- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- ISE's Relationship with the 'Pre-Windows 2000 Compatible Access' Group
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
03-06-2025 01:01 PM - edited 03-06-2025 01:14 PM
In ISE Admin Guide, we read:
Cisco ISE uses Microsoft Active Directory as an external identity source to access resources such as users, machines, groups, and attributes. User and machine authentication in Active Directory allows network access only to users and devices that are listed in Active Directory. After a Cisco ISE node joins Active Directory, in Active Directory, it is a member of the Authenticated Users group. The Authenticated Users group is a member of the Pre-Windows 2000 group by default. If you disable the Pre-Windows 2000 Compatible Access group or remove Authenticated Users from the Pre-Windows 2000 Compatible Access group, authentication failures occur. We recommend that you do not disable the Pre-windows 2000 Compatible Access group. However, if you must disable this group for any reason, grant the “Read Remote Access Information” permission to Cisco ISE in AD for the relevant users or users' folders.
In the statement above, several topics need to be carefully clarified, as many Active Directory hardening documents recommend removing members from the 'Pre-Windows 2000 Compatible Access' group or even revoking the group's permissions entirely from the domain. I have handled several TAC cases that were directly or indirectly related to this operation, which was carried out by the network administrator. As a result, ISE was no longer able to fetch groups attributes from Active Directory.
Now, let's clarify the purpose of the 'Pre-Windows 2000 Compatible Access' group in Active Directory:
One of the key topics in Active Directory hardening revolves around a common concept frequently raised by hardening team members: 'Everyone Can See Everything in AD!' Before we dive into defining the visibility of AD objects, let's first examine the default ACLs assigned when an AD domain is created. These permissions may be assumed by poorly designed applications or older ones dating back to the Windows NT era. Such applications may fail to function correctly until they can retrieve all the information exposed by the default settings.
When it comes to revealing more information than we'd like to expose, we can focus on unprivileged identities. The permissions granted to these identities by default are often described, in simple terms, as 'everyone can see everything in AD.' To better understand this, we need to examine the following permission levels:
- Permissions granted to literally everyone—i.e., the 'Everyone' group, which includes guest accounts. Prior to Server 2003, this group also included anonymous access.
- Permissions granted to the ‘Authenticated Users’ group.
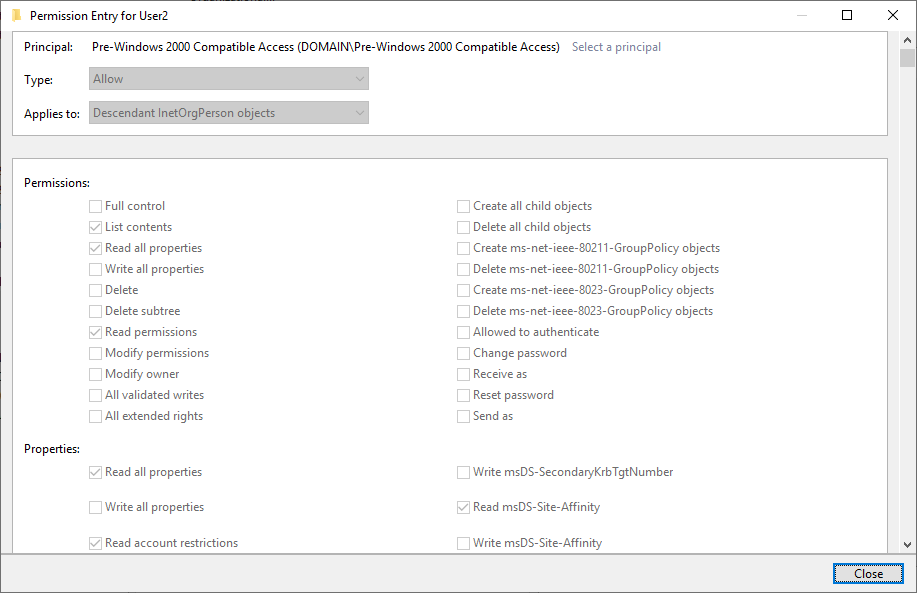
- Permissions granted to the 'Pre-Windows 2000 Compatible Access' group, which by default includes 'Authenticated Users' as members. In other words, the 'Authenticated Users' group is nested within the 'Pre-Windows 2000 Compatible Access' group by default, as you can see below:
- Permissions granted to ‘Domain Users’ and ‘Domain Computers’.
There is one major difference in handling permissions granted to special groups, such as 'Authenticated Users,' and real groups, such as 'Domain Users.' A security principal's membership in a real group can be removed, allowing you to keep the default ACEs in place and simply remove the unprivileged object from the respective group. Membership in a special group represents a hardcoded behavior of the operating system. Therefore, the only way to revoke permissions granted to a special group is by removing the ACEs. Keep in mind that removing default ACEs makes it harder to create exceptions or roll back hardening changes.
The following permissions are granted by default on user objects for the 'Pre-Windows 2000 Compatible Access' group:
- Read “Account Restrictions”
- Read “Logon Information”
- Read “Group Membership”
- Read “General Information”
- Read “Remote Access Information”
- Read all properties
- Read permissions
- List contents
The following permissions are granted by default on user objects for the 'Everyone' group:
- Change password
The following permissions are granted by default on user objects for the 'Authenticated Users' group:
- Read “General Information”
- Read “Public Information”
- Read “Personal Information”
- Read “Web Information”
Apart from the 'Read permissions' ACE for ‘Authenticated Users’, all attributes directly related to security are readable by the 'Pre-Windows 2000 Compatible Access' group rather than 'Authenticated Users' or 'Everyone.' Based on this fact, it's clear why security hardening teams strongly recommend removing the 'Pre-Windows 2000 Compatible Access' group access from objects in AD. For computers and groups, the impact of the legacy access group on information disclosure is less significant. In other words, in Windows NT domains (which is what 'Pre-Windows 2000' refers to), these object classes had fewer attributes and less functionality compared to user objects.
Hopefully, it is now clear why Cisco does not recommend removing this group's permissions from the domain or revoking the 'Authenticated Users' group membership from this group.
Resources used:
- Cisco ISE Admin Guide
- Microsoft.com
- "Building Modern Active Directory" book from Apress
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Thanks.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: