- Cisco Community
- Technology and Support
- Security
- Security Knowledge Base
- Protecting Access to Network devices with ISE TACACS+ and DUO MFA
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
01-20-2019 03:13 PM - edited 02-21-2020 10:02 PM
- Objective
- Network Policy
- Connection Flow
- Assumptions
- Enable ISE Device Administration Service (TACACS)
- Configuration for RADIUS communication between ISE and DUO
- Create an Active Directory Join Point in ISE
- Add Network Device
- Enable Device Administration
- Assigning device administration privileges based on Active Directory group membership
- Validation
Objective
I would like to protect access to my network devices (Wired switches, Wireless lan controllers and Firewall) and enhance authentication using MFA.
Network Policy
Employee’s can connect to my network devices and can view and edit the configurations. Contractors can connect to my network devices but can only view the configurations.
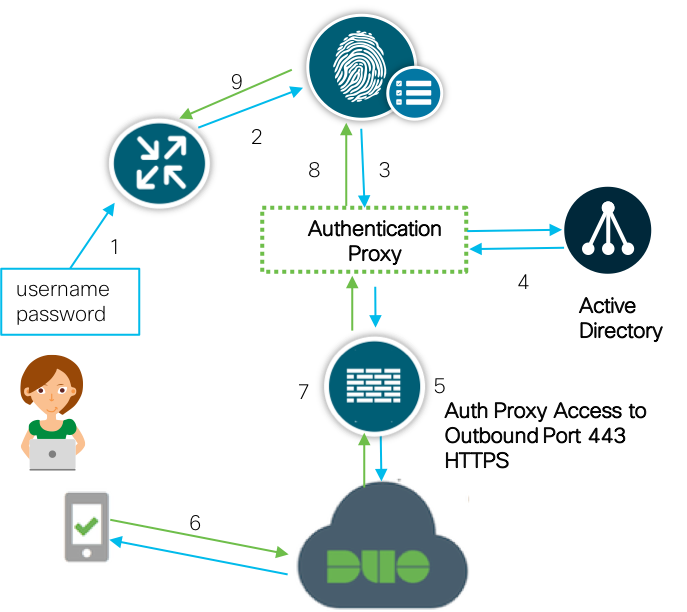
Connection Flow
1. User initiates a SSH connection to the router
2. Router sends TACACS+ authentication request to ISE
3. ISE sends RADIUS to Duo Security's authentication proxy
4. Primary authentication uses Active Directory
5. Duo authentication proxy connection established to Duo Security over TCP port 443
6. Secondary authentication via Duo Security's service
7. Duo authentication proxy receives authentication response
8. SSH access granted per ISE Device Admin policy set
Assumptions
This guide assumes:
- The reader is familiar with the Cisco Identity Services Engine (ISE) features and functions
- The reader is familiar with the configuration of ISE AAA functions
Enable ISE Device Administration Service (TACACS)
Step 1. Navigate to Administration->System->Deployment
Step 2. Enable "Device Administration Service" on the appropriate node
Step 3. Click Save
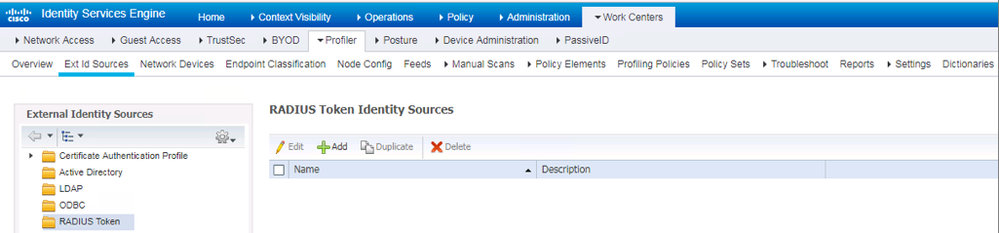
Configuration for RADIUS communication between ISE and DUO
Step 1. On ISE, navigate to WorkCenters->Device Administration->Ext Id Sources->RADIUS Token
Step 2. Click Add
Step 3. Starting from left to right, configure the settings within each tab menu item as follows:
a. In the General tab, configure a name for the configuration
b. In the Connection tab, configure the Primary Server details:
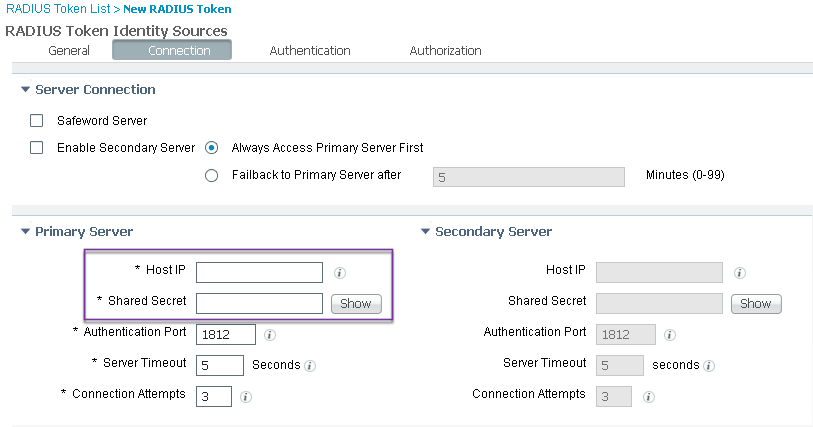
Step 4. Click Submit
Create an Active Directory Join Point in ISE
With DUO auth proxy as the authentication ID source, no group information is returned. As a result, we also connect ISE to Active Directory as the authorization ID source.
Note: If you already have integrated ISE with AD, skip this section
Step 5. Under Work Centers->Device Administration, select the submenu Ext Id Sources. In the left-hand pane, select Active Directory
Step 6. Click +Add in the right-hand pane and fill in as below and click Submit. Click "Yes" when asked "Would you like to Join all ISE Nodes to this Active Directory Domain?".
Step 7. In the Join Domain pop-up windows, fill in the necessary details:
Step 8. Click OK to start the join operation. A window "Join Operation Status" will pop up. Wait until the node status changes to Completed and then click Close
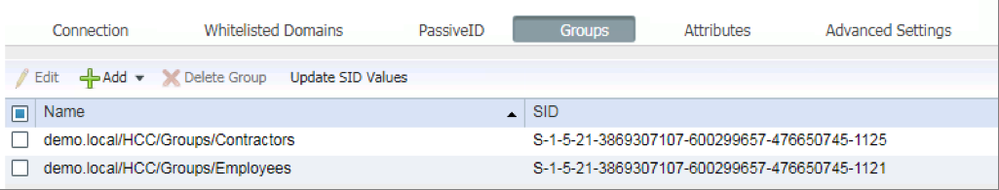
Step 9. Navigate to the Groups tab and add the Employees and Contractors groups
Add Network Device
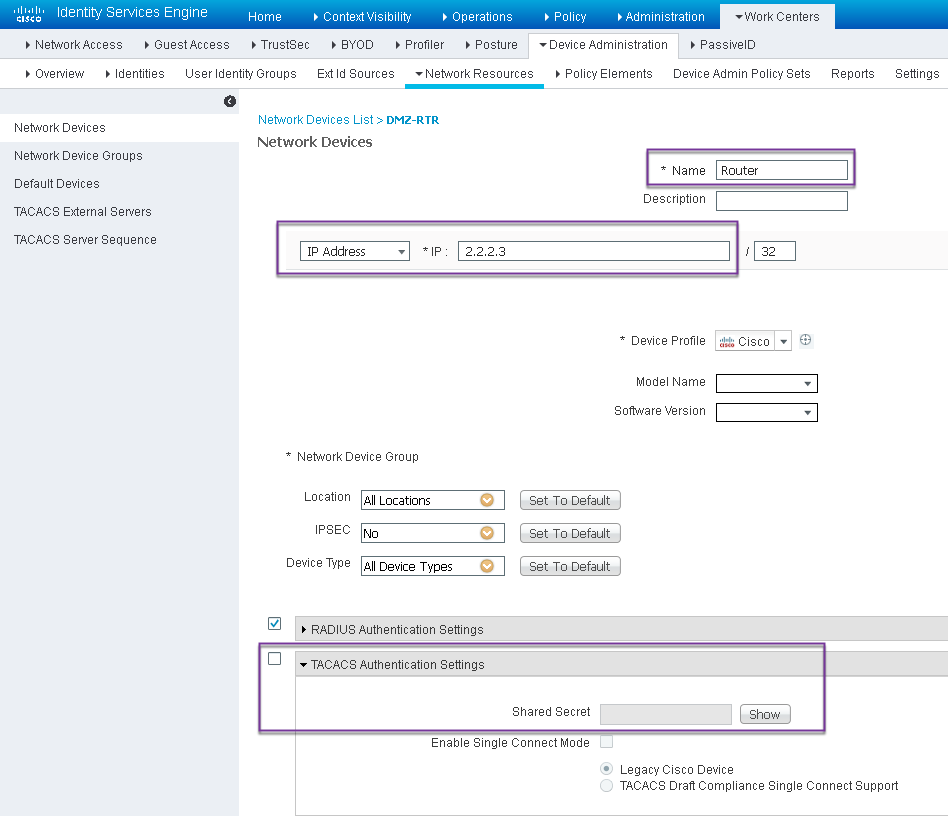
Step 10. Navigate to Work Centers->Device Administration-> Network Resources-> Network Devices
Step 11. Click Add. Provide Name, IP Address, select TACACS Authentication Settings checkbox and provide Shared Secret key.
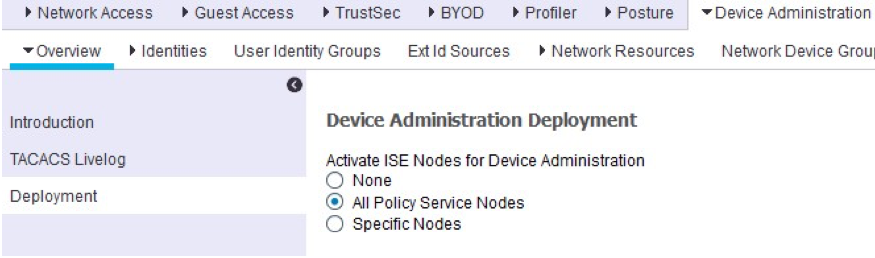
Enable Device Administration
Step 10. Navigate to Work Centers->Device Administration. Select Deployment from the left-hand pane to jump to the page Device Administration Deployment. Select the appropriate ISE node configuration option
Step 11. Click Save when finished
Assigning device administration privileges based on Active Directory group membership
Step 12. Navigate to Work Centers->Device Administration->Device Admin Policy Sets
Step 13. Configure the identity store for the Authentication Policy to the policy that you configured in step 3a
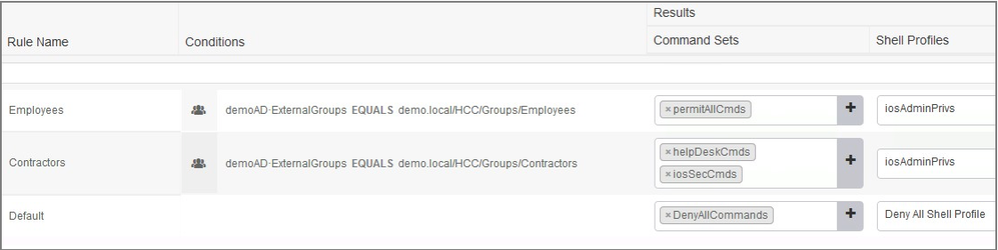
Step 14. Configure the authorization results within the authorization policy to assign the command sets and shell profiles for each user group. See below for an example:
Validation
- SSH to the network device
- Log in
- When prompted for password, enter in this exact sequence : “ <login password>, <pin code on Duomobile app>”
- Once logged in, verify that the user is able to execute the defined command sets
- To review logs, on ISE Navigate to Operations-> TACACS->Live logs
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
I have this (almost) working with ISE 3.1 and a 3850 switch. We were using TACACS+ already. I added DUO to the mix and when entering my password in the SSH session, I only have maybe 3 seconds before the switch says
End of keyboard-interactive prompts from server
Access denied
It then presents a new Password: prompt. If I manage to have my mobile device in hand and can accept the DUO push quickly enough, I get in. If the switch already says Access denied and gives a new Password: prompt, it doesn't let me in. ISE and DUO logs show that I successfully authenticated, but ISE logs only show successful authorization if I accept the DUO push in that very short period of time.
My question is where can this be adjusted? Ideally a user would have 10 seconds or so to pick up their device and accept the DUO push.
Thanks,
- Mark as Read
- Mark as New
- Bookmark
- Permalink
- Report Inappropriate Content
Answering my own question from earlier. On the switch I was testing with, there was a default "tacacs-server timeout 5" that doesn't show up in running-config unless you show running-confg all. I changed that value to 30 and now we have a proper 30 second window to receive and accept the DUO push before the switch times out the login attempt.
Find answers to your questions by entering keywords or phrases in the Search bar above. New here? Use these resources to familiarize yourself with the community: