
These attributes are used with Device Administration / TACACS+ and are found as dictionaries and attributes in the Cisco Identity Services Engine (ISE) Conditions Studio when configuring a Device Administration Policy Set :
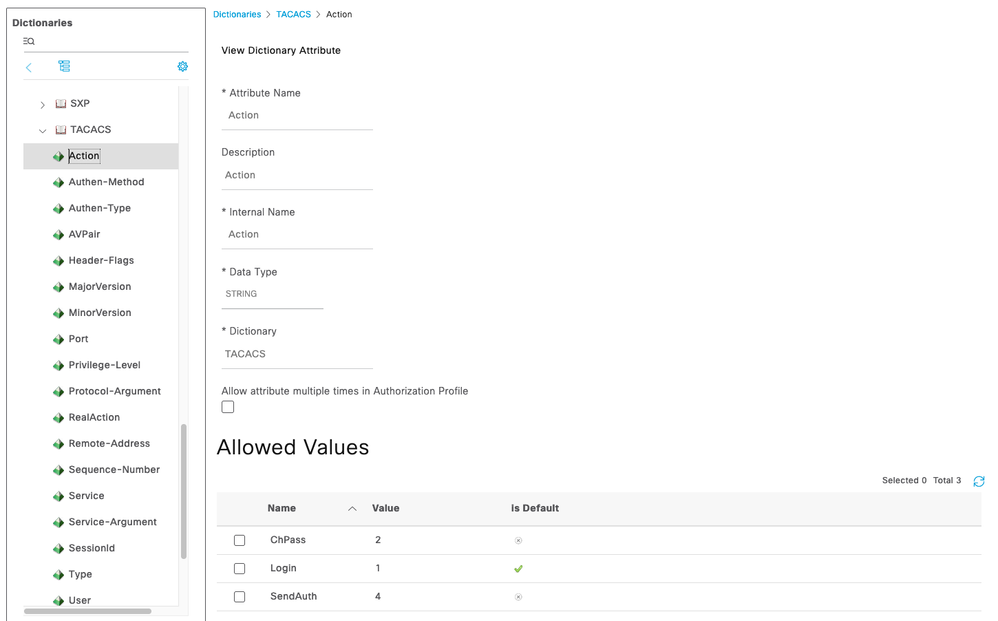
These dictionaries and attributes are also listed in the ISE Dictionaries (Policy > Policy Elements > Dictionaries) under TACACS. You may select an attribute and view it's Allowed Values:
| Attribute |
Values |
ISE
Version |
Usage Description |
Device
|
|
|
|
| Device Type |
|
2.x |
|
| IPSEC |
|
2.x |
|
| Location |
|
2.x |
|
| Model Name |
|
2.x |
|
| Network Device Profile |
|
2.x |
|
| Software Version |
|
2.x |
|
IdentityGroup
|
|
|
|
| Description |
|
2.x |
|
| Name |
|
2.x |
|
InternalUser
|
|
|
|
| Description |
|
2.x |
|
| EnableFlag |
|
2.x |
|
| Firstname |
|
2.x |
|
| IdentityGroup |
|
2.x |
|
| Lastname |
|
2.x |
|
| Name |
|
2.x |
|
| OPC |
|
? |
|
| SubscriberKey |
|
? |
|
| UserType |
|
2.x |
|
Network Access
|
|
|
|
| AD-Host-DNS-Domain |
|
2.x |
|
| AD-Host-Join-Point |
|
2.x |
|
| AD-User-DNS-Domain |
|
2.x |
|
| AD-User-Join-Point |
|
2.x |
|
| AuthenticationIdentityStore |
|
2.x |
|
| AuthenticationMethod |
|
2.x |
|
| AuthenticationStatus |
|
2.x |
|
| Device IP Address |
|
2.x |
|
| EapAuthentication |
|
2.x |
|
| EapChainingResult |
|
2.x |
|
| EapTunnel |
|
2.x |
|
| GroupsOrAttributesProcessFailure |
|
2.x |
|
| ISE Host Name |
|
2.x |
|
| MachineAuthenticationIdentityStore |
|
2.x |
|
| NetworkDeviceName |
|
2.x |
|
| Protocol |
|
2.x |
|
| RADIUS Server |
|
2.x |
|
| RADIUS Server Sequence |
|
2.x |
|
| SessionLimitExceeded |
|
2.x |
|
| UseCase |
|
2.x |
|
| UserName |
|
2.x |
|
| VN |
|
? |
|
| WasMachineAuthenticated |
|
2.x |
|
TACACS
|
|
|
These were taken from RFC-8907, The Terminal Access Controller Access-Control System Plus (TACACS+) Protocol |
| Action |
|
2.x |
action
This indicates the authentication action.
TAC_PLUS_AUTHEN_LOGIN := 0x01
TAC_PLUS_AUTHEN_CHPASS := 0x02
TAC_PLUS_AUTHEN_SENDAUTH := 0x04 |
| Authen-Method |
|
2.x |
|
| Authen-Type |
|
2.x |
|
| AVPair |
|
2.x |
|
| Header-Flags |
|
2.x |
flags
This field contains various bitmapped flags. |
| MajorVersion |
|
2.x |
major_version
This is the major TACACS+ version number.
TAC_PLUS_MAJOR_VER := 0xc |
| MinorVersion |
|
2.x |
minor_version
This is the minor TACACS+ version number.
TAC_PLUS_MINOR_VER_DEFAULT := 0x0
TAC_PLUS_MINOR_VER_ONE := 0x1 |
| Port |
|
2.x |
|
| Privilege-Level |
|
2.x |
priv-lvl (Numeric)
The privilege level to be assigned.
TAC_PLUS_PRIV_LVL_MIN := 0x00. The level normally allocated to an unauthenticated session.
TAC_PLUS_PRIV_LVL_USER := 0x01. The level normally allocated to a regular authenticated session.
TAC_PLUS_PRIV_LVL_ROOT := 0x0f. The level normally allocated to a session authenticated by a highly privileged user to allow commands with significant system impact.
TAC_PLUS_PRIV_LVL_MAX := 0x0f. The highest privilege level. |
| Protocol-Argument |
|
2.x |
|
| RealAction |
|
2.x |
Same as Action |
| Remote-Address |
|
2.x |
|
| Sequence-Number |
|
2.x |
seq_no
This is the sequence number of the current packet. The first
packet in a session MUST have the sequence number 1, and each subsequent packet will increment the sequence number by one. TACACS+ clients only send packets containing odd sequence numbers, and TACACS+ servers only send packets containing even sequence numbers. |
| Service |
|
2.x |
authen_service
This is the service that is requesting the authentication.
TAC_PLUS_AUTHEN_SVC_NONE := 0x00
TAC_PLUS_AUTHEN_SVC_LOGIN := 0x01 (default)
TAC_PLUS_AUTHEN_SVC_ENABLE := 0x02
TAC_PLUS_AUTHEN_SVC_PPP := 0x03
TAC_PLUS_AUTHEN_SVC_PT := 0x05
TAC_PLUS_AUTHEN_SVC_RCMD := 0x06
TAC_PLUS_AUTHEN_SVC_X25 := 0x07
TAC_PLUS_AUTHEN_SVC_NASI := 0x08
TAC_PLUS_AUTHEN_SVC_FWPROXY := 0x09 |
| Service-Argument |
|
2.x |
Use the Service-Argument to determine which vendor/product the request is coming from.
| Vendor |
Service-Argument |
| Avaya |
? |
| Brocade |
? |
| Checkpoint |
? |
| Cisco |
shell |
| Juniper |
junos-exec |
| Alcatel |
? |
| Altheon |
? |
| F5 |
F5-LTM-User-Info-1=ADMIN_ROLE
F5-LTM-User-Console=1
F5-LTM-User-Role=0
F5-LTM-User-Partition=all
F5-BIGIQ-User-Info-01=bigiq-admin |
| Extreme |
? |
| Fortinet |
admin_prof=super_admin
memberof=Fortinet_Admins |
| HP |
? |
| Huawei |
? |
| MicroTik |
? |
| Omnivista |
? |
| Palo Alto |
? |
| Riverbed |
riverbed-roles-list=System Administrator
service=system |
|
| SessionId |
|
2.x |
session_id
The Id for this TACACS+ session. This field does not change for the duration of the TACACS+ session. This number MUST be generated by a cryptographically strong random number generation method. Failure to do so will compromise security of the session. For more details, refer to [RFC4086]. |
| Type |
|
2.x |
type
This is the packet type.
TAC_PLUS_AUTHEN := 0x01 (Authentication)
TAC_PLUS_AUTHOR := 0x02 (Authorization)
TAC_PLUS_ACCT := 0x03 (Accounting) |
| User |
|
2.x |
a user (or entity) |