Introduction
Certificates are small data files that digitally bind a cryptography key to an organization’s details. It allows creating a secure and trusted communication to the ASA or for authentication purposes for the VPN connections.
Requirements:
· ASA running 8.0 or up
· ASDM 7.2.x or up
What is a CSR?
Certificate signing request, is an encrypted text that is generated on the server that the certificate will be used. It includes information about your organization and the public key of the certificate.
Example of a CSR:
-----BEGIN CERTIFICATE REQUEST-----
MIIByjCCATMCAQAwgYkxCzAJBgNVBAYTAlVTMRMwEQYDVQQIEwpDYWxpZm9ybmlh
MRYwFAYDVQQHEw1Nb3VudGFpbiBWaWV3MRMwEQYDVQQKEwpHb29nbGUgSW5jMR8w
6iNh8f8z0ShGsFqjDgFHyF3o+lUyj+UC6H1QW7bn
-----END CERTIFICATE REQUEST-----
Components of the CSR
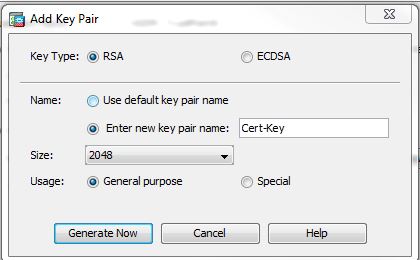
Key pair: On this case, refers to the ASA key that will be used on the CSR and later as the public key for the certificate.
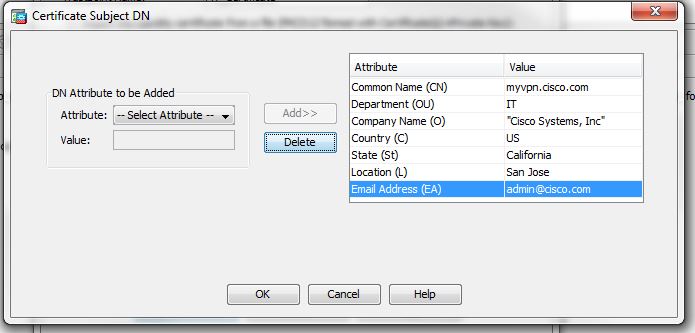
Certificate Subject DN (Distinguish name)
CN (common name) this is the way the certificate is associated with one or more hostnames, this determine which hostnames are covered by those certificates.
In case you're using Anyconnect this value must match the name on your VPN profile to avoid certificate warnings.
OU (organization unit): The department that handles the certificate examples IT , Accounting , etc.
Organization (O): The legal name of your organization, example Cisco Systems, etc
Country (C): Country where your organization is located.
State (ST): State where your organization is located
Location (L): Location where your organization is located.
Email Address (EA): an email address used to contact your organization.
Advanced options
FQDN(Fully qualified domain name )
Is the complete domain name for a specific computer, or host, on the Internet. The FQDN consists of two parts: the hostname and the domain name, example myasa.cisco.com
The SSL Certificate can only be used on this FQDN and nothing else - otherwise a name mismatch occurs. For example:
An SSL Certificate issued to www.yourdomain.com can only be used on www.yourdomain.com. It cannot be used on secure.yourdomain.com or even just yourdomain.com (with no sub domain). If you require a single SSL Certificate that can be used on multiple sub domains then you may want to consider a *wildcard certificate.
Creating the CSR
1. Go to ASDM -> Configuration-Remote -> Access VPN -> Certificate Management -> Identity certificates -> Add
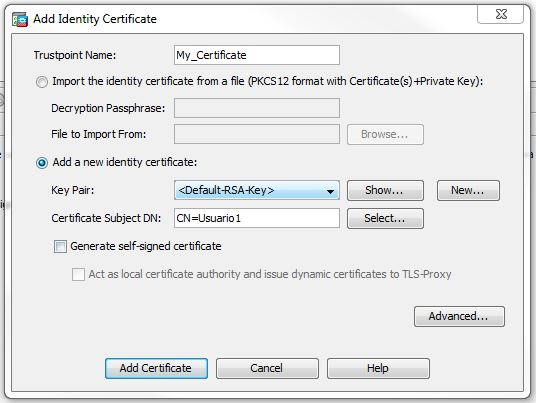
2. Create a new keypair or use the default keys.
3.Fill the certificates values.
4.Fill the FQDN value on the advanced options.
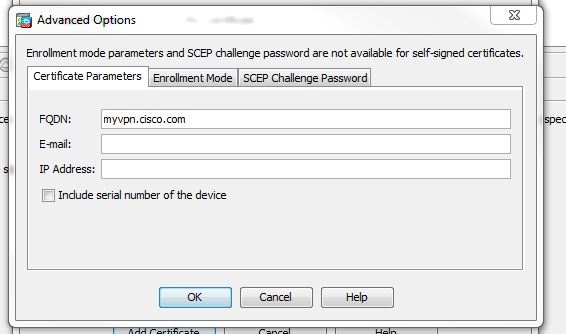
Is not recommended to include the SN of your device on the certificate, remember with your SN you can open TAC cases and have access to other Cisco services, certificates are a public and can be seen by everyone.
5.Create an save the CSR.
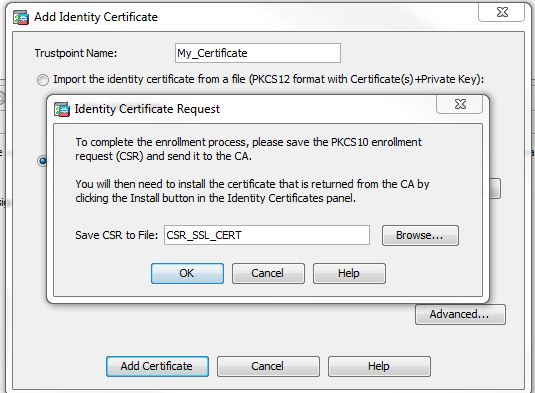
When we have our CSR created, go to the certificate authority to get your certificate, back on the ASA click on install to proceed with the installation of the certificate.
6.Apply the certificate to an interface if required.
Configuration > Device Management > Advanced > SSL Settings
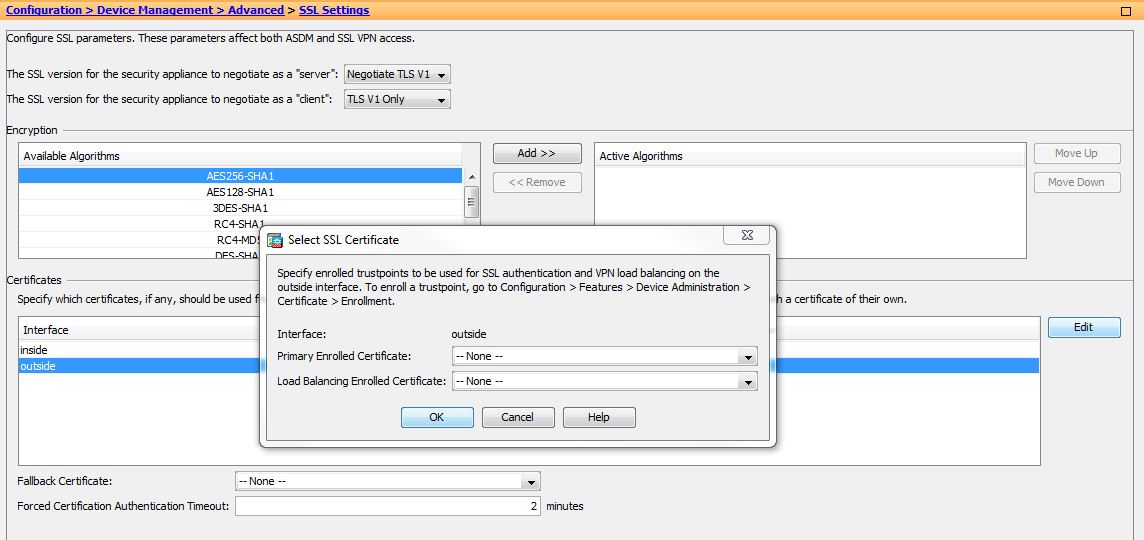
Equivalent CLI of the configuration.
ASA5520A(config)#crypto key generate rsa usage-keys label Cert-key modulus 2048 noconfirm
ASA5520A(config)#crypto ca trustpoint My_Certificate
ASA5520A(config-ca-trustpoint)#keypair Cert-Key
ASA5520A(config-ca-trustpoint)# fqdn myvpn.cisco.com
ASA5520A(config-ca-trustpoint)#subject-name CN=myvpn.cisco.com,OU=IT,O="Cisco Systems, Inc",C=US,St=California,L=San Jose,EA=admin@cisco.com
ASA5520A(config-ca-trustpoint)#enrollment terminal
ASA5520A(config)#crypto ca enroll My_Certificate noconfirm
ASA5520A(config)#crypto ca authenticate My_Certificate
ASA5520A(config)#ssl trustpoint outside My_Certificate
Verify the settings were applied.
ASA5520A# Show crypto ca certificates
ASA5520A# Show run ssl
How to generate a wildcard certificate.
Change the CN field on the CSR, for the subdomains you would like to include, example *.cisco.com will cover vpn.cisco.com, webvpn.cisco.com, etc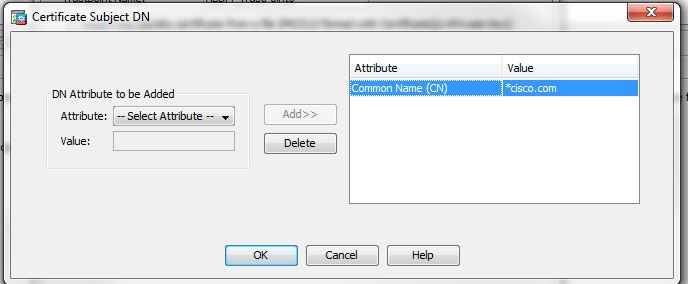
Install a certificate that is already created.
In order to install a certificate which CSR was not generated on the ASA , it needs to be in a pkcs12 format, this contains the private key and the certificate itself. You need to have the password generated when teh original certificate was exported.
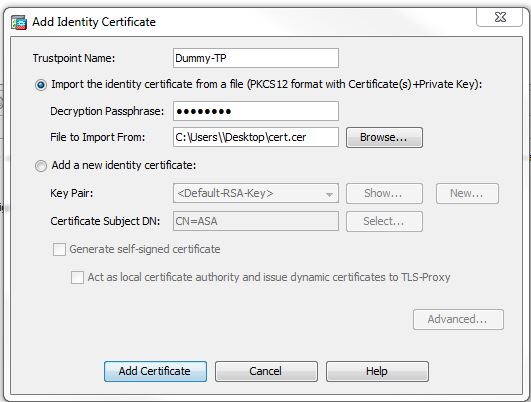
Equivalent CLI command:
ASA5520A(config)#crypto ca import dummy-TP pkcs12 cisco123
You may also check
https://supportforums.cisco.com/document/12466681/how-export-asa-identity-certificate-through-asdm
Hope it helps
- Randy -