- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Nexus Integration (For admin access) With Free Radius
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
04-20-2013 12:44 PM - edited 02-21-2020 09:59 PM
- Introduction:
- Prerequisites:
- Components Used:
- Configure Nexus Device for Authentication and Authorization:
- Process to Configure free radius at Server side:
- Verification:
Introduction:
This document provides an example of configuring Radius Authentication on a Nexus switch. By default, if you configure the Nexus to authenticate through Radius, you'll automatically be placed in to the network-operator/vdc-operator role, which provides read-only access.If you want that user to be placed in the network-admin/vdc-admin role, you need to push the following cisco-av-pair.
cisco-avpair := "shell:roles*\"network-admin vdc-admin\""
Prerequisites:
Ensure that you have your Nexus switch defined as a client in free radius with the ip address and same shared secret key defined on the free radius and Nexus.
Note: On Nexus, Create a checkpoint or a backup before making any changes in order to avoid any potential issues related to a misconfiguration.
Components Used:
- Free Radius
- Nexus 5000, 5.2(1)N1(1)
Configure Nexus Device for Authentication and Authorization:
1. Create a local user on the switch with full privileges for fallback with the username command as shown here:
Switch(config)#username admin privilege 15 password 0 cisco123!
2. Provide the IP address of the Radius server (Free Radius)
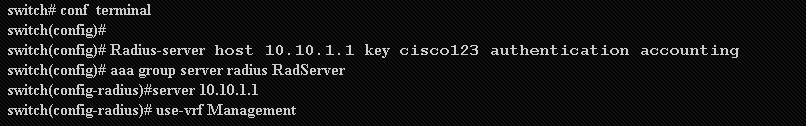
Note: The key must match the Shared Secret configured on the free radius for this Nexus device.
3. Test the RADIUS server availability with the test aaa command as shown.
switch# test aaa server Radius 10.10.1.1 user1 Ur2Gd2BH
Test authentication will fail with a Reject from the server since it is not configured, However, it will confirms that server is reachable.
4. Configure login authentications as shown here:
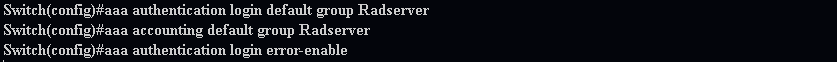
Note: You dont have to worry about the local fallback method here, Because, Nexus fallback to local on its own if the tacacs is not available.
Process to Configure free radius at Server side:
- Configuration on FreeRadius Server:
- Defining Client on the Free Radius server:
- Move to the config directory:
cd /etc/freeradius
- Edit the clients.conf file:
sudo nano clients.conf
- Add each device (router or switch), which is identified by its hostname and requires secret key:
client 192.168.179.152 {secret = secretkeynastype = ciscoshortname = switch}
- Restart the FreeRADIUS service:
sudo /etc/init.d/freeradius restart
Push the below role, The user in the nexus will get the network-admin role. This one is applicable for the whole group. As you have defined Default group=cisco-rw.
DEFAULT Group == cisco-rw, Auth-Type = System
Service-Type = NAS-Prompt-User,
cisco-avpair := "shell:roles*\"network-admin vdc-admin\"",
Note:The configuration of Free Radius is done on Ubuntu(Linux) Server. The commands may differ in any other Linux OS.
Verification:
To verify the configuration on Nexus use the following commands:
- switch# show Radius
- switch# show running-config aaa
- switch# show startup-config Radius
#Please post comments if there are any queries and rate if useful
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
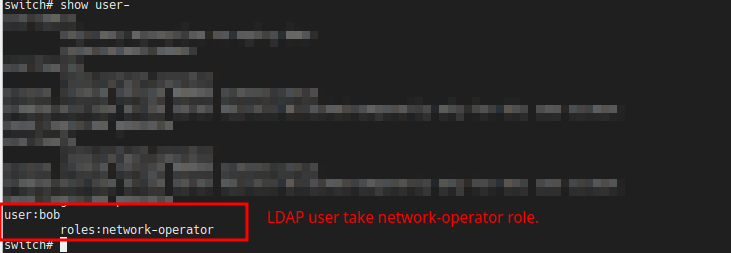
Hi @minkumar. Thanks for the excellent post. I have a different issue, it seems. Perhaps I am doing something wrong.
I have set up freeradius RADIUS server and integrated to my LDAPS server. I am able to successfully log-in and verify when a user is connected or not via LDAPS, but when I attempt to authenticate to my NX-OS switch I am always getting a network-admin level privilege.
I have tried setting up Admin and Reader privileges which correspond to network-admin and network-operator roles on the NX-OS switch.
I am hoping that I would be able to have four occurrences:
1. user is not in LDAP at all - RADIUS server denies access
2. user is in LDAP, but not in the LDAP groups (Admin/Reader) and the RADIUS server denies access
3. User is in LDAP, and is in the Admin group, so is placed into network-admin role
4. User is in LDAP, and is in the Reader group, so is placed into network-operator role
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
hi @TrivialPants, In my case, I really need network-operator level but getting network-admin for every login with LDAP's user. Did you find your answer?
Please share with me the configuration. Thank for your help
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: