- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Implemention of IPsec VPNs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on 06-12-2024 07:51 AM
IPsec VPN’s
Introduction
IPsec Protocols
IPsec Modes
Internet Key Exchange (IKE) protocol
IKE Phases: Phase-1 and Phase-2
IPsec VPN Configuraton
Conclusion
Introduction:
- The “IPSec” is a framework of open standard (IETF) and it is used for configuring “Secure VPN’s” over a third party network such as Internet to connect Branch Offices, Remote Users and Business Partners. The Secure Site-to-Site VPN’s between Central and Remote Sites can be implemented by using IPSec protocol. IPSec can also be used for remote-access tunnels for Telecommuter access. IPSec works at L3 (Network Layer) and operates over all L2 (Data-Link) protocols such as Ethernet, ATM, Frame-Relay, SDLC, HDLC, etc.
- IPsec (Internet Protocol Security) is a framework that helps us to protect IP traffic on the network layer, As because the IP protocol itself doesn’t have any security features at all. IPsec can protect our traffic with the following features: Confidentiality, Integrity, Authentication, Anti-replay
- IPSec can be used to protecting data flows between a pair of hosts (Host-to-Host), between pair of security gateways (Network-to-Network) or between security gateway and host (Network-to-Host).
- IPSec has a Plain-text Layer-3 header, so there are no issues with Routing.
IPsec Protocols:
- There are two main IPSec framework protocols:
- Authentication Header (AH)
- Runs over IP protocol number 51.
- It only provides authentication, so this wouldn’t be ideal, where we are taking confidentiality into consideration.
- Encapsulation Security Payload (ESP)
- Runs over IP protocol number 50.
- ESP also has the capability of optionally providing authentication and it adds confidentiality through the use of encryption.
- ESP supports several different types of symmetric encryption algorithms, including: DES, 3DES and AES.
- The common authentication methods in VPNs are pre-shared keys (small and medium-sized organizations) and digital certificates with the use of Public Key Infrastructure (PKI) (Several Large Organizations).
- ESP includes Header and trailer fields to support the encryption and optional authentication.
- Authentication Header (AH)
IPsec Modes: AH and ESP can be applied to IP packets in two different modes:
- Transport Mode: In transport mode security is provided only for the Transport Layer of the OSI model and above (Good for Host-to-Host). Transport Mode protects payload of the packet and leaves the original IP Header in plain text.
- Tunnel Mode: Tunnel Mode provides security for the complete Original IP Packet (Good for Network-to-Network/Host). The Original IP packet is encrypted and then it is encapsulated in another IP packet. This is also known as “IP-IN-IP Encryption”.
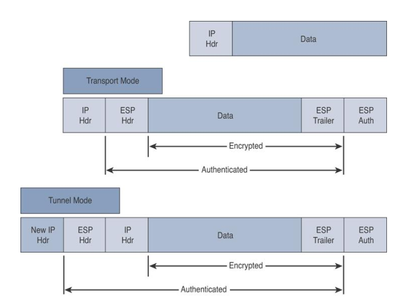
Internet Key Exchange (IKE):
- The IPSec VPN solution negotiates Key exchange parameters, establishes shared secret key, authenticates peer and negotiates Encryption parameters.
- The Negotiation of Security parameters between two devices known as a Security Association. A Security Association (SA) is SIMPLEX (one-way communication channel) and logical connection which endorse and provides a secure connection between network devices.
- IPSec uses the Internet Key Exchange (IKE) protocol to establish the key exchange process. Which means IKE/IKEv2 is a protocol used to setup a Security Association (SA) in the IPSec protocol.
- Instead of transmitting keys directly across the network, IKE calculates shared secret keys based on the Exchange of series of data packets.
- IKE is Layered up on UDP and uses port number 500.
- IKE is Hybrid Protocol combining: ISAKMP & OAKLAY. ISAKMP stands for Internet Security Association Key Management Protocol
IKE Phases:
- To establish secure communication channel between two peers, the IKE protocol executes two phases:
- IKE Phase -1
- IKE Phase -2
IKE Phase-1
- An IKE session begins with a Router(Initiator) sending a proposal to another Router(Responder)
- In IKE Phase-1, two IPSec peers perform initial negotiation of SA’s, which includes: Negotiation of IKE Policy Set, Authenticates peer and setup secure channel between peers.
- There are five parameters that must coordinate during IKE Phase-1 (HAGLE)
- HASH – MD5/SHA
- AUTHENTICATION – PSK/RSA SIGNATURE
- GROUP – DH1/DH2/DH3….. (DH14 or above is recommended)
- LIFE TIME – IKE TUNNEL LIFE TIME (TIME/BYTES COUNT)
- ENCRYPTION – DES/3DES/AES
- Negotiation of IKE Policy Set can be implemented in either one of the mode:
- MAIN MODE
- Default Mode
- Three Exchanges with 6 packets
- Main mode provides identity protection if pre-shared keys are used
- AGGRESSIVE MODE
- Faster than Main Mode
- One Exchange with 3 packets
- Aggressive mode offers identity protection only if digital certificates are employed.
Note: Cisco products that support IKEv1 typically use main mode for site-to-site tunnels and use aggressive mode for remote-access VPN tunnels. This is the default behavior when pre-shared keys are employed as the authentication method.
- Once the IKE Phase-1 tunnel is established, that is not going to used for forwarding user packets. Instead, it only used for forwarding management traffic like VPN configuration information.
IKE Phase-2
- Once IKE Phase-1 is established, router immediately begins IKE Phase-2, which is also referred as “IPSec Tunnel”. The main purpose of IKE Phase-2 is to negotiate the IP Security Parameters that will be used to secure IPSec Tunnel.
- SA’s are negotiated by the IKE process on behalf of IPSec. It (IPSec Policy Set / IPSec Transform Set) can be negotiated in Quick Mode. Hence, IKE Phase-2 also called as “QUICK MODE”
- Transform Set:- Transform Set is a Group of Policies that the routers establishing the VPN need to agree on.
- There are Five Parameters must coordinate during Quick Mode:
- IPSec Protocol – AH/ESP
- IPSec Encryption – DES/3DES/AES
- IPSec Authentication – MD5/SHA1
- IPSec Mode – Tunnel/Transport
- IPSec Life Time -- Seconds
- In addition to generating the keying material, quick mode also negotiates identity information. The Phase 2 identity information specifies which network, protocol, and/or port number to encrypt. Hence, the identities can vary anywhere from an entire network to a single host address, allowing a specific protocol and port.
IPsec VPN Configuration:
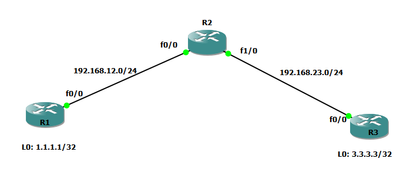
All routers are configured with ip addressing and Eigrp-100 as routing protocol. We can ping from R1 Loopback to R3 Loopback.
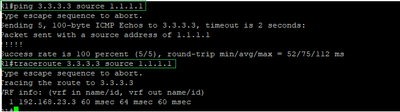
R1# ping 3.3.3.3 source 1.1.1.1
R1# traceroute 3.3.3.3 source 1.1.1.1
we can see the communication and traffic is going through R2 (R1 to R2 to R3).
Steps to configure IPSec VPN Tunnel
- Create IKE(ISAKMP) Policy Set
- Configure Pre-Shared-Key(PSK)
- Configure IPSec Transform Set
- Configure Crypto Map
- Apply Crypto Map to the Interface
R1 configuration
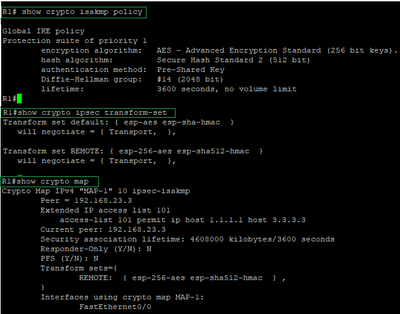
R1(config)#crypto isakmp policy 1
R1(config-isakmp)#hash sha512
R1(config-isakmp)#authentication pre-share
R1(config-isakmp)#group 14
R1(config-isakmp)#lifetime 3600
R1(config-isakmp)#encryption aes 256
R1(config-isakmp)#exit
R1(config)#crypto isakmp key 6 xxxxxxxx address 192.168.23.3
R1(config)#Crypto ipsec transform-set REMOTE esp-aes 256 esp-sha512-hmac
R1(cfg-crypto-trans)#mode transport
R1(cfg-crypto-trans)#exit
R1(config)# access-list 101 permit ip host 1.1.1.1 host 3.3.3.3 log
R1(config)#crypto map MAP-1 10 ipsec-isakmp
R1(config-crypto-map)#match address 101
R1(config-crypto-map)#set transform-set REMOTE
R1(config-crypto-map)#set peer 192.168.23.3
R1(config-crypto-map)#exit
R1(config)#Interface fa0/0
R1(config-if)#crypto map MAP-1
R2 Configuration
R2(config)#crypto isakmp policy 1
R2(config-isakmp)#hash sha512
R2(config-isakmp)#authentication pre-share
R2(config-isakmp)#group 14
R2(config-isakmp)#lifetime 3600
R2(config-isakmp)#encryption aes 256
R2(config-isakmp)#exit
R2(config)#crypto isakmp key 6 xxxxxxx address 192.168.12.1
R2(config)#Crypto ipsec transform-set REMOTE esp-aes 256 esp-sha512-hmac
R2(cfg-crypto-trans)#mode transport
R2(cfg-crypto-trans)#exit
R2(config)# access-list 101 permit ip host 3.3.3.3 host 1.1.1.1 log
R2(config)#crypto map MAP-1 10 ipsec-isakmp
R2(config-crypto-map)#match address 101
R2(config-crypto-map)#set transform-set REMOTE
R2(config-crypto-map)#set peer 192.168.12.1
R2(config-crypto-map)#exit
R2(config)#Interface fa0/0
R2(config-if)#crypto map MAP-1
Conclusion:
The original implementation of IPsec VPNs used on Cisco IOS was known as crypto maps. The concept of configuring a crypto map was closely aligned to the IPsec protocol, with traffic that was required to be encrypted being defined in an access control list.
This list was then referenced within an entry in the crypto map along with the IPsec cryptographic algorithms within the transform set. This configuration could become overly complex, and administrators introduced many errors when long access control lists were used.
Cisco IOS also has an alternative to crypto maps: tunnel interfaces with tunnel protection. This is accomplished by creating a logical interface that represents the source and destination endpoints of the tunnel. The tunnel interface connects the transport network and the overlay network (the traffic that will transverse within the tunnel).
Thank you very muich....!!
--------------------------------------------- THE END --------------------------
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Interesting and thank You for sharing!!!
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:

