- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ISE 2.3+ Remember Me guest using guest endpoint group logging display
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
on
11-15-2017
04:08 PM
- edited on
12-02-2019
11:34 AM
by
Jason Kunst
![]()
ISE 2.3 brings a new functionality that is very useful for troubleshooting and monitoring the Guest flow around Guest Remember Me functionality. Basically pointing a guest endpoint into an endpoint group and granting access for a set number of days until their endpoint is purged and have to go through Credentialed portal again. We are working on these in ISE 2.3-2.5 and hope to backport them as well as far back as we can. If you have any needs please bring up through the TAC for patching in prior releases and they will be evaluated if available.
Another option of remembering the guest is to use sleeping client feature on the WLC. This will pin up the wireless session so that a device keeps same authorization for a set period of time. For example. I connect to the network, login to the portal and get access. My device goes to sleep and then I unlock it again and connect as long as its within the timeout i don't need to be redirected again. The issue with this is memory is consumed and pinned up while these session are sleeping so you don't want to do with too many clients or for a long period of time. For more information reach out to the wireless team.
Associated defect for licensing:
CSCvp16734 - Plus Licenses Consumed without Plus Features
see post - ISE Guest flow with guest user type license required
Background
In the case of Guest Access on Wired or wireless. if the Network Access Device doesn't already have a session for that user's MAC address, then the WLC sends the client's MAC address to ISE and two possible scenarios exist
- If ISE doesn't recognise this MAC address in a 'Guest' Identity Group, then redirect user to the Guest Portal. If Login was successful then MAC address is added to the appropriate Guest Identity Group.
- If ISE recognises the MAC address in a 'Guest' Identity Group then the Authorization happens accordingly and no Portal is presented. This is the so-called "Remember Me" feature.
The problem with scenario 2 is that ISE didn't correlate the user's username that was used during Portal login with the MAC address. This results in a few issues, please reach out to the ISE Product Managers at http://cs.co/ise-feedback or http://cs.co/ise-pm (for cisco employees only) to request this be addressed:
- Radius Access-Accept to the NAD is the MAC address. Makes like difficult for monitoring clients on the WLC - all you'll see is a MAC address with no relation to the user identity
- CSCvh04231 & CSCva66612 Enhancement for future, please reach out to our Product Managers via - http://cs.co/ise-feedback Guest remember me radius accounting and access accept not sending guest username
- CSCvm77990 - Certain RADIUS attribute direction is not RFC2865 compliant
- CSCvm46971 - Allow admin to select RADIUS:Username attribute to send back
Solution
The current solution addressed guest and internal user accounts. It does not address other identity stores.
Also if you were to redirect a flow to the hotspot portal then the reporting will no longer work, for example - ISE Guest Flow with Multiple Endpoint Identities
Recommended release is ISE 2.4
- ISE 2.3 the identity in the live logs is rewritten with the guest username. There is no way to revert back to prior behavior
- CSCvj29117 - ISE Guest Remember Me flow live logs should show guest username as identity
- ISE 2.4 Live sessions is also rewritten: CSCvh05703 - remember me radius live sessions view does not show the guest username. This is the default behavior with fresh install but on upgrade you will need to enable it. The setting to enable this is under Work Centers > Guest Access > Settings > Logging
- Fixed in 2.4 and 2.6 which are recommended releases (use latest patch)
- CSCvh93370 - ISE Guest: Incorrect accounting in syslog causes issues
- CSCux55288 - Guest remember-me breaks ISE Guest Activity Logging
- CSCvg19708 - Guest accounting report broken
- Radius Accounting contains MAC address. Makes reporting very difficult.
Setting in 2.4 to revert behavior (not available in 2.3)
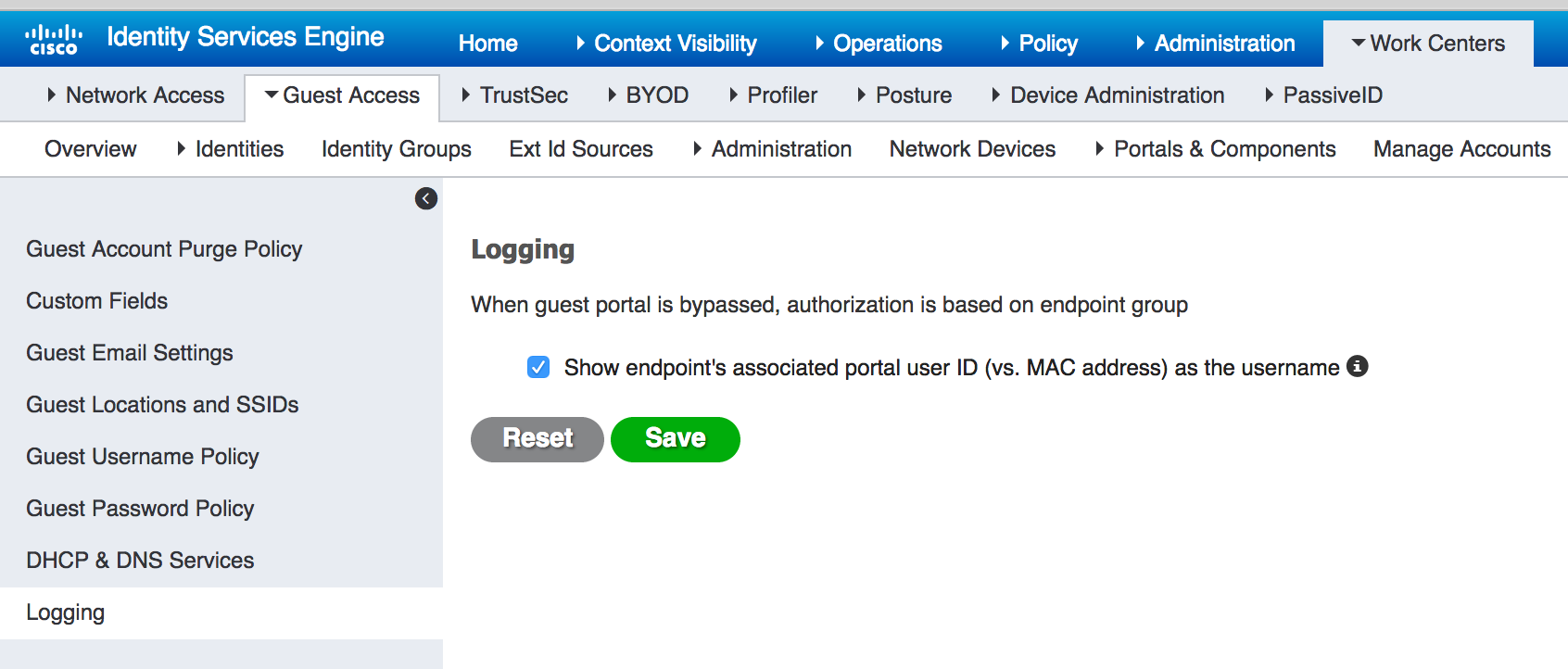
The screen shot from the WLC below shows the Authenticated user (who was authenticated via Remember Me) as the MAC address of the guestendpoint. We would like it to show the actual guest user as is showing in the livelogs. See CSCvh04231 listed above
From ISE 2.3, The Identity column now displays the username that was used during portal login for subsequent logins (previously it used to display the MAC address) in 2.4 the live sessions also shows the guest rewrite
Click on pic to gain better clarity
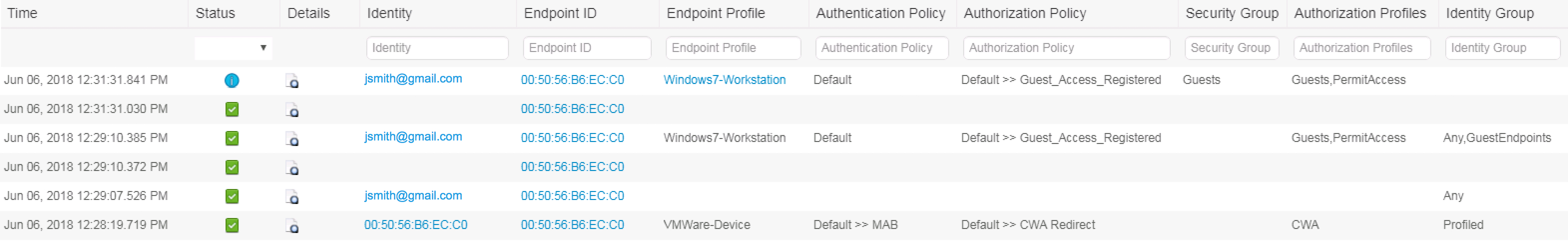
Syslog Update for 2.4 patch 1
adds new variable UserName, this allows to keep same behavior with prior releases and also for systems looking to track guest via syslog (external vendor perhaps) then they will be able to key off it. We hope to change this in the future.
- When a new device is seen on the network it is redirect to the guest portal for credentialed login. After they login the User-Name (common variable sent to NAD) will show the guest username. Also the UserName field should show same.
- After a device is gone for a while and comes back they will now be in the Remember Me flow and authorized off GuestEndpoint with no portal login. Because of this the User-Name only contains the mac address. The newly introduced UserName will still have the guest user (portaluser) attached to it.
MAB + CWA login:
cisco.mnt.collection.syslog.SyslogCollectorUsingPacket: UdpMessage: <181>Jun 27 14:58:15 ise115 CISE_Passed_Authentications 0000001221 1 0 2018-06-27 14:58:15.476 +05:30 0000008146 5231 NOTICE Guest: Guest Authentication Passed, ConfigVersionId=73, AuthenticationMethod=PAP_ASCII, NAS-IP-Address=10.126.172.30, Framed-IP-Address=10.10.40.251, Calling-Station-ID=1c-36-bb-f0-e9-9a, UserType=GuestUser, UserName=Guest1, MacAddress=1C:36:BB:F0:E9:9A, IpAddress=10.10.40.251, AuthenticationIdentityStore=Guest Users, PortalName=Self-Registered Guest Portal (default), IdentityGroup=GuestType_Daily (default), PsnHostName=ise115.ise.com, GuestUserName=Guest1, EPMacAddress=1C:36:BB:F0:E9:9A, NADAddress=10.126.172.30, AuditSessionId=1eac7e0a0001691d08f05c57, ResponseTime=70, cisco-av-pair=audit-session-id=1eac7e0a0001691d08f05c57, Step=5231,
Radius Accounting interim:
=======================================
2018-05-22 21:42:24.433 +05:30 0000011733 3002 NOTICE Radius-Accounting: RADIUS Accounting watchdog update, ConfigVersionId=77, Device IP Address=10.126.172.30, UserName=Guest1, RequestLatency=20, NetworkDeviceName=WLC30, User-Name=02-1A-78-34-21-D3, NAS-IP-Address=10.126.172.30, NAS-Port=1, Service-Type=Authorize Only, Framed-IP-Address=10.10.40.207, class="CACS":1eac7e0a000163cc1ad82d57:ise115/316103314/416, Called-Station-ID=00-0c-29-d1-5d-e5, Calling-Station-ID=02-1a-78-34-21-d3, NAS-Identifier=anand-ctlr, Acct-Status-Type=Interim-Update, Acct-Delay-Time=0, Acct-Input-Octets=0, Acct-Output-Octets=0, Acct-Session-Id=572dd822/02:1a:78:34:21:d3/11180, Acct-Authentic=RADIUS, Acct-Session-Time=44, Acct-Input-Packets=0, Acct-Output-Packets=0, Acct-Input-Gigawords=0, Acct-Output-Gigawords=0, Event-Timestamp=1462622286, NAS-Port-Type=Wireless - IEEE 802.11, Tunnel-Type=(tag=0) VLAN, Tunnel-Medium-Type=(tag=0) 802, Tunnel-Private-Group-ID=(tag=0) 200, Framed-IPv6-Prefix=fe80::/64, cisco-av-pair=audit-session-id=1eac7e0a000163cc1ad82d57, Airespace-Wlan-Id=10, AcsSessionID=ise115/316103314/417, SelectedAccessService=Default Network Access, Step=11004, Step=11017, Step=15049, Step=15008, Step=22094, Step=11005, NetworkDeviceGroups=IPSEC#Is IPSEC Device#No, NetworkDeviceGroups=Location#All Locations, NetworkDeviceGroups=Device Type#All Device Types, CPMSessionID=1eac7e0a000163cc1ad82d57, Network Device Profile=Cisco, Location=Location#All Locations, Device Type=Device Type#All Device Types, IPSEC=IPSEC#Is IPSEC Device#No
Stop:
==========================================================
2018-05-22 21:45:43.542 +05:30 0000011776 3001 NOTICE Radius-Accounting: RADIUS Accounting stop request, ConfigVersionId=77, Device IP Address=10.126.172.30, UserName=Guest1, RequestLatency=13, NetworkDeviceName=WLC30, User-Name=02-1A-78-34-21-D3, NAS-IP-Address=10.126.172.30, NAS-Port=1, Service-Type=Authorize Only, Framed-IP-Address=10.10.40.207, class="CACS":1eac7e0a000163cc1ad82d57:ise115/316103314/416, Called-Station-ID=00-0c-29-d1-5d-e5, Calling-Station-ID=02-1a-78-34-21-d3, NAS-Identifier=anand-ctlr, Acct-Status-Type=Stop, Acct-Delay-Time=0, Acct-Input-Octets=79692, Acct-Output-Octets=75665, Acct-Session-Id=572dd822/02:1a:78:34:21:d3/11180, Acct-Authentic=RADIUS, Acct-Session-Time=244, Acct-Input-Packets=731, Acct-Output-Packets=250, Acct-Terminate-Cause=Admin Reset, Acct-Input-Gigawords=0, Acct-Output-Gigawords=0, Event-Timestamp=1462622486, NAS-Port-Type=Wireless - IEEE 802.11, Tunnel-Type=(tag=0) VLAN, Tunnel-Medium-Type=(tag=0) 802, Tunnel-Private-Group-ID=(tag=0) 200, Framed-IPv6-Prefix=fe80::/64, cisco-av-pair=audit-session-id=1eac7e0a000163cc1ad82d57, Airespace-Wlan-Id=10, AcsSessionID=ise115/316103314/420, SelectedAccessService=Default Network Access, Step=11004, Step=11017, Step=15049, Step=15008, Step=22094, Step=11005, NetworkDeviceGroups=IPSEC#Is IPSEC Device#No, NetworkDeviceGroups=Location#All Locations, NetworkDeviceGroups=Device Type#All Device Types, CPMSessionID=1eac7e0a000163cc1ad82d57, Network Device Profile=Cisco, Location=Location#All Locations, Device Type=Device Type#All Device Types, IPSEC=IPSEC#Is IPSEC Device#No,
Start
====================================================
2018-05-22 21:46:33.515 +05:30 0000011808 3000 NOTICE Radius-Accounting: RADIUS Accounting start request, ConfigVersionId=77, Device IP Address=10.126.172.30, UserName=Guest1, RequestLatency=11, NetworkDeviceName=WLC30, User-Name=02-1A-78-34-21-D3, NAS-IP-Address=10.126.172.30, NAS-Port=1, Framed-IP-Address=10.10.40.207, class="CACS":1eac7e0a000163cd44d92d57:ise115/316103314/421, Called-Station-ID=00-0c-29-d1-5d-e5, Calling-Station-ID=02-1a-78-34-21-d3, NAS-Identifier=anand-ctlr, Acct-Status-Type=Start, Acct-Session-Id=572dd947/02:1a:78:34:21:d3/11181, Acct-Authentic=RADIUS, Event-Timestamp=1462622535, NAS-Port-Type=Wireless - IEEE 802.11, Tunnel-Type=(tag=0) VLAN, Tunnel-Medium-Type=(tag=0) 802, Tunnel-Private-Group-ID=(tag=0) 200, Framed-IPv6-Prefix=fe80::/64, cisco-av-pair=audit-session-id=1eac7e0a000163cd44d92d57, Airespace-Wlan-Id=10, AcsSessionID=ise115/316103314/422, SelectedAccessService=Default Network Access, Step=11004, Step=11017, Step=15049, Step=15008, Step=22095, Step=11005, NetworkDeviceGroups=IPSEC#Is IPSEC Device#No, NetworkDeviceGroups=Location#All Locations, NetworkDeviceGroups=Device Type#All Device Types, CPMSessionID=1eac7e0a000163cd44d92d57, Network Device Profile=Cisco, Location=Location#All Locations, Device Type=Device Type#All Device Types, IPSEC=IPSEC#Is IPSEC Device#No
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hello,
This works well on a single flow (simple guest or selfreg).
In the case of a second redirection in the same flow towards a hotspot portal for endpoint group differentiation, the UserName is no longer populated in the logging messages (it makes sense, as it is a hotspot portal). Would there be a workaround for this case?
Thanks
Gustavo
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Good point as the endpoint and user are linked together in the initial flow and the redirect to a hotspot portal is simply a device registration
No I don’t think there is a way
Please when requesting feature request mention you need a true remember me with different endpoint group association depending on user group criteria
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community:




