- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ISE Easy Connect
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
06-15-2016 11:54 AM - edited 11-20-2023 09:48 AM
- Get Started
- 802.1X vs Easy Connect Comparison
- Enable Easy Connect
- Easy Connect Authorization Policies
- Resources
ISE 2.1 introduced a new feature called Easy Connect where Microsoft Active Directory (AD) logins are used to passively map user information onto existing network sessions initiated with MAC Authentication Bypass (MAB). This is similar to a Centralized Web Authentication (CWA) or CWA Chaining scenario where ISE combines an active MAB or 802.1X authentication session with the identity obtained from a Web Authentication. ISE leverages the identity and group memberships from the passive identity (PassiveID) to be used as conditions to assign policy.
The benefits of Easy Connect over 802.1X are:
- No 802.1X supplicant required for user authentication
- No Public Key Infrastructure (PKI) required for trusted credential transport
- Can be used as primary user identity or supplement another active identity such as MAB or 802.1X
Get Started
How to Configure Easy Connect on ISE 2.1
802.1X vs Easy Connect Comparison
| 802.1X | Easy Connect | |
|---|---|---|
| Requires Microsoft Active Directory | No | Yes, with WMI access allowed from ISE |
| Identity Stores |
|
Microsoft Active Directory |
| Machine Authentication Methods |
|
None |
| User Authentication Methods |
|
Kerberos User login - not Machine |
| User Logoff Detection | Yes. Note: Fast User Switching (FUS) not detected |
No - not detected via WMI, but AD login from different user will overwrite Passive Identity for endpoint. Note: Fast User Switching (FUS) not detected. |
| Session Expiration | RADIUS Session-Timeout (configurable in ISE authorization policy results) | User Session age (configurable in ISE Active Directory settings) |
| Supported Operating Systems |
|
|
| Agents |
|
None (Microsoft Windows OS) |
| Network Devices |
|
|
| NAD Configuration | 802.1X See the ISE Design Guides for best practice switchport configs |
MAB or 802.1X (required for ISE to stitch RADIUS session with PassiveID info) |
| Enforcement | VLANs, dACLs, SGTs | VLANs, dACLs, SGTs |
| Identity & Session published to pxGrid | Yes | Yes |
| Scale | Depends on the Authentication Method's encryption requirements and round-trips. See ISE Performance & Scale |
TBD |
Enable Easy Connect
How to Configure Easy Connect on ISE 2.1
To enable Easy Connect in ISE:
- Navigate to Administration > System > Deployment > (node) > General Settings
- Enable Passive Identity Service on PSN
Note: It is recommended to enable Easy Connect on two PSN nodes for high availability but no more than two.
Note: Dedicated PSNs are recommended for Easy Connect Passive Identity Mapping - Navigate to Administration > PassiveID > AD Domain Controllers
- Select Add and provide the credentials to your Active Directory domain controllers for PassiveID. Alternatively, you may Import a list of AD controllers via a CSV file.
- You may customize your Passive Identity caching options under Active Directory General Settings.
The User Session Timer is reset when there is a 1) new AD login with the same username or 2) Kerberos ticket renewal
Easy Connect Authorization Policies
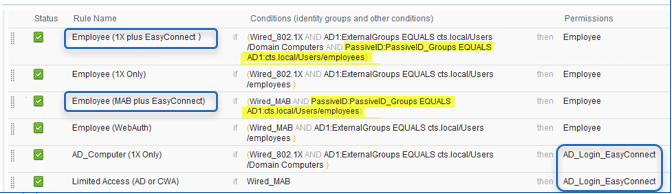
Here are a few examples of ISE authorization policies using the PassiveID attributes from Easy Connect :
Resources
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Hi Thomas,
Thanks for the wonderful article.
May i please check with 2 things :
1. Does Easy Connect Supported on Wireless network also (CISCO AP & WLC).
2. Can Easy Connect & BYOD Solution co-exist on the same ISE box (With Different AUTHE & AUHTO Profile).
Thanks
MS
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
When will support for Mac come about?
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: