ensure you have Apex license as MDM service requires Apex license.
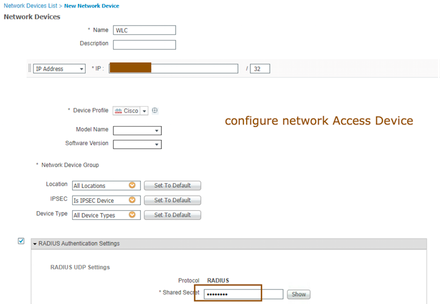
- A network device has to be configured initially to honor the RADIUS requests from WLC. Navigate to Administration > Network Resources> Network Devices and configure WLC with shared secret. Provide Name of the WLC in ISE reference purpose, provide IP address and shared secret (shared secret should be same in WLC too) then submit the configuration.
- If your environment requires proxy to reach internet, please configure proxy server.
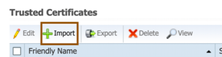
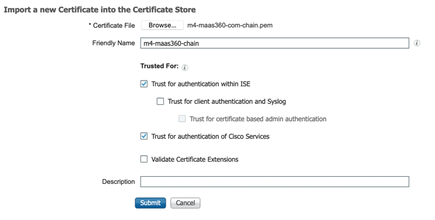
- Come back to ISE and navigate to Administration > system > Certificates > Trusted Certificates and click on Import to MaaS360 chain that was downloaded in earlier step.
- Browse for imported certificate in earlier section, provide friendly name and ensure to check “Trust for authentication of Cisco Services”. Click on submit to add the chain to ISE trusted certificates. (accept any warnings/notifications that ISE was notifying)
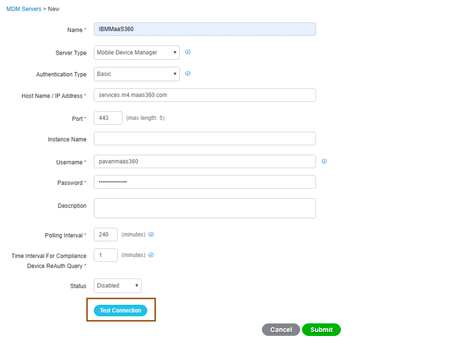
- Now that we have ensured that ISE could reach external MDM server through proxy and trust external MDM server, now it’s time to configure MDM server on ISE. Navigate to Administration > Network Resources > External MDM, click on “ADD” to configure an MDM server.
- Please configure appropriate details like Server type, authentication type, hostname .. Enter the credentials under username and password field.
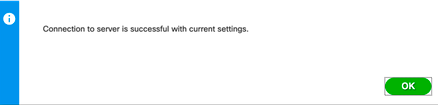
- Click on “Test Connection” to test the connection whether ISE is able to communicate to IBM MaaS360 properly or not. Ensure you are getting below message.
- Ensure to select Enable from the dropdown list available under status and click on submit to save the configuration.
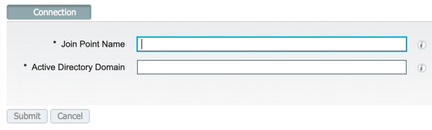
- In my case, users are being managed with the help of active directory so let’s configure active directory now. Navigate to Administration > Identity management > External Identity Sources > Active Directory and click on add to add an active directory. Provide join point name in ISE for reference and actual domain name and provide credentials to join ISE to the domain.
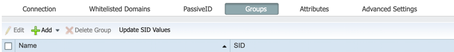
- Once ISE is successfully joined to the domain controller, navigate to Groups tab to fetch the groups in which users belong to
- Select groups from the AD and select the groups that you want to write the policies on
- Import the groups to ISE and save the configuration.
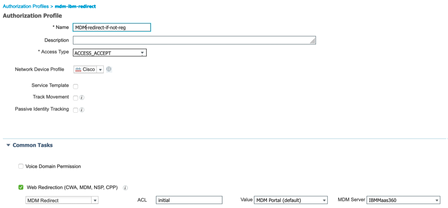
- Now that we have successfully configured IBM MaaS360 MDM server, we will create an authorization profile. Navigate to Policy > Policy Elements > Results > Authorization > Authorization profiles, click on Add to create an authorization profile. Provide name of the authorization profile and provide web-redirection details as shown below.
NOTE: “Initial” is the ACL configured in Wireless Lan controller which will allow necessary privileges for the user to onboard the device against IBM Maas360 in case if not enrolled already. - Navigate to Policy > Policy Sets > Default and click on “>” to configure default policy set.
- Leave the authentication policies as is.
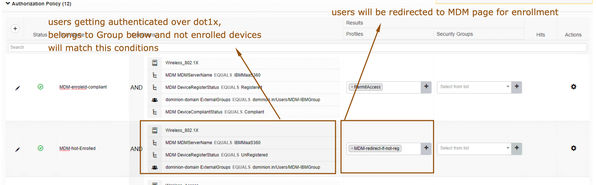
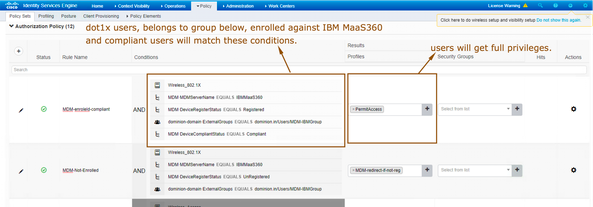
- Configure an authorization policy like below.
- One authorization policy for the users to redirect to MDM server who haven’t enrolled their devices against IBM MaaS360.
- One authorization policy for the users to get full network privileges who have enrolled and compliant against IBM MaaS360 MDM server.
- One authorization policy for the users to redirect to MDM server who haven’t enrolled their devices against IBM MaaS360.
Troubleshooting
Connection from ISE to MDM server issues: If the connection from ISE to MDM server isn’t successful, you will have to check for
- the certificates available in trusted store of ISE
- check for connectivity or proxy details whether it is allowing ISE to communicate to MDM server or not.
- basic authentication is allowed under IBM MaaS360 portal
Onboard and validating access from Windows Client
- Authenticate against ISE using the user trying to onboard.
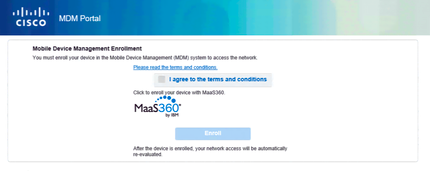
- If the user hasn’t enrolled the device, users are supposed to be redirected to MDM server like below.
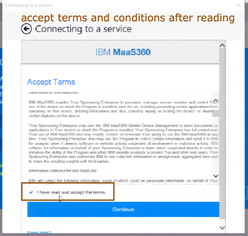
- Agree terms and conditions and click on enroll. (you must ensure users should be able to enroll their devices against IBM Maas 360 by providing privileges in the authorization profile that was created earlier)
- Sometimes, users are required to enroll their devices by following the procedure mentioned in “Enrolling windows 10 device against IBM MaaS360”.
- Once after successful enrollment, users should be able to get full privileges as per the authorization policy written earlier
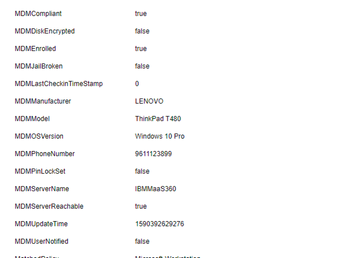
- Ensure MDM attributes are pulled properly and showing up in context visibility. Navigate to Context visibility > End Points > authentication and select the endpoint that was onboarded earlier.
Troubleshooting
- MDM server rules in authorization policy issues: In case ISE has multiple MDM servers configured, then you will have to ensure in each policy to use MDM:servername condition to differentiate the servers in ISE to check against.
- Getting full privileges after enrolling issues: once after successful enrollment, IBM MaaS360 application gets downloaded and install to sync the policies enforced on the device. If Maas 360 application isn’t installed after enrollment process, wait for few minutes so that app gets installed.
- ISE checks with the MAC address in Isle Royale for the enrollment/registration details of the endpoint. If the endpoint MAC address isn’t showing up under IBM MaaS360 “Device enrollment” device then application hasn’t synced it, or mac address might have been changed. Disable MAC randomization to check for the actual mac address.
- After redirection, if windows wasn't able to enroll through MDM page, then windows 10 devices will have to be enrolled against IBM MaaS 360 with connect to work or school. Refer to “Enrolling windows 10 device against IBM MaaS360” section.
Enrolling Windows 10 against IBM MaaS 360
Here is how you could enroll a windows device against IBM MaaS 360 which would be helpful offline/via policies written above.
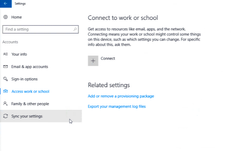
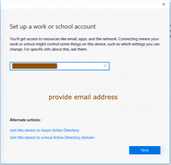
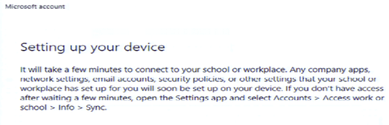
- Once after login to Windows 10 device, Go to Settings > Account > Access work or School > Connect to Work or School
- Click on “Connect”, Microsoft would ask end user to provide email address.
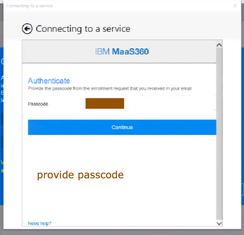
- If the discovery fails to find the domain, then Microsoft will ask you to provide the MDM URL along with email address provided earlier. Provide email address and MDM url that you got through IBM Maas360 device enrollment process and click on “Next”. Provide the Passcode that you got during enrollment process and click on “continue”, Accept “Terms and Conditions”.
- It will take few seconds for the enrollment process to be completed. You would be able to see below screen in your accounts page that you are successfully connected to your IBM Maas 360. Behind the scenes, IBM Maas 360 will also push the IBM Maas360 application to the endpoint for the managing the endpoint through the IBM Maas360 policies.
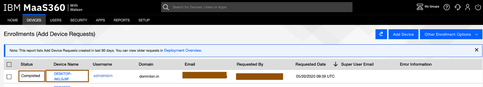
- As an administrator, you should be able to see enrolled device in your IBM MaaS360 Portal.
Troubleshooting
User’s enrollment process issues: users who haven’t enrolled their devices are supposed to be redirected to MDM page. If the user wasn’t able to enroll their device properly, then this requires multiple factors to look into such as
- make use of edge browser for enrolling purpose.
- Users’ privileges given in ACL configured in WLC
- Connectivity to MDM server from the end users.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: